Transcription
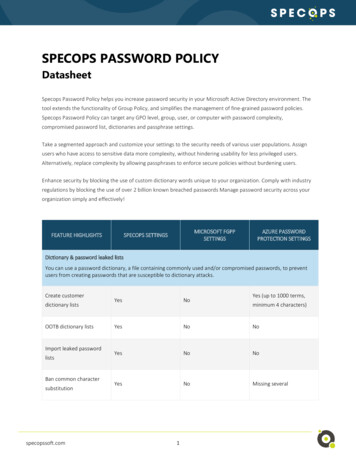
WHITE PAPER: ENZOIC FOR ACTIVE DIRECTORYWHITEPAPERAutomate Password Policy Enforcement& NIST Password GuidelinesEnzoic for Active Directory enables real-time password policy enforcement withdaily password auditing and automated remediation. With compromisedpassword detection, custom password dictionary, fuzzy matching with commoncharacter substitutions, and continuous ongoing monitoring; enterprises caneasily adopt NIST password requirements and eliminate vulnerable passwordsin Active Directory.The newest version Enzoic for Active Directory follows NIST password guidelinesas it screens for weak, commonly-used, expected, and compromised passwords.It checks the password at the time it is created or reset, and then monitors itdaily against a real-time compromised password database.Why Do Organizations NeedContinuous PasswordProtection?that attackers use, so they provide limitedprotection. Additionally, since those lists requiremanual updates, it doesn’t protect organizationsfrom any recent breach lists.The average person reuses a given password atleast 13 times. Most people know not to reusepasswords, but struggle to recall uniquepasswords for all of their personal and workaccounts. Cybercriminals rely on this laxbehavior and prey upon the vulnerabilitiescaused by password reuse. This is whycompromised passwords are responsible for 81%of hacking-related breaches.Screening passwords against a consistentlyupdated list is critical. Attackers are frequentlyusing the freshest exposures they can findbecause they know the more recent exposureswill result in more successful outcomes. If anorganization only uses old password blacklists,they are giving attackers a much larger attackwindow to take over an employee account.IT and Security teams are fighting back withcompromised password screening. For example,some IT organizations download static passwordblacklists off the Internet and then periodicallymonitor their passwords against thoselists. That is a great first step, but those lists aretypically only 10-20% of the common passwordsEnzoic for Active Directory enables continuouspassword monitoring against a proprietarydatabase of previous breach corpuses that isrefreshed daily. It is NIST 800-63b compliant. Itthen continues to monitor the password daily toensure it doesn’t become unsafe while it is inuse.GET A FREE TRIAL enzoic.com 1-720-773-4515 info@enzoic.com1
WHITE PAPER: ENZOIC FOR ACTIVE DIRECTORYWhy Should OrganizationsScreen for Commonly-UsedPasswords?Many employees use weak, common passwordsand are completely unaware of it becausethey’ve satisfied password policies based ontraditional algorithmic password complexityrules. For years the security industry has beentrying to educate employees, yet still haven’tbeen able to secure this vulnerability. Manyorganizations are now choosing to take thisburden off their employees and automatingpassword screening to account for normalhuman limitations and behavior when it comesto passwords.It starts with preventing common dictionarywords. Every English-language word can befound in cracking dictionaries so organizationsshould prevent employees from using basicdictionary words in isolation. Pairing commonwords with other words, special characters andnumbers can be allowed with appropriatecharacter lengths. Additionally, organizationsshould block repetitive characters or sequentialcharacters (for example: aaaaaa, 111111). Lastly,there are the most common passwords thatattackers know some people will use soorganizations should be blocking commonpasswords (for example: 123456, 12345678,qwerty, abc123, password1, iloveyou, etc.)Why Should OrganizationsBlock Expected and SimilarPasswords?Most employees will also create or reusepasswords that are context-specific or expected.This can be expected passwords in the form of aroot password that gets changed by just a fewcharacters or even just capitalization. Onceagain, attackers know that this is a commonpractice on any system with users logging in, soorganizations also need to prevent theseexpected passwords and their various forms.Organizations should also deploy fuzzypassword matching against the entries in theirpassword blacklist. The reason why fuzzymatching is important is if your password isrecently exposed online from another site, anattacker will choose to try patterns of thatpassword. They will be highly successful in thatendeavor because most people use patternswhen selecting their passwords. Fuzzy passwordmatching checks for multiple variants of thepassword, including case sensitivity as well ascommon substitutions such as leetspeak andpassword reversing.For example: If your exposed password is“HolidayVacation1”, attackers will usually tryvariations such as::“HolidayVacationi” Leetspeak (substitutingnumbers for letters like leet 1337)“1noitacaVyadiloH” reversed password“holidayvacation1” a case-sensitive changeAnother common employee password behaviorthat attacks exploit is using one root passwordand then use various iterations of it. This practicemakes it easier for the employee to remembertheir password, but unfortunately it also makesit easy for bad actors to figure out.GET A FREE TRIAL enzoic.com 1-720-773-4515 info@enzoic.com2
