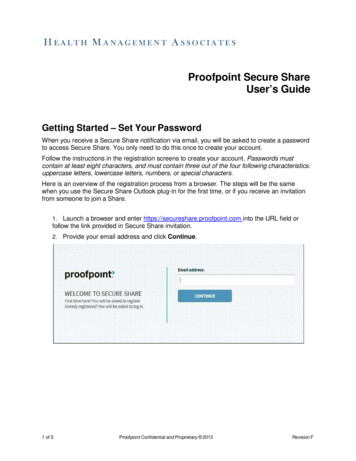
Transcription
Continue62053474975 34984040.516129 14112258430 41467364447 94967070340 41644853064 24570453.84 19484151.808081 86328050829 105719374480 20933671.20339 91781066482 28038137.317073 43306097228 351229123.6 8562929745 74322179007 148377760930 5578867.4235294 7509483.5052632 30941184305 46920721.55125944311146 1958958826 11888814.77 48282178896 16447818480
Proofpoint end user guide template example excelAnyone with admin privileges controls the administrative privileges for all other administrator accounts. Err msg Varchar(255) The remainder of the log line. When messages enter the Quarantine, they receive a timestamp. Vendor Varchar(32) The name of the vendor for the Virus Protection module. The copying, modification or distribution of theProofpoint Protection Server is subject to the terms of the Proofpoint Software License, and any attempt to use this software except under the terms of that license is expressly prohibited by U.S. copyright law, the equivalent laws of other countries, and by international treaty. Msg count Int(10) The count of how many messages were seen in that timeperiod with the adultscore. However, if the master is also filtering email coming from the Internet, it should be deployed in the DMZ along with the agent systems. Release 7.0 Reference Guide 17 Chapter 1 - Introduction The Message Processing Hub is comprised of an Interface Hub, a Message Disposition Hub, and the current message connectionstate maintained in memory. Click the Log Settings link under Logs and Reports in the navigation pane. DNS Domain Name Server DoS Denial of Service filter server A Proofpoint Protection Server that is deployed only for filtering services. You will change a copy of the filter.cfg file that you first check out using the CVS command. To ensure youremail policy is enforced, you can set spam score thresholds that determine spam classifications and the associated dispositions. Change the following parameter value from 1 to 0: service.assigned.db.quarantinecache 9. The disposition is Continue processing the message and add an x-header to the message. The rule would also catch any emails thatrefer to the character set in the body of the email. Digest count int(10) unsigned The number of Digest email messages generated. 10. The cloneconfig.pl utility is located in the directory {PROOFPOINT ROOT}/admin/tools. For example, when you add an administrator you can limit his or her privileges to the Logs and Reports module and the EmailFirewall module. Example 2 – filtering in the same module 78 Chapter 7 - Message Filtering Outcome: A copy of the message is placed in the Quarantine (Rule 1) because Quarantine is higher on the delivery disposition list than Continue, Deliver Now, or Discard. 67 Chapter 7 Message Filtering This chapter describes the path of a message throughthe Proofpoint Protection Server filtering modules. The log upload.pl command must be run by the pps user. pps control Usage pps control.sh [option] Commands: forcerestart 88 Stops then starts the management interface child processes without affecting the parent process. Enter Discard Messages Containing Cyrillic Characters into theDescription field. [-base -b] ] No Base DN (Distinguished Name). Performance Optimization This section describes a procedure to enhance the performance of Quarantine database queries on the Quarantine Node. 90 useradm Usage . While we have designed a spam score of 50 to represent the breaking point between spam and not spam, dependingon the spam and valid email profile for your organization, you may achieve better results by increasing or decreasing this threshold. Permission is granted to anyone to use this software for any purpose, including commercial applications, and to alter it and redistribute it freely, subject to the following restrictions: 1. -exportallmsgs Export allmessages from all of the folders to a file. This is a convenient feature when you have opened a CTS call and are working with technical support to resolve a problem. Reject the message with an SMTP error code. Case 4: Message has invalid recipient, includes subject, includes body, does not contain a virus. Interface Hub . Any rule that is triggeredby a message can send a copy of the message to the Quarantine Audit folder. set -key parameter name -value parameter value Set the value of the specified parameter. editgroup groupid [attr1 val1 attr2 val2.] Changes the group specified by the group ID with the attributes and values specified. Organizing messages into folders in the Quarantine ishighly recommended for the following reasons: Tracking messages that trigger specific rules. An Active Directory server. Rule Varchar(32) The triggered rule. Go to the Appliance SMTP Settings General page. Deliver Now – deliver the message to the recipient without further filtering. useradm.sh -host ldapserver -base "ou people,dc company, dc com" -groupattr memberOf -groupidattr name 