Transcription
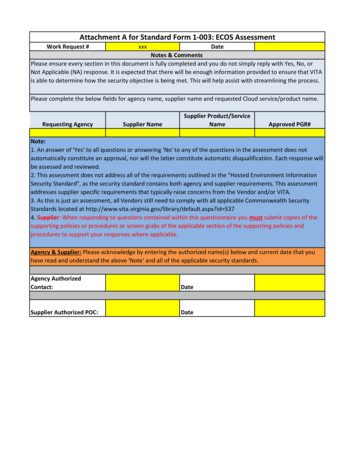
Attachment A for Standard Form 1-003: ECOS AssessmentWork Request #xxxDateNotes & CommentsPlease ensure every section in this document is fully completed and you do not simply reply with Yes, No, orNot Applicable (NA) response. It is expected that there will be enough information provided to ensure that VITAis able to determine how the security objective is being met. This will help assist with streamlining the process.Please complete the below fields for agency name, supplier name and requested Cloud service/product name.Requesting AgencySupplier NameSupplier Product/ServiceNameApproved PGR#Note:1. An answer of 'Yes' to all questions or answering 'No' to any of the questions in the assessment does notautomatically constitute an approval, nor will the latter constitute automatic disqualification. Each response willbe assessed and reviewed.2. This assessment does not address all of the requirements outlined in the "Hosted Environment InformationSecurity Standard", as the security standard contains both agency and supplier requirements. This assessmentaddresses supplier specific requirements that typically raise concerns from the Vendor and/or VITA.3. As this is just an assessment, all Vendors still need to comply with all applicable Commonwealth SecurityStandards located at id 5374. Supplier: When responding to questions contained within this questionnaire you must submit copies of thesupporting policies or procedures or screen grabs of the applicable section of the supporting policies andprocedures to support your responses where applicable.Agency & Supplier: Please acknowledge by entering the authorized name(s) below and current date that youhave read and understand the above 'Note' and all of the applicable security standards.Agency AuthorizedContact:DateSupplier Authorized POC:Date
WR NumberSEC 525 Mapping Document forSaaS Control GroupCloud Classification &ConfigurationCloud Classification &ConfigurationAccess Control: Policies &ProceduresCGIDCCC-1CCC-2ACP-1525 CIDCCC-1.0CCC-2ACP-1.1525MappingControl SpecificationEnsures appropriate information securityguards are established.Is the cloud solution you are proposing a Softwareas a Service, Platform as a Service, orInfrastructure as a Service Delivery ModelEstablishing, monitoring, and operating ITsystems in a manner consistent with COVInformation Security policies and standardsAre you offering Public, Private or governmentcloud? Please describe the solution supportmodel.Develops, documents, and disseminates to allorganization personnel, contractors, andservice providers with a responsibility toimplement access controls:Does the provider have access control policies andprocedures that are reviewed and/or updated atleast annually or required due to environmentalchanges?User access policies and procedures shall beestablished, and supporting businessprocesses and technical measuresimplemented, for restricting user access asper defined segregation of duties to addressbusiness risks associated with a user-roleconflict of interest.Does the solution have the capability to identifyand select the following types of accounts:Individual, group, System, Service, Application,Guest/anonymous and temporary?EC -1EC - 2AC-1ACP-2.1Assessment QuestionDoes the provider have the capability to segmentand identify administrative accounts by tenant?ACP-2.2Are controls in place to prevent unauthorizedaccess to your application, program or objectsource code, and assure it is restricted toauthorized personnel only?ACP-2.3Does provider document how access to tenantdata is granted and approved?Is timely deprovisioning, revocation ormodification of user access to the organizationssystems, information assets and dataimplemented upon any change in status ofemployees, contractors, customers, businesspartners or involved third parties?ACP-2.4ACP-2.5Do you provide tenants with documentation onhow segregation of duties within proposed cloudservice offering are maintained? Please providecopy of procedure(s)ACP-2.6Access Control - AccountManagementACP-2AC-2Control Enhancements for Sensitive Systems Does the provider or solution automaticallyRemoval of Temporary/Emergency Accounts. terminate temporary and emergency accountsafter a predetermined period which is not toexceed 30-days in accordance with sensitivity andrisk? Please provide copy of procedure(s)ACP-2.7Do you provide open encryption methodologies(3.4ES, AES, etc.) to tenants in order for them toprotect their data if it is required to move throughpublic networks (e.g., the Internet)?YesNoxxxAssessment ResponseN/AExplanation of response
Do you require at least annual certification ofentitlements for all system users andadministrators (exclusive of users maintained byyour tenants)?If users are found to have inappropriateentitlements, are all remediation and certificationactions recorded/documented?If different actions are taken for Admin and UserAccounts, please provide information on both.Disable Inactive AccountsACP-2.8Inactivity logoutACP-2.9Access Control - AccessEnforcementAccess Control - Separation ess Control - Least PrivilegeACP-5ACP-5.2AC-6ACP-5.3ACP-6.1Access Control - UnsuccessfulLogon AttemptsACP-6ACP-6.2ACP-6.3AC-7The information system enforces approvedauthorizations for logical access toinformation and system resources inaccordance with applicable access controlpolicies.User access policies and procedures shall beestablished, and supporting businessprocesses and technical measuresimplemented, for restricting user access asper defined segregation of duties to addressbusiness risks associated with a user-roleconflict of interest.Does the provider or solution automaticallydisable inactive accounts after 90 consecutivedays of non-use?Does the solution logout users automaticallywhen the session inactivity time has exceeded 30minutes?Are policies and procedures established forlabeling, handling and the security of data andobjects that contain data?Are controls in place to prevent unauthorizedaccess to your application, program or objectsource code, and assure it is restricted toauthorized personnel only? Providedocumentation on controls in place to preventunauthorized access.Are controls in place to prevent unauthorizedaccess to tenant application, program or objectsource code, and assure it is restricted toauthorized personnel only? Providedocumentation on controls in place to preventunauthorized access.The organization employs the principle ofDo you document how you grant and approveleast privilege, allowing only authorizedaccess to tenant data? Please procedure for doingaccesses for users (or processes acting onthis.behalf of users) which are necessary toDo you have a method of aligning provider andaccomplish assigned tasks in accordance with tenant data classification methodologies fororganizational missions and businessaccess control purposes?functions.Will you share user entitlement remediation andcertification reports with your tenants, ifinappropriate access may have been allowed totenant data?Enforces a limit of 3 consecutive invalid logon Do you allow tenants/customers to defineattempts by a user during a 15 minute period; password and account lockout policies for theiraccounts? Provide system password requirementsand policies.Automatically locks the account/node for aDo you support password (minimum length, age,minimum of a 30 minute period when thehistory, complexity) and account lockout (lockoutmaximum number of unsuccessful attempts is threshold, lockout duration) policy enforcement?exceeded.Please provide policies for both standard andadmin accounts.Password Policy must meet or exceed current Do you support tenant defined passwordpassword policy defined in SEC 501.complexity policies? Specify your password lengthand complexity requirements in the notes field
ATP-1.1ATP-1.2Awareness and Training - Policyand oyment agreements shall incorporateprovisions and/or terms for adherence toestablished information governance andsecurity policies and must be signed by newlyhired or on-boarded workforce personnel(e.g., full or part-time employee or contingentstaff) prior to granting workforce personneluser access to corporate facilities, resources,and assets.ATP-1.4ATP-1.5Audit plans shall be developed andmaintained to address business processdisruptions. Auditing plans shall focus onreviewing the effectiveness of theimplementation of security operations. Allaudit activities must be agreed upon prior toexecuting any audits.AUC-1.1AUC-1.2AUC-1.3Audit and Control -Audit andAccountabilityAUC-1AU-1AUC-1.4Do you document employee acknowledgment oftraining they have completed?Are all personnel required to sign NDA orConfidentiality Agreements as a condition ofemployment to protect customer/tenantinformation?Is successful and timely completion of the trainingprogram considered a prerequisite for acquiringand maintaining access to sensitive systems?Are personnel trained and provided withcustomer defined awareness programs at leastonce a year?Do you produce audit assertions using astructured, industry accepted format (e.g., CloudAudit/A6 URI Ontology, Cloud Trust, SCAP/CYBEX,GRC XML, ISACA's Cloud Computing ManagementAudit/Assurance Program, etc.)