Transcription
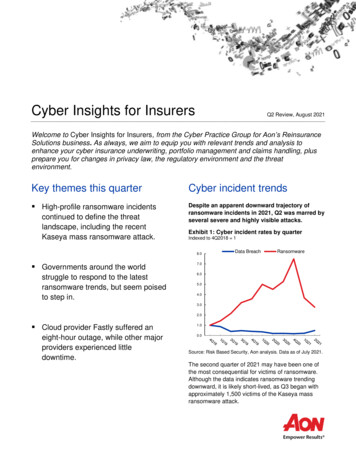
Cyber Insights for InsurersQ2 Review, August 2021Welcome to Cyber Insights for Insurers, from the Cyber Practice Group for Aon’s ReinsuranceSolutions business. As always, we aim to equip you with relevant trends and analysis toenhance your cyber insurance underwriting, portfolio management and claims handling, plusprepare you for changes in privacy law, the regulatory environment and the threatenvironment.Key themes this quarterCyber incident trends High-profile ransomware incidentsDespite an apparent downward trajectory ofransomware incidents in 2021, Q2 was marred byseveral severe and highly visible attacks.continued to define the threatlandscape, including the recentKaseya mass ransomware attack.Exhibit 1: Cyber incident rates by quarterIndexed to 4Q2018 1(Index: Q4 2018 1.0)8.0 Governments around the worldstruggle to respond to the latestransomware trends, but seem poisedto step in.Data BreachRansomware7.06.05.04.03.02.0 Cloud provider Fastly suffered aneight-hour outage, while other majorproviders experienced littledowntime.1.00.0Source: Risk Based Security, Aon analysis. Data as of July 2021.The second quarter of 2021 may have been one ofthe most consequential for victims of ransomware.Although the data indicates ransomware trendingdownward, it is likely short-lived, as Q3 began withapproximately 1,500 victims of the Kaseya massransomware attack.
An attack on a US-based oil and gas pipelineunderscored the susceptibility of criticalinfrastructure to ransomware and other attacks. Inaddition, the pipeline attack followed the disclosureof four zero-day vulnerabilities in Microsoft’s onpremises Exchange servers, which resulted in anumber of data breaches. Although technically a Q3event, the Kaseya mass ransomware event was thefirst financially-motivated mass ransomware attack(see the Aggregation Monitor section for additionaldetails). In other words, it was a rough quarter.Exhibit 2: Cyber incident rates by month in 2021Indexed to 4Q2018 1(Index: Q4 2018 1.0)9.0Data BreachRansomware8.07.06.05.04.03.02.0Additional details of the pipeline attacks laid bare thedire need for companies to shore up their defensesby practicing basic cyber-hygiene. According topipeline officials, a compromised password of aformer employee was used to gain initial access tothe network. In addition, multi-factor authentication(MFA) was not enabled, allowing the attacker to usethe compromised credentials to gain access withoutbeing challenged.It is important to note that the motivation behind thepipeline attack was purely financial, actioned by anyone of a diffuse group of criminals accessingDarkside’s ransomware as a service (RaaS) model.Coveware asserts that, “given the volume of attacksRaaS groups conduct, and the de minimis diligencethat these groups perform, we are quite certain thatthe DarkSide affiliate that attacked the pipeline hadno idea that a) it controlled 45% of the gasolinesupply on the US east coast, b) that shutting downthat pipeline would cause a consumer run ongasoline.”All this being said, what of the apparent drop inransomware attack frequency so far this year? Wedid not want to read too much into Q1, but havingseen a further drop in Q2 we wanted to investigatefurther. Indeed, observed ransomware attacks fellsharply in January and again in May and June –corresponding to the timeframes when theSolarWinds, Colonial Pipeline and JBS attacks weremost covered in the media spotlight. The REvilattackers behind JBS and Kaseya in fact went darkshortly after Kaseya.Cyber Insights for Insurers – August 20211.00.0Aon Analysis: The ransomware patterns this year suggest aninverse relationship between ransomwarefrequency and severity – or at least, betweenfrequency and notoriety. Most ransomwareattacks are financially motivated, and a highprofile attack in the headlines may cause threatactors to sink below the radar – for a time. Afterthe January drop, attack levels began risingagain and by April exceeded their December2020 levels. In addition, media attention to the ColonialPipeline event underlines the difference betweeneconomic and insured losses following aransomware attack. Gas prices spiked andsupply chains were significantly delayedfollowing that attack, but only a single tower ofcyber insurance was potentially in play. Finally, Aon assesses that RaaS criminals aretargeting companies based on signatures, not byname recognition or industry classification.Ransomware gangs are looking for the lowesthanging fruit, conducting minimal due diligenceon their targets, motivated solely by financialgain. Insurers should assess risk based on thesame signatures, which can be done using anumber of the leading risk scoring and modelingtools.2
