Transcription
FireEye HX Series AppliancesFireEye, Inc.Common Criteria Security TargetDocument Version: 1.0Prepared By:Acumen Security18504 Office Park DrMontgomery Village, MD 20886www.acumensecurity.net1
Table Of Contents1Security Target Introduction . 51.1Security Target and TOE Reference . 51.2TOE Overview . 51.2.11.3TOE Description. 51.3.123TOE Product Type. 5HX Series Appliances: HX 4400, HX 4400D, HX 4402, HX 9402 Appliances . 51.4TOE Evaluated Configuration . 61.5TOE Architecture . 71.5.1Physical Boundaries . 71.5.2Logical Boundaries . 71.5.2.1Security Audit . 71.5.2.2Cryptographic Support . 81.5.2.3User Data Protection. 91.5.2.4Identification and Authentication . 91.5.2.5Security Management . 91.5.2.6Protection of the TSF . 101.5.2.7Trusted Path/Channels. 101.5.2.8TOE Access . 10Conformance Claims . 122.1CC Conformance . 122.2Protection Profile Conformance . 122.3Conformance Rationale . 12Security Problem Definition . 133.1Assumptions . 133.1.1A.NO GENERAL PURPOSE. 133.1.2A.PHYSICAL . 133.1.3A.TRUSTED ADMIN. 133.2Threats . 133.2.1Communications with the TOE (T.UNAUTHORIZED ACCESS) . 133.2.2Malicious Updates (T.UNAUTHORIZED UPDATE). 143.2.3Undetected System Activity (T.ADMIN ERROR, T.UNDETECTED ACTIONS,T.UNAUTHORIZED ACCESS) . 143.2.42Accessing the TOE (T.UNAUTHORIZED ACCESS) . 15
3.2.5User Data Disclosure (T.USER DATA REUSE) . 153.2.6TSF Failure (T. TSF FAILURE) . 153.33.3.1Protected Communications (O.PROTECTED COMMUNICATIONS) . 153.3.2Verifiable Updates (O.VERIFIABLE UPDATES) . 163.3.3System Monitoring (O.SYSTEM MONITORING) . 163.3.4TOE Administration (O.TOE ADMINISTRATION) . 173.3.5Residual Information Clearing (O.RESIDUAL INFORMATION CLEARING) . 173.3.6TSF Self-Test (O.TSF SELF TEST). 173.3.7O.DISPLAY BANNER . 173.3.8O.SESSION LOCK . 173.445Security Objectives for the TOE . 15Security Objectives for the Operational Environment . 173.4.1OE.NO GENERAL PURPOSE . 173.4.2OE.PHYSICAL. 183.4.3OE.TRUSTED ADMIN . 18Security Requirements . 194.1Conventions . 194.2TOE Security Functional Requirements . 194.2.1Class: Security Audit (FAU) . 204.2.2Class: Cryptographic Support (FCS) . 214.2.3Class: User Data Protection (FDP) . 234.2.4Class: Identification and Authentication (FIA) . 234.2.5Class: Security Management (FMT) . 244.2.6Class: Protection of the TSF (FPT) . 244.2.7Class: TOE Access (FTA) . 254.2.8Class: Trusted Path/Channels (FTP) . 254.3TOE SFR Dependencies Rationale for SFRs . 264.4Security Assurance Requirements . 264.5Rationale for Security Assurance Requirements . 264.6Assurance Measures . 26TOE Summary Specification . 285.1Key Zeroization. 33Annex A: References . 353
Revision HistoryVersion1.04DateFebruary 2016DescriptionInitial release
1 Security Target Introduction1.1 Security Target and TOE ReferenceThis section provides information needed to identify and control this ST and its TOE.CategoryST TitleST VersionST DateST AuthorTOE IdentifierTOE Hardware VersionsTOE Software VersionTOE DeveloperKey WordsIdentifierFireEye HX Series Appliances Security Target1.0January 25, 2015Acumen Security, LLC.FireEye HX Series AppliancesHX 4400, HX 4400D, HX 4402, HX 94023.1.0FireEye, Inc.Network Device, Security ApplianceTable 1 TOE/ST Identification1.2 TOE OverviewThe TOE consists of the FireEye HX series appliances. These products include the HX4400, HX4400D, HX4402, and HX 9402. These products provide organizations with the ability to continuously monitorendpoints for advanced malware and indicators of compromise.1.2.1 TOE Product TypeFireEye HX series appliances are network devices that provide a managed solution for managing thesecurity posture of connected end points. The FireEye HX series appliances run a custom-built hardenedversion of Linux with only the required services enabled.1.3 TOE DescriptionThis section provides a description of the FireEye HX series appliances Target of