Transcription
MuseKnowledge Proxyand SAML AuthenticationMuseGlobal, Inc.One EmbarcaderoSuite 500San Francisco, CA 94111415 896-6873www.museglobal.comMuseGlobal S.ACalea BucurestiBl. 27B, Sc. 1, Ap. 10Craiova, România40 251-413496www.museglobal.roEduLib, S.R.L.Calea BucurestiBl. 27B, Sc. 1, Ap. 2Craiova, România40 351-420970www.edulib.comVersion: 1.0Date: 4th August 2016Author: EduLib, S.R.L.
MuseKnowledge ProxyHighly customizable multi-platform proxy server Easy to use and configure via the MuseKnowledge Proxy Administrator Console; Gateway to authenticated restricted content; Rewriting web server; Web Access Management (WAM); Proxy server and reverse proxy; Supports SAML 2.0 as a Service Provider (SP).More than 10 years within the Muse Federated Search Platform tomanage the authentication to resources and the navigation to full textPAGE 2COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
What is SAML? Security Assertion Markup Language; XML-based, open-standard data format for exchanging authentication andauthorization data between parties, in particular, between an Identity Provider(IDP) and a Service Provider (SP); Single Sign-On; OASIS approved standard; Flexible and extensible protocol designed for integrations;IDPAsserting PartyTrust relationshipAuthenticateSPRelying PartyAccess ServicesUserPAGE 3COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
SP Initiated Single Sign-On End-user accesses directly a resource on the SP;User1. Request resource5. Redirect to theresource3. AuthenticateIDPSPPAGE 4COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
IDP Initiated Single Sign-On End-user accesses directly the IDP for SSO; Not anymore common and not the direction recommended; MuseKnowledge Proxy responds to IDP Initiated SSO (Unsolicited SSO) as long as the IDP allowsfor passing a RelayState, because the assertion point is different than the entrypoint in a MuseKnowledge Proxy application, or than a direct source link.User1. Request for SSO2. Authenticate4. Redirect to theresourceIDPSPPAGE 5COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Features Theoretically all products supporting SAML 2.0 in Identity Provider mode shouldbe compatible with Muse Proxy; Includes a local Discovery service; Supports external Discovery; Supports specifying the IDP metadata either by uploading the IDP metadata fileor by specifying the IDP metadata URL with a local file backup with periodicallyrefreshes; Supports specifying IDP metadata as a file/URL containing one EntityDescriptoror as multiple EntityDescriptor wrapped in EntitiesDescriptor (e.g. a federation)with filters eliminating conflicts if the SP metadata is also present in the samefile; Easy restart of only the Servlet Engine, not affecting MuseKnowledge Proxyend-users already authenticated; Post-SAML authentication decisions via server side JavaScript on letting the userin the application, choosing a source group, choosing an attribute to be loggedinto the statistics;MorePAGE 6COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Features Mapping SAML attributes which are then available to be used in the Muse ProxyHTML interface level.; Metadata management supporting adding IDP metadata and generation of SPmetadata, pre-validation of IDP metadata to detect the need of certificates, testsfor authentication, seeing SAML attributes, guidelines and more; The SAML authentication works combined with proxified widgets (forms), ?url like links; Other authentications, especially IP authentication (as a sufficientauthentication) can be combined with SAML authentication.PAGE 7COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
MuseKnowledge Proxy SAMLAuthentication ScenarioSteps taken by MuseKnowledge ProxyAccess MuseKnowledge Proxy Application pageSession exists?Steps taken by IDPYesDisplayMuseKnowledge ProxyApplication pageAccess DeniedNoNoSelect AuthenticationMethod (LocalAuthentication, IDP)Create MuseKnowledge Proxy SessionSelect LocalAuthenticationRedirect to IDP(DelegateAuthentication)YesYesCredentials are Valid?Request User CredentialsNoDiscovery(Select IDP)IDP SessionExists?NoRequest User IDPCredentialsPAGE 8YesPOST User Attributes toMuseKnowledge ProxyYesCredentials are Valid?NoAccess DeniedCOMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
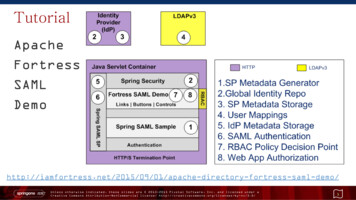
SAML Implementation inMuseKnowledge Proxy Based on Spring Security SAML Extension and running inside Jetty ServletsContainer which is integrated within MuseKnowledge Proxy; Supports ADFS, Okta, Shibboleth, OpenAM, Efecte EIM or Ping Federate; Indirect Authentication type as the authentication process happens on theIdentity Provider (IDP) side; Because of this, the configuration is more complexthan other login modules such as LDAP, IMAP, etc.; Multiple Service Provider for multiple customer applications (multi-tenancy); MuseKnowledge Proxy acts as a Reverse Proxy for certain paths and passes therequest transparently to Spring Security SAML Extension inside Jetty; the URLswill contain /alias/AppIP, for /alias/MuseProxyFoundation Jetty is embedded inside MuseKnowledge Proxy and controlledprogrammatically, hence only a single piece of software for handling SAML; All the communication MuseKnowledge Proxy -- Jetty being done internally,only on localhost; from outside the host:port being the same either for a SAMLAuth requests or for a usual proxy request.PAGE 9COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