?Are your audits performed at least annually? if no,please describe in the comments section.Do you allow tenants to view your SOC2/ISO27001 or similar third-party audit or certificationreports?Do you conduct network penetration tests of yourcloud service infrastructure regularly asprescribed by industry best practices andguidance?AUC-1.5Do you conduct application penetration tests ofyour cloud infrastructure regularly as prescribedby industry best practices and guidance?AUC-1.6Are the results of the penetration tests availableto tenants at their request?AUC-1.7Are the results of internal and external auditsavailable to tenants at their request?AUC-2.1Audit and Control:Audit EventsIndependent reviews and assessments shallbe performed at least annually to ensure thatthe organization addresses nonconformitiesof established policies, standards, procedures,and compliance obligations.Do you specifically train your employees regardingtheir specific role and the information securitycontrols they must fulfill?AUC-2AU-2AUC-2.2An event is any observable occurrence in anorganizational information system.Organizations identify audit events as thoseevents which are significant and relevant tothe security of information systems and theenvironments in which those systems operatein order to meet specific and ongoing auditneeds.Audit events on Web ApplicationsIs the solution capable of auditing the followingevents? Successful and unsuccessful accountlogon events, account management events, objectaccess, policy change, privilege functions, processtracking, and system events.Is the solution capable of auditing the followingevents, for Web applications? All administratoractivity, authentication checks, authorizationchecks, data deletions, data access, data changes,and permission changes.
Audit Review, Analysis, and ReportingAudit and Control:Audit Review, Analysis, andReportingAudit and Control:AUC-3AUC-4AUC-3.1AUC-4.1AU-6Is the solution capable of automated mechanismsto centrally review, analyze and correlate auditand log records from multiple components of thesolution to support organizational processes forinvestigation, alerting and response to suspiciousactivities? is the information available to yourtenants?AU-11Is the solution capable of maintaining all auditrecords in accordance with commonwealth recordretention policies found at the following AA-1.1Control Assessment -1.2CMP-1Risk assessments associated with datagovernance requirements shall be conductedat planned intervals and shall consider thefollowing: Awareness of where sensitive data is storedand transmitted across applications,databases, servers, and networkinfrastructure Compliance with defined retention periodsand end-of-life disposal requirements Data classification and protection fromunauthorized use, access, loss, destruction,and falsificationDo you provide security control health data inorder to allow tenants to implement industrystandard Continuous Monitoring (which allowscontinual tenant validation of your physical andlogical control status)?Organization shall follow a defined qualitychange control and testing process (e.g., ITILService Management) with establishedbaselines, testing, and release standardswhich focus on system availability,confidentiality, and integrity of systems andservicesDo you provide your tenants with documentationthat describes your quality assurance process?The organization develops, documents, andmaintains under configuration control, acurrent baseline configuration of theinformation system.Do you have a capability to continuously monitorand report the compliance of your infrastructureagainst your information security baselines?CM-1CMP-1.3CMP-1.4Configuration Management Policy and 2-COVCM-3CM-3-COVCM-7Do you conduct risk assessments associated withdata governance requirements at least once ayear?Is documentation describing known issues withcertain products/services available?Are there policies and procedures in place totriage and remedy reported bugs and securityvulnerabilities for product and service offerings?Are tenants provided with documentation onremedied issues?Are mechanisms in place to ensure that alldebugging and test code elements are removedfrom released software versions? Are theretechnical controls in place to prevent?Do you have controls in place to restrict andmonitor the installation of unauthorized softwareonto your systems?Can you provide evidence that the proposedsolution adheres to a security baseline, which isbased on least functionality?Are all changes to proposed solution authorizedaccording to change management policies?
