Transcription
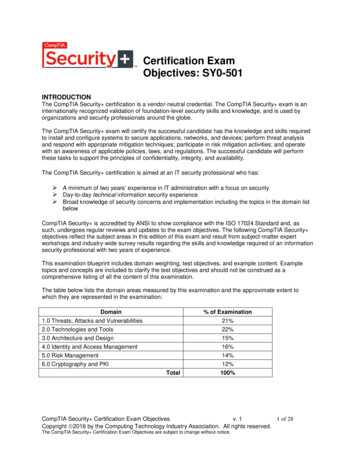
Certification ExamObjectives: SY0-501INTRODUCTIONThe CompTIA Security certification is a vendor-neutral credential. The CompTIA Security exam is aninternationally recognized validation of foundation-level security skills and knowledge, and is used byorganizations and security professionals around the globe.The CompTIA Security exam will certify the successful candidate has the knowledge and skills requiredto install and configure systems to secure applications, networks, and devices; perform threat analysisand respond with appropriate mitigation techniques; participate in risk mitigation activities; and operatewith an awareness of applicable policies, laws, and regulations. The successful candidate will performthese tasks to support the principles of confidentiality, integrity, and availability.The CompTIA Security certification is aimed at an IT security professional who has: A minimum of two years’ experience in IT administration with a focus on security Day-to-day technical information security experience Broad knowledge of security concerns and implementation including the topics in the domain listbelowCompTIA Security is accredited by ANSI to show compliance with the ISO 17024 Standard and, assuch, undergoes regular reviews and updates to the exam objectives. The following CompTIA Security objectives reflect the subject areas in this edition of this exam and result from subject-matter expertworkshops and industry-wide survey results regarding the skills and knowledge required of an informationsecurity professional with two years of experience.This examination blueprint includes domain weighting, test objectives, and example content. Exampletopics and concepts are included to clarify the test objectives and should not be construed as acomprehensive listing of all the content of this examination.The table below lists the domain areas measured by this examination and the approximate extent towhich they are represented in the examination:Domain% of Examination1.0 Threats, Attacks and Vulnerabilities2.0 Technologies and Tools3.0 Architecture and Design4.0 Identity and Access Management5.0 Risk Management6.0 Cryptography and PKITotal21%22%15%16%14%12%100%CompTIA Security Certification Exam Objectivesv. 11 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
CompTIA Authorized Materials Use PolicyCompTIA Certifications, LLC is not affiliated with and does not authorize, endorse or condone utilizing any contentprovided by unauthorized third-party training sites, aka 'brain dumps'. Individuals who utilize such materials inpreparation for any CompTIA examination will have their certifications revoked and be suspended from futuretesting in accordance with the CompTIA Candidate Agreement. In an effort to more clearly communicateCompTIA’s exam policies on use of unauthorized study materials, CompTIA directs all certification candidates tothe CompTIA Certification Exam Policies testingcenters/policies.aspxPlease review all CompTIA policies before beginning the study process for any CompTIA exam. Candidates will berequired to abide by the CompTIA Candidate g/testingcenters/policies/agreement.aspx) at the time of exam delivery.If a candidate has a question as to whether study materials are considered unauthorized (aka brain dumps), he/sheshould contact CompTIA at examsecurity@comptia.org to confirm.**Note: The lists of examples provided in bulleted format below each objective are not exhaustive lists. Otherexamples of technologies, processes or tasks pertaining to each objective may also be included on the exam althoughnot listed or covered in this objectives document.CompTIA is constantly reviewing the content of our exams and updating test questions to be sure our exams arecurrent and the security of the questions is protected. When necessary, we will publish updated exams based onexisting exam objectives. Please know that all related exam preparation materials will still be valid.CompTIA Security Certification Exam Objectivesv. 12 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
1.0 Threats, Attacks and Vulnerabilities1.1 Given a scenario, analyze indicators of compromise and determine the type ofmalware. Viruses Crypto-malware Ransomware Worm Trojan Rootkit Keylogger Adware Spyware Bots RAT Logic bomb Backdoor1.2 Compare and contrast types of attacks. Social engineeringo Phishingo Spear phishingo Whalingo Vishingo Tailgatingo Impersonationo Dumpster divingo Shoulder surfingo Hoaxo Watering hole attacko Principles (reasons for effectiveness) Authority Intimidation Consensus Scarcity Familiarity Trust Urgency Application/service attackso DoSo DDoSo Man-in-the-middleo Buffer overflowo Injectiono Cross-site scriptingo Cross-site request forgeryo Privilege escalationo ARP poisoningo Amplificationo DNS poisoningo Domain hijackingo Man-in-the-browsero Zero dayo ReplayCompTIA Security Certification Exam Objectivesv. 13 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
oo Pass the hashHijacking and related attacks Clickjacking Session hijacking URL hijacking Typo squattingo Driver manipulation Shimming Refactoringo MAC spoofingo IP spoofingWireless attackso Replayo IVo Evil twino Rogue APo Jammingo WPSo Bluejackingo Bluesnarfingo RFIDo NFCo DisassociationCryptographic attackso Birthdayo Known plain text/cipher texto Rainbow tableso Dictionaryo Brute force Online vs. offlineo Collisiono Downgradeo Replayo Weak implementations1.3 Explain threat actor types and attributes. Types of actorso Script kiddieso Hacktivisto Organized crimeo Nation states/APTo Insiderso Competitors Attributes of actorso Internal/externalo Level of sophisticationo Resources/fundingo Intent/motivation Use of open-source intelligence1.4 Explain penetration testing concepts. Active reconnaissance Passive reconnaissance Pivot Initial exploitationCompTIA Security Certification Exam Objectivesv. 14 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
PersistenceEscalation of privilegeBlack boxWhite boxGray boxPen testing vs. vulnerability scanning1.5 Explain vulnerability scanning concepts. Passively test security controls Identify vulnerability Identify lack of security controls Identify common misconfigurations Intrusive vs. non-intrusive Credentialed vs. non-credentialed False positive1.6 Explain the impact associated with types of vulnerabilities. Race conditions Vulnerabilities due to:o End-of-life systemso Embedded systemso Lack of vendor support Improper input handling Improper error handling Misconfiguration/weak configuration Default configuration Resource exhaustion Untrained users Improperly configured accounts Vulnerable business processes Weak cipher suites and implementations Memory/buffer vulnerabilityo Memory leako Integer overflowo Buffer overflowo Pointer dereferenceo DLL injection System sprawl/undocumented assets Architecture/design weaknesses New threats/zero day Improper certificate and key management2.0 Technologies and Tools2.1 Install and configure network components, both hardware- and software-based, tosupport organizational security. Firewallo ACLo Application-based vs. network-basedo Stateful vs. statelesso Implicit deny VPN concentratoro Remote access vs. site-to-siteCompTIA Security Certification Exam Objectivesv. 15 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
o IPSec Tunnel mode Transport mode AH ESPo Split tunnel vs. full tunnelo TLSo Always-on VPNNIPS/NIDSo Signature-basedo Heuristic/behavioralo Anomalyo Inline vs. passiveo In-band vs. out-of-bando Ruleso Analytics False positive False negativeRoutero ACLso AntispoofingSwitcho Port securityo Layer 2 vs. Layer 3o Loop preventiono Flood guardProxyo Forward and reverse proxyo Transparento Application/multipurposeLoad balancero Scheduling Affinity Round-robino Active-passiveo Active-activeo Virtual IPsAccess pointo SSIDo MAC filteringo Signal strengtho Band selection/widtho Antenna types and placemento Fat vs. thino Controller-based vs. standaloneSIEMo Aggregationo Correlationo Automated alerting and triggerso Time synchronizationo Event deduplicationo Logs/WORMDLPo USB blockingo Cloud-basedCompTIA Security Certification Exam Objectivesv. 16 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
