Transcription
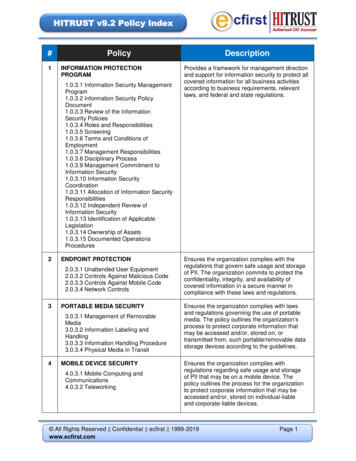
HITRUST v9.2 Policy Index#1PolicyINFORMATION PROTECTIONPROGRAM1.0.3.1 Information Security ManagementProgram1.0.3.2 Information Security PolicyDocument1.0.3.3 Review of the InformationSecurity Policies1.0.3.4 Roles and Responsibilities1.0.3.5 Screening1.0.3.6 Terms and Conditions ofEmployment1.0.3.7 Management Responsibilities1.0.3.8 Disciplinary Process1.0.3.9 Management Commitment toInformation Security1.0.3.10 Information SecurityCoordination1.0.3.11 Allocation of Information SecurityResponsibilities1.0.3.12 Independent Review ofInformation Security1.0.3.13 Identification of ApplicableLegislation1.0.3.14 Ownership of Assets1.0.3.15 Documented OperationsProcedures2ENDPOINT PROTECTION2.0.3.1 Unattended User Equipment2.0.3.2 Controls Against Malicious Code2.0.3.3 Controls Against Mobile Code2.0.3.4 Network Controls3PORTABLE MEDIA SECURITY3.0.3.1 Management of RemovableMedia3.0.3.2 Information Labeling andHandling3.0.3.3 Information Handling Procedure3.0.3.4 Physical Media in Transit4MOBILE DEVICE SECURITY4.0.3.1 Mobile Computing andCommunications4.0.3.2 TeleworkingDescriptionProvides a framework for management directionand support for information security to protect allcovered information for all business activitiesaccording to business requirements, relevantlaws, and federal and state regulations.Ensures the organization complies with theregulations that govern safe usage and storageof PII. The organization commits to protect theconfidentiality, integrity, and availability ofcovered information in a secure manner incompliance with these laws and regulations.Ensures the organization complies with lawsand regulations governing the use of portablemedia. The policy outlines the organization’sprocess to protect corporate information thatmay be accessed and/or, stored on, ortransmitted from, such portable/removable datastorage devices according to the guidelines.Ensures the organization complies withregulations regarding safe usage and storageof PII that may be on a mobile device. Thepolicy outlines the process for the organizationto protect corporate information that may beaccessed and/or, stored on individual-liableand corporate-liable devices. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 1
HITRUST v9.2 Policy Index#5PolicyWIRELESS SECURITY5.0.3.1 Network Controls6CONFIGURATION MANAGEMENT6.0.3.1 Compliance with Security Policiesand Standards6.0.3.2 Technical Compliance Checking6.0.3.3 Change Management6.0.3.4 Separation of Development, Test,and Operational Environments6.0.3.5 Control of Internal Processing6.0.3.6 Control of Operational Software6.0.3.7 Access Control to ProgramSource Code6.0.3.8 Change Control Procedures7VULNERABILITY MANAGEMENT7.0.3.1 Inventory of Assets7.0.3.2 Security of SystemDocumentation7.0.3.3 Input Data Validation7.0.3.4 Control of TechnicalVulnerabilities8NETWORK PROTECTION8.0.3.1 Policy on the Use of NetworkServices8.0.3.2 User Authentication for ExternalConnections8.0.3.3 Segregation in Networks8.0.3.4 Network Connection Control8.0.3.5 Network Routing Control8.0.3.6 Sensitive System Isolation8.0.3.7 Network Controls8.0.3.8 Security of Network Services8.0.3.9 Input Data Validation9TRANSMISSION PROTECTION9.0.3.1 Network Controls9.0.3.2 Information Exchange Policiesand Procedures9.0.3.3 Electronic Messaging9.0.3.4 Interconnected BusinessInformation Systems9.0.3.5 Electronic Commerce Services9.0.3.6 Online Transactions9.0.3.7 Message Integrity9.0.3.8 Policy on the Use ofCryptographic ControlsDescriptionDefines the essential rules regarding themanagement and maintenance of switches,routers and firewalls at the organization.Demonstrates the organization’s commitmentto respect all computer software copyrights andto adhere to the terms of all software licenses.Establishes the organization’s commitment toan information security risk managementprocess in compliance with applicable laws andregulations regarding safe usage and storageof PII on a device.Protects the confidentiality, integrity, andavailability of organization’s coveredinformation in compliance with applicable lawsand regulations. The policy reflects theorganization's commitment to establishingappropriate controls that protect its systems,network, and networking devices from securitythreats.Demonstrates organization’s commitment toprotecting the confidentiality, integrity, andavailability of covered information incompliance with laws and regulations regardingdata in transit. The organization alsoaddresses the requirements for electronicsignatures and e-commerce. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 2
