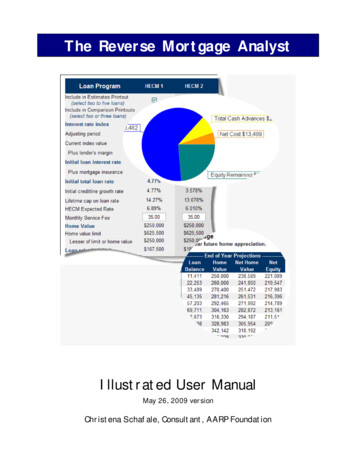
Transcription
Introduction toReverse EngineeringInbar RazMalware Research Lab ManagerDecember 2011 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.
What is Reverse Engineering?Reverse engineering is the process ofdiscovering the technological principles of adevice, object, or system through analysis ofits structure, function, and operation.aka: Reversing, RE, SRE 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.22
Why do Research(Yeah, right )Circumvent[Copy]ProtectionPatch BinaryandAlter BehaviorAnalyseProtocolsPureCuriosity 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.33
Soundsawesome,right? 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.44
So where’s the catch? Low-level is, well, low level 00401000 pushebp00401001 movebp, esp00401003 pushecx00401004 pushecx00401005 anddword ptr [ebp-4], 000401009 pushesi0040100A movesi, [ebp 8]for (Serial 0, i 0; i strlen(UserName);0040100D i )push { ediCurChar (int) UserName[i];0040100E pushesiSerial CurChar;0040100F callds:[00402008h]Serial (((Serial 1) && 0xFFFFFFFE)((Serialedi, 31)00401015 moveax && 1));Serial (((Serial * CurChar) CurChar) CurChar);00401017 xoredx, edx}00401019 testedi, ediUserSerial ((UserSerial 0x1337C0DE)0xBADC0DE5);0040101B jle00401047h0040101D movsxecx, byte ptr [edx esi]00401021 add[ebp-4], ecx00401024 mov[ebp-8], ecx00401027 roldword ptr [ebp-4], 10040102A moveax, ecx0040102C imuleax, [ebp-4]00401030 mov[ebp-4], eax00401033 moveax, [ebp-8]00401036 add[ebp-4], eax00401039 xor[ebp-4], ecx0040103C incedx0040103D cmpedx, edijl Ltd. [PROTECTED]0040101Dh 2011 Check Point0040103FSoftware Technologies— All rights reserved.55
So where’s the catch? Low-level is, well, low level Needle in a haystack– Average opcode size:3 bytes– Average executable size:500KB (on WinXP)– There are executables,libraries, drivers . 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.66
So where’s the catch? Low-level is, well, low level Needle in a haystack Sometimes, the code resists– Packers and compressors– Obfuscators 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.77
So where’s the catch? Low-level is, well, low level Needle in a haystack Sometimes, the code resists Sometimes, the code fights back– Detect reversing tools– Detect VMs and emulators 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.88
A Battle of Wits Video clip: The Battle of Wits, “The Princess Bride” 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.99
A Battle of Wits Author writes code Reverser reverses it Author creates an anti-reversing technique Reverser bypasses it And so on 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1010
So what do you needin order to bea good reverser? 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1111
We’ll come backto this 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1212
Tools of the Trade Debugger (Dynamic code analysis) Disassembler (Static code analysis) Hex Editor PE Analyzer Resource Editorand more 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1313
Debuggers באג בדיזיין – זין בדיבאג 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1414
First, there was DEBUG 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1515
GUI and much more: Turbo Debugger 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1616
GUI and much more: Turbo Debugger 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1717
GUI and much more: Turbo Debugger 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1818
Next major step: Soft-ICE 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.1919
And finally: OllyDbg 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2020
Disassemblers 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2121
The old world: Sourcer 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2222
The old world: Sourcer 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2323
Old ages: Sourcer 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2424
Old ages: Sourcer 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2525
Welcome to Windows: W32DASM 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2626
The Holy Grail: IDA-Pro Started as an Interactive Dis-Assembler, enabling userinteraction with the disassembler’s decisions. Slowly evolved into an automatic RE tool:– Built-in full-control script language– Library recognition (including user-generated)– Function prototype information– Display– Propagate throughout the code– Support for plug-ins– Support for Python scripting– Multi-architecture, cross-platform support– Full incorporation with built-in and external debuggers 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2727
Hex-Editor 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2828
PE Analyzer 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.2929
Resource Editor 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3030
Let’s playwith them tools 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3131
60 seconds on x86 registers General purpose registers:32bit/16bit/8bit Index registers:32bit/16bit Segment registers:16bit Flags:32bit/16bit 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3232
Exercise 1:Static Reversing 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3333
Exercise 1: Static Reversing Target: a 2004 “Crack-Me” Tools: IDA-Pro 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3434
Exercise 2:Dynamic Reversing 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3535
Exercise 2: Dynamic Reversing Target: a 2004 “Crack-Me” Tools: OllyDbg, IDA-Pro 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3636
Exercise 3:Simple Anti-Debugging 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3737
Exercise 3: Simple Anti Debugging Target: a 2006 “Crack-Me” Tools: OllyDbg 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3838
Reversing Malware Malware is comprised of the following building blocks:– Infection Vector– Concealment– Operation– Communications Check Point’s Anti-Malware Software Bladesits at the gateway Therefore, communications interest us the most 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.3939
Introducing: Spy Eye A CrimeWare ToolKit, originating in Russia. Used mostly for stealing financial information, but will settlefor any other identity information and key logging Like any serious trojan, Spy Eye compresses its traffic andencrypts it– Compression is performed using a public library (LZO)– Encryption algorithm is proprietary 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4040
Act 1:Encryption 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4141
Act 2:Configuration Download 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4242
Act 3:Another Encryption 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4343
So what do you needin order to bea good reverser? 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4444
What makes a good reverser?QualitiesKnowledge Patient Assembly Language Curious Some High-Level programming Best: origin of binary Persistent Outside-the-Box Thinking Operating System Internals API Data Structures File Structures Good scripting skills Anti-Debugging Tricks Optional: Good lookin’ 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4545
Outside-the-Box Thinking 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4646
And remember, kids:BinaryReverse Engineer 2011 Check Point Software Technologies Ltd. ?[PROTECTED] — All rights reserved.4747
Which means 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4848
Questions? 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.4949
Thank you!inbarr@checkpoint.com 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.5050
CreditsAll images and videos have their origin URL in the “Alt Text” property.All rights belong to their respective owner. 2011 Check Point Software Technologies Ltd.[PROTECTED] — All rights reserved.5151
The Holy Grail: IDA-Pro Started as an Interactive Dis-Assembler, enabling user interaction with the disassembler’s decisions. Slowly evolved into an automatic RE tool: – Built-in full-control script language – Library recognition (including user-generated) – Function prototype information – Display – Propagate throughout the code