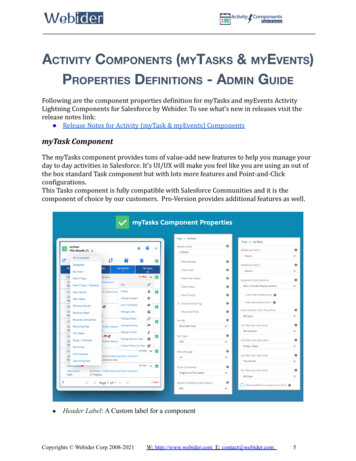
Transcription
TRITON AP-EMAIL
Stop advancedtargeted attacks,identify high riskusers and controlInsider ThreatsFrom socially engineered lures to targeted phishing, most large cyberattacks begin with email. As these advanced, multi-stage threats blendweb and email elements throughout attacks, they present a ‘Kill Chain’of opportunities to stop them before the breach occurs.Maximize your use and safety of emailTRITON AP-EMAIL identifies targeted attacks, high risk users and InsiderThreats while empowering mobile workers and the safe adoption of newtechnologies like Microsoft Office 365 and Box. From inbound attackactivity to outbound data theft or botnet communication attempts,Websense TRITON Email security protects email communications aspart of a complete TRITON APX defense against APTs and otherAdvanced Threats.Email security challenges APTs commonly use email for early stages in their advanced attacks. Email must do more to address data theft and Insider Threats. Businesses need to adopt Microsoft Office 365 and other services toexpand and compete. Risky user habits can easily lead to security breaches and data loss.Websense TRITON AP-EMAIL
TRITON AP-EMAIL capabilitiesStop APT and other AdvancedTargeted ThreatsThe Websense ACE (Advanced ClassificationSafely adopt new technologies likeMicrosoft Office 365 and Box whilesupporting your roaming workforceEngine) is at the heart of all TRITON solutionsIT departments are strained to maintainand identifies malicious lures, exploit kits,current systems while supporting anemerging threats, botnet communicationsincreasingly mobile workforce and theand other advanced threat activity across thedemands to adopt new technologies likeKill Chain. This enables TRITON AP-EMAIL toMicrosoft Office 365. TRITON AP-EMAILidentify the early stages of an attack. Withprovides industry-leading capabilities thatits powerful malware assessment capabilitiesleverage systems and other information tothat include a fully-integrated, file behavioralcontrol communications, such as preventingsandboxing, it can even identify Zero-daytotal access to sensitive email attachmentsmalware threats.on vulnerable mobile devices, while permittingfull access on fully secured laptops. TheseSecure sensitive data against externalattacks and Insider ThreatsTo prepare for a malicious Insider Threat orthe potentially successful cyber-attack, it’svital that outbound communications beinbound and outbound defenses are allsupported on Microsoft Office 365.Identify ‘high-risk’ user behavior andeducate users to improve awarenessmonitored. This is also necessary both forThe rich data collections in TRITON AP-EMAILdata theft compliance needs as well as forare used by a number of policies to reportbusiness requirements. Only Websenseand identify systems that may require specialprovides the technology to stop dataIT attention. They generate a report on ainfiltration and exfiltration, with capabilitiesnumber of Indicators of Compromise tosuch as:identify infected systems and more proactive reports on suspicious behavior, or evenOCR (Optical Character Recognition)scanning to identify sensitive datahidden in images such as scanneddocuments or screen shots. Encrypted file detection to recognizecustom encrypted files designed todefy identification. Drip DLP monitoring to identify wheresensitive data is leaked in small quantitiesover time.Websense TRITON AP-EMAIL‘disgruntled employee’ activity as potentialInsider Threats. User feedback capabilitieshelp educate employees as mistakes aremade, helping them to better learn andunderstand safe email best practices.