HITRUST v9.2 Policy Index#PolicyDescription9.0.3.9 Key Management10PASSWORD MANAGEMENT10.0.3.1 User Password Management10.0.3.2 Password Use10.0.3.3 Password Management System11ACCESS CONTROL11.0.3.1 Access Control Policy11.0.3.2 User Registration11.0.3.3 Privilege Management11.0.3.4 Review of User Access Rights11.0.3.5 Clear Desk and Clear ScreenPolicy11.0.3.6 User Authentication for ExternalConnections11.0.3.7 Equipment Identification inNetworks11.0.3.8 Remote Diagnostic andConfiguration Port Protection11.0.3.9 Secure Log-on Procedures11.0.3.10 User Identification andAuthentication11.0.3.11 Use of System Utilities11.0.3.12 Session Time-out11.0.3.13 Limitation of Connection Time11.0.3.14 Information Access Restriction11.0.3.15 Termination or ChangeResponsibilities11.0.3.16 Return of Assets11.0.3.17 Removal of Access Rights11.0.3.18 Prevention of Misuse ofInformation Assets11.0.3.19 Monitoring System Use12AUDIT LOGGING & MONITORING12.0.3.1 Protection of OrganizationalRecords12.0.3.2 Prevention of Misuse ofInformation Assets12.0.3.3 Protection of InformationSystems Audit Tools12.0.3.4 Audit Logging12.0.3.5 Monitoring System Use12.0.3.6 Protection of Log Information12.0.3.7 Administrator and Operator Logs12.0.3.8 Fault Logging12.0.3.9 Clock Synchronization12.0.3.10 Segregation of Duties12.0.3.11 Electronic Commerce ServicesOutlines a process for the organization topossess secure passwords and user IDs incompliance with applicable laws andregulations.Demonstrates the organization’s commitmentto HITRUST guidelines and other applicablelaws and regulations that protect coveredinformation.Ensures the organization complies withapplicable guidelines regarding safe usage andstorage of PII by outlining a process forregularly auditing user access. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 3
HITRUST v9.2 Policy Index#PolicyDescription12.0.3.12 Required Uses and Disclosures13EDUCATION, TRAINING & AWARENESS13.0.3.1 Secure Log-on Procedures13.0.3.2 Mobile Computing andCommunications13.0.3.3 Teleworking13.0.3.4 Information Security Awareness,Education, and Training13.0.3.5 Prevention of Misuse ofInformation Assets13.0.3.6 Acceptable Use of Assets13.0.3.7 Controls Against Malicious Code13.0.3.8 Information Exchange Policiesand Procedures13.0.3.9 Developing and ImplementingContinuity Plans Including InformationSecurity14THIRD PARTY ASSURANCE14.0.3.1 Identification of Risks Related toExternal Parties14.0.3.2 Addressing Security WhenDealing with Customers14.0.3.3 Addressing Security in ThirdParty Agreements14.0.3.4 Service Delivery14.0.3.5 Monitoring and Review of ThirdParty Services14.0.3.6 Managing Changes to ThirdParty Services14.0.3.7 Exchange Agreements14.0.3.8 Outsourced SoftwareDevelopment15INCIDENT MANAGEMENT15.0.3.1 Disciplinary Process15.0.3.2 Prevention of Misuse ofInformation Assets15.0.3.3 Control of Internal Processing15.0.3.4 Reporting Information SecurityEvents15.0.3.5 Reporting a Security Weakness15.0.3.6 Responsibilities and Procedures15.0.3.7 Learning from InformationSecurity Incidents15.0.3.8 Collection of Evidence16BUSINESS CONTINUITY & DISASTERRECOVERY POLICYOutlines the organization’s program toproperly educate staff on matters of securityand privacy awareness in compliance withapplicable laws and regulations.Demonstrates the organization’s compliancewith guidelines regarding safe usage andstorage of PII/sensitive information on theorganization’s systems and devices.Outlines the organization’s commitment toprotect the confidentiality, integrity, andavailability of data and information systemsfrom adverse incidents, whether intentional oraccidental. The organization will develop aframework to address these incidents, maintainindustry-standard security measures, andcontinually assess potential risks andvulnerabilities to PII/sensitive information.Demonstrates the organization’s commitmentto protect PII/sensitive information from an All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 4