How are governments responding?Governments around the world seem to beprioritizing ransomware defense and recognizing itas a national security issue, and not only because ofgas prices. The White House announced theestablishment of a ransomware task force shortlyafter the Kaseya event with a mandate to disruptransomware purveyors, to offer rewards to bringgang members to justice, and to developpartnerships with other governments and privatesector entities.In addition, some US lawmakers are pushing forransom payments to be disclosed to the governmentwhile others have argued that paying the ransomshould be outlawed. While it is unlikely that payingransoms will be prohibited by US law, it is apparentthat Congress and US security and law enforcementservices continue to grapple with the best way tothwart and disrupt ransomware actors.In the UK, Lindy Cameron, the head of the NationalCyber Security Centre (NCSC) noted thatransomware is the top cybersecurity threat tobusinesses and individuals. Cameron urged apublic/private partnership to stem the attacks.Aon Analysis: Whether it has been the volume ofrecent attacks or, as Coveware assesses, theresulting gasoline price increases, governmentsacross the globe seem to have finally started to takeransomware seriously. Whether governments cancooperate enough to turn the tide – particularly withgovernments known for tolerating cybercriminalsyndicates within their borders – is another question.Cyber Insights for Insurers – August 2021Aggregation risk monitorKaseya once again illustrates the unforeseendangers of supply chain risk.REvil, an infamous RaaS framework operated byPinchy Spider, either bought or developed a zeroday exploit of Kaseya’s VSA software. At the time ofpublication, it is believed REvil exploited anauthentication bypass vulnerability in Kaseya’s webinterface. Kaseya is a remote managementsoftware frequently used by managed serviceproviders (MSP) to manage the informationtechnology (IT) networks of small and mediumbusinesses. By gaining access to MSPs via theKaseya zero-day vulnerability, Pinchy Spidercompromised the networks of all of the MSPs’downstream customers.According to reports, as many as 30 MSPs werecompromised, resulting in approximately 1,500downstream victims. Pinchy Spider initiallydemanded 70 million in ransom, but then loweredits demand to 50 million. But then on July 13Pinchy Spider’s infrastructure and website wentunexpectedly dark. Kaseya obtained the decryptionkey, which appeared to be legitimate, according toEmsisoft. It is still unclear how the decryption keywas obtained without paying the ransom in full.The motivation of this attack appears to be financial,which diverges from previous cyber events at thisscale. However, ultimately Pinchy Spider did notstick around long enough to collective the ransom.Aon Analysis: Curiously, this attack ended asabruptly as it began. There could be severalreasons for Pinchy Spider’s abrupt exit, but the mostlikely explanation is pressure. The number of highprofile attacks during the first two quarters of 2021have made it impossible for responsiblegovernments to ignore the ransomware problem.Could pressure from an influential government(s)have caused Pinchy Spider to fold? Possibly. Aonstill assesses that financially motivated threat actors(i.e. criminals) are more likely to conduct targetedattacks than widespread indiscriminate, due to thepotential backlash.3
Q2 cloud outages were minimal, breaking a trendof at least one extended outage from a majorprovider during a quarter.Fastly, a cloud and content delivery network (CDN)provider experienced the longest and most impactfuloutage of the quarter. On June 8th, an invalidcustomer configuration triggered a software bug inFastly’s network, causing 85% of its network to fail.The outage began at approximately 09:47, lastinguntil 17:25. Fastly claims most services wererestored within 2 hours; however, the bug fix was notrolled out until roughly 8 hours later. Amazon.com,the New York Times, and other major websites wereaffected by the outage.Exhibit 3: Cloud provider downtime during Q2:Top U.S. providers vs. other regionsProviderNorth 142,224Europe185234,196APAC319175,358All OthersCraig Guiliano, CISSPDirector of Threat ModelingAon Reinsurance Solutions 1 312 381 1566craig.guiliano@aon.comJon Laux, FCAS, MAAAHead of Cyber AnalyticsAon Reinsurance Solutions 1 312 381 5370jonathan.laux@aon.comCatherine MulliganGlobal Head of CyberAon Reinsurance Solutions 1 212 441 1018catherine.mulligan@aon.comAside from Fastly, cloud outages during Q2 2021were minimal.Outages(count)Contact InformationLuke Foord-KelceyInternational Head of CyberAon Reinsurance Solutions 44 (0)20 7086 2067luke.foord-kelcey@aon.comSource: Cloud Harmony, analysis by AonAon Analysis: The Fastly outage highlights thecomplexities of cloud computing, and evencustomer-side configurations can result in seriouscascading failures. Although dependent businessinterruption claims appear rare, configuration errors– or malicious attacks – can result in multi-houroutages.Cyber Insights for Insurers – August 20214
About AonAon plc (NYSE:AON) is a leading globalprofessional services firm providing a broad range ofrisk, retirement and health solutions. Our 50,000colleagues in 120 countries empower results forclients by using proprietary data and analytics todeliver insights that reduce volatility and improveperformance.DisclaimerThis newsletter is made available for informationalpurposes and is not intended to be a substitute forprofessional or legal advice. No attorney clientrelationship is formed or implied between you andthe authors(s) or Aon.Cyber Insights for Insurers – August 20215
Fastly, a cloud and content delivery network (CDN) provider experienced the longest and most impactful outage of the quarter. On June 8th, an invalid customer configuration triggered a software bug in Fastly's network, causing 85% of its network to fail. The outage began at approximately 09:47, lasting until 17:25. Fastly claims most services .











