Transcription
Ephesoft Transact 4.5.0.x — Manual SSO Configuration GuideEphesoft TransactManual SAML 2.0 SSO Configuration GuideVersion 4.5.0.x and 2019.1April 2, 2019Revision 1.1bCopyright 2019 by Ephesoft, Inc.All rights reserved1
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideRevision HistoryDateVersionRev.DescriptionSeptember 18,20184.5.0.x1.0Initial publication of the document, for manually configuring SSO with ADFSand SAML 2.0 (not automated configuration).This document is also available in the Ephesoft Wiki at the following URL: mber 1, 20184.5.0.x1.1Added Transport Layer Security (TLS) support information: 1.3. SSO Support Information for Ephesoft TransactAdded a new issue resolution to the “Troubleshooting” chapter: 5. No redirection to the SSO Login screen upon login to TransactApril 2, 20194.5.0.x2019.11.1bUpdated hypertext links to support Ephesoft.com/Docs.ContentsRevision History .21. Introduction .41.1. SSO Overview .41.2. Benefits .41.3. SSO Support Information for Ephesoft Transact .41.4. SSO Configuration Overview on Ephesoft Transact .52. Prerequisites .62.1. Prerequisite Components .63. Obtaining and Installing OpenSSL — Required .64. Configuring SSL/TLS — Required .74.1. Introduction .74.2. SSL/TLS Setup: Server Certificates .74.2.1. Production Environment: CA Certificates .74.2.2. Testing Environment: Self-Signed Certificates .75. Configuring SSL/TLS for Ephesoft Transact — as Needed .135.1. Introduction .135.2. SSL/TLS Setup: Configuring the Ephesoft Transact JavaAppServer (Tomcat) .135.3. SSL/TLS Setup: Configuring Ephesoft Transact Files.145.3.1. dcma-batch.properties .155.3.2. dcma-workflows.properties .155.3.3. web.xml .156. Configuring Ephesoft Transact for SAML SSO .166.1. Introduction to SAML .162 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide6.2. SAML v2 Support in Ephesoft Transact.167. Configurations for Integrating SAML-Enabled Spring Security Framework .177.1. Introduction .177.2. applicationContext.xml .177.3. web.xml .177.3.1. Multiple Group Support in web.xml .197.4. samlKeystore.jks .197.4.1. Create a private key .197.5. applicationContext-security.xml .207.6. Testing at the SSOCircle .247.7. Configuring Ephesoft Transact and ADFS .247.7.1. Configuring Ephesoft Transact for the ADFS Server .24Obtain the ADFS Metadata .25Import the ADFS Certificates to Ephesoft Transact .257.7.2. Configuring the ADFS Server for Ephesoft Transact .257.7.3. Exporting the Certificate from the ADFS Server .297.7.4. Successful Configuration .317.8. Configuring Okta with Ephesoft Transact .317.8.1. Introduction .317.8.2. Creating the Okta Developer Account .317.8.3. Assigning People in the Okta Account to Ephesoft Transact .387.8.4. Adding People to the Okta Account .397.8.5. Configuring Ephesoft Transact to Operate with Okta .408. Exporting the Self-signed Certificate from Keystore .439. Troubleshooting SSO in Ephesoft Transact .439.1. Introduction .439.2. General Troubleshooting Tasks .439.3. Logging for SAML Requests .459.4. Getting the Fiddler Trace .453 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide1. Introduction1.1. SSO OverviewSingle sign-on (SSO) is a mechanism of access control that can be applied on multiple related, butindependent software systems. With this mechanism a user logs in once and gains access to multiplesystems without being prompted to log in again for each individual application. Conversely, single sign-offis property mechanism whereby a single action of signing out terminates access to multiple softwaresystems.As different applications and resources support different authentication mechanisms, single sign-oninternally translates to and stores different credentials, compared to what is used for initial authentication.1.2. BenefitsSSO has several general benefits, to include the following: Reducing password fatigue from different user name and password combinationsReducing time spent re-entering passwords for the same identityReduced logins for discreet systemso Corporate systemso Shared intranet/web applicationso Web logon aggregators Reduced cost to reset a passwordReduced time spent logging into multiple systems each timeReduces multiple authentication, unnecessary user clicks, forgotten passwords, multiple profilesLimited time and resources to develop IT solutions1.3. SSO Support Information for Ephesoft TransactThis document describes how to make manual SAML 2.0 SSO configurations during a new installation ofEphesoft Transact 4.5.0.x or 2019.1.Note:Automated SSO configuration for Ephesoft Transact does not have scheduled availability.Ephesoft Transact has been tested with the following SSO-related components: SAML 2.0 — An XML-based protocol that entails security tokens for authentication and authorization.Ephesoft Transact supports SAML 2.0, and has tested and certified the following identity providers thatare compatible with Ephesoft Transact:oooo ADFSOktaPingFederateSSOCircleTransport Layer Security (TLS) — Ephesoft Transact 4.5.0.x and 2019.1 support TLS versions 1.0,1.1 and 1.2.There are multiple additional identity providers in the market that support SAML 2.0. Ephesoft has nottested every available identity provider or security product.4 