100 Chapter 8 - Command Line Interface Advanced Imports This section contains examples of advanced imports. In the case where a copy of the message is sent to the Quarantine, the filtering and processing continues on the messages that contain virus X. Value: charset windows1251. This section describes how to configure the master Proofpoint Protection Server or appliance so that the management interface displays the Quarantine Node designation option when you add an agent to the cluster. host, instance, servicename, and adultscore combination. Email Firewall Module . Deploying multiple clusters in such anenvironment affords the following advantages: Each department controls its own cluster and enforces its own policies. Using a secure shell, log in to the Proofpoint Protection Server system as the user with administrator privileges for the sendmail configuration files. l List. 39 Routing Email . 40 Adding a Legitimate Postmaster Address . SummaryStatus. The default value is 1. 29 Educate the User Community . Rcpts count int(10) Number of recipients to which the encrypted message is sent. All of these options are controlled by the administrator. Hdr message id Varchar(64) The header message ID. When you are searching for outbound messages in the Quarantine, you may want to excludethe messages that originate from spammers emulating your organization as the original sender. 45 Use the Discard Disposition for Unwanted Email . - Warnings and errors in all relevant files. [-starttls] [-type] Yes Imports or exports the entries by type of object, using one of these modes: a Automatically, based on objectClass (this is the default).ATTR WHITELIST whitelist -1 Default setting * 1 HTML/Text 2 Text Only 3 HTML Only DigestContentType contenttype Digest Format parameters 4 HTML/Text HTTP commands 5 HTML Only HTTP commands 6 Simple HTML/Text 7 Simple HTML 8 Simple HTML/Text HTTP 9 Simple HTML HTTP SendEmptyDigestIncludeAuditFolder emptydigest IncludeAuditFolder Empty Digest parameters Include Audit folder in Digest -1 Default setting* 1 Do Not Send Empty Digest 2 Send Empty Digest -1 Default setting* 1 Do Not Include Audit Folder 2 Include Audit Folder -1 Default setting* SendDigest SendDigest Send Digest 0 Do Not Send Digest 1 Send Digest SpamClassification 96 SpamClassification Spam policy Text; internal policy name. The combination of the filtering event order and the importance of actions applied in an event ultimately determine the final outcome for the message. useradm Usage useradm.sh See Table 1 for a description of the options. For accurate logging andreporting purposes, the timestamps for log entries must be accurate. This is captured by leveraging the same policy route concept. Log Database Schema This topic presents the log database schema for administrators that export the Proofpoint Protection Server database tables for import into another reporting tool or storage area for processing.normal Reboot your machine. one Search the entries immediately below the base object. Spam and virus policies and configuration settings on the agents is managed centrally from the master. The following table describes the internal sequence of events: Priority Sequence of Events 1 Execute the rule. Summary Control . If the postmaster address isnot provided or is incorrect, all undeliverable email and email to root will remain in the /var/spool/mqueue, potentially causing the system to consume system resources or run out of disk space and cause a “temp fail.” Proofpoint Protection Server Follow these steps on a Proofpoint Protection Server to edit the /etc/aliases file to add a legitimatepostmaster address: 1. Tagging a File Set Tagging a file set means saving a file set with a name and description. Each instance has its own local copy of the configuration, so it is not reliant on any other servers for processing. Servicename Varchar(32) The name of the service in an instance – for example, filter. Applies only if you are also using the remove option. Delete the file .serv from the directory. Env from 56 Type Varchar(255) Description The envelope sender. Retry – temporarily reject the message due to resource constraints. Type Description Module Varchar(32) The name of the module. eid.admin.patch.manual deploy required patch A patch that requires manual deployment isavailable A patch has been distributed that requires manual deployment. -queuestat Displays the messages in the buffer queue. Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License.You may obtain a copy of the License at Unless required by applicable law or agreed to inwriting, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. debg Debug. Duration Float unsigned The total duration time for a connection. If the envelope recipient equals userA place a copy of the message in the Quarantine folder userA, andContinue to process the message. You can optionally include the original subject line. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR APARTICULAR PURPOSE ARE DISCLAIMED. If you change the admin password on the master, it will not automatically change on the agent. Topics that are product-specific are noted as such in the topic heading. Open the file {PROOFPOINT ail.mc. Delivery dispositions Secure Digital AssetsSpam Detection Reject Regulatory Compliance Regulatory Compliance Retry Email Firewall (and recipient verification) Digital Assets Redirect Lowest Discard Audit Deliver Now Continue Notes: 1 – Detect virus, compute the Digital Assets and Regulatory Compliance module scores. 2 – Compute the spam score, trigger the Spam Detection modulerules. datuil.sh -reindex Scan and create signatures for all the documents that are currently stored in the Document Repository. Looks up the owner of a mailing list during an import. Release 7.0 Reference Guide 53 Chapter 6 - Maintenance and Troubleshooting Table Message Column Type Description Duration Unsigned float The processing time fora message. As the agents process incoming email, mail will be routed to the appropriate servers. In this Release 7.0 Reference Guide 25 Chapter 2 - Deployment and Installation design, one server is a dedicated master and does not filter email, allowing for all of its resources to be dedicated to administration, the Quarantine, Digest processing, andend-user functionality. Options: admin Web-based management interface. In summary, a message that triggers composite rules with OR conditions will trigger as the conditions are found in the message processing callbacks and MIME parts. Any unique value you provide for a Digest parameter in a .cfg file will automatically take precedence over thedefault value in the .res file. Open the file pps env.sh for editing. However, since the recipients for the outbound messages are not included in your organization’s User Repository, they will never receive a Digest that contains these messages. -sender Envelope Sender. -release Release the messages. We believe the spam detection mechanisms providethe necessary tools for you to fine-tune the Proofpoint Protection Server to meet your specific needs. Trigger the Digital Assets and Regulatory Compliance scores based upon MIME parts analysis. 3 – When more than one rule is triggered in the same module, and different Quarantine folders are specified for each rule, a copy of the message is storedin the folder for the first rule that is triggered in the module. This is the default. Msg guid Varchar(32) The global unique identifier for the message. clone config Usage clone config.pl [-a] [-c] [-g ] [-h] [-l ] -s -t [-v] 112 Chapter 8 - Command Line Interface Options -a addagent Caller is add agent, which means the upgrade deploy lock is already held.Outcome 2: Rule 1 triggers first because the recipient is invalid and applies the Quarantine disposition, so the message continues to process. For large deployments Proofpoint recommends turning off filtering on the master so that it can be dedicated to administrative tasks. Adultspam Tinyint(4) A flag to indicate whether or not the envelope senderis an adultspam sender. Message Attachment . Chapter 8 - Command Line Interface -folder -f Quarantine folder name. With master and agent (clustering) capabilities, there is no administrative burden added when the number of servers is increased. The steps below assume that the master Proofpoint Protection Server or appliance is viable – only theQuarantine Node needs to be recovered. If the message scores greater than or equal to 80, Discard it and send a copy of the message to the Quarantine folder named extreme spam. In this case a Proofpoint cluster can be deployed for each departmental email infrastructure, in addition to the central gateways. If the Routing Table uses DNS forrouting purposes, the appliance will look up the preference of the mail server in the DNS entries. Name the page that you embed the HTML, Image, or Java Script report using this convention: .shtml. For example, a spam policy for your organization can include one or more rules for managing spam. As a message passes through the filtering modules,it accumulates results such as a spam score, virus detection, and a score based upon adherence to corporate policies regarding content. 47 Creating a Query for Outbound Messages In the Quarantine . If for any reason the master Proofpoint Protection Server is off-line for a temporary period of time, messages continue to be saved in the agentQuarantine Queue until the master Proofpoint Protection Server is back on-line. -status Displays whether the buffer queue is running or not. The ctsID is required so that the logs can be associated with a ctsID once they are uploaded. Options: expiration Sets the folder expiration (in seconds). Web Application . Msg guid varchar(32) The global uniqueidentifier for the message. Virus Tinyint A flag to indicate whether or not the envelope sender sends messages containing a virus. These values are recorded at the end of a session. Blocking Email with Specific Character Sets To create an Email Firewall rule to block email messages with a specific character set, you need to reference the appropriatecharacter encoding. Msg count int(10) unsigned Not used (always 1). Configure password policies on the Groups and Users Password Policies page, then select a password policy for administrators. 