Transcription
TMTechnical infrastructureand securityPanopto cloud video platformpanopto.com
ContentsIntroduction3Architecture4- Hardware and software4- Panopto components/prerequisites4- Amazon server locations5- Amazon content backup and disaster recovery5- Panopto server redundancy and business continuity6- Panopto server architecture8- Panopto content delivery with Amazon CloudFront9Security10- Amazon EC2 security10- Certifications and accreditations11- Network security11- Environmental safeguards12- Components14- Panopto application security15Availability and maintenance16- Panopto SLA16- Amazon SLA16- Upgrades and maintenance17Appendix A182 of 17 Technical infrastructure and securitypanopto.com
IntroductionPanopto’s online video platform can be deployedeither as a cloud-hosted service or as an on-premisessolution. With the cloud-hosted service, Panoptomaintains server infrastructure and ensures itscontinuous, optimal delivery.This document covers the physical infrastructureand security protocols of the Panopto cloudhosted service. It provides specifications for all ofthe hardware components, network routing, andapplication security features that comprise thePanopto Cloud. Information detailing networksecurity for Amazon Web Services (AWS) – whichprovides the backbone for the Panopto Cloud– as well as information on backup procedures,redundancy, and protection against commonsecurity threats is included.3 of 17 Technical infrastructure and securitypanopto.com
ArchitectureHardware and softwarePanopto’s cloud service enables customers to usePanopto software hosted on Panopto servers.Panopto Cloud is hosted on Amazon Web Serviceswith geographic server options in the United States,European Union, Canada, and Asia Pacific.Panopto Cloud is secure, scalable, has highavailability for redundancy, and is built to ensureuptime and reliability.The Panopto software is installed on Amazon EC2instances, uses Amazon S3 for content storageand Amazon CloudFront as the contentdelivery network.Panopto cloud componentsWeb server componentsData server components Microsoft Windows Server 2019 Internet Information Services (IIS) 10.0 Microsoft .Net Framework 4.6.2 Microsoft Windows Server 2019 Microsoft .Net Framework v 4.6.2 Microsoft PowerPoint 2016Database server components Microsoft Windows Server 2019 Microsoft SQL Server 2019 – latest update4 of 17 Technical infrastructure and securitypanopto.com
Amazon server locationsAmazon EC2 is hosted in multiple locationsworldwide. These locations are composed of regionsand Availability Zones. Each region is a separategeographic area. Each region has multiple, isolatedlocations known as Availability Zones. Amazon EC2provides the ability to place instances and data inmultiple locations. Panopto’s cloud operates out ofmultiple US East (us-east-1), EU West (eu-west-1),AP Southeast (ap-southeast-1), and CA Central(ca-central-1) availability zones, located in the US,Ireland, Singapore, and Montreal.Panopto database and securitylog backupFor disaster recovery and security purposes, Panoptostores copies of its SQL database backups andsecurity log information in geographically andlogically fully distinct regions.SQL database and security logbackup locations:NA Cloud: US East (Ohio) RegionEU Cloud: Europe (London) RegionAmazon content backupand disaster recoveryAP Cloud: Asia Pacific (Sydney) RegionAll of the content for Panopto Cloud is storedin Amazon S3, which is designed to provide99.999999999% durability of objects over a givenyear. Data is redundantly stored across multipleAvailability Zones using multiple devices in eachfacility. Each Availability Zone runs on its ownphysically distinct, independent infrastructureand is engineered to be highly reliable. Commonpoints of failure like generators and coolingequipment are not shared across Availability Zones.Additionally, they are physically separate, such thateven extremely uncommon disasters such as fires,tornados or flooding would only affect a singleAvailability Zone.This backup process increases metadata durabilityin the event of a catastrophic AWS region failure,improves protection against data integrity failures,and provides tamper resistance from maliciousactors.5 of 17 Technical infrastructure and securityCA Cloud: Europe (Ireland) RegionAll data is encrypted at rest and in transit. Pleaserefer to “Encryption” below for more information onPanopto’s encryption standards.Panopto will retain this data for up to five (5) years.panopto.com