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide1.4. SSO Configuration Overview on Ephesoft TransactThis document describes how to make manual SAML 2.0 SSO configurations during a new installationof Ephesoft Transact 4.5.0.x or 2019.1.Note:This document emphasizes tasks for operational deployment. At some time in thefuture, Ephesoft may provide a separate document that describes security and SSOconcepts.This document contains the following sections and purposes:Section TitlePurpose and Description2. PrerequisitesRequired — This section identifies the prerequisite conditions that must be in place inorder to configure SSO for use with Ephesoft Transact.3. Obtaining andInstalling OpenSSLRequired — This section describes the steps for downloading and installing OpenSSL.You must complete these steps prior to performing the additional SSO configurations inthis document.4. ConfiguringSSL/TLSRequired — This section describes the steps for configuring multiple components of theSecure Sockets Layer (SSL) protocol or the Transport Layer Security (TLS) protocol. Oneor more of these components may need to be configured, depending on your currentrequirements and status.Not all identity providers (IdP) will require SSL/TLS configuration, but this section providesinstructions for those IdPs that do require it.5. ConfiguringEphesoft Transactfor SSL/TLSRequired — This section describes how to configure Ephesoft Transact over SSL/TLS.5.1. Introduction5.2. SSL/TLS Setup: Configuring the Ephesoft Transact JavaAppServer (Tomcat)5.3. SSL/TLS Setup: Configuring Ephesoft Transact Files6. ConfiguringEphesoft Transactfor SAML SSORequired — This section describes the steps for configuring SAML SSO within EphesoftTransact.7. Configurations forIntegrating SAMLEnabled SpringSecurity FrameworkRequired — This section describes the steps for configuring the various components ofthe SAML-enabled Spring Security framework. There are several elements to configure inthis phase of SSO setup.7.1. Introduction7.2. applicationContext.xml7.3. web.xml7.4. samlKeystore.jks7.5. applicationContext-security.xml7.6. session-timeout.js7.7. Testing at the SSO Circle7.8. Configuring Ephesoft Transact and ADFS7.9. Configuring Okta with Ephesoft Transact8. Exporting theSelf-signedCertificate fromKeystoreAs Needed — This short section describes how to export the self-signed certificates, if youneed these for the additional configurations in this document.9. TroubleshootingSSO in EphesoftTransactAs Needed — This section provides a reference monitoring and troubleshooting SSOconfiguration issues in Ephesoft Transact.9.1. Introduction9.2. General Troubleshooting Tasks9.3. Logging for SAML Requests9.4. Obtaining the Fiddler Trace5 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide2. Prerequisites2.1. Prerequisite ComponentsThe following items are required to set up SAML SSO authentication with Ephesoft Transact.1. CA Certificate — If you have access to a trusted Certificate Authority (CA), you should complete theCA process to get a CA certificate, server certificate and server private key.If you do not have a trusted Certificate Authority (CA), you can create dummy CA certificates to testthe setup in a lab or test environment.In an ideal scenario, you should have a trusted Certificate Authority (CA).2. Identity Provider — You must have an installed identity provider (IdP) server that supports SAML 2.0.Ephesoft has tested and certified Ephesoft Transact with the following four identity providers:ooooActive Directory Federation Services (ADFS)OktaPingFederateSSOCircle3. Active Directory — This document does not provide step-by-step instructions for installing orconfiguring Active Directory. If you need to set up Active Directory in preparation for configuring SSO,refer to one or more of the following articles:o How to: Configure Active y/oKB0007802 Active Directory Configuration/Setup: Sample File Changes for Proper proper-setup/oMultiple Groups as Roles in Active -active-directoryoHow to Administer Ephesoft Users & ephesoft-users-groups3. Obtaining and Installing OpenSSL — RequiredOpenSSL is a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS)and Secure Sockets Layer (SSL) protocols. Use OpenSSL in the case that a trusted Certificate Authority(CA) certificate is not available.You can download OpenSSL on Windows from the following 1 0 2g.exeYou need to install PERL on the system before using OpenSSL. Refer to the PERLwebsite.6 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide4. Configuring SSL/TLS — Required4.1. IntroductionThis chapter provides detailed steps for setting up certificates for the Secure Sockets Layer (SSL) orTransport Layer Security (TLS).This chapter contains the following topics for configuring SSL certificates: 4.2. SSL/TLS Setup: Server Certificatesoo4.2.1. Production Environment: CA Certificates4.2.2. Testing Environment: Self-Signed CertificatesIf you already have CA certificates, and the keystore is ready for SSL setup on the server, navigate to thechapter titled 5. Configuring SSL/TLS for Ephesoft Transact — As Needed.If the server is already set up for certificates, keystore and SSL, navigate to the chapter titled ConfiguringEphesoft Transact for SAML