Transcription
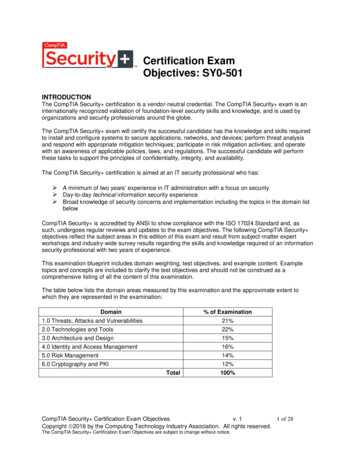
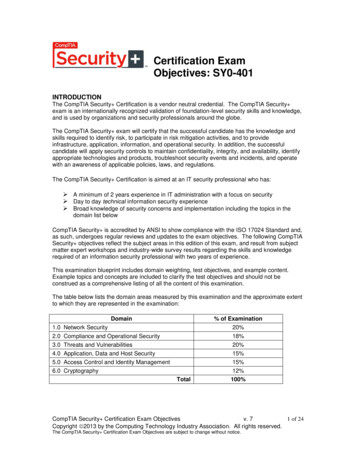
Certification ExamObjectives: SY0-401INTRODUCTIONThe CompTIA Security Certification is a vendor neutral credential. The CompTIA Security exam is an internationally recognized validation of foundation-level security skills and knowledge,and is used by organizations and security professionals around the globe.The CompTIA Security exam will certify that the successful candidate has the knowledge andskills required to identify risk, to participate in risk mitigation activities, and to provideinfrastructure, application, information, and operational security. In addition, the successfulcandidate will apply security controls to maintain confidentiality, integrity, and availability, identifyappropriate technologies and products, troubleshoot security events and incidents, and operatewith an awareness of applicable policies, laws, and regulations.The CompTIA Security Certification is aimed at an IT security professional who has: A minimum of 2 years experience in IT administration with a focus on security Day to day technical information security experience Broad knowledge of security concerns and implementation including the topics in thedomain list belowCompTIA Security is accredited by ANSI to show compliance with the ISO 17024 Standard and,as such, undergoes regular reviews and updates to the exam objectives. The following CompTIASecurity objectives reflect the subject areas in this edition of this exam, and result from subjectmatter expert workshops and industry-wide survey results regarding the skills and knowledgerequired of an information security professional with two years of experience.This examination blueprint includes domain weighting, test objectives, and example content.Example topics and concepts are included to clarify the test objectives and should not beconstrued as a comprehensive listing of all the content of this examination.The table below lists the domain areas measured by this examination and the approximate extentto which they are represented in the examination:Domain% of Examination1.0 Network iance and Operational SecurityThreats and VulnerabilitiesApplication, Data and Host SecurityAccess Control and Identity ManagementCryptographyTotalCompTIA Security Certification Exam Objectivesv. 71 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
CompTIA Authorized Materials Use PolicyCompTIA Certifications, LLC is not affiliated with and does not authorize, endorse or condone utilizingany content provided by unauthorized third-party training sites, aka 'brain dumps'. Individuals who utilizesuch materials in preparation for any CompTIA examination will have their certifications revoked and besuspended from future testing in accordance with the CompTIA Candidate Agreement. In an effort to moreclearly communicate CompTIA’s exam policies on use of unauthorized study materials, CompTIA directsall certification candidates to the CompTIA Certification Exam Policies testingcenters/policies.aspxPlease review all CompTIA policies before beginning the study process for any CompTIA exam.Candidates will be required toabide by the CompTIA Candidate g/testingcenters/policies/agreement.aspx) at the time of examdelivery.If a candidate has a question as to whether study materials are considered unauthorized (aka brain dumps),he/she should perform a search using CertGuard'sengine, found here:http://www.certguard.com/search.aspOr verify against this tingcenters/policies/unauthorized.aspx**Note: The lists of examples provided in bulleted format below each objective are not exhaustive lists.Other examples of technologies, processes or tasks pertaining to each objective may also be included on theexam although not listed or covered in this objectives document.CompTIA is constantly reviewing the content of our exams and updating test questions to be sure ourexams are current and the security of the questions is protected. When necessary, we will publish updatedexams based on existing exam objectives. Please know that all related exam preparation materials will stillbe valid.CompTIA Security Certification Exam Objectivesv. 72 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