Panopto server redundancyand business continuityThe Panopto Cloud solution offers redundancy in multiple AmazonAvailability Zones, eliminating single points of failure and providingadditional reliability. This design provides redundancy for serversused in the hosted architecture including; web servers, data servers,and the database server.Panopto’s relational database is mirrored between multipleAvailability Zones within the region.In the event that a single server goes offline, other servers willstill be available for use. In the event of an availability zone goingcompletely offline, the architecture allows the other availabilityzone to still be available for use. This ensures that customers are notaffected by an availability zone outage.6 of 17 Technical infrastructure and securitypanopto.com
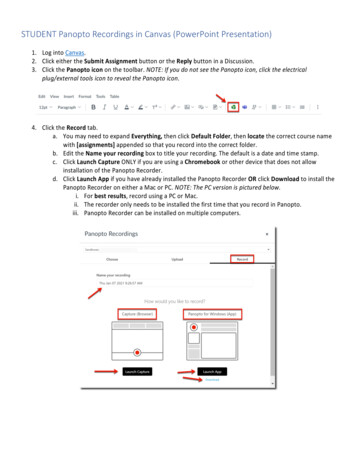
1AAmazonEC2LoadBalancerWebservers 42Elastic LoadBalancingAmazonEC2Synchronous replicationElastic LoadBalancingAuto scalingAmazonS33Auto scalingExample diagram of Panopto’s cloud architectureApplication5serversArchitecture overview1 The Amazon CloudFront CDN is a global network of edgelocations and regional edgecaches that temporarily storescontent close to viewers. AmazonCloudFront ensures that enduser requests are served by theclosest edge location, enablingviewer requests to travel ashorter distance. This improvesperformance.2 HTTPS requests are handled by Elastic Load Balancingwhich automatically distributesincoming application trafficacross multiple PanoptoWeb Servers across multipleAvailability Zones (AZs). Thisenables greater fault tolerance,7 of 17 Technical infrastructure and securityand seamlessly provides loadbalancing capacity needed inresponse to incoming user traffic. 3 Resources and static content usedby Panopto Web Servers are storedin Amazon Simple Storage Service(S3), a highly durable storageinfrastructure designed formission-critical and primary datastorage. S3 is available across allAvailability Zones.4 Panopto uses multiple Web Servers in multiple Availability Zones,providing reliability and redundancyfor customers. Auto Scaling providesPanopto with the on-demand abilityto increase the number ofWeb Servers to accommodateincreased traffic.Auto scalingBAuto baseservers5 Multiple Application Servers or Data Servers are used in multipleAvailability Zones, providingreliability and redundancy toensure that all content isencoded quickly for customers.Additional Data Servers canbe added to accommodateincreased encoding needsfrom customer uploads. 6 Panopto’s SQL databases arelocated in multiple AvailabilityZones and feature synchronoushigh-safety database mirroringwith automatic failover, providingreliability and fault tolerance.panopto.com
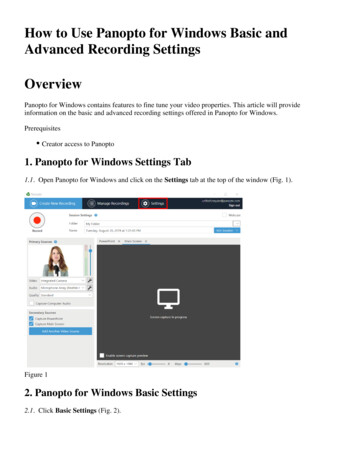
Panopto server architectureThe following diagram displays the Panoptoserver architecture of a single availability zone,the components of each server, and theinteraction with the client.(Note: The amount of servers being used is forreference only; servers are added as needed toaccommodate usage).TCP/IPPorts 80and 443Panopto ServerTCP/IPPorts 80and 443TCP/IPPorts 80and 443CDNStorageAutoscaling MediaProcessorsTCP/IPPorts 80and 443Client (Viewing)Search ServersTCP/IPPorts 80and 443SQL ServerAutoscaling WebServersMobile ClientsiOS and Android appsClient(Recording)Web recorder,third party recorders,Mac recorder, etcLoad BalancerClient ComponentsTCP/IPPorts 80 and 4438 of 17 Technical infrastructure and securitypanopto.com
Panopto content deliverywith Amazon CloudFrontAmazon CloudFront employs a global networkof edge locations and regional edge caches thatcache copies of content close to viewers. AmazonCloudFront ensures that end-user requests areserved by the closest edge location. As a result,viewer requests travel a short distance, improvingperformance for viewers. For files not cached atthe edge locations and the regional edge caches,Amazon CloudFront keeps persistent connectionswith Panopto’s origin servers so that those filescan be fetched from the origin servers as quicklyas possible.To deliver content to end users with lower latency,Amazon CloudFront uses a global network of210 Points of Presence (199 Edge Locations and11 Regional Edge Caches)* in 78 cities across37 countries.* Panopto does not make use of any mainland Chinese CDNs.Amazon continously adds new CDN PoP locations.For more information and an up-to-date list of edge locations,visit: https://aws.amazon.com/cloudfront/details9 of 17 Technical infrastructure and securitypanopto.com