MuseKnowledge Proxy SAML WorkflowRequestNoIs it a normalrequest? (e.g. forapplication listing,source entry point,etc)YesMuseKnowledge Proxy session existsand associated tothe application?YesServe the requestNoIdentify the logonconfiguration to useNoIs it an internalrecursive AMLanalyzes SAMLProperties, andtake post-SAML decisionsIs it SAML?NoYesIssue a redirect to/ssoRWP/SAMLAuth/alias/AppName containing aspecial parameter where initial request is codedas a Tiny URL.Present error screen sayingthat SAML succeeded butfinal decisions are not infavor.Other login module. Notsubject to this scheme.NoIs decisionOK?YesCreate new MP session and/or associateexistent session with the currentapplication process the real requestMorePAGE 10COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
MuseKnowledge Proxy SAML WorkflowRelay request-responses tolocalhost:8787 where Jetty withSpring Security SAML Extensionis running (/SAML)Is it a request forreverse SSO proxy(e.g./ssoRWP/SAMLAuth/alias/AppName)Spring SecuritySSO Session isalready presentand authenticated?NoYesNoYesRequest is for theAssertionConsumerService end point (e.g./ssoRWP/saml/SSO/alias/MuseProxyFoundation) withSAMLResponse in it?NoPAGE 11Request containsspecial rwp Tiny URLparameter andresponse containsproperties file withspecial markings incomments?YesAuthenticated by Spring SAMLSecurity Extension.Decode the initial proxy requestfrom the Tiny URL, add SAMLProperties into the MP request andmake an internal recursive requestto MP and then send this newresponse instead of the rawproperties to the browser.Return directly theresponse withproperties file withattribute.YesDecode SAML response whichwas coming from IDP.Create new SSO Session (JSESSIONID)which is not authenticated and presentresponse with SAMLRequest form onloadpage submission to IDP sending theJSESSIONID cookie. If discover is presentmore steps will take place [not shown here].Browser will perfom post with SAMLRequestagainst the IDP where the authenticationtakes place.All SAMLvalidation/signature is fine?YesMake the SSO Sessionauthenticated and from theassertion extract the attributes andthen redirect to the initial requestCOMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
SAML Configuration Requirements andCheck ListRequirements: Make sure all server names are configured into SERVER NAMES, including theload balanced name if applicable; MuseKnowledge Proxy administrator necessary skills: SAML, XML, SSLcertificates.Check List: Activate the internal Servlet Engine where SAML SP component is running (onetime action); Identify the IDP(s) to use and configure references to its/theirs metadata; Generate and store the Service Provider metadata for the desiredMuseKnowledge Proxy application; Publish the freshly SP generated metadata on the IDP(s) and if it is the case onthe Discovery / Federation Services; MuseKnowledge Proxy application wiring and authentication decisions (e.g.sources group based on SAML attributes).PAGE 12COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
SAML Configuration Files and Locations Files and locations that have to do with SAML authentication: {MUSE adata/is the storage for all the defined SP Metadata files as well as for the IDP ones ifthey are first downloaded and not referred through remote URLs. {MUSE textmetadata.xmlIs an index for the IDP and all the alias SP metadata as well as an index for thesigning and encryption keys used in the process. {MUSE urity/samlKeystore.jksIs the storage for the certificates and private keys (according to Javaterminology they are keypairs) used during SAML flows for signature andencryption. {MUSE HOME}/proxy/webcontexts/Applications/ {APP ID}/profiles/AuthenticationGroups.xmlMuseKnowledge Proxy Application authentication file. {MUSE HOME}/proxy/webcontexts/Applications/ {APP wledge Proxy SAML login module authentication file.PAGE 13COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Activate the Internal Servlet Engine Edit the file: {MUSE HOME}/proxy/MuseProxy.xmland set to true the value in the SERVLET ENGINE ENABLED node; Restart the MuseKnowledge Proxy service; Jetty Servlet Engine configuration file: {MUSE HOME}/proxy/ServletEngine.xml Accessible only on localhost; Restart feature from the MuseKnowledge Proxy Administrator Console,Configuration – SAML Authentication left menu, Restart SSO button:PAGE 14COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Generate new Service Provider Metadata MuseKnowledge Proxy Administrator Console, Configuration - SAMLAuthentication, Metadata Administration button, Generate new