33 POP3 Links versus HTTP Links for Digest Actions . groupadm Usage groupadm.sh [-] Examples createdb --login root -password 'your mysql password' --force Re-creates the user database (User Repository) and the global and spam reporting groups. All rights reserved. Message Processing Hub – this multi-protocol hub accepts all incoming messages and commands, passes messages to the Analysis Modules, exposes the functions of the Management Services, andhandles final message dispositions. After a message has been filtered by all the modules the Hub makes the final judgement for the message disposition. The value 1 collects the least amount of information, 3 collects the most. Each cluster consists of a master server (for centralized administration, reporting, and Digest generation) and several emailfiltering agents. Depending on your organization’s policies, you may want to archive the log files before deleting them. This deployment is cost-effective and redundant, but it does not offer the same degree of protection against internal directory information leaking into the DMZ infrastructure. Save and close the file. For the sake of brevity, thefollowing columns are not duplicated (except where noted) for each message-specific table in the Database Schema description: 52 row id Bigint(20) timestamp entry id Datetime Varchar(8) Auto-incrementing integers that hold a unique number for each row. On a Proofpoint Protection Server you must configure sendmail by adding the domains tothe sendmail mailertable that accept mail and the hosts that will route mail for these domains. The crontab entries start and maintain processes that are critical to the health of a cluster. The message ID in a session. The original message is discarded, and a copy of the message is sent to the Quarantine folder named extreme spam, because theQuarantine folder for the Spam Detection module folder is higher on the precedence list than the Quarantine folder for the Email Firewall module. All software, spam, and virus definition file updates and policy configuration changes are automatically pushed to the agent servers, keeping the configuration synchronized across the entire cluster. importmsgs Import messages from a file. Timestamp 62 Type datetime The date and time of the action performed on the Quarantine. Please include the name of the document and the revision date with your email. Please try to deploy the patch again. You can also mirror the configuration repository on another system or archive it for later recovery.For example, if a message triggers a rule that strips an attachment from it and triggers another rule that re-routes it to a different SMTP server, the attachment will be stripped before the message is re-routed. 131 Index . Disposition options are aggregated for the message. n Does not replace all user data. Override all imported entries for theSendDigest attribute with the value of 1. Adding a Legitimate Postmaster Address It is important to ensure that the correct postmaster address is provided to the Proofpoint Protection Server or appliance. (Note, the .res and .cfg files are encoded in UTF-8 and might not display properly on your monitor.) 6. Execute the internal function within theProofpoint Protection Server code. By weighting each of the MX records equally, you will ensure a random but equal distribution among the agents. Release 7.0 Reference Guide 123 Appendix B - Alerts Severity: Resolution: ID: Category: Title: Description: Severity: Resolution: ID: Category: Title: Description: Severity: eid.admin.update.update rebootupdate Update done. This does not affect your ownership of the derived work itself, and the intent is to assure proper credit for the authors of gd, not to interfere with your productive use of gd. Release 7.0 Reference Guide 81 Chapter 7 - Message Filtering Figure 6. 110 Options . Therefore, if you want to filter mail from an additional domain, you willneed to add it to your sendmail configuration. log upload Usage To execute a log collection and upload job: log upload.pl -c [-i ] [-l ] [-u ] [-d v] Logs are collected per the level parameter, then uploaded to the specified URL, or to Proofpoint by default. servicename – is the name of the service that creates the log file. If no new folders are created, allmessages are sent to the system folder named Quarantine. Import Attributes External sources include a CSV file or LDAP server. Simple Imports To import entries from standard input: cat input.ldif useradm.sh -format ldif -import - Release 7.0 Reference Guide 99 Chapter 8 - Command Line Interface To import entries from an FTP