Transcription
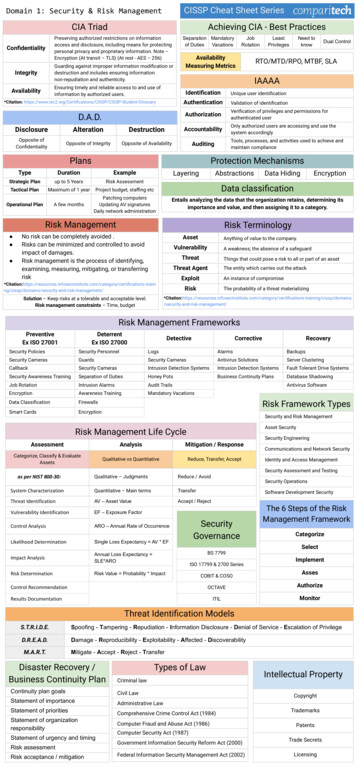
CISSP Cheat Sheet SeriesDomain 1: Security & Risk ManagementCIA TriadAchieving CIA - Best PracticesPreserving authorized restrictions on informationaccess and disclosure, including means for protectingpersonal privacy and proprietary information. Note –Encryption (At transit – TLS) (At rest - AES – 256)ConfidentialitySeparation Mandatoryof DutiesVacationsGuarding against improper information modification ordestruction and includes ensuring informationnon-repudiation and authenticity.IntegrityEnsuring timely and reliable access to and use ofinformation by authorized users.Availability*Citation: ing MetricsLeastPrivilegesNeed toknowDual ControlRTO/MTD/RPO, MTBF, SLAIAAAAIdentificationUnique user identificationAuthenticationValidation of identificationAuthorizationVerification of privileges and permissions forauthenticated userOnly authorized users are accessing and use thesystem bilityOpposite ofConfidentialityOpposite of IntegrityOpposite of AvailabilityAuditingPlansTools, processes, and activities used to achieve andmaintain complianceProtection MechanismsLayeringAbstractionsData HidingEncryptionTypeDurationExampleStrategic Planup to 5 YearsRisk AssessmentTactical PlanMaximum of 1 yearProject budget, staffing etcData classificationOperational PlanA few monthsPatching computersUpdating AV signaturesDaily network administrationEntails analyzing the data that the organization retains, determining itsimportance and value, and then assigning it to a category.Risk Management Risk TerminologyNo risk can be completely avoided .Risks can be minimized and controlled to avoidimpact of damages.Risk management is the process of identifying,examining, measuring, mitigating, or transferringriskAssetAnything of value to the company.VulnerabilityA weakness; the absence of a safeguardThreatThings that could pose a risk to all or part of an assetThreat AgentThe entity which carries out the p/domains/security-and-risk-management/An instance of compromiseRiskThe probability of a threat p/domains/security-and-risk-management/Solution – Keep risks at a tolerable and acceptable level.Risk management constraints – Time, budgetRisk Management FrameworksPreventiveEx ISO 27001DeterrentEx ISO 27000DetectiveCorrectiveRecoverySecurity PoliciesSecurity PersonnelLogsAlarmsBackupsSecurity CamerasGuardsSecurity CamerasAntivirus SolutionsServer ClusteringCallbackSecurity CamerasIntrusion Detection SystemsIntrusion Detection SystemsFault Tolerant Drive SystemsSecurity Awareness TrainingSeparation of DutiesHoney PotsBusiness Continuity PlansDatabase ShadowingJob RotationIntrusion AlarmsAudit TrailsEncryptionAwareness TrainingMandatory VacationsData ClassificationFirewallsSmart CardsEncryptionAntivirus SoftwareRisk Framework TypesSecurity and Risk ManagementAsset SecurityRisk Management Life CycleAssessmentAnalysisMitigation / ResponseCategorize, Classify & EvaluateAssetsQualitative vs QuantitativeReduce, Transfer, AcceptQualitative – JