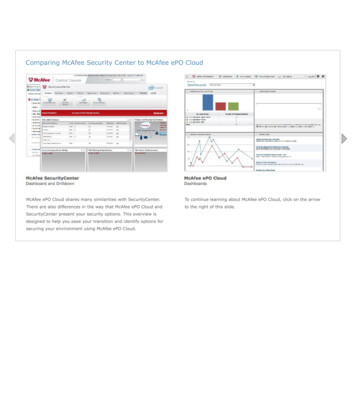
Transcription
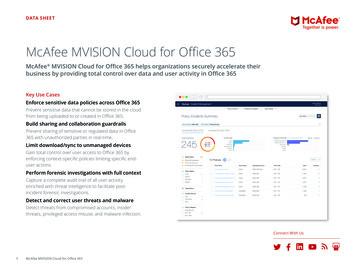
DATA SHEETMcAfee MVISION Cloud for Custom ApplicationsMcAfee MVISION Cloud for Custom Applications helps organizations securely accelerate theirbusiness by providing total control over data and user activity in custom-built cloud servicesKey Use CasesEnforce sensitive data policies in customapplicationsPrevent sensitive data that cannot be stored in the cloudfrom being uploaded to custom applications.Limit download/sync to unmanaged devicesGain total control over user access to customapplications by enforcing context-specific policieslimiting specific end-user actions.Perform forensic investigations with full contextCapture a complete audit trail of all user activityenriched with threat intelligence to facilitate postincident forensic investigations.Detect and correct user threats and malwareDetect threats from compromised accounts, insiderthreats, privileged access misuse, and malware infection.Connect With Us1McAfee MVISION Cloud for Custom Applications
DATA SHEETData Loss Prevention (DLP)Prevent regulated data from being stored in customapplications. Leverage McAfee’s content analyticsengine to discover sensitive data uploaded to a customapplication based on: Keywords and phrases indicative of sensitive orregulated informationPre-defined alpha-numeric patterns with validation(e.g. credit card numbers)Regular expressions to detect custom alpha-numericpatterns (e.g. part numbers)File metadata such as file name, size, and file typeFingerprints of unstructured files with exact andpartial or derivative matchFingerprints of structured databases or otherstructured data filesKeyword dictionaries of industry-specific terms (e.g.stock symbols)“McAfee’s Cloud-Native Data Securitytechnology is helping CaesarsEntertainment protect our valuablecompany data as we move from legacyapplications to cloud applications.”—Les Ottolenghi, Executive Vice President and CIO, CaesarsEntertainment2McAfee MVISION Cloud for Custom ApplicationsDLP remediation options: Notify the end user Notify an administrator Quarantine the file Delete the file
DATA SHEETAccess ControlProtect corporate data from unauthorized access byenforcing granular, context-aware access policies suchas preventing download from custom applications tounmanaged devices.Control access to custom apps based on: Device type (e.g. managed, unmanaged) Activity type (e.g. download, upload) Specific user (e.g. David Carter) User attributes (e.g. role, department) IP address range (e.g. network, proxy) Geographic location (e.g. Ukraine)Enforce granular access policies such as: Allow/block access to custom apps Allow/block specific custom apps user actions Force step-up authentication“We now have the visibility and control weneed to be able to allow access to thecloud-based tools our employees needto be competitive and efficient, withoutcompromising our security standards.”—Rick Hopfer, Chief Information Officer, Molina Healthcare3McAfee MVISION Cloud for Custom Applications
DATA SHEETActivity MonitoringGain visibility into custom application usage andaccelerate post-incident forensic investigations bycapturing a comprehensive audit trail of all activity.McAfee captures hundreds of unique activity typesand groups them into 14 categories for streamlinednavigation. With McAfee, organizations can monitor: Who is accessing a custom app, their role, device type,geographic location and IP addressHow much data is being shared, accessed, created orupdated, uploaded, downloaded, or deletedSuccessful/failed login attemptsUser account creation/deletion as well as updates toaccounts by administratorsDrill down further into activity streams toinvestigate: A specific activity and all its associated users All activities generated by a single user 4All activities performed by users accessing via TOR oranonymizing proxyAll activities generated by a specific source IP addressor geographic locationAll access of and actions performed on a filecontaining sensitive dataMcAfee MVISION Cloud for Custom Applications