SecurityAmazon EC2 securityCertifications, accreditations, frameworksAWS is compliant with various certifications andthird-party attestations. These include:Certifications /attestationsLaws, regulations,and privacyAlignments /frameworks CS [Germany] Cyber Essentials Plus [UK] DoD SRG FedRAMP FIPS IRAP [Australia] ISO 9001 ISO 27001 ISO 27017 ISO 27018 MTCS [Singapore] PCI DSS Level 1 SEC Rule 17-a-4(f ) SOC 1 SOC 2 SOC 3 CISPE EU Model Clauses FERPA GLBA HIPAA HITECH IRS 1075 ITAR My Number Act [Japan] U.K. DPA - 1988 VPAT/Section 508 EU Data Protection Directive Privacy Act [Australia] Privacy Act [New Zealand] PDPA - 2010 [Malaysia] PDPA -2012 [Singapore] PIPEDA [Canada] Spanish DPA Authorization CIS CJIS CSA ENS [Spain] EU-US Privacy Shield FFIEC FISC FISMA G-Cloud [UK] GxP [FDR 21 Part 11) ICREA IT-Grundschutz [Germany] MITA 3.0 MPAA NIST PHR Uptime Institute Tiers UK Cloud Security PrinciplesFor more information on risk andcompliance activities in the AWS cloud,consult the Amazon Web Services Riskand Compliance whitepaper which canbe found at: S Riskand Compliance Whitepaper.pdf10 of 17 Technical infrastructure and securitypanopto.com
Network securityPort scanningThe AWS network provides significant protectionagainst traditional network security issues, andPanopto’s Cloud Operations Team has implementedadditional measures for further protection.The following are a few examples:Unauthorized port scans by Amazon EC2 customersare a violation of the AWS Acceptable Use Policy.Violations of the AWS Acceptable Use Policy aretaken seriously, and every reported violationis investigated.Distributed Denial of Service(DDoS) attacksEncryptionAWS Application Programming Interface (API)endpoints are hosted on large, Internet-scale,world-class infrastructure that benefits from thesame engineering expertise that has built Amazoninto the world’s largest online retailer. ProprietaryDDoS mitigation techniques are used. Additionally,AWS’s networks are multi-homed across a numberof providers to achieve Internet access diversity.Man In the Middle (MITM) attacksAll of the AWS APIs are available via SSL-protectedendpoints which provide server authentication.Amazon EC2 AMIs automatically generate new SSHhost certificates on first boot and logs them to theinstance’s console.All user data being uploaded to Panopto orviewed by end-users is protected in transit toand from the Panopto system through the use ofTLS v1.2 encryption. For the protection of data atrest, Panopto utilizes Server-Side Encryption withAmazon S3-Managed Keys (SSE-S3). Each object inPanopto’s S3 bucket is encrypted with a unique keyemploying strong multi-factor encryption.As an additional safeguard, it encrypts the key itselfwith a master key that it regularly rotates. AmazonS3 server-side encryption uses one of the strongestblock ciphers available, 256-bit Advanced EncryptionStandard (AES-256), to encrypt data.For more information about SSE-S3: rv-sideencryption.htmlIP spoofingAmazon EC2 instances cannot send spoofednetwork traffic. The AWS-controlled, host-basedfirewall infrastructure will not permit an instance tosend traffic with a source IP or MAC address otherthan its own.11 of 17 Technical infrastructure and securitypanopto.com
Environmental safeguardsPhysical accessAWS data centers are state of the art, utilizinginnovative architectural and engineeringapproaches. AWS has many years of experience indesigning, constructing, and operating large-scaledata centers. This experience has been appliedto the AWS platform and infrastructure. AWS datacenters are housed in nondescript facilities. Physicalaccess is strictly controlled both at the perimeterand at building ingress points by professionalsecurity staff utilizing video surveillance, intrusiondetection systems, and other electronic means.Authorized staff must pass two-factor authenticationa minimum of two times to access data center floors.All visitors and contractors are required to presentidentification and are signed in and continuallyescorted by authorized staff. AWS only provides datacenter access and information to employees andcontractors who have a legitimate business needfor such privileges. When an employee no longerhas a business need for these privileges, his or heraccess is immediately revoked, even if they continueto be an employee of Amazon or Amazon WebServices. All physical access to data centers by AWSemployees is logged and audited routinely.12 of 17 Technical infrastructure and securityFire detection and suppressionAutomatic fire detection and suppressionequipment has been installed to reduce risk.The fire detection system utilizes smoke detectionsensors in all data center environments, mechanicaland electrical infrastructure spaces, chiller roomsand generator equipment rooms. These areas areprotected by either wet-pipe, double-interlockedpre-action or gaseous sprinkler systems.panopto.com
PowerManagementThe data center electrical power systems aredesigned to be fully redundant and maintainablewithout impact to operations, 24 hours a day, andseven days a week. Uninterruptible Power Supply(UPS) units provide back-up power in the event of anelectrical failure for critical and essential loads in thefacility. Data centers use generators to provideback-up power for the entire facility.AWS monitors electrical, mechanical and life supportsystems and equipment so that any issues areimmediately identified. Preventative maintenanceis performed to maintain the continued operabilityof equipment.Climate and temperatureClimate control is required to maintain a constantoperating temperature for servers and otherhardware, which prevents overheating and reducesthe possibility of service outages. Data centers areconditioned to maintain atmospheric conditionsat optimal levels. Personnel and systems monitorand control temperature and humidity atappropriate levels.13 of 17 Technical infrastructure and securityStorage device decommissioningWhen a storage device has reached the endof its useful life, AWS procedures include adecommissioning process that is designedto prevent customer data from being exposedto unauthorized individuals. AWS usestechniques detailed NIST 800-88 (“Guidelinesfor Media Sanitization as part of thedecommissioning process“).panopto.com
ComponentsThe Panopto components listed in this documentalso have multiple levels of security. You can viewa whitepaper for each component at the linkslisted below.Panopto componentsMicrosoft Windows Server /windows-serverMicrosoft SQL Server 2019 SP1 server-2019HTTP Live Streaminghttps://developer.apple.com/streaming IIS security-between-iis-60-and-iis-7-and-above .Net 4.6.2 details.aspx?id 5334414 of 17 Technical infrastructure and securitypanopto.com
Panopto application securityAPI and integrationsOur API is publicly available and can be configuredfor use with other platforms. Panopto currentlyprovides integrations for various platforms.AuditingPanopto software tracks a variety of data such aswhich user creates or deletes a session.Client-side and Server-side validationThe user authenticates on the Panopto clientapplication. The client encrypts the passwordand sends it to the server. The server checks thepassword with the hashed password.Encryption of user informationPanopto uses SSL in the web interface to encrypt allsensitive user information. The Panopto server usespassword hash checking. Passwords are not storedas plaintext.Inbound data validationThe Panopto software checks and tests for valid dataas well as protects against SQL injection and othermalicious inputs. Validation of all data is handled onthe client-side where possible, but the server neverresponds with sensitive validation data.Passwords and authenticationPanopto secures the video repository perimeterwith support for multiple credential types, includingOAuth, SAML 2.0, Active Directory, and a number ofLMS ID providers.15 of 17 Technical infrastructure and securityPanopto’s single-sign on (SSO) implementationsupports rolling two-way synchronization ofcredentials, ensuring that user information is alwaysup to date.Additionally administrators have the ability to enforcestrong passwords, set password expiration, requiretwo-factor authentication via SSO and definesession timeout.Role based accessRoles are specifically assigned to each user account(Administrator, Videographer, Creator, and Viewer).Software developmentThe Panopto development team has a formal SDLCthat is followed for each release. Because Panopto isa private company, we are not able to disclose thedetails of our development lifecycle.Session time outThe web interface has a configurable session timeout in place. The time out is based on the expirationof the cookie. The cookie is valid for 2 weeks afterfirst log in.User access controlPanopto allows for content to have two accesslevels; “Public” and “Unlisted”. Public content can beaccessed by anyone that has the URL or the ability tobrowse to the session. Unlisted content requires theuser to specifically be given access to the content.All unlisted content requires the user to be logged into view the content.panopto.com
Availability andmaintenancePanopto SLAFor purchasers of our hosted solution, Panoptowill continue, for the Term of the Agreement, tooffer hosting services to the Licensee. Panoptowill use reasonable efforts to make the hostingservices available 7 days a week, 24 hours a day.Panopto shall make the hosting services available,as measured in accordance with the formula belowover the course of any one-month period, anaverage of 99.9% of the time. “Available” means thatthe end user or intersystem action requests receivea response within thirty (30) seconds. “Unavailable”means that the hosting services are not available.“Hosting Availability” is expressed generally as apercentage of the requested hours during which thehosting services are available for use by Licensee.Amazon SLAPlanned Uptime is the total number ofhours (TH) in each calendar month. HostingAvailability is calculated as follows and ismeasured on a calendar month basisHA 100 x (1 - (DH – SDH)THHAHosting AvailabilityDHTotal of all downtimes measuredin hoursSDHTotal of all agreed and scheduleddowntimes, not to exceed three (3) hoursin any month, measured in hoursTHTotal hours in each calendar monthAmazon Web Services will use commerciallyreasonable efforts to make Amazon EC2 availablewith an Annual Uptime Percentage (definedin Appendix A) of at least 99.95% during theServiceYear.16 of 17 Technical infrastructure and securitypanopto.com