Evaluation (TOE). Thefollowing section provides an overview of the functionality provided by the TOE and its physicalcharacteristics.1.3.1 HX Series Appliances: HX 4400, HX 4400D, HX 4402, HX 9402 AppliancesThe FireEye HX series appliances enable security operations teams to correlate network and endpointactivity. Organizations can automatically investigate alerts generated by FireEye Threat PreventionPlatforms, log management, and network security products, apply intelligence from FireEye tocontinuously validate Indicators of Compromises on the endpoints and identify if a compromise hasoccurred and assess the potential risk. Further, organizations can quickly triage the incident tounderstand the details and contain compromised endpoints with a single click and contain compromiseddevices within a single click workflow.The following table identifies the characteristics of each of the appliances.HX 4400Network PortsStorageEnclosurePower SupplyOperating Temp52x 10/100/1000BASE-T Ports4x 600 GB HDD, RAID 10, 2.5 inch, FRU1RU, Fits 19 inch RackRedundant (1 1) 750 watt, 100 - 240 VAC, 9 –4.5A, 50-60 Hz, IEC60320-C14 inlet, FRU10 C to 35 CHX 4400D2x 10/100/1000BASE-T Ports4x 600 GB HDD, RAID 10, 2.5 inch, FRU1RU, Fits 19 inch RackRedundant (1 1) 750 watt, 100 - 240 VAC, 9 –4.5A, 50-60 Hz, IEC60320-C14 inlet, FRU10 C to 35 C
HX ptoAlgorithmImplementationHX 4400DAMD Optetron 6328CentOS 6.5 (kernel version 3.10.53)AMD Optetron 6328CentOS 6.5 (kernel version 3.10.53)Image-hsm.imgImage-hsm.imgFireEye Algorithms Implementation, Version1.0 (used for general cryptography)FireEye Algorithms Implementation, Version1.0 (used for general cryptography)FireEye Image Signature Verification, Version1.0 (used for secure software update)FireEye Image Signature Verification, Version1.0 (used for secure software update)Table 2 HX Series Appliances (1)HX 4402HX 9402Network Ports2x 10/100/1000BASE-T PortsStorageEnclosure4x 1.8 TB HDD, RAID 10, 2.5 inch, FRU1RU, Fits 19 inch RackPower SupplyOperating ptoAlgorithmImplementationRedundant (1 1) 750 watt, 100 - 240 VAC, 9 –4.5A, 50-60 Hz, IEC60320-C14 inlet, FRU10 C to 35 CAMD Optetron 6328CentOS 6.5 (kernel version 3.10.53)2x 10/100/1000BASE-T Ports2 x 1.92TB Samsung 2.5” SATA SSD (RAID1)plus 4 x 6TB SAS 3.5” HDD (RAID10)2RU, Fits 19 inch RackRedundant (1 1) 1200 watt, 100-140 VAC, 14.7- 10.5 A 1400 watt, 180-240 VAC, 9.5 - 7.2 A,50-60 Hz, FRU10 C to 35 CAMD Optetron 6328CentOS 6.5 (kernel version 3.10.53)Image-hsm.imgImage-hsm.imgFireEye Algorithms Implementation, Version1.0 (used for general cryptography)FireEye Algorithms Implementation, Version1.0 (used for general cryptography)FireEye Image Signature Verification, Version1.0 (used for secure software update)FireEye Image Signature Verification, Version1.0 (used for secure software update)Table 3 HX Series Appliances (2)1.4 TOE Evaluated ConfigurationThe TOE evaluated configuration consists of one of the HX series appliances listed above. The TOE alsosupports (sometimes optionally) secure connectivity with several other IT environment devices,including,ComponentRequiredManagement Workstationwith Web Browser/SSHClientYesTime ServerNoAudit serverNoLDAP AAA ServerNo6Usage/Purpose Description for TOE performanceThis includes any IT Environment Management workstation with a WebBrowser and a SSH client installed that is used by the TOE administratorto support TOE administration through HTTPS and SSH protectedchannels. Any SSH client that supports SSHv2 may be used. Any webbrowser that supports TLS 1.0 or greater may be used.The TOE supports communications with an NTP server to synchronizedate and time.The syslog audit server is used for remote storage of audit records thathave been generated by and transmitted from the TOE.This includes any IT environment LDAP AAA server that providesauthentication services to TOE administrators.