CP-1.1CP-1.2CP-1.3CP-1.4Contingency Planning Information System backupCP-1CP-1.5A consistent unified framework for business Do you provide tenants with geographicallycontinuity planning and plan developmentresilient hosting options?shall be established, documented, andadopted to ensure all business continuityDo you provide tenants with infrastructure serviceplans are consistent in addressing prioritiesfailover capability to other providers?for testing, maintenance, and informationsecurity requirements. Requirements forAre business continuity plans subject to test atbusiness continuity plans include theplanned intervals or upon significantfollowing:organizational or environmental changes to Defined purpose and scope, aligned withensure continuing effectiveness?relevant dependencies Accessible to and understood by those who Can the solution provide and maintain a backup ofwill use themcommonwealth data that can be recovered in an Owned by a named person(s) who isorderly and timely manner within a predefinedCP-2responsible for their review, update, andfrequency consistent with recovery time andCP4approvalrecovery point objectives?CP-6 Defined lines of communication, roles, andCP-7responsibilitiesCan the solution store a backup of commonwealthCP-9 Detailed recovery procedures, manual workdata, at least daily, in an off-site “hardened”CP-9-COV around, and reference informationfacility, located within the continental UnitedCP-10 Method for plan invocationStates, maintaining the security of commonwealthSA-9-COVdata?Can the solution partition, in aggregate for thisproposal, all commonwealth data submitted intothe solution by the data owner in such a mannerthat it will not be impacted or forfeited due to Ediscovery, search and seizure or other actions bythird parties obtaining or attempting to obtainrecords, information or commonwealth data forreasons or activities that are not directly relatedto the business of the data owner?CP-1.6Vendor should have An identification andauthentication policy that addresses purpose,scope, roles, responsibilities, managementcommitment, coordination amongorganizational entities, and complianceIDA-1.1Identification and Authentication;Organizational on and Authentication;Authenticator ManagementIDA-2IA-1Does your management provision theauthorization and restrictions for user access (e.g.,employees, contractors, customers (tenants),business partners and/or suppliers) prior to theiraccess to data and any owned or managed(physical and virtual) applications, infrastructuresystems and network components?Do you require at least annual updates andProcedures to facilitate the implementation of reviews of your access policies for all system usersthe identification and authentication policyand administrators (exclusive of users maintainedand associated identification andby your tenants)?authentication controlsInternal agency or customer (tenant) userDo you support use of, or integration with,account credentials shall be restricted as per existing customer-based Single Sign On (SSO)the following, ensuring appropriate identity, solutions to your service?entitlement, and access management and in Do you support identity federation standardsaccordance with established policies and(SAML, SPML, WS-Federation, etc.) as a means ofprocedures:authenticating/authorizing users? Identity trust verification and service-toservice application (API) and informationprocessing interoperability (e.g., SSO andFederation) Account credential lifecycle managementfrom instantiation through revocationIA-2 Account credential and/or identity storeIA-2-COV minimization or re-use when feasibleIA-5 Adherence to industry acceptable and/orregulatory compliant authentication,authorization, and accounting (AAA) rules
IDA-1.3Identification and Authentication;Authenticator ManagementIDA-2IDA-1.4IDA-1.5account credentials shall be restricted as perthe following, ensuring appropriate identity,entitlement, and access management and inaccordance with established policies andprocedures: Identity trust verification and service-toservice application (API) and informationprocessing interoperability (e.g., SSO andFederation) Account credential lifecycle managementfrom instantiation through revocationIA-2 Account credential and/or identity storeIA-2-COV minimization or re-use when feasibleIA-5 Adherence to industry acceptable and/orregulatory compliant authentication,authorization, and accounting (AAA) rules(e.g., strong/multi-factor, expireable, nonshared authentication secrets)IDA-1.6IDA-1.8Identify immediate mitigation procedures,including specific instructions, based oninformation security incident categorizationlevel, on whether or not to shut down ordisconnect affected IT systems.Establishprocedures for information security incident Do you publish a roles and responsibilitiesinvestigation, preservation of evidence, and document specifying what you vs. your tenantsforensic analysis.are responsible for during security incidents?IR-1.1IR-1.2IR-1.3IR-1.4The organization tracks and documentsinformation system security Requires personnel to report suspectedsecurity incidents to the organizationalincident response capability within 24 hoursfrom when the agency discovered or shouldhave discovered their occurrence; andReports security incident information todesignated authorities.MPP-1Do you have a defined and documented incidentnotification process for reporting suspectedsecurity incidents within 24 hours?Does your security information and eventmanagement (SIEM) system merge data sources(app logs, firewall logs, IDS logs, physical accesslogs, etc.) for granular analysis and alerting?Do you maintain liaisons and points of contactwith local authorities in accordance with contractsand appropriate regulations?IR-1.10Media Protection Policy andProcedures:Media SanitizationHave you tested your security incident responseplans