1.0 Network Security1.1 Implement security configuration parameters on network devices and othertechnologies. Firewalls Routers Switches Load Balancers Proxies Web security gateways VPN concentrators NIDS and NIPSo Behavior basedo Signature basedo Anomaly basedo Heuristic Protocol analyzers Spam filter UTM security applianceso URL filtero Content inspectiono Malware inspection Web application firewall vs. network firewall Application aware deviceso Firewallso IPSo IDSo Proxies1.2 Given a scenario, use secure network administration principles. Rule-based management Firewall rules VLAN management Secure router configuration Access control lists Port Security 802.1x Flood guards Loop protection Implicit deny Network separation Log analysis Unified Threat Management1.3 Explain network design elements and components. DMZ Subnetting VLAN NAT Remote Access TelephonyCompTIA Security Certification Exam Objectivesv. 73 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
NACVirtualizationCloud Computingo Platform as a Serviceo Software as a Serviceo Infrastructure as a Serviceo Privateo Publico Hybrido CommunityLayered security / Defense in depth1.4 Given a scenario, implement common protocols and services. Protocolso IPSeco SNMPo SSHo DNSo TLSo SSLo TCP/IPo FTPSo HTTPSo SCPo ICMPo IPv4o IPv6o iSCSIo Fibre Channelo FCoEo FTPo SFTPo TFTPo TELNETo HTTPo NetBIOS Portso 21o 22o 25o 53o 80o 110o 139o 143o 443o 3389 OSI relevance1.5 Given a scenario, troubleshoot security issues related to wireless networking. WPA WPA2 WEPCompTIA Security Certification Exam Objectivesv. 74 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
EAPPEAPLEAPMAC filterDisable SSID broadcastTKIPCCMPAntenna PlacementPower level controlsCaptive portalsAntenna typesSite surveysVPN (over open wireless)2.0 Compliance and Operational Security2.1 Explain the importance of risk related concepts. Control typeso Technicalo Managemento Operational False positives False negatives Importance of policies in reducing risko Privacy policyo Acceptable useo Security policyo Mandatory vacationso Job rotationo Separation of dutieso Least privilege Risk calculationo Likelihoodo ALEo Impacto SLEo AROo MTTRo MTTFo MTBF Quantitative vs. qualitative Vulnerabilities Threat vectors Probability / threat likelihood Risk-avoidance, transference, acceptance, mitigation, deterrence Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective2.2 Summarize the security implications of integrating systems and data with thirdparties. On-boarding/off-boarding business partners Social media networks and/or applications Interoperability agreementsCompTIA Security Certification Exam Objectivesv. 75 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
o SLAo BPAo MOUo ISAPrivacy considerationsRisk awarenessUnauthorized data sharingData ownershipData backupsFollow security policy and proceduresReview agreement requirements to verify compliance and performancestandards2.3 Given a scenario, implement appropriate risk mitigation strategies. Change management Incident management User rights and permissions reviews Perform routine audits Enforce policies and procedures to prevent data loss or theft Enforce technology controlso Data Loss Prevention (DLP)2.4 Given a scenario, implement basic forensic procedures. Order of volatility Capture system image Network traffic and logs Capture video Record time offset Take hashes Screenshots Witnesses Track man hours and expense Chain of custody Big Data analysis2.5 Summarize common incident response procedures. Preparation Incident identification Escalation and notification Mitigation steps Lessons learned Reporting Recovery/reconstitution procedures First responder Incident isolationo Quarantineo Device removal Data breach Damage and loss control2.6 Explain the importance of security related awareness and training. Security policy training and procedures Role-based trainingCompTIA Security Certification Exam Objectivesv. 76 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