SSO.4.2. SSL/TLS Setup: Server CertificatesTo set up SSL/TLS protocols, you need to use either certificates issued by CA or self-signed certificates,which can be used in TEST environment as mentioned above.4.2.1. Production Environment: CA CertificatesIn a production environment, you must make use of certificates issued by a trusted CA.4.2.2. Testing Environment: Self-Signed CertificatesFor a lab or test environment, you can generate your own dummy self-signed certificates for testing theEphesoft SSO integration. This can be done using OpenSSL tool, as described below.OpenSSL is an open source general purpose cryptography library, which is used for implementation ofSSL and TLS.Perform the following steps to create self-signed certificates using OpenSSL:In the case that cacert.pem, servercert.pem and serverkey.pem files are alreadyavailable, then you can directly proceed to Step 7 below.1. Locate the OpenSSL CA.pl file, as this file is required to create the dummy CA certificate file.2. Create a directory to store certificates:mkdir certificates3. In Linux, execute the following command:/usr/lib/ssl/misc/CA.pl -newcaOR,In Windows, execute the above command, replacing the path of CA.pl with the Windows path.This creates demoCA/cacert.pem (CA Certificate) and demoCA/private/cakey.pem (private key).7 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideThe generated cacert.pem is located inside the demoCA folder.Viewing the cacert.pem (CA Certificate) [migrated]4. Make a server certificate signing request (CSR) using the following command:openssl req -newkey rsa:1024 -nodes -keyout newreq.pem -out newreq.pem8 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideUsing the openssl reg Command [migrated]Note:Make sure to use the same name/value in Common Name as that of theservername/hostname. Otherwise, when trying to access the server, the browsermight warn the user that the name does not match the hostname. Also, make sureto access the server with same hostname as mentioned here.5. Create Server Certificate — that is, sign the certificate CSR (certificate signing request) with CA usingthe following command:/usr/lib/ssl/misc/CA.pl -signReplace the path of the CA.pl file according to your operating system (Windows/Linux).9 Page
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideCreating the Server Certificate [migrated]The following files will be created after executing the previous steps. cacert.pem (CA certificate) created in Step 3newreq.pem (Server key) created in Step 4newcert.pem (Server certificate or certificate signed by CA) created in Step 5 above6. For improved clarity, rename these files: Rename newreq.pem to serverkey.pemRename newcert.pem to servercert.pemThe following PEM files will be available after renaming the original files: cacert.pemservercert.pemserverkey.pem7. Convert the servercert.pem file to PKC12 format (*.p12) using the following command:openssl pkcs12 -export -in servercert.pem -inkey serverkey.pem -outservercert.p12 -name servercertificate10 P a g e
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideThe converted file (servercert.p12) acts as a server certificate and is used to generatekeystore.When prompted for Export Password, enter a password and keep the password safe.Converting the servercert.pem File to PKC12 Format8. Create a java keystore file by converting the servercert.p12 file to Java Keytool format by using thefollowing command:keytool -importkeystore -destkeystore servercert.jks -srckeystoreservercert.p12 -srcstoretype PKCS12 -alias servercertificateWhen prompted for the destination keystore password, enter a password and keep itsafe. It will be used as keystore password in the server.xml file.Also, when prompted for source keystore password, enter the export password for inputservercert.p12 file created in the previous step (Step 7).Keytool Command9. Create a java truststore file by converting the cacert.pem file to Java Keytool format by using thefollowing command:keytool -import -keystore cacerts.jks -alias cacert -file cacert.pemWhen prompted for keystore password, enter a password and keep the password safe. Itwill be used as truststore password in server.xml.11 P a g e
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration GuideCreating a java truststore fileThese files will be used while configuring SSL/TLS on the Ephesoft Transact server.12 P a g e
Ephesoft Transact 4.5.0.x and 2019.1 — Manual SSO Configuration Guide5. Configuring SSL/TLS for Ephesoft Transact — as Needed5.1. IntroductionUse the steps in this section to configure SSL/TLS on Ephesoft, after you have generated the certificateswith the previous chapter.This chapter describes the following topics: 5.2. SSL/TLS Setup: Configuring the Ephesoft Transact JavaAppServer (Tomcat) 5.3. SSL/TLS Setup: Configuring Ephesoft Transact Filesooo5.3.1. dcma-batch.properties5.3.2. dcma-workflows.properties5.3.3. web.xmlIf you do not need to perform any of these SSL/TLS setup tasks, please proceed to the ne
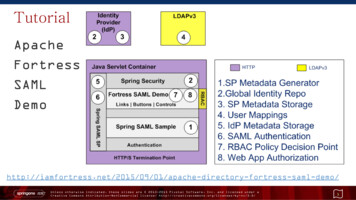
— An XML-based protocol that entails security tokens for authentication and authorization. Ephesoft Transact supports SAML 2.0, and has tested and certified the following ident