Transcription
HITRUST CSF 101: Fast FactsHITRUST CSF & HIPAAHITRUST CSF & NISTHITRUST CSF v9.3Achieving HITRUST CSF Certification2
3
4
5
PrescriptiveFrameworkCross-Referencedto Regulations6PrescriptiveControlsOne Audit–One ReportReducesComplexityProtectsBrand
Built on ISO 27001HITRUST CSF organization14 ControlCategories across19 domains49 ControlObjectivesIntegrates other standards7HIPAA23 NYCRR 500MARS-E RequirementsCIS Critical SecurityControls v6FISMA ComplianceEU GDPRFTC Red Flag RulesPDPAPCI ComplianceAnd more 156 ControlSpecifications
CSF Control Category8ControlSpecificationsRequired ForHITRUST CSFCertification0Information Security Management Program111Access Control25162Human Resources Security953Risk Management434Security Policy225Organization of Information Security1156Compliance1057Asset Management528Physical & Environmental Security1349Communications & Operations Management321910Information Systems Acquisition, Development & Maintenance13711Information Security Incident Management5312Business Continuity Management5313Privacy Practices2115675
9
10116 CFR Part 68112 DHS CRR v1.12201 CMR 17.0013 EHNAC3AICPA TSP 1004APEC14 21 CFR Part 1115 EU GDPR5CCPA16 OCR Guidance for Unsecured PHI6CAQH Core Phase 117 FFIEC IS7CAQH Core Phase 218 FedRAMP8CIS Controls v7.19CSA CCM v3.0.110 CMS ARS v3.119 HITRUST De-ID Framework v120 45 CFR Part 164, HIPAA General Provisions21 45 CFR Part 164, HIPAA Security Rule11 COBIT 522 45 CFR Part 164, HIPAA Breach Notification Rule00
23 45 CFR Part 164, HIPAA Privacy Rule34 NIST SP 800-53 R424 IRS Publication 1075 v201635 NIST SP 800-12225 ISO/IEC 27001:201326 ISO/IEC 27002:201336 NIST SP 800-171 R2 (DFARS)37 NRS 603A27 ISO/IEC 27799:201638 OCR Audit Protocol (2016)39 OECD Privacy00Framework28 ISO/IEC 29100:20110029 ISO/IEC 29151:201730 Joint Commission Standards31 MARS-E v2.01140 PCI DSS v3.2.141 PDPA32 23 NYCRR Part 50042 PMI DSP Framework v1.043 SCIDSA 465533 NIST Cybersecurity Framework v1.144 1 TAC 15 390.2
12
13
14#HIPAA Privacy RuleHITRUST CSF v9.31.§164.502(a)Uses and Disclosures – General Rules STD2.§164.502(a)(2)Covered entities: Required disclosures STD13.k Use and Disclosure3.§164.502(a)(4)Business associates: Permitted uses and disclosures STD13.k Use and Disclosure4.§164.502(a)(4)Business associates: Required uses and disclosures13.k Use and Disclosure5.§164.502(a)(5)Prohibited uses and disclosures6.§164.502(f)Deceased Individuals STD06.c Protection of Organizational Records7.§164.502(g)13.e Choice8.§164.502(j)(1)Disclosures by whistleblowers13.k Use and Disclosure9.§164.502(j)(2)Disclosures by workforce members who are victims of a crime13.k Use and Disclosure13.f Principal Access13.k Use and Disclosure13.j Data Minimization13.k Use and Disclosure
#HIPAA Security RuleHITRUST CSF v9.3Administrative Safeguards00.a Information Security Management Program02.a Roles and Responsibilities1.§164.308(a)(1)(i)Security ManagementProcess03.a Risk Management Program Development05.a Management Commitment to Information Security05.h Independent Review of Information Security09.t Exchange Agreements03.b Performing Risk Assessments2.164.308(a)(2)Assigned SecurityResponsibility05.a Management Commitment to Information Security05.c Allocation of Information Security Responsibilities05.d Authorization Process for Information Assets and Facilities06.g Compliance with Security Policies and Standards15
#HITRUST CSF v9.31.§164.40203.b Performing Risk Assessments§164.404(a)(1)General rule STD11.a Reporting Information Security Events2.11.c Responsibilities and Procedures§164.404(a)(2)Breaches treated as discovered STD§164.404(b)Implementation specification: Timeliness ofnotification SPEC05.k Addressing Security in Third Party Agreements5.§164.404(c)(1)Elements SPEC11.a Reporting Information Security Events6.§164.404(c)(2)Plain language requirement SPEC11.a Reporting Information Security Events7.§164.404(c)(3)11.a Reporting Information Security Events8.§164.404(d)(1)Written notice SPEC11.a Reporting Information Security Events9.§164.404(d)(2)Substitute notice SPEC11.a Reporting Information Security Events10.§164.404(d)(3)Additional notice in urgent situations SPEC11.a Reporting Information Security Events3.4.16HIPAA Breach Notification Rule11.a Reporting Information Security Events11.a Reporting Information Security Events
OrganizationFactors17System FactorsRegulatoryFactors
Four types of HITRUST AssessmentsHITRUST CSFSecurity AssessmentHITRUST CSFPrivacy and SecurityAssessmentHITRUST CSFComprehensiveSecurity AssessmentHITRUST CSFComprehensivePrivacy and SecurityAssessmentAll incorporate NIST Cybersecurity FrameworkNIST Cybersecurity Framework Certification with HITRUST CSF CertificationDetermined as part of scoping process18
