Transcription
FRAMEWORK MAPPINGHITRUST CSF V9 TO ISO 27001/27002:2013Visit us online at Flank.org to learn more.
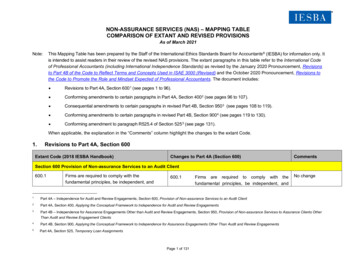
HITRUST CSF v9 FrameworkISO 27001/27002:2013FrameworkFLANK ISO 27001/27002:2013Documentation from ISO our all-in-one toolkit04.a Information Security Policy Document05.a Management Commitment to Information SecurityISO/IEC 27002:2013 5.1.15.1.1 - Policies for Information Security Policy and Procedures(5 pages)04.b Review of the Information Security PolicyISO/IEC 27002:2013 5.1.25.1.2 - Review of the Policies for Information Security Policy andProcedures (5 pages)02.a Roles and Responsibilities02.g Termination or Change Responsibilities05.c Allocation of Information Security ResponsibilitiesISO/IEC 27002:2013 6.1.16.1.1 - Information Security Roles and Responsibilities Policy andProcedures (5 pages)09.c Segregation of DutiesISO/IEC 27002:2013 6.1.26.1.2 - Segregation of Duties Policy andProcedures (5 pages)05.c Allocation of Information Security Responsibilities05.f Contact with AuthoritiesISO/IEC 27002:2013 6.1.36.1.3 - Contact with Authorities Policy and Procedures (4 pages)05.g Contact with Special Interest Groups06.a Identification of Applicable LegislationISO/IEC 27002:2013 6.1.46.1.4 - Contact with Special Interest Groups Policy and Procedures(4 pages)01.x Mobile Computing and Communications01.y Teleworking08.k Security of Equipment Off-PremisesISO/IEC 27002:2013 6.2.16.2.1 - Mobile Device Policy and Procedures (6 pages)01.y Teleworking08.k Security of Equipment Off-PremisesISO/IEC 27002:2013 6.2.26.2.2 - Teleworking Policy and Procedures(8 pages)02.b Screening05.k Addressing Security in Third Party AgreementsISO/IEC 27002:2013 7.1.102.a Roles and Responsibilities02.c Terms and Conditions of EmploymentISO/IEC 27002:2013 7.1.27.1.2 - Terms of Conditions and Employment Policy and Procedures(4 pages)02.d Management Responsibilities11.a Reporting Information Security EventsISO/IEC 27002:2013 7.2.17.2.1 - Management Responsibilities Policy and Procedures(4 pages)27.1.1 - Employee and Contractor Screening Policy and Procedures(5 pages)
01.p Secure Log-on Procedures02.e Information Security Awareness,Education, and Training06.a Identification of Applicable Legislation11.a Reporting Information Security EventsISO/IEC 27002:2013 7.2.27.2.2 - Information Security Awareness, Education and TrainingPolicy and Procedures (8 pages)02.f Disciplinary ProcessISO/IEC 27002:2013 7.2.37.2.3 - Information Security Sanction & Disciplinary Process Policyand Procedures – Personal Data (EU) (6 pages)7.2.3 - Information Security Sanction & Disciplinary Process Policyand Procedures – Personally Identifiable Information (PII) (7 pages)02.g Termination or Change ResponsibilitiesISO/IEC 27002:2013 7.3.17.3.1 - Termination/Change of Employment Responsibilities Policyand Procedures (4 pages)07.a Inventory of Assets07.d Classification GuidelinesISO/IEC 27002:2013 8.1.18.1.1 - 8.1.2 - Inventory and Ownership of Assets Policy andProcedures (4 pages)07.b Ownership of Assets07.d Classification GuidelinesISO/IEC 27002:2013 8.1.28.1.1 - 8.1.2 - Inventory and Ownership of Assets Policy andProcedures (4 pages)07.c Acceptable Use of AssetsISO/IEC 27002:2013 8.1.38.1.3 - Information System Usage Policy and Procedures (5 pages)8.1.3 - Internet Usage Policy and Procedures(5 pages)8.1.3 - Laptop Usage Policy and Procedures(6 pages)8.1.3 - Software Usage Policy and Procedures(6 pages)02.h Return of AssetsISO/IEC 27002:2013 8.1.48.1.4 - Return of Assets Policy and Procedures (4 pages)06.c Protection of Organizational Records07.d Classification GuidelinesISO/IEC 27002:2013 8.2.18.2.1 - 8.2.3 - Data and Information Classification Policy andProcedures (18 pages)07.e Information Labeling and HandlingISO/IEC 27002:2013 8.2.28.2.1 - 8.2.3 - Data and Information Classification Policy andProcedures (18 pages)01.h Clear Desk and Clear Screen Policy07.e Information Labeling and Handling09.q Information Handling ProceduresISO/IEC 27002:2013 8.2.38.2.1 - 8.2.3 - Data and Information Classification Policy andProcedures (18 pages)3