Enhanced Protection ModulesEmail Cloud orEmail Hybrid ModuleLeverage cloud services for performance and scalabilityEmail DLP ModuleBlock data theft with enterprise-class content-aware DLPCombine on-premise threat defenses with cloud-based prefiltering services to preserve bandwidth with industry-leadinganti-spam SLA’s. Or choose a 100% Cloud deployment of allTRITON AP-EMAIL services.Prepare for the Insider Threat and malware data theft, achievecompliance goals and further mitigate the risk to personalinformation or IP. Advanced capabilities detect data theftconcealed in images or custom encrypted files, or eventransmitted in small amounts over time to evade detection.Email Sandbox ModuleIntegrate behavioral sandboxing for additional malwareassessmentSupplement Websense ACE analytics with an integrated filesandbox for additional deep inspection, and take advantageof behavioral analysis in a virtual environment to uncover themalicious behaviour of Zero-day and other advanced malware.Test files automatically or manually to generate detailedforensics.Email Encryption ModuleEnsure the confidentiality of sensitive communicationsEnable mobile devices in your workplace by extending yourexisting security policies to mobile devices to protect themfrom Advanced Threats, mobile malware, phishing attacks,spoofing and more.Image Analysis ModuleIdentify explicit images to enforce acceptable use andcomplianceThe Websense Image Analysis Module allows employers totake proactive measures to monitor, educate and enforce thecompany email policy in regard to explicit or pornographicimage attachments.TRITON APXThe Websense recommended solution for completeprotectionExtend your protection from TRITON AP-EMAIL to TRITONAP-WEB, TRITON AP-DATA or TRITON AP-ENDPOINT forpowerful, unified protection across all channels of attack.Websense TRITON AP-EMAIL
The power behindTRITON solutionsACE (Advanced Classification Engine)Websense ACE provides real-time, inline contextual defenses for Web,Email, Data and Mobile security by using composite risk scoring andpredictive analytics to deliver the most effective security available. Italso provides containment by analyzing inbound and outbound trafficwith data-aware defenses for industry-leading data theft protection.Classifiers for real-time security, data and content analysis — the resultof years of research and development — enable ACE to detect morethreats than traditional anti-virus engines every day (the proof is updateddaily at http://securitylabs.websense.com). ACE is the primary defensebehind all Websense TRITON solutions and is supported by theWebsense ThreatSeeker Intelligence Cloud.Integrated set of defense assessmentcapabilities in 8 key areas. EMAIL ATTACKSReputationAnalysisAnti-Malwareavailable to supportdeep inspections. Predictive securityengine sees severalURLClassificationmoves ahead. BehavioralSandboxingInline operation notReal-timeSecurityClassificationKACTTBAblocks threats.WEonly monitors, onReal-time DataClassificationTADAWebsense TRITON AP-EMAILIL ATTAC KS10,000 analyticsEMA BWETFHET
ThreatSeeker Intelligence CloudThe ThreatSeeker Intelligence Cloud, managed by Websense SecurityLabs , provides the core collective security intelligence for all Websensesecurity products. It unites more than 900 million endpoints, includinginputs from Facebook, and, with Websense ACE security defenses,analyzes up to 5 billion requests per day. This expansive awarenessof security threats enables the ThreatSeeker Intelligence Cloud tooffer real-time security updates that block Advanced Threats, malware,phishing attacks, lures and scams, plus provides the latest web ratings.The ThreatSeeker Intelligence Cloud is unmatched in size and in its use ofACE real-time defenses to analyze collective inputs. (When you upgradeto Web Security, the ThreatSeeker Intelligence Cloud helps reduceyour exposure to web threats and data theft.)TRITON ArchitectureWith best-in-class security, Websense TRITON unified architecture offerspoint-of-click protection with real-time, inline defenses from WebsenseACE. The unmatched real-time defenses of ACE are backed by WebsenseThreatSeeker Intelligence Cloud and the expertise of Websense SecurityLabs researchers. The powerful result is a single, unified architecture withone unified user interface and unified security intelligence.TRITON APXTRITON APX provides many key benefits to organizations interested indeploying the best possible protection against Advanced Threats acrossthe 7-Stage Kill Chain. They can be summarized in these three statements: Deploy Adaptive Security- Deploy adaptive security solutionsfor rapidly changing technology and threat landscapes. Protect Everywhere- The perimeter is the data. Protect criticalinformation from theft whether on-premise, in the cloud or onmobile devices. Raise the Security IQ- Combat the cyber security skills shortageby providing predictive actionable intelligence across the entirethreat lifecycle.Websense TRITON AP-EMAIL
BRAVE THE NEW WORLD.www.websense.com/APX 2015 Websense, Inc. All rights reserved. Websense, the Websense logo, TRITON and TheatSeeker, are registeredtrademarks of Websense, Inc. in the United States and various countries. All other trademarks are the property of theirrespective owner. [TRITON AP-EMAIL-BROCHURE-US-EN-23DEC14]
Websense TRITON AP-EMAIL ThreatSeeker Intelligence Cloud The ThreatSeeker Intelligence Cloud, managed by Websense Security Labs , provides the core collective security intelligence for all Websense security products. It unites more than 900 million endpoints, including inputs from Facebook, and, with Websense ACE security defenses,