Personally identifiable informationInformation classificationo Higho Mediumo Lowo Confidentialo Privateo PublicData labeling, handling and disposalCompliance with laws, best practices and standardsUser habitso Password behaviorso Data handlingo Clean desk policieso Prevent tailgatingo Personally owned devicesNew threats and new security trends/alertso New viruseso Phishing attackso Zero-day exploitsUse of social networking and P2PFollow up and gather training metrics to validate compliance and securityposture2.7 Compare and contrast physical security and environmental controls. Environmental controlso HVACo Fire suppressiono EMI shieldingo Hot and cold aisleso Environmental monitoringo Temperature and humidity controls Physical securityo Hardware lockso Mantrapso Video Surveillanceo Fencingo Proximity readerso Access listo Proper lightingo Signso Guardso Barricadeso Biometricso Protected distribution (cabling)o Alarmso Motion detection Control typeso Deterrento Preventiveo Detectiveo Compensatingo Technicalo AdministrativeCompTIA Security Certification Exam Objectivesv. 77 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
2.8 Summarize risk management best practices. Business continuity conceptso Business impact analysiso Identification of critical systems and componentso Removing single points of failureo Business continuity planning and testingo Risk assessmento Continuity of operationso Disaster recoveryo IT contingency planningo Succession planningo High availabilityo Redundancyo Tabletop exercises Fault toleranceo Hardwareo RAIDo Clusteringo Load balancingo Servers Disaster recovery conceptso Backup plans/policieso Backup execution/frequencyo Cold siteo Hot siteo Warm site2.9 Given a scenario, select the appropriate control to meet the goals of security. Confidentialityo Encryptiono Access controlso Steganography Integrityo Hashingo Digital signatureso Certificateso Non-repudiation Availabilityo Redundancyo Fault toleranceo Patching Safetyo Fencingo Lightingo Lockso CCTVo Escape planso Drillso Escape routeso Testing controls3.0 Threats and Vulnerabilities3.1 Explain types of malware.CompTIA Security Certification Exam Objectivesv. 78 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
AdwareVirusSpywareTrojanRootkitsBackdoorsLogic bombBotnetsRansomwarePolymorphic malwareArmored virus3.2 Summarize various types of attacks. Man-in-the-middle DDoS DoS Replay Smurf attack Spoofing Spam Phishing Spim Vishing Spear phishing Xmas attack Pharming Privilege escalation Malicious insider threat DNS poisoning and ARP poisoning Transitive access Client-side attacks Password attackso Brute forceo Dictionary attackso Hybrido Birthday attackso Rainbow tables Typo squatting/URL hijacking Watering hole attack3.3 Summarize social engineering attacks and the associated effectiveness witheach attack. Shoulder surfing Dumpster diving Tailgating Impersonation Hoaxes Whaling Vishing Principles (reasons for effectiveness)o Authorityo Intimidationo Consensus/Social proofCompTIA Security Certification Exam Objectivesv. 79 of 24Copyright 2013 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
ooooScarcityUrgencyFamiliarity/likingTrust3.4 Explain types of wireless attacks. Rogue access points Jamming/Interference Evil twin War driving Bluejacking Bluesnarfing War chalking IV attack Packet sniffing Near field communication Replay attacks WEP/WPA attacks WPS attacks3.5 Explain types of application attacks. Cross-site scripting SQL injection LDAP injection XML injection Directory traversal/command injection Buffer overflow Integer overflow Zero-day Cookies and attachments LSO (Locally Shared Objects) Flash Cookies Malicious add-ons Session hijacking Header manipulation Arbitrary code execution / remote code execution3.6 Analyze a scenario and select the appropriate type of mitigation and deterrenttechniques. Monitoring system logso Event logso Audit logso Security logso Access logs Hardeningo Disabling unnecessary serviceso Protecting management interfaces and applicationso Password protectiono Disabling unnecessary accounts Network securityo MAC limiting and filteringo 802.1xo Disabling unused interfaces and unused application service portsCompTIA Secur
Broad knowledge of security concerns and implementation including the topics in the domain list below CompTIA Security is accredited by ANSI to show compliance with the ISO 17024 Standard and, as such, undergoes regular reviews and updates to the exam objectives. The following CompTIA Security objectives reflect the subject areas in this edition of this exam, and result from subject matter .File Size: 385KBPage Count: 24