09.o Management of Removable MediaISO/IEC 27002:2013 8.3.18.3.1 - 8.3.3 - Removable Media Policy and Procedures (7 pages)09.p Disposal of MediaISO/IEC 27002:2013 8.3.28.3.1 - 8.3.3 - Removable Media Policy and Procedures (7 pages)09.u Physical Media in TransitISO/IEC 27002:2013 8.3.38.3.1 - 8.3.3 - Removable Media Policy and Procedures (7 pages)01.a Access Control Policy01.c Privilege ManagementISO/IEC 27002:2013 9.1.19.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.a Access Control Policy01.i Policy on the Use of Network ServicesISO/IEC 27002:2013 9.1.29.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)08.d Protecting Against External andEnvironmental ThreatsISO/IEC 27002:2013 9.1.49.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.a Access Control Policy01.b User Registration01.q User Identification and AuthenticationISO/IEC 27002:2013 9.2.19.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.a Access Control Policy01.b User RegistrationISO/IEC 27002:2013 9.2.29.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.a Access Control Policy01.c Privilege Management01.q User Identification and AuthenticationISO/IEC 27002:2013 9.2.39.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.d User Password Management01.r Password Management SystemISO/IEC 27002:2013 9.2.49.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.e Review of User Access Rights02.g Termination or Change ResponsibilitiesISO/IEC 27002:2013 9.2.59.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)02.g Termination or Change Responsibilities02.i Removal of Access RightsISO/IEC 27002:2013 9.2.69.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.d User Password Management01.f Password UseISO/IEC 27002:2013 9.3.19.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.v Information Access RestrictionISO/IEC 27002:2013 9.4.19.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.d User Password Management01.p Secure Log-on Procedures01.t Session Time-out01.u Limitation of Connection TimeISO/IEC 27002:2013 9.4.29.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.d User Password Management01.r Password Management SystemISO/IEC 27002:2013 9.4.39.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)01.s Use of System UtilitiesISO/IEC 27002:2013 9.4.49.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)4
10.j Access Control to Program Source CodeISO/IEC 27002:2013 9.4.59.1 - 9.4.5 - Access Control Policy and Procedures (22 pages)10.d Message Integrity10.f Policy on the Use of Cryptographic ControlsISO/IEC 27002:2013 10.1.110.1.1 - 10.1.2 - Cryptography Policy and Procedures (17 pages)10.g Key ManagementISO/IEC 27002:2013 10.1.210.1.1 - 10.1.2 - Cryptography Policy and Procedures (17 pages)09.o Management of Removable MediaISO/IEC 27002:2013 10.7.18.3.1 - 8.3.3 - Removable Media Policy and Procedures (7 pages)08.a Physical Security Perimeter08.b Physical Entry ControlsISO/IEC 27002:2013 11.1.111.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.b Physical Entry ControlsISO/IEC 27002:2013 11.1.211.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.c Securing Offices, Rooms, and FacilitiesISO/IEC 27002:2013 11.1.311.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.d Protecting Against External andEnvironmental Threats08.g Equipment Siting and ProtectionISO/IEC 27002:2013 11.1.411.