Transcription
B ot M a n ag e m e n t:An Overlooked Layer in Account Takeover Defense
BotMa na ge m e nt:An Overlooked Layer in Account Takeover DefensePG. 2There are faceless armies of robots arrayed against you. They are legion, they are tireless and, ifthey overwhelm your defenses, they can be lethal—to your business. Bots are not the minions ofan evil super-intelligence in a science fiction film bent on dominion over mankind. They are simplya tool that can be used by anyone who picks it up. But forgive fraud professionals for thinking thatway, because their daily battle to preserve revenue against constantly evolving and increasinglysophisticated attacks is being facilitated and exacerbated by bots in the hands of criminals.Merchants focused on fraud in their digital channels may not come into direct contact with botsand the ways they attack a company’s systems. But, for those who operate downstream from abusiness’s main security architecture, the effect of bots on the most pernicious types of fraud theyface is clear. And, employing technology to combat bots should be a vital part of any e-commercemerchant’s layered defense against fraud.What is a Bot?Bots are neither good nor bad, in and of themselves. They are simply pieces of software designedto complete repetitive tasks on an automated basis much faster than a human ever could. Whethera bot is beneficial or malicious depends entirely on its programming and the task toward which it isdirected by an operator. A search engine is an example of a bot that most would agree is beneficial,as is a chatbot that enables companies to automate online engagement between their customerservice departments and customers.One 2016 analysis by Cambridge, Mass.-based CDN provider Akamai Technologies estimated thatmore than 30 percent of all Internet traffic in that year was not human in origin—it was bots goingabout their automated business. And, that total, both good and bad, is growing each year.While they might not have direct contact with malicious bots, online fraud professionals deal withthe negative fallout from bad-bot attacks on a daily basis. The e-commerce, ticketing, airline andgambling industries deal with the highest percentage of bad bot traffic. For gambling sites, badbots account for more than 50 percent of their traffic. For e-commerce sites, some experts haveestimated it is nearly one quarter of their traffic. And those bots are one of the primary reasons forthe explosion of a particular type of fraud that has grown significantly in the past several years—account takeover fraud.How Bots Facilitate ATOIncidences of account takeover (ATO) fraud tripled from 2016 to 2017, costing businesses 5.1billion last year.1 And, bots are the engine driving that growth through a process called “credentialstuffing.”How bots and ATO fraud relate to each other is much easier to understand when you realizethat fraud has become an enormous industry. Like any industry, an ecosystem of producers andsuppliers has evolved enabling participants to specialize and find efficiencies to become moreprofitable.
BotMa na ge m e nt:An Overlooked Layer in Account Takeover DefensePG. 3The fraudster that uses a stolen username andpassword to illegally access and monetize an onlineaccount is simply the last person in a very long chain.The first person is the hacker who breachesthe system of an unlucky business and unearthshundreds of thousands, millions or even, in somecases, hundreds of millions of username/passwordcombinations. Depending on the amount ofinformation stolen in the breach, the hacker eitherputs the entire list up for sale on a dark web siteor breaks it into smaller chunks and does the samething.But the person who buys those lists generally isnot the person defrauding online businesses. Andthis is where bots enter the picture—far upstreamfrom the actual fraud. The recipient of the bulkdata wants to validate the username/passwordcombinations on as many sites as possible. Sothey load up specially programmed bots with thethousands or millions of credentials and aim them atsites around the internet.The bots then engage in credential stuffing—automatically testing those credentials to see whichaccounts they can successfully log into. The credential stuffer then sells the smaller list of validaccount credentials for much more than they paid for the original bulk list.Those valid account credentials are bought by individuals whose work has become all too familiarto e-commerce fraud departments at businesses of all kinds. With a valid login, a fraudster becomesextremely difficult to identify and can monetize their illegal access in a number of ways. Theycan purchase physical products with the account’s card on file and resell them, they can drain anaccount of any stored value (e.g., cash, store credit, gaming credits or loyalty points), etc.Companies are investing significantly in technology solutions that attempt to identify whichaccounts are legitimate and which have been accessed using stolen login credentials. In one study,credit card issuers cited retail ATO fraud as the biggest reason for investing in machine learningbased antifraud technology.2Nearly all of these solutions, however, are focused on catching the criminals after they haveaccessed the accounts—completely understandable given the way online fraud departmentsdeveloped. But, working with other parts of an organization that are more focused on networksecurity to address bot traffic could significantly lessen the burden many shoulder due to accounttakeover fraud.