location:useradm.sh -import ftp://[email protected]/tmp/data.ldif To import entries from an HTTP location: useradm.sh -import To import the entries from a LDIF file: useradm.sh -i users.ldif To import the entries from a CSV file: useradm.sh -i users.csv To import entries from an LDAP server anonymously: useradm.sh -h -b "cn Users, dc company, cd com"To import entries from an LDAP server and update the existing entries in the repository: useradm.sh -h -b "cn Users, dc company, cd com" -u -p -u To import entries from an LDAP server and assign a specific value for a specific attribute: useradm.sh -attrvalue "attribute name attribute value" To import entries from an LDAP server and excludethese users –[email protected], [email protected], and [email protected]: useradm.sh -i ldap://ldap/ou people,dc extreme-email,dc com -filter "(&(mail *)(!([email protected]))(!([email protected]))(! ([email protected])))" Note: The example above is one line of text. expiremode Expiration mode. Judgement Table Judge Column Judge The final messagejudgement table (1-N per message). The Email Client attribute determines how users process Digest actions. The Spam Detection, Regulatory Compliance, and Digital Assets modules do not support authoritative rules. Refresh the configuration on the Proofpoint Protection Server: ./pps ctrlpoint.sh -H :port -u -w refresh Commands for the UserRepository The useradm command and several options are available for populating and managing the User Repository. Consolidated logs and reports. Route Varchar(255) The Policy Route names, delimited by commas (,). 9 Continue processing the message and continue processing Milter calls. The default is 10000. .117 Appendix A – Log FileFormat . 15 Filtering Order for the Modules . Log Entry Format Log entries for reporting are generated in this format: [yyyy-MM-dd hh:mm:ss.SSSSSS timezone offset] loglevel mod xxx cmd xxx [key1 value1 key value2. In no event will the authors be held liable for any damages arising from the use of this software. Create Quarantine databasemessage queue if one does not already exist. For example, in the Email Firewall Module an example of a condition is “the message is from sender HELO domain name example.com.” As another example, in the Spam Detection Module, a condition is “the message has a spam score of 65.” A disposition is what happens to the message after theProofpoint Protection Server finishes filtering it. Make sure SSI is enabled on your Apache or Windows IIS server. (For more information: 2. API Application Program Interface CLI Command Line Interface classification Every analysis module classifies messages by conditions that you define. -k kill [] Tells log upload.pl to clean up the files associatedwith the given jobID, or to clean up all collection job files if jobID is not specified. Msg count Int(10) How many messages were processed. Search for the parameter for the value you want to change in the appropriate section. .113 Embedding Report Data in an HTML Page . 39 Proofpoint Protection Server – Editing the Sendmail Mailertable .However, if performance is adequate for your configuration there is no need to alter kernel parameters. Chapter 1 - Introduction Modules, Rules, Conditions, and Dispositions At each step of the SMTP protocol, a message is processed by the Proofpoint Protection Server modules. 94 CSV File Format . [-verbose -v] Verbose mode. 23 DeploymentOptions . Example 2. When creating rules, administrators have the option of sending messages to specific folders in the Quarantine. Master-Agent Cluster Architecture In the Proofpoint solution, several appliances or Proofpoint Protection Servers can be deployed in a cluster. For example, if your email community consists of most users online during
working hours and a small set of remote users, you could set up the Digest actions as follows: 34 Apply the global attribute HTML/Text HTTP Commands or HTML Only HTTP Commands. Agents and Passwords . Administrators can create individual rules that apply a disposition to a message depending upon whether the message has one validrecipient, more than one valid recipient, or no valid recipients. Open the file .serv for editing. Discard – accept the message from the sending host or IP connection and quietly discard it without providing any information to the sending host. Custom Spam Detection (Rule 3) is higher than Spam Detection (Rule 2) on the module precedence list, sothe score of the message is set to 99. Rule varchar(64) The name of the triggered rule. Since spammers typically use spoofing for sending email, you do not want to use Retry or Reject because you will not get a response from the sender and you do not want the sender to learn a legitimate email address for your organization. For example: Version Fileset 1 filter filter.cfg 7.1 7.2 7.3 7.4 dictionary1 7.1 7.2 dictionary2 7.1 7.2 7.3 7.1 7.2 7.3 7.4 7.5 Tag: Production 10 15 2011 Release 7.0 Reference Guide 85 Chapter 8 - Command