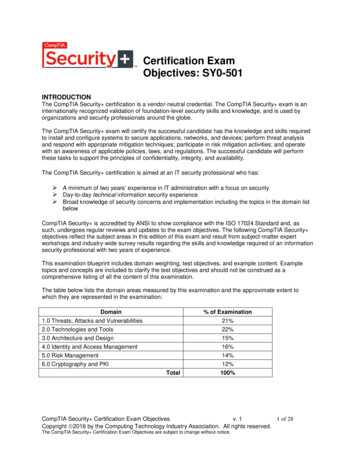
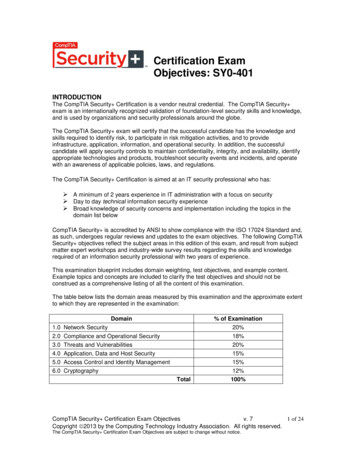
Transcription
STUDY PLANCompTIA Security SY0-501Total Videos: 110Time: 23 hrs
STUDY STRATEGIESLearners use a great variety of strategies to attack theirtraining. Here are some options you can choose from toget the most out of your training experience:PRACTICE EXAM STRATEGIESCBT Nuggets offers practice exams as part of yoursubscription. You can take the practice exams as manytimes – and as often – as you like! Here are some tips tohelp you take full advantage of this excellent resource:Proceed through all CBT Nuggets video training on doublespeed to develop a strong overview of the material; Thenproceed through all the training for a second time, taking goodnotes and focusing on deeper learning.ORProceed through all CBT Nuggets video training, taking goodnotes and focusing on deep learning on the first pass; Thenproceed back through all training a second time, using doublespeed when appropriate.Supplement all video training with book study and practicalapplication of knowledge.Develop a test environment where new skills can be practiced.PLAN TO TAKE THE PRACTICE EXAM 3 TIMESFIRST EXAMCreate a baseline againstwhich you can measure yourprogress with future exams.Identify areas of weakness inorder to direct your trainingas you move forward.SECOND EXAMMeasure your progress since your firstpractice exam! Ask yourself: Are youretaining the information and materialyou learned at the beginning of yourtraining? Are there areas to whichyou should return now to ensureyour understanding before movingforward?The results from yoursecond practice examexperience should help youidentify areas where youmay need to spend extraeffort and energy in thetraining ahead.THIRD EXAMLearn more about how to get all you canout of your practice exam experiencefrom a quick video by Keith BarkerMeasure your progressagainst your first twopractice exams! Askyourself: Are youscoring 90% by now? Ifso, you might be readyfor the real thing!Allow the results from yourpractice exam to directyour review ahead of yourcertification exam. Askyourself: Are you retainingall the material? And are youunderstanding it well?2
1. Welcome toSecurity The number and title for each videocorresponds to the number andtitle you will find on the CompTIASecurity SY0-501 course pageonline (and on your mobile device).KEY2. InfrastructureSecurity DevicesEXTRAMILE32 min.The Extra Mile section of your study plan challenges youto dig a little deeper with your training. The Extra Milemight be a textbook recommendation, supplementalmaterials downloads, or other resources to help youtake your training to the next level. Nothing in the ExtraMile is required, but it is here to help you learn.The duration of the video.WEEK 1CompTIA Security SY0-5011. Welcome toSecurity 3. Application andTraffic Analysis2. InfrastructureSecurity Devices4. NetworkSegmentation andSeparation withVLANs32 min.26 min.EXTRAMILE5. Proper Placementof Technology toImprove Security6. ACL Case Study23 min.Explore the CompTIA website to learn more aboutthe Security exam, its requirements, and availableresources.7. DesignConsiderations9. NAT and PATCase Study8. LeveragingBest Practices,Frameworks, andGuidelines10. Firewall andSwitch ProtectionMechanisms24 min.29 min.Download CBT Nuggets apps toyour various mobile devices so youcan have your training with youwhen you’re on the go!“With self-discipline mostanything is possible.”– Theodore Roosevelt3
WEEK 211. VirtualizationOverview13. ICMP and a FewMore Protocols12. IPsec, Protocols,and Well-knownPorts14. Checking forand Using SecureProtocols34 min.24 min.WEEK 3EXTRAMILE16. VPNs andUpdates for MobileSecurity23 min.Consider purchasing an exampreparation book to furthersupplement your training. (Thereare lots of good ones, so choosethe one you feel will best meetyour unique needs!)20. Attack Vectors,Risk Management,and Recovery22. ChangeManagement andAccount Auditing21. Third-Party Riskfrom Integration23. Data LossPrevention (DLP)23 min.28 min.EXTRAMILE15. Security for WiFi17. Case Study:Technology andTools18. Risk Overview37 min.Visit the CBT Nuggets blog tolearn more about how to get themost out of your practice examexperience!24. Forensics25. IncidentResponse Concepts32 min.Create flashcards! It’s a little old school, but it works!Or, take advantage of free, online resources that canhelp like cram.com.Schedule your certification exam with an approvedtesting site.19. Risk Calculation26. SecurityAwareness, RBAC,and Data Labeling27. Passwords,Best Practices, andStandards30 min.Obtain and review theCompTIA Security exam objectives.19 min.Take the Practice Exams! Use the results to drive yourongoing study.*Transcender CompTIA Cert - SY0-501*Keep in mind that you’ve just started the training - so you probably won’t ace the exam.This is just to establish a benchmark for future practice exam performance.28. EnvironmentalControls29. Physical Security24 min.“Start by doing what’snecessary; then do what’spossible; and suddenly youare doing the impossible.”– St. Francis of Assisi4