o EmailNACo Dissolvable vs. permanento Host health checkso Agent vs. agentlessMail gatewayo Spam filtero DLPo EncryptionBridgeSSL/TLS acceleratorsSSL decryptorsMedia gatewayHardware security module2.2 Given a scenario, use appropriate software tools to assess the security posture ofan organization. Protocol analyzer Network scannerso Rogue system detectiono Network mapping Wireless scanners/cracker Password cracker Vulnerability scanner Configuration compliance scanner Exploitation frameworks Data sanitization tools Steganography tools Honeypot Backup utilities Banner grabbing Passive vs. active Command line toolso pingo netstato tracerto nslookup/digo arpo ipconfig/ip/ifconfigo tcpdumpo nmapo netcat2.3 Given a scenario, troubleshoot common security issues. Unencrypted credentials/clear text Logs and events anomalies Permission issues Access violations Certificate issues Data exfiltration Misconfigured deviceso Firewallo Content filtero Access pointsCompTIA Security Certification Exam Objectivesv. 17 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
Weak security configurationsPersonnel issueso Policy violationo Insider threato Social engineeringo Social mediao Personal emailUnauthorized softwareBaseline deviationLicense compliance violation (availability/integrity)Asset managementAuthentication issues2.4 Given a scenario, analyze and interpret output from security technologies. HIDS/HIPS Antivirus File integrity check Host-based firewall Application whitelisting Removable media control Advanced malware tools Patch management tools UTM DLP Data execution prevention Web application firewall2.5 Given a scenario, deploy mobile devices securely. Connection methodso Cellularo WiFio SATCOMo Bluetootho NFCo ANTo Infraredo USB Mobile device management conceptso Application managemento Content managemento Remote wipeo Geofencingo Geolocationo Screen lockso Push notification serviceso Passwords and pinso Biometricso Context-aware authenticationo Containerizationo Storage segmentationo Full device encryption Enforcement and monitoring for:o Third-party app storeso Rooting/jailbreakingCompTIA Security Certification Exam Objectivesv. 18 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
o Sideloadingo Custom firmwareo Carrier unlockingo Firmware OTA updateso Camera useo SMS/MMSo External mediao USB OTGo Recording microphoneo GPS taggingo WiFi direct/ad hoco Tetheringo Payment methodsDeployment modelso BYODo COPEo CYODo Corporate-ownedo VDI2.6 Given a scenario, implement secure protocols. Protocolso DNSSECo SSHo S/MIMEo SRTPo LDAPSo FTPSo SFTPo SNMPv3o SSL/TLSo HTTPSo Secure POP/IMAP Use caseso Voice and videoo Time synchronizationo Email and webo File transfero Directory serviceso Remote accesso Domain name resolutiono Routing and switchingo Network address allocationo Subscription services3.0 Architecture and Design3.1 Explain use cases and purpose for frameworks, best practices and secureconfiguration guides. Industry-standard frameworks and reference architectureso Regulatoryo Non-regulatoryo National vs. internationalo Industry-specific frameworksCompTIA Security Certification Exam Objectivesv. 19 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Objectives are subject to change without notice.
Benchmarks/secure configuration guideso Platform/vendor-specific guides Web server Operating system Application server Network infrastructure deviceso General purpose guidesDefense-in-depth/layered securityo Vendor diversityo Control diversity Administrative Technicalo User training3.2 Given a scenario, implement secure network architecture concepts. Zones/topologieso DMZo Extraneto Intraneto Wirelesso Guesto Honeynetso NATo Ad hoc Segregation/segmentation/isolationo Physicalo Logical (VLAN)o Virtualizationo Air gaps Tunneling/VPNo Site-to-siteo Remote access Security device/technology placemento Sensorso Collectorso Correlation engineso Filterso Proxieso Firewallso VPN concentratorso SSL acceleratorso Load balancerso DDoS mitigatoro Aggregation switcheso Taps and port mirror SDN3.3 Given a scenario, implement secure systems design. Hardware/firmware securityo FDE/SEDo TPMo HSMo UEFI/BIOSo Secure boot and attestationo Supply chainCompTIA Security Certification Exam Objectivesv. 110 of 28Copyright 2016 by the Computing Technology Industry Association. All rights reserved.The CompTIA Security Certification Exam Object
Broad knowledge of security concerns and implementation including the topics in the domain list below CompTIA Security is accredited by ANSI to show compliance with the ISO 17024 Standard and, as such, undergoes regular reviews and updates to the exam objectives. The following CompTIA Security objectives reflect the subject areas in this edition of this exam and result from subject-matter .File Size: 625KBPage Count: 28