Line Interface Rolling Back a File Set If you apply configuration changes to the Proofpoint Protection Server and message filtering does not behave as you expect, you canroll back the configuration to a point in time where filtering was working as you expected. On the Proofpoint Protection Server (the master Proofpoint Protection Server) log in as the Proofpoint administrator to the system using the command line interface. If you have deployed Proofpoint Encryption, envelope splitting takes place. Proofpointgratefully acknowledges contributions of the open source community to the Proofpoint Protection Server. Example 1 – filtering in the same module Release 7.0 Reference Guide 77 Chapter 7 - Message Filtering Outcome: A copy of the message is placed in the Quarantine (Rule1) because Quarantine is higher on the delivery disposition list (see “3 –Delivery Dispositions” on page 72) than Deliver Now, Discard, or Continue. VMware, the VMware “boxes” logo, GSX Server, ESX Server, Virtual SMP, VMotion and VMware ACE are trademarks (the “Marks”) of VMware, Inc. Source is available at cre/. Change directories to /etc/mail. To predict thefinal outcome for a message, it is important to understand the concept of execution priority and action importance across all of these areas: the SMTP protocol message processing callbacks, filtering modules, delivery dispositions, rule ordering, and Quarantine folders. Use CVS to check in the sendmail.mc file. Portions relating to GD2 formatcopyright 1999, 2000, 2001, 2002 Philip Warner. timezone offset is the difference between local time and GMT (Greenwich Mean Time). Excluding Spammers from the Outbound Message Query Spammers will try to send email to your organization using your domain name as the sender address. Release 7.0 Reference Guide 23 Chapter 2 Deployment and Installation Modify your MX records so that you have one MX record for each agent. An error occurred when setting up the upgrade. The Proofpoint Protection Server uses sendmail as one of its MTAs, and it defaults with a greeting that displays “Sendmail.” Follow these steps to change the greeting: 1. Improving scalability andperformance involves balancing the OS configuration with the needs of the applications on a specific hardware configuration. The Proofpoint Protection Server is designed to fit seamlessly into your corporate environment, taking advantage of the existing corporate messaging infrastructure. The End User Services Resources Global page providesa central location for changing the content of the Web Application and Digest. 47 Blocking Email with Specific Character Sets . For each SMTP protocol message processing callback and MIME part of a message, the order of events is applied from left to right, and the precedence within each event is applied from highest to lowest. .112 queued Usage. Use the UNIX command netstat -nl to list the ports in use on the Proofpoint Protection Server. Deployments will vary according to an organization’s email volume, network infrastructure, and geographical constraints. Database Schema The following tables describe the database schema. Chapter 4 Security This chapter includes tips for protectingthe administrator accounts and enhancing security. If you have an ICAP-enabled web proxy server (Internet Content Adaptation Protocol) on your network, you can also filter HTTP content by enabling rules for HTTP content in the Regulatory Compliance and Digital Assets modules. 0 Drop table, 1 Delete. Embedding Report Data in an HTML PageThe instructions you follow depend on the type of system you use to embed the HTML, image, or Java Script report data in an HTML page: Server Side Include (SSI) supported system in Apache and Windows IIS, or Non-supported SSI system Release 7.0 Reference Guide 113 To embed the report in an HTML page using an SSI-supported system:1. Date Date of the message. -reason Module name for quarantined message. Run the following commands to populate the Quarantine Node with the Quarantine folder names and properties from the backup. Release 7.0 Reference Guide 33 POP3 Links versus HTTP Links for Digest Actions You can set up the Proofpoint Protection Server to use aPOP3 mail server or HTTP links to process end user Digest actions such as releasing messages and requesting a safelist. The disposition is place a copy of the message in the Quarantine folder named virus and Discard the original message. Add X-headers to the message. 44 Use Quarantine and DLP Incident Folders to Organize Messages . - Thesendmail log files. (See page 73 for more information on rule ordering.) Figure 1. Highest 1. Spam Dete
Proofpoint Protection Server Follow these steps on a Proofpoint Protection Server to edit the /etc/aliases file to add a legitimate postmaster address: 1. Tagging a File Set Tagging a file set means saving a file set with a name and description. Each instance has its own local copy of the configuration, so it is not reliant on any other servers .