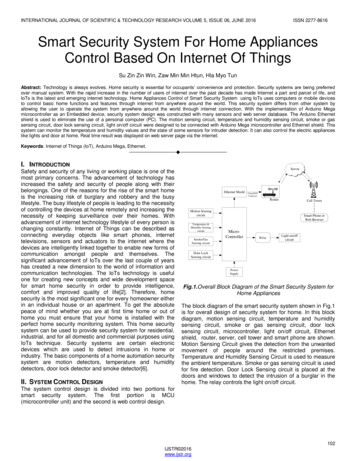
Table 4 IT Environment ComponentsThe following figure provides a visual depiction of an example of the TOE. The TOE boundary issurrounded with hashed red lines. Each TOE interconnection is through an SSH secured channel.1.5 TOE Architecture1.5.1 Physical BoundariesThe TOE is a hardware and software solution that is comprised of the security appliance modelsdescribed above in Section 1.3. The TOE guidance documentation that is considered to be part of theTOE can be found listed in the FireEye FIPS Mode and Common Criteria Addendum document and isdownloadable from the http://fireeye.com web site.The network on which the TOE resides is considered part of the environment. The software is preinstalled and is comprised of only the software versions identified in Section 1.1. In addition, thesoftware images are also downloadable from the FireEye website. A login ID and password is requiredto download the software image.1.5.2 Logical BoundariesThe TOE is comprised of several security features. Each of the security features identified above consistsof several security functionalities, as identified below. Security Audit Cryptography Support User Data Protection Identification & Authentication Security Management Protection of the TSF Trusted Path/Channel TOE AccessThese features are described in more detail in the subsections below. In addition, the TOE implementsall RFCs of the [NDPP] as necessary to satisfy testing/assurance measures prescribed therein.1.5.2.1 Security AuditThe FireEye HX Series Appliances provide extensive auditing capabilities. The TOE generates acomprehensive set of audit logs that identify specific TOE operations. For each event, the TOE recordsthe date and time of each event, the type of event, the subject identity, and the outcome of the event.Auditable events include: failure on invoking cryptographic functionality such as establishment,7
termination and failure of a TLS session; establishment, termination and failure of an SSH session;modifications to the group of users that are part of the authorized administrator roles; all use of theuser identification mechanism; any use of the authentication mechanism; any change in theconfiguration of the TOE, changes to time, initiation of TOE update, indication of completion of TSF selftest, maximum sessions being exceeded, termination of a remote session; and initiation and terminationof a trusted channel.The TOE is configured to transmit its audit messages to an external syslog server. Communication withthe syslog server is protected using TLS and the TOE can determine when communication with thesyslog server fails.The logs for all of the appliances can be viewed on the TOE via the TOE CLI. The records include thedate/time the event occurred, the event/type of event, the user ID associated with the event, andadditional information of the event and its success and/or failure. The TOE does not have an interfaceto modify audit records, though there is an interface available for the authorized administrator to clearaudit data stored locally on the TOE.1.5.2.2 Cryptographic SupportThe TOE provides cryptographic support for the following features, TLS connectivity with the following entities:o External LDAP Servero Audit Servero Management Web BrowserSSH connectivity with the following entities:o Management SSH ClientSecure software updateThe cryptographic services provided by the TOE are described below.Cryptographic MethodTLS EstablishmentSSH EstablishmentECDSA Signature ServicesRSA Signature ServicesSP 800-90 DRBGSHSHMAC-SHSAESUse within the TOEUsed to establish initial TLS session.Used to establish initial SSH session.Used in TLS session establishment.Used in TLS session establishment.Used in SSH session establishmentUsed in secure software updateUsed in TLS session establishment.Used in SSH session establishmentUsed in secure software updateUsed to provide TLS traffic integrity verificationUsed to provide SSH traffic integrity verificationUsed to encrypt TLS trafficUsed to encrypt SSH trafficTable 5 TOE Provided CryptographyThis cryptography has been validated by the CAVP for conformance to the individual algorithmstandards, as identified below.AlgorithmRSAECDSA8CAVP Certificate #Cert. #1759, 1758Cert. #696
AlgorithmSP 800-90 DRBGSHSHMAC-SHSAESCAVP Certificate #Cert. #843Cert. #2837, 2836Cert. #2195Cert. #3447Table 6 CAVP Algorithm Testing ReferencesEach of the above referenced algorithms are implemented within the FireEye AlgorithmsImplementation, version 1.0 and FireEye Image Signature Verification, version 1.0 cryptographiclibraries. Each service requiring cryptography directly calls the cryptographic libraries.1.5.2.3 User Data ProtectionThe TOE ensures that all information flows from the TOE do not contain residual information fromprevious traffic. Packets are padded with zeros. Residual data is never transmitted from the TOE.1.5.2.4 Identification and AuthenticationThe TOE performs three types of authentication: device-level authentication of remote IT Environmentdevices (e.g., audit servers and LDAP servers) and user authentication for the Authorized Administratorof the TOE. Device-level authentication of remote IT Environment devices allows the TOE to establish asecure channel with an IT Environment trusted peer. The secure channel is established only after eachdevice authenticates the other. This device-level authentication is performed via TLS authentication.The TOE provides authentication services for administrative users to connect to the TOEs secure GUI orCLI administrator interface. The TOE requires Authorized Administrators to authenticate prior to beinggranted access to any of the management functionality. In the Common Criteria evaluatedconfiguration, the TOE is configured to require a minimum password length of 15 characters, as well as,mandatory password complexity rules. The TOE provides two administrator authentication m
The FireEye HX series appliances enable security operations teams to correlate network and endpoint activity. Organizations can automatically investigate alerts generated by FireEye Threat Prevention Platforms, log management, and network security products