in the last year?Do you monitor and quantify the types, volumesand impacts on all information security incidents?Will you share statistical information for securityincident data with your tenants upon request?IR-1.9MPP1.1Do you allow tenants to use third-party identityassurance services?Do you support password (minimum length, age,history, complexity) and account lockout (lockoutthreshold, lockout duration) policy enforcement?Do you support the ability to force passwordchanges upon first logon?Do you have mechanisms in place for unlockingaccounts that have been locked out (e.g., selfservice via email, defined challenge questions,manual unlock)?Do you have a documented security incidentresponse plan?Do you integrate customized tenant requirementsinto your security incident response plans?IDA-1.7Incident ResponseDo you have an identity management system(enabling classification of data for a tenant) inplace to enable both role-based and contextbased entitlement to data?Do you provide tenants with strong (multifactor)authentication options (digital certs, tokens,biometrics, etc.) for user access?Policies and procedures shall be establishedwith supporting business processes andtechnical measures implemented for theMP-6 secure disposal and complete removal of dataMP-6-COV from all storage media, ensuring data is notrecoverable by any computer forensic means.Do you enforce and attest to tenant dataseparation when producing data in response tolegal subpoenas?Do you support secure deletion (e.g.,degaussing/cryptographic wiping) of archived andbacked-up data as determined by the tenant?
Media Protection Policy andProcedures:Media SanitizationMPP-1MPP1.2Physical and EnvironmentalProtection: Physical AccessAuthorizationsPEP-1PEP-1.1Policies and procedures shall be establishedwith supporting business processes andtechnical measures implemented for theMP-6 secure disposal and complete removal of dataDoes supplier meet all data disposal requirementsMP-6-COV from all storage media, ensuring data is notrecoverable by any computer forensic means. as outlined in the current Removal ofCommonwealth Data from Electronic MediaStandard (SEC514-04)?PE-2(1)PE-2(3)PEP-2.1Physical and EnvironmentalProtection:Physical Access al and EnvironmentalProtection:Physical stem and Information Integrity:Vulnerability / PatchManagement (Flaw Remediation)SII-1SII-1.3SII-1.4SII-1.5The organization authorizes physical access to Can you provide a published procedure for exitingthe facility where the information systemthe service arrangement, including assurance toresides based on position or role.sanitize all computing resources of tenant dataonce a customer has exited your environment orhas vacated a resource?Ingress and egress points such as serviceareas and other points where unauthorizedpersonnel may enter the premises shall bemonitored, controlled and, if possible, isolatedfrom data storage and processing facilities toprevent unauthorized data corruption,compromise, and loss.Do you restrict physical access to informationassets and functions by users and supportpersonnel?Are ingress and egress points, such as serviceareas and other points where unauthorizedpersonnel may enter the premises, monitored,controlled and isolated from data storage andprocess?All information system components andDo you allow tenants to define acceptableservices remain within the continental United geographical locations for data routing orStates.resource instantiation?Can you provide the physical geographicalAll physical components associated with anlocation of the storage in advance for a tenantsinformation system or service classified asdata?sensitive with respect to confidentiality orCan you provide the physical geographicalintegrity must be housed within the samelocation of a tenants data upon request?storage location dedicated for the exclusivePE-18-COV use of the organization and are clearlyCan you ensure that data does not migrateSA-9-COV- marked.beyond a defined geographical residency?1Each hypervisor can only host one tier of theapplication architecture and no hypervisorDo you have the capability to restrict the storagemay host the application interface and theof customer data to specific countries ordata storage component for any information geographic locations?system, even if the components in questiondo not interact within the same information Does the solution have the capability to setsystem.affinity on tiered systems, no one hypervisor canhost the application and the data storage?Policies and procedures shall be established,and supporting processes and technicalmeasures implemented, for timely detectionof vulnerabilities within organizationallyowned or managed applications,infrastructure network and systemcomponents (e.g., network vulnerabilityassessment, penetration testing) to ensureSI-2the efficiency of implemented securityRA-5controls. A risk-based model for prioritizingRA-5-COVremediation of identified vulnerabilities shallbe used. Changes shall be managed through achange management process for all vendorsupplied patches, configuration changes, orchanges to the organization's internallydeveloped software. Upon request, theprovider informs customer (tenant) of policiesand procedures and identified weaknessesespecially if customer (tenant) data is used asDo you conduct network-layer vulnerability scansregularly as prescribed by industry best practices?Provide the frequency.Do you conduct application-layer vulnerabilityscans regularly as prescribed by industry bestpractices? Provide the frequencyDo you conduct local operating system-layervulnerability scans regularly as prescribed byindustry best practices? Provide the frequencyWill you make the results of vulnerability scansavailable to tenants at their request?Do you have a capability to rapidly patchvulnerabilities across all of your computingdevices, applications and systems?