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.e Working in Secure AreasISO/IEC 27002:2013 11.1.511.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.f Public Access, Delivery, and Loading AreasISO/IEC 27002:2013 11.1.611.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.g Equipment Siting and Protection08.h Supporting Utilities08.h Supporting UtilitiesISO/IEC 27002:2013 11.2.111.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)12.c Developing and Implementing Continuity PlansIncluding Information SecurityISO/IEC 27002:2013 11.2.211.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.i Cabling SecurityISO/IEC 27002:2013 11.2.311.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.h Supporting Utilities08.j Equipment MaintenanceISO/IEC 27002:2013 11.2.411.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.m Removal of PropertyISO/IEC 27002:2013 11.2.511.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.a Physical Security Perimeter08.k Security of Equipment Off-PremisesISO/IEC 27002:2013 11.2.611.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)08.l Secure Disposal or Re-Use of EquipmentISO/IEC 27002:2013 11.2.711.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)5
01.g Unattended User EquipmentISO/IEC 27002:2013 11.2.811.1.1 - 11.2.8 - Physical and Environmental Security Policy andProcedures (16 pages)01.h Clear Desk and Clear Screen PolicyISO/IEC 27002:2013 11.2.911.2.9 - Clear Desk and Clear Screen Policy and Procedures(5 pages)09.a Documented Operations ProceduresISO/IEC 27002:2013 12.1.112.1.1 - Documented Operating Policy and Procedures (4 pages)03.d Risk Evaluation09.b Change Management09.d Separation of Development, Test, andOperational EnvironmentsISO/IEC 27002:2013 12.1.212.1.2 - Change Management Policy and Procedures (13 pages)09.h Capacity ManagementISO/IEC 27002:2013 12.1.312.1.3 - Capacity Management Plan Policy and Procedures(6 pages)09.d Separation of Development, Test, andOperational EnvironmentsISO/IEC 27002:2013 12.1.412.1.4 - Separation of Development, Testing, and OperationalEnvironments Policy and Procedures (6 pages)09.j Controls Against Malicious Code09.k Controls Against Mobile CodeISO/IEC 27002:2013 12.2.112.2.1 - Malware Policy and Procedures (9 pages)09.l Back-upISO/IEC 27002:2013 12.3.112.3.1 - Information Backup Policy and Procedures (10 pages)09.aa Audit Logging09.ab Monitoring System Use09.ad Administrator and Operator Logs09.ae Fault LoggingISO/IEC 27002:2013 12.4.112.4.1 - 12.4.3 - Logging and Monitoring Policy and Procedures(10 pages)09.aa Audit Logging09.ac Protection of Log InformationISO/IEC 27002:2013 12.4.212.4.1 - 12.4.3 - Logging and Monitoring Policy and Procedures(10 pages)09.aa Audit Logging09.ac Protection of Log Information09.ad Administrator and Operator LogsISO/IEC 27002:2013 12.4.312.4.1 - 12.4.3 - Logging and Monitoring Policy and Procedures(10 pages)09.af Clock SynchronizationISO/IEC 27002:2013 12.4.412.4.4 - Clock Synchronization Policy and Procedures (4 pages)09.k Controls Against Mobile Code10.h Control of Operational SoftwareISO/IEC 27002:2013 12.5.112.5.1 - Installation of Software Policy and Procedures (5 pages)03.b Performing Risk Assessments03.c Risk Mitigation10.m Control of Technical VulnerabilitiesISO/IEC 27002:2013 12.6.112.6.1 - Vulnerability Management Policy and Procedures (21pages)09.j Controls Against Malicious CodeISO/IEC 27002:2013 12.6.212.6.2 - Software Usage Policy and Procedures (6 pages)03.c Risk Mitigation06.i Information Systems Audit Controls06.j Protection of Information Systems Audit ToolsISO/IEC 27002:2013 12.7.112.7.1 - Information System Audit Controls Policy and Procedures(5 pages)6