WEEK 430. BusinessContinuity32. Fault Tolerance31. Planning Aheadfor Security33 min.27 min.EXTRAMILE33. Controls forConfidentiality34. Tools andControls for DataIntegrity36. Malware:Adware - Spyware35. Availability andSafety37. Trojans,Backdoors, andMore Malware25 min.31 min.38. Attack TypesMITM - SpearFishing39. Attack Types:Xmas - Client Side35 min.Retake the Practice Exams! Use the results to driveyour ongoing study.*Transcender CompTIA Cert - SY0-501“The results you achievewill be in direct proportionto the effort you apply.”WEEK 5*Generally speaking, you should be able to score about 90% on the practice examsif you expect to succeed on your certification exam.40. Password Attacksand Watering Holes41. SocialEngineering Threats28 min.EXTRAMILE42. Vishing and WhySocial EngineeringWorks– Denis Waitley44. Cross-site andInjection Attacks46. Monitoring andDevice Hardening43. Wireless Attacks45. ApplicationAttacks47. Network Accessand Data Protection28 min.30 min.35 min.Join the CBT Nuggets Learners Community on Slack! Join otherCBT Nuggets learners in a community where you can postquestions, share study resources, and connect with IT experts allover the world.48. Baselines,Detection, andReporting49. Analyzers andScanners32 min.“Success is dependent oneffort.”– Sophocles*Please allow 48 hours for your request to join the community to be processed.5
WEEK 650. Tools for aSecurity PostureAssessment51. Discovering andAssessing Threats27 min.EXTRAMILE52. PenetrationTesting54. ApplicationSecurity Controls56. Mobile DeviceSecurity Overview61. Host Security57. Mobile DevicePolicies58. Benefits of Followinga Mobile Device Policy59. Mobile Devices andAuto-Wipe60. SecurityConsiderations forMobile Devices53. Techniques forSecuring Apps55. AppDevelopmentand DeploymentConcepts25 min.28 min.27 min.15 min.25 min.62. Hardwareand VirtualizationSecurity“When you link desire witheffort you can accomplishextraordinary things and leadan extraordinary life.”Consider activating a free trial forCompTIA’s CertMaster, allowingyou to assess your preparednessfor the exam.WEEK 7- Michael Josephson63. Strategies andControls to ReduceRisk65. Securing Datawith H/W, Controls,and Policy64. Data Security66. Elements ofSecure Systems19 min.18 min.EXTRAMILE67. Security in StaticEnvironments68. AAA Concepts25 min.69. AuthenticationProtocols andServices71. AuthenticationControls70. MultifactorAuthentication72. Managementand Controls forAccess and Identity33 min.29 min.LEARN WHAT TO EXPECT ON YOUR EXAM: You need to earn 750 to pass the exam You will have a maximum of 90 minutes to complete your exam73. ControllingAccess viaAuthorization19 min.“Success is the sum of smallefforts, repeated day in andday out.”- R. Collier6
WEEK 874. AccountManagement76. CryptographyConsiderations78. Hashing andEncryption Protocols75. Symmetricand AsymmetricEncryption77. Crypto KeyManagement79. ComparingCryptographyAlgorithms40 min.34 min.38 min.WEEK 9EXTRAMILEEXTRAMILE81. PKI and DigitalCertificate Uses23 min.82. Layered SecurityCase Study11 min.“To be prepared is half thevictory.”Gather support for your training by sharingyour training goals with friends, family, andcolleagues.83. Attack Types andVectors84. Vulnerabilities asPart of IoT85. CertificateWarnings and TrustModels23 min.80. PKI Overview86. Threat Actor Typesand Ethics87. ReconnaissanceInformation GatheringConcepts88. HackingVocabulary and Terms23 min.- Miguel de Cervantes89. Malware Concepts90. Case Study: ASystem Compromisedby Malware91. Network ScanningOverview92. Factors DrivingVulnerabilityManagement93. Trojans94. Port Security20 min.27 min.Retake the Practice Exams! Use the results to driveyour ongoing study.*Transcender CompTIA Cert - SY0-501*Use your results to drive your final review ahead of your exam!95. ScanningMethodologies96. FocusedVulnerabilityScanning97. SniffingOverview28 min.98. VulnerabilityScanning99. Case Study: SlowPerformance19 min.“No one succeeds without effort.Those who succeed owe theirsuccess to perserverance.”- Ramana Maharshi7
WEEK 10100. SocialEngineeringOverview102. Buffer Overflow103. OWASP BWAP105. CentralizedIdentityManagement101. System HackingStages and Goals24 min.24 min.EXTRAMILE104. Honeypots andHoneynetsConsider activating a free trial forCompTIA’s CertMaster, allowingyou to assess your preparednessfor the exam.26 min.106. SSO, Kerberos,and SecurityThreats108. PenetrationTesting Legally107. IncidentResponse109. SCAP OverviewConsiderations forMobile Devices30 min.16 min.110. Case Study #121 min.“When you link desire witheffort you can accomplishextraordinary things and leadan extraordinary life.”WEEK 11- Michael JosephsonTHE BIG DAY!Take the exam.Get a good night’s sleep ahead ofyour exam!Brag about it! Tweet us or let us knowhow your exam went and what you’redoing to celebrate your success!8
Security Posture Assessment 51. Discovering and Assessing Threats 63. Strategies and Controls to Reduce Risk 64. Data Security 54. Application Security Controls 55. App Development and Deployment Concepts 67. Security in Static Environments 68. AAA Concepts 52. Penetration Testing 53. Techniques for Securing Apps 65. Securing Data with H/W, Controls, and Policy 66. Elements of