1.0 Access ControlAutomatically remove or disable accounts thathave been inactive for a period of sixty (60)days or more. (01.b) (Level 1)09.0 Communications and OperationsManagementThe firewall and router rule sets shall be reviewed atleast every six (6) months. (09.m) (Level 3).03.0 Risk ManagementRepeating the risk management process prior to anysignificant change, after a serious incident, whenevera new significant risk factor is identified, or at aminimum annually. (03.a) (Level 1)07.0 Asset ManagementRecords of property assigned to employees shall bereviewed and updated annually. (07.a) (Level 1)11.0 Information SecurityIncident Management19The incident management plan is reviewed andupdated annually (11.c) (Level 2)Perform quarterly scans for unauthorized wirelessaccess points and take appropriate action if anyaccess points are discovered. (09.m) (Level 2)12.01 Information Security Aspects ofBusiness Continuity ManagementResponsibilities are assigned for regular reviews ofat least a part of the business continuity plan, at aminimum, annually. (12.e) (Level 1)
Baseline ID: 0707.10b2System.1RequirementStatementApplications that store, process or transmit covered information undergo automated applicationvulnerability testing by a qualified party on an annual basis.PolicyReview policies relatedto input validation inapplications.20ProcessDetermine if theprocedures address allthe required elementsof the policy.ImplementationMeasuredManagedExamine the mostrecent applicationvulnerability test anddetermine if it wasperformed within thepast twelve (12)months by a qualifiedparty.Measure the effectivenessof the implementedcontrols and tovulnerability testing by aqualified party on anannual basis.Determine if ad hocprocesses forinvestigation andresolution exist and ifdeviations occurredand were corrected.
21
22
23
#NIST Cybersecurity Framework v1.1Identify (ID)ID.AM-1Physical devices and systems within the1.organization are inventoried.2.ID.AM-2Software platforms and applications withinthe organization are inventoried.HITRUST CSF v9.307.a Inventory of Assets07.d Classification Guidelines01.l Remote Diagnostic and Configuration Port Protection07.a Inventory of Assets07.d Classification Guidelines01.l Remote Diagnostic and Configuration Port Protection01.m Segregation in NetworksID.AM-3Organizational communication and dataflows are mapped.01.o Network Routing Control01.i Policy on the Use of Network Services4.ID.AM-4External information systems arecatalogued.01.a Access Control Policy5.ID.AM-5Resources (e.g., hardware, devices, data,time, personnel, and software) areprioritized based on their classification,criticality, and business value.3.2405.i Identification of Risks Related to External Parties09.m Network Controls09.n Security of Network Services09.e Service Delivery09.n Security of Network Services01.w Sensitive System Isolation06.c Protection of Organizational Records07.a Inventory of Assets
25
HITRUST CSF v9.3 incorporates and harmonizes 44 authoritative sources,added one new data privacy-related and two new security-relatedauthoritative sources, as well as updated six existing sources. HITRUST CSF v9.3 updates include:o CCPA – requiring qualifying organizations to protect consumer data in specificways as well as that consumers be able to opt-out sharing of their data.o The South Carolina Insurance Data Security Act 2018 (SCIDSA) – requiringqualifying organizations have a comprehensive information security programand the reporting of cybersecurity events.o NIST SP 800-171 R2 (DFARS) – providing guidance on protecting ControlledUnclassified Information (CUI) in non-federal systems and organizations.26
o Updating various authoritative sources to latest versions, specifically: AICPA 2017 CIS CSC v7.1 ISO 27799:2016 CMS/ARS v3.1 IRS Publication 1075 2016 NIST Cybersecurity Framework v1.1o Establish and prioritize solutions that address root-cause issues tomitigate system vulnerabilities. Further enhancements include:o Updates to the glossary to better clarify terms found in the HITRUST CSF.o Adjusted authoritative source mappings to more fully harmonize requirementsacross industries and sectors.27
28
29
30
Key FactsEffective January 1, 2020.Enforced July 1, 2020.Privacy rights for California residents.Grants new enforcement power to theAttorney General.GivesOwnershipGivesSecurity31GivesControl
32
33
34
35
36
Learning ObjectivesExamine the fundamentals of the HITRUST CSF.Leveraging the HITRUST CSF to implement the NIST CybersecurityFramework.Addressing regulatory mandates such as GDPR, HIPAA, and FISMA.Getting organized: From a Readiness-Assessment, through a ValidatedAssessment to Certification.Roadmap to HITRUST CSF and NIST certification.Delivered On-Site!37
38
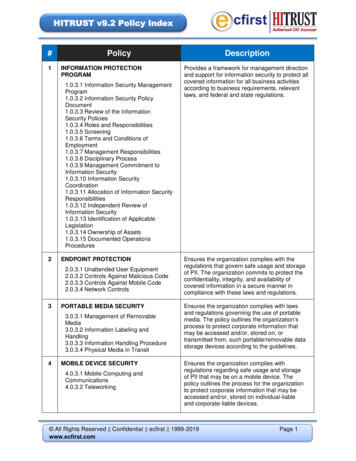
8 0 Information Security Management Program 1 Access Control 2 Human Resources Security 3 Risk Management 4 Security Policy 5 Organization of Information Security 6 Compliance 7 Asset Management 8 Physical & Environmental Security 9 Communications & Operations Management 10 Information Systems Acquisition, Development & Maintenance 11 Information Security Incident Management