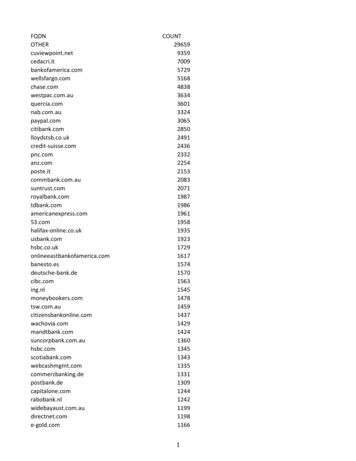
BotMa na ge m e nt:An Overlooked Layer in Account Takeover DefensePG. 4Bots Directing Credential Stuffing Attacks at Online Retailers and Travel IndustryCompanies that have visibility into bot-delivered credential stuffing attacks and effective solutionsto mitigate those attacks are preventing account takeover before it happens. For some time, fraudexperts have been recommending that fraud fighters consider layering multiple tools in theirdefense. Implementing one of those layers at an earlier stage could markedly affect the amount ofATO fraud a company faces.The challenge specific to bots and account takeover fraud was highlighted recently in a new studyfrom Akamai.3 With visibility into up to 30 percent of the world’s web traffic, Akamai is uniquelypositioned to tap into security data surrounding that traffic and identify bots that are taskedwith testing stolen login credentials. In Q4 2017, for the first time, Akamai examined login trafficwith an eye toward credential abuse and found it’s happening on a massive scale. Of 8.3 billionlogin attempts across its network, the company determined that 3.6 billion were malicious loginattempts.“In other words,” the report’s authors wrote, “43 percent of all logins seen by Akamai wereattempts to log in to an account using password guessing or account details gathered fromelsewhere on the Internet.”
BotMa na ge m e nt:An Overlooked Layer in Account Takeover DefensePG. 5In November 2017 alone, e-commerce retailers that used Akamai to make their Website contentavailable around the world faced more than one billion login requests from bots that were partof credential stuffing attacks. Hotel and travel sites, another vertical suffering from an increase inATO fraud, saw nearly that many.Just like the fraud they are used to commit, bad bot attacksare becoming more sophisticated and difficult to detect.Just as antifraud solutions are evolving to meet thatsophistication (i.e., integrating advanced technologies likeartificial intelligence and machine learning), so are solutionsdesigned to identify and manage malicious Web trafficgenerated by bots.And, while bot management generally is seen as an IT orsecurity initiative, hence, outside the purview and controlof the fraud department, a solution that could interceptmalicious login attempts before they occurred wouldtranslate directly into a reduction in the number of stolencredentials validated and sold to fraudsters to monetize.Fraud departments are vital to the bottom line of card-notpresent merchants and account takeover fraud is not goingaway. But a reduction in the overall number of compromisedaccounts will likely result in the number of fraudulenttransaction attempts and the attendant customer impact.“Of 8.3 billion login attempts acrossits network. 3.6 billion weremalicious login attempts.In other words, 43 percent ofall logins seen by Akamai wereattempts to log in to an account“Employ Bot Management in a Layered Defenseusing password guessing oraccount details gathered fromelsewhere on the Internet.For online sellers increasingly suffering from account takeover fraud, initiating an organizationaldialogue about how bot management can benefit multiple areas of a business could result in theaddition of an important layer of defense.1 – 2018 Identity Fraud Study, Javelin Strategy & Research2 – Machine Learning: Fraud is Now a Competitive Issue, Aite Group3 – Q4 2017 Akamai State of the Internet Report, Akamai Technologies
BotMa na ge m e nt:An Overlooked Layer in Account Takeover DefensePG. 6ABOUT CARD NOT PRESENT Card Not Present, part of the RELX Group, is an independent voice generating originalnews, information, education and inspiration for and about the companies and peopleoperating in the card-not-present space—one of the only sources of content focused solelyon this growing segment of the payments industry. Our only product is information. Ouronly goal is to provide it in an unbiased manner to our subscribers. The company’s mediaplatforms include the CardNotPresent.com portal, the hub for news, information andanalysis about the payments issues that most affect merchants operating in the space; theCNP Report, an e-newsletter delivering that focused information directly to your emailinbox twice a week with no extraneous clutter; the CNP Expo, an annual gathering of theleading companies in the space from the smallest e-commerce Websites and technologyproviders to global retailers and payment processors; and the CNP Awards, an annual eventhonoring the products and solutions CNP merchants rely on most to increase sales. Formore information, visit www.CardNotPresent.com.ABOUT AKAMAIAs the world’s largest and most trusted cloud delivery platform, Akamai makes it easierfor its customers to provide the best and most secure digital experiences on any device,anytime, anywhere. Akamai’s massively distributed platform is unparalleled in scale withover 200,000 servers across 130 countries, giving customers superior performance andthreat protection. Akamai’s portfolio of web and mobile performance, cloud security,enterprise access, and video delivery solutions are supported by exceptional customerservice and 24/7 monitoring. To learn why the top financial institutions, e-commerceleaders, media & entertainment providers, and government organizations trust Akamaiplease visit www.akamai.com, blogs.akamai.com, or @Akamai on Twitter. Copyright 2018 Card Not Present This document was produced as a joint effort between Card Not Present and Akamai.
anytime, anywhere. Akamai’s massively distributed platform is unparalleled in scale with over 200,000 servers across 130 countries, giving customers superior performance and threat protection. Akamai’s portfolio of web and mobile performance, cloud security, enterprise access, and video delivery solutions are supported by exceptional customer