WHITE PAPER: ENZOIC FOR ACTIVE DIRECTORYWith this in mind, it is important fororganizations to implement password similarityblocking. With password similarity blocking,new passwords are screened by similarity toformer password using the DamerauLevenshtein distance.For example: If your compromised password is“HolidayVacation2018” , attackers usually tryiterations like:“HolidayVacation2019” one-characterchange“HolidayVacation2020” two-characterchange“HolidayVacation18” two-digit changeIn Enzoic for Active Directory, the systemsadmin can determine the amount of difference(called distance) that will be required betweenthe old password and the new password. Withthis password policy, the minimum number ofdifferences would be 1 and the maximumnumber of differences would be8. Organizations have varying opinions on howmany characters should be different, includingtranspositions, between old and new passwords.This configurability allows them to adjust it tothe right level for their business.Why Should OrganizationsScreen for Context-SpecificPasswords?Savvy cybercriminals will also attempt to usecontext-specific passwords to gain access intoActive Directory. They know that companiesthat have headquarters in Boston will be morelikely to have employee passwords that include“GoPatriots” due to the New EnglandPatriots. They know that since manyorganizations enforce quarterly forced passwordresets, many employees will include seasons intheir password like “Winter2019” and they knowthat many people include their company namein their password as well. Attackers exploitcontext-specific passwords because they arecommonly used by employees. To combat this,companies need the ability to create a filter for acustom password dictionary.With Enzoic for Active Directory, organizationscan add up to 5,000 custom passwords storedlocally that will be screened and blocked atcreation. These words can be local sports team,years, product names, company names, officelocations, etc. Custom passwords are partiallymatched and case insensitive so any passwordthat includes that word would be blocked. Thesecan also be optionally fuzzy matched if you havefuzzy matching turned on.For example: If your custom passworddictionary includes the word “GeneralElectric”Users would not be allowed to use that wordin any password so a password like“ILovegeneralElectric” will be blocked.How Does Automation HelpSave IT Team Time andEnergy?The goal of Enzoic for Active Directory is to allowIT to set it up and then just let it run. When anexisting password becomes vulnerable, Enzoicautomates the remediation steps that wouldotherwise require manual intervention by anAdmin or Helpdesk.Some organizations buy password policyenforcement tools that handle one or some ofthese, but the most recent version of Enzoic forActive Directory can meet all the NISTcriteria. There is no additional manual workrequired. Enzoic for Active Directory serves as aGET A FREE TRIAL enzoic.com 1-720-773-4515 info@enzoic.com3
WHITE PAPER: ENZOIC FOR ACTIVE DIRECTORYcomprehensive, automated password blacklistthat filters for weak, commonly-used, expected,and compromised passwords.Organizations have unique needs, so theautomated responses can be customized whencompromised or weak passwords arefound. The organization can select theappropriate automated action—ranging fromprompting the user to change their password todisabling the account. These remediation stepscan be set to kick-in immediately or after apredetermined delay. Alerts can also be sent tothe user directly and/or an admin or helpdesk sothe right individuals are kept informed.What Visibility Is Available?Enzoic for Active Directory has also incorporatedadditional insights into the product. It hasenhanced usage tracking so Active Directoryadministrators can see the total number ofdetections, including the number of detectionsdue to fuzzy matching, local dictionary orpassword similarity matching. With log filesnow stored in a JSON format, outsideconsumption by SIEM and log managementtools can help streamline reporting.What is Required forInstallation?Enzoic for Active Directory runs on each domaincontroller so it can check every passwordwherever it is being created; however, it onlyneeds to be configured once. All of itsconfiguration settings are stored in ActiveDirectory itself and automatically shared acrossother domain controllers to make it easy. Withthe installation wizard, it is easy to install. Somecustomers have it fully implemented in 3minutes, but of course, that depends on thecomplexity of your environment.Daily ScreeningContinuous exposed password filteringNew ExposuresDetects if a safe password becomesexposedAutomatedNo extra manual workInsightfulEnhanced dashboard and SIEM loggingQuick and QuietChecks in milliseconds and only impactsemployees that need to change theirpassword.Easy to installTake a short amount of time to install, thenyou just let it run because everything isautomated.GET A FREE TRIAL enzoic.com 1-720-773-4515 info@enzoic.com4
WHITE PAPER: ENZOIC FOR ACTIVE DIRECTORYFlow chart of how it worksEnzoic for Active Directory enables quick-to-deploy password policy enforcement and dailyexposed password screening. With a fully automated weak password filtering, fuzzy passwordmatching, password similarity blocking, and custom password dictionary filtering; enterprisescan easily adopt NIST password requirements and secure passwords in Active Directory.GET A FREE TRIAL enzoic.com 1-720-773-4515 info@enzoic.com5
password blacklist. The reason why fuzzy matching is important is if your password is recently exposed online from another site, an attacker will choose to try patterns of that password. They will be highly successful in that endeavor because most people use patterns when selecting their passwords. Fuzzy password