09.m Network ControlsISO/IEC 27002:2013 13.1.113.1.1 - Network Controls Policy and Procedures (5 pages)09.f Monitoring and Review of Third Party Services09.m Network Controls09.n Security of Network ServicesISO/IEC 27002:2013 13.1.213.1.2 - Security of Network Services Policy and Procedures (4pages)01.m Segregation in Networks01.o Network Routing Control09.m Network Controls09.w Interconnected Business Information SystemsISO/IEC 27002:2013 13.1.313.1.3 - Segregation in Networks Policy and Procedures (5 pages)09.s Information Exchange Policies and ProceduresISO/IEC 27002:2013 13.2.113.2.1 - Information Transfer Policy and Procedures (6 pages)09.t Exchange AgreementsISO/IEC 27002:2013 13.2.213.2.2 - Agreements on Information Transfer Policy and Procedures(6 pages)09.v Electronic MessagingISO/IEC 27002:2013 13.2.313.2.3 - Electronic Mail (E-Mail) and Electronic Messaging Policyand Procedures (6 pages)05.e Confidentiality AgreementsISO/IEC 27002:2013 13.2.413.2.4 - Confidentiality/Non-Disclosure Agreements Policy andProcedures (4 pages)10.a Security Requirements Analysis andSpecificationISO/IEC 27002:2013 14.1.114.1.1 - 14.3.1 - System Acquisition,Development, and Maintenance Policy and Procedures (16 pages)05.j Addressing Security When Dealing withCustomers09.x Electronic Commerce Services09.z Publicly Available InformationISO/IEC 27002:2013 14.1.214.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)09.y On-line TransactionsISO/IEC 27002:2013 14.1.314.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.a Security Requirements Analysis andSpecificationISO/IEC 27002:2013 14.2.114.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)09.i System Acceptance10.k Change Control ProceduresISO/IEC 27002:2013 14.2.214.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.k Change Control ProceduresISO/IEC 27002:2013 14.2.314.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.k Change Control ProceduresISO/IEC 27002:2013 14.2.414.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.a Security Requirements Analysis andSpecification10.e Output Data ValidationISO/IEC 27002:2013 14.2.514.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.a Security Requirements Analysis andSpecification10.k Change Control ProceduresISO/IEC 27002:2013 14.2.614.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)7
10.k Change Control Procedures10.l Outsourced Software DevelopmentISO/IEC 27002:2013 14.2.714.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.a Security Requirements Analysis andSpecificationISO/IEC 27002:2013 14.2.814.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)09.i System AcceptanceISO/IEC 27002:2013 14.2.914.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)10.i Protection of System Test DataISO/IEC 27002:2013 14.3.114.1.1 - 14.3.1 - System Acquisition, Development, andMaintenance Policy and Procedures (16 pages)05.i Identification of Risks Related to ExternalParties05.k Addressing Security in Third PartyAgreements09.e Service DeliveryISO/IEC 27002:2013 15.1.115.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)05.i Identification of Risks Related to ExternalParties05.k Addressing Security in Third PartyAgreementsISO/IEC 27002:2013 15.1.215.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)05.i Identification of Risks Related to ExternalParties05.k Addressing Security in Third PartyAgreementsISO/IEC 27002:2013 15.1.315.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)ISO/IEC 27002:2013 15.215.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)09.e Service Delivery09.f Monitoring and Review of Third PartyServicesISO/IEC 27002:2013 15.2.115.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)09.g Managing Changes to Third Party ServicesISO/IEC 27002:2013 15.2.215.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)11.a Reporting Information Security Events11.c Responsibilities and Procedures11.e Collection of EvidenceISO/IEC 27002:2013 16.1.115.