Vulnerability / PatchManagement (Flaw Remediation)SII-1SII-1.6SII-2.1System and Information Integrity:Malicious Code protectioncontrols. A risk-based model for prioritizingremediation of identified vulnerabilities shallbe used. Changes shall be managed through achange management process for all vendorsupplied patches, configuration changes, orchanges to the organization's internallydeveloped software. Upon request, theprovider informs customer (tenant) of policies Will you provide your risk-based systems patchingand procedures and identified weaknessestime frames to your tenants upon request?especially if customer (tenant) data is used asDoes the provider ensure that they will utilizeindustry standard malware protection,Policies and procedures shall be established, incorporating both signature and non-signatureand supporting business processes andbased detection mechanisms, on all systems withtechnical measures implemented, to prevent access to commonwealth data?SI-3the execution of malware on organizationallySI-3-COV owned or managed user end-point devicesDoes the provider ensure that malware protection(i.e., issued workstations, laptops, and mobile will be centrally managed and receive regulardevices) and IT infrastructure network andautomatic updates to malicious code protectionsystems components.mechanisms and data files from the softwareRA-5-COVSII-2SII-2.1vendor?SCP-01.1System and CommunicationsProtection:Boundary 3System and P-02.5SCP-3.1SCP-3.2SCP-3.3Systems and CommunicationProtection; Cryptographic KeySCP-3Establishment and ManagementSC-1SC-8SC-8-COVSC-23SC-28Policies and procedures shall be established,and supporting business processes andtechnical measures implemented, for the useof encryption protocols for protection ofsensitive data in storage (e.g., databases) anddata in transmission (e.g., system interfaces,over public networks, and electronicmessaging) as per applicable legal, statutory,and regulatory compliance obligations.Does the provider ensure that the solution willutilize industry standard firewalls regulating alldata entering the internal data network from anyexternal source which will enforce secureconnections between internal and externalsystems and will permit only authorized data topass through?Does the offeror ensure that external connectionsincorporated into the solution have appropriatesecurity controls including industry standardintrusion detection and countermeasures that willdetect and terminate any unauthorized activityprior to entering the firewall maintained byofferor?Do you encrypt tenant data at rest (ondisk/storage) within your environment?Do you use encryption for storing and transmittingemail attachments?Do you leverage encryption to protect data andvirtual machine images during transport acrossand between networks and hypervisor instances?Do you support tenant-generated encryption keysor permit tenants to encrypt data to an identitywithout access to a public key certificate (e.g.,identity-based encryption)?Do you have documentation establishing anddefining your encryption management policies,procedures and guidelines?The organization establishes and managesDo you have platform and data appropriatecryptographic keys for required cryptography encryption that uses open/validated formats andemployed within the information system instandard algorithms?accordance with the organization-definedDo you support encryption keys being solelyrequirements for key generation, distribution, maintained by the cloud consumer or a trustedstorage, access, and destruction. Platformkey management provider?and data appropriate encryption (e.g., AESDo you store encryption keys in the cloud?SC-12 256) in open/validated formats and standardSC-12-COV algorithms shall
in order to meet specific and ongoing audit needs. Is the solution capable of auditing the following events? Successful and unsuccessful account logon events, account management events, object access, policy change, privilege functions, process tracking, and system events. AUC-2.2 Audit events on Web Applications