Upgrades and maintenanceThe Panopto Cloud servers are upgraded to thelatest version of the Panopto software when it isreleased. Typically there are two major upgradesper year. All expected downtime will be plannedfor non-core hours, on a weekend, varying by cloudlocation. Typical downtime windows start after6pm local time and end before 8am local time, forprimary locations served by the cloud.During the time your site is offline, you will notbe able to access recordings on your server, andany attempts to upload from clients will result ina “Server unable to connect” message. Scheduledrecordings will capture offline and upload after thesite is back online.Recorder clients are able to select the record offlineoption and upload after the site is back online.The duration of the downtime window can varyfrom release to release, but it typically ranges fromtwo to four hours.Customers are notified via email three weeks inadvance of any planned downtime. Reminders willbe sent via alert messages and will also beposted to trust.panopto.com.Staging sites will be available prior to anymajor release.Support will be available on live chat duringupgrades and will be monitoring the ticket queuefor widespread problems related to the upgrade(Authorized Point of Contacts only).Support will not monitor live chat during plannedmaintenance or hotfixes.17 of 17 Technical infrastructure and securitypanopto.com
Appendix ADefinitionsAnnual uptime percentage is calculated bysubtracting from 100% the percentage of 5 minuteperiods during the Service Year in which AmazonEC2 was in the state of region unavailable.AWS means Amazon Web Services.Cloud solution means the licensed products,subject to the purchase of usage bundles describedbelow, that are made available to the licensee bymeans of the internet or other electronic means,which are installed and maintained by Panoptoon Panopto controlled servers and that Panoptoprovides access to and support for the licensedproducts for authorized uses as further describedin the Panopto Software License and ServicesAgreement. Access shall be accomplished througha password protected site. Panopto shall create andmaintain, on its server, a management page foreach licensee, which page shall show then-currentusage statistics for such licensee. Components ofthe hosted solution may be delivered to the hostedsolution for installation on the licensee’s equipmentfor use with the hosted solution.Panopto means Panopto,Inc.,a Delawarecorporation,including its successors and assigns.18 of 17 Technical infrastructure and securityPanopto recorder software/Panopto clientmeans all of the software owned by Panopto andlicensed to the licensee hereunder that is installedon computers located at the primary location forpurposes of enabling the production of content.Panopto software means the Panopto recordersoftware and the Panopto server software.Update means either (i) a modification or additionthat, when made or added to the licensed products,establishes material conformity of the licensedproducts to the functional specifications, or (ii)a procedure or routine that, when observed inthe regular operation of the licensed products,eliminates the practical adverse effect on thelicensee of such nonconformity. Updates aredesignated by a change in the number to the rightof the second decimal point (V.X.1).Upgrade means any modification or addition thatmaterially changes the software’s utility, efficiency,functional capability, or application but is notseparately priced and marketed by Panopto anddoes not constitute an Update. Panopto maydesignate upgrades as minor or major, dependingon Panopto’s assessment of their value and of thefunction added to the preexisting licensed products.Such determination shall be at the sole discretionof Panopto. Upgrades are designated by a changein the number to the right of the first decimal point(V.1.Y) language.panopto.com
3 of 17 Technical infrastructure and security panopto.com Introduction Panopto's online video platform can be deployed either as a cloud-hosted service or as an on-premises solution. With the cloud-hosted service, Panopto maintains server infrastructure and ensures its continuous, optimal delivery.