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)11.a Reporting Information Security EventsISO/IEC 27002:2013 16.1.215.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)11.a Reporting Information Security Events11.b Reporting Security Weaknesses11.c Responsibilities and ProceduresISO/IEC 27002:2013 16.1.315.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)11.a Reporting Information Security EventsISO/IEC 27002:2013 16.1.415.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)09.l Back-up8
11.c Responsibilities and ProceduresISO/IEC 27002:2013 16.1.515.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)11.a Reporting Information Security Events11.c Responsibilities and Procedures11.d Learning from Information Security IncidentsISO/IEC 27002:2013 16.1.615.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)07.e Information Labeling and Handling11.e Collection of EvidenceISO/IEC 27002:2013 16.1.715.1.1 – 15.2.2 - Supplier Relationships (Third-Party Due Diligence& Vendor Management Program (52 pages)03.b Performing Risk Assessments03.c Risk Mitigation12.b Business Continuity and Risk AssessmentISO/IEC 27002:2013 17.1.117.1 - 17.2.1 - Business Continuity and Disaster Recovery Planning(BCDRP) Policy and Procedures (44 pages)12.a Including Information Security in the BusinessContinuity Management Process12.b Business Continuity and Risk Assessment12.c Developing and Implementing Continuity PlansIncluding Information Security12.d Business Continuity Planning FrameworkISO/IEC 27002:2013 17.1.217.1 - 17.2.1 - Business Continuity and Disaster Recovery Planning(BCDRP) Policy and Procedures (44 pages)12.e Testing, Maintaining and Re-Assessing BusinessContinuity PlansISO/IEC 27002:2013 17.1.317.1 - 17.2.1 - Business Continuity and Disaster Recovery Planning(BCDRP) Policy and Procedures (44 pages)10.a Security Requirements Analysis andSpecificationISO/IEC 27002:2013 17.2.117.1 - 17.2.1 - Business Continuity and Disaster Recovery Planning(BCDRP) Policy and Procedures (44 pages)06.a Identification of Applicable Legislation06.f Regulation of Cryptographic ControlsISO/IEC 27002:2013 18.1.118.1.1 – Identification of Applicable Legislation and ContractualRequirements Policy and Procedures (4 pages)06.b Intellectual Property Rights06.f Regulation of Cryptographic ControlsISO/IEC 27002:2013 18.1.218.1.2 – Intellectual Property Rights Policy and Procedures (5pages)06.c Protection of Organizational Records06.d Data Protection and Privacy of CoveredInformation06.f Regulation of Cryptographic Controls09.l Back-upISO/IEC 27002:2013 18.1.318.1.3 - Data Retention, Disposal, and Protection of Records Policyand Procedures (10 pages)06.d Data Protection and Privacy of CoveredInformation06.f Regulation of Cryptographic ControlsISO/IEC 27002:2013 18.1.418.1.4 - Personally Identifiable Information (PII) Policy andProcedures (11 pages)06.f Regulation of Cryptographic ControlsISO/IEC 27002:2013 18.1.518.1.5 - Regulation of Cryptographic Controls Policy andProcedures (4 pages)05.a Management Commitment to InformationSecurity05.h Independent Review of Information SecurityISO/IEC 27002:2013 18.2.118.2.1 - Independent Review of Information Security Policy andProcedures (5 pages)9
06.g Compliance with Security Policies andStandards06.h Technical Compliance CheckingISO/IEC 27002:2013 18.2.218.2.2 - Compliance with Security Policies and Standards Policyand Procedures (
HITRUST CSF v9 Framework 04.a Information Security Policy Document 05.a Management Commitment to Information Security 04.b Review of the Information Security Policy 02.a Roles and Responsibilities 02.g Termination or Change Responsibilities 05.c Allocation of Informa