HITRUST v9.2 Policy Index#Policy16.0.3.1 Capacity Management16.0.3.2 Back-up16.0.3.3 Including Information Security inthe Business Continuity ManagementProcess16.0.3.4 Business Continuity and RiskAssessment16.0.3.5 Developing and ImplementingContinuity Plans Including InformationSecurity16.0.3.6 Business Continuity PlanningFramework16.0.3.7 Testing, Maintaining, and ReAssessing Business Continuity Plans17RISK MANAGEMENT17.0.3.1 Risk Management ProgramDevelopment17.0.3.2 Performing Risk Assessments17.0.3.3 Risk Mitigation17.0.3.4 Risk Evaluation17.0.3.5 Authorization Process forInformation Assets and Facilities17.0.3.6 Contact with Authorities17.0.3.7 Contact with Special InterestGroups17.0.3.8 Information Systems AuditControls17.0.3.9 Classification Guidelines17.0.3.10 System Acceptance17.0.3.11 Security RequirementsAnalysis and Specification17.0.3.12 Opportunity Required18PHYSICAL & ENVIRONMENTALSECURITY18.0.3.1 Physical Security Perimeter18.0.3.2 Physical Entry Controls18.0.3.3 Securing Offices, Rooms, andFacilities18.0.3.4 Protecting Against External andEnvironmental Threats18.0.3.5 Working in Secure Areas18.0.3.6 Public Access, Delivery, andLoading Areas18.0.3.7 Equipment Siting and Protection18.0.3.8 Supporting Utilities18.0.3.9 Cabling Security18.0.3.10 Equipment Maintenance18.0.3.11 Security of Equipment OffPremisesDescriptionunexpected event to the physical facilities orwithin information systems.Demonstrates the organization’s compliancewith applicable laws and regulations.Demonstrates the organization’s commitmentto compliance with applicable laws andregulations related to physical security. Theorganization controls access to its informationsystems/applications. Access to physicalbuildings/facilities that house thesesystems/applications is granted only toauthorized users. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 5
HITRUST v9.2 Policy Index#PolicyDescription18.0.3.12 Secure Disposal or Re-Use ofEquipment18.0.3.13 Removal of Property18.0.3.14 Disposal of Media19DATA PROTECTION & PRIVACY19.0.3.1 Privilege Management19.0.3.2 Confidentiality Agreements19.0.3.3 Addressing Security WhenDealing with Customers19.0.3.4 Intellectual Property Rights19.0.3.5 Protection of OrganizationalRecords19.0.3.6 Data Protection and Privacy ofCovered Information19.0.3.7 Prevention of Misuse ofInformation Assets19.0.3.8 Regulation of CryptographicControls19.0.3.9 Information Labeling andHandling19.0.3.10 Management of RemovableMedia19.0.3.11 Publicly Available Information19.0.3.12 Control of Internal Processing19.0.3.13 Output Data Validation19.0.3.14 Key Management19.0.3.15 Protection of System Test Data19.0.3.16 Notice of Privacy Practices19.0.3.17 Rights to Protection andConfidentiality19.0.3.18 Authorization Required19.0.3.19 Opportunity Required19.0.3.20 Authorization or OpportunityNot Required19.0.3.21 Access to IndividualInformation19.0.3.22 Accounting of Disclosures19.0.3.23 Correction of Records19.0.3.24 Required Uses and Disclosures19.0.3.25 Permitted Uses andDisclosures19.0.3.26 Prohibited or Restricted Usesand Disclosures19.0.3.27 Minimum Necessary Use19.0.3.28 Confidential Communications19.0.3.29 Organizational RequirementsEstablishes the organization’s compliance withfederal and other applicable privacy laws. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 6
HITRUST v9.2 Policy Index # Policy Description 9.0.3.9 Key Management 10 PASSWORD MANAGEMENT 10.0.3.1 User Password Management 10.0.3.2 Password Use 10.0.3.3 Password Management System Outlines a process for the organization to possess secure passwords and user IDs in complianc