service providermetadata button; Mandatory to configure SERVER NAMES option in the {MUSE HOME}/proxy/MuseProxy.xml file to reflect all the fully qualifieddomain name used to access MuseKnowledge Proxy.MorePAGE 15COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Generate new Service Provider MetadataClick on Create File button to save the metadata under folder: {MUSE adata Update the identity provider(s) with the generated metadata; Modify bean "metadata" in {MUSE textmetadata.xmland include the generated content from the Configuration section under the list element. Restart the Servlet Engine from the MuseKnowledge Proxy Administrationconsole, Configuration - SAML Authentication, Restart SSO button; In case a single IDP is used for authentication for the application add its entityID in {MUSE in the element IDP ENTITY ID. Otherwise a discovery is firstly performed;Configure the module ProxyLoginModuleSAML in {MUSE dationSAML/profiles/AuthenticationGroups.xml so that it is used in the authentication flow for the desired authentication group.MorePAGE 16COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Generate new Service Provider Metadata PAGE 17Metadata generation and detailed configuration steps:COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Generate new Identity Provider Metadata MuseKnowledge Proxy Administrator Console, Configuration - SAMLAuthentication, Metadata Administration button, Add new identity providermetadata button; 2 methods available: By URL. Provide the URL pointing to the IDP metadata (it can be afederation URL, too); By Upload.Modify bean "metadata" in {MUSE textmetadata.xmland add the generated content under the list element. Restart the Servlet Engine from the MuseKnowledge Proxy Administrationconsole, Configuration - SAML Authentication, Restart SSO button;MorePAGE 18COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Generate new Identity Provider Metadata PAGE 19Add IDP Metadata and complete steps.COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
Configuration Helpers Various helper tools are available to easily spot the errors: XML file viewinside thebrowser todetect notwellformed XMLfiles; See full stacktrace of errors.PAGE 20COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
ProxyLoginModuleSAML.xml ConfigurationFile and Final Authentication Decisions Make sure that the ProxyLoginModuleSAML.xml file is linked to from theAuthenticationGroups.xml file; Use the IDP ENTITY ID element and fill it with an entity ID to avoid discoveryscreens; INPUT XML element: defines input parameters to be used as global JavaScript variables in theSCRIPT section by mapping between a variable id and the friendly namefrom Principal's SAML Attributes; saml2:Attribute FriendlyName "eduPersonPrincipalName"Name "urn:oid:1.3.6.1.4.1.5923.1.1.1.6"NameFormat "urn:oasis:names:tc:SAML:2.0:attrname-format:uri" saml2:AttributeValue gabi@sharepoint.museglobal.com /saml2:AttributeValue /saml2:Attribute saml2:Attribute FriendlyName "displayName" Name "urn:oid:2.16.840.1.113730.3.1.241"NameFormat "urn:oasis:names:tc:SAML:2.0:attrname-format:uri" saml2:AttributeValue Gabriel Toma-Tumbar /saml2:AttributeValue More /saml2:Attribute PAGE 21COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
ProxyLoginModuleSAML.xml ConfigurationFile and Final Authentication Decisions OUTPUT XML element: defines the output parameters usable in the Freemarker templates in theMuse Proxy Application interface; contains PARAM elements with id and source attribute; the id represents the name of the property to be further used in the MuseProxy application interface;MorePAGE 22COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
ProxyLoginModuleSAML.xml ConfigurationFile and Final Authentication Decisions SCRIPT XML element (optional): contains under a CDATA construction the JavaScript code; the variables defined in the INPUT section can be used for comparisons forfinal decision on the authentication; the following global variables have to be used: succeeded variable say if authentication pass or not; logUserID variable which caries the value of the user identifier to belogged; sourcesGroupID selects the source group to be used. If missing orempty, the default group is implied; errorMessage variable that store the error message sent back to loginmodule.MorePAGE 23COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
ProxyLoginModuleSAML.xml ConfigurationFile and Final Authentication DecisionsPAGE 24COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
References Muse Proxy.pdf; Muse Proxy Advanced Configuration.pdf; Muse Proxy Administrator Console.pdf;PAGE 25COMPANY CONFIDENTIAL 2016 MUSEGLOBAL, INC. ALL RIGHTS RESERVED
MuseKnowledge Proxyand SAML Authentication
Authenticated by Spring SAML Security Extension. Decode the initial proxy request from the Tiny URL, add SAML Properties into the MP request and make an internal recursive request to MP and then send this new response instead of the raw properties to the browser. Yes R