DATA SHEETUser Behavior Analytics and Malware DetectionSupervised Machine LearningMcAfee uses data science and machine learning toautomatically build models of typical user behavior andidentifies behavior that may be indicative of a threat.McAfee incorporates security analyst input into machinelearning models to improve accuracy. As analysts markfalse positives and adjust detection sensitivity, McAfeetunes detection models. Insider threats: Detect anomalous behavior acrossmultiple dimensions including the amount of datauploaded/downloaded, volume of user action, accesscount, and frequency across time and cloud services.Compromised accounts: Analyze access attemptsto identify impossible cross-region access, bruteforce attacks, and suspicious locations indicative of acompromised account.Privileged user threats: Identify inappropriate userpermissions, dormant accounts, and unwarrantedescalation of user privileges and provisioning.Malware: Block known malware signatures, sandboxsuspicious files, and identify behavior indicative ofmalware data exfiltration or ransomware activity.“In an environment with millions of uniqueevents each day, McAfee does a nice job ofcutting through the noise and directing usto the areas of greatest security concern.”—Ralph Loura, Chief Information Officer, HP5McAfee MVISION Cloud for Custom ApplicationsNetwork EffectsWith the largest installed base of any cloud securitysolution, McAfee leverages network effects othervendors cannot replicate. With more users, behaviormodels are able to more accurately detect threats.
DATA SHEETUnified Policy EngineMcAfee leverages a central policy engine to applyconsistent policies to all cloud services. There are threeways to define policies that can be enforced on new andpre-existing content, user activity, and malware threats.Policy templatesOperationalize custom applicationpolicy enforcement with pre-builttemplates based on industry, securityuse case, and benchmark.Policy importImport policies from existing securitysolutions or policies from otherMcAfee customers or partners.Policy creation wizardCreate a custom policy with Booleanlogic to conform to any corporate orregulatory requirement. 6Combine DLP, collaboration, and access rules toenforce granular policiesFlexible policy framework leverages triggers andresponse actionsBuild policies using Boolean logic and nested rules andrule groupsEnforce multi-tier remediation based on the severity ofthe incidentSelectively target or exclude specific users and defineexception rulesMcAfee MVISION Cloud for Custom Applications“With McAfee we were able to implementcloud security policies without impactingbusiness user productivity.”—Brian Lillie, Chief Information Officer, Equinix
DATA SHEETIncident Response ManagementIntegrationsMcAfee’s incident response management console offersa unified interface to triage and resolve incidents. WithMcAfee, organizations can:McAfee integrates with your existing security solutionsincluding the leading vendors in:Security information and event management (SIEM) Identify a single policy and all users violating it Secure web gateway (SWG) Analyze all policy violations by a single user Next-generation firewall (NGFW) Review the exact content that triggered a violation Access management (AM) Information rights management (IRM) Enterprise mobility management (EMM/MDM) Rollback an automatic remediation action to restore afile and its permissionsMcAfee streamlines incident response throughautonomous remediation that: 7 Provides end-user coaching and in-app notifications ofattempted policy violationsEnables end users to self-correct the policy violationand resolve the incident alertDramatically reduces manual incident review bysecurity analysts by 97%McAfee MVISION Cloud for Custom Applications
DATA SHEETMcAfee Sky GatewayEnforces policies inline for data in motion in real-time.Universal modeSits inline between the user and a custom applicationand steers traffic after authentication to cover all usersand all devices, without agents.McAfee Ground LinkBrokers the connection between McAfee and onpremises LDAP directory services, DLP solutions,proxies, firewalls, and key management services.McAfee Sky GatewayUniversal ModeVisit us at www.mcafee.com.McAfee Ground Link2821 Mission College Blvd.Santa Clara, CA 95054888.847.8766www.mcafee.com8McAfee MVISION Cloud for Custom ApplicationsMcAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the US and other countries. Othermarks and brands may be claimed as the property of others. Copyright 2018 McAfee, LLC. 3854 1018OCTOBER 2018
6 McAfee MVISION Cloud for Custom Applications DATA SHEET Combine DLP, collaboration, and access rules to enforce granular policies Flexible policy framework leverages triggers and response actions Build policies using Boolean logic and nested rules and rule groups Enforce multi-tier remediation based on the severity of the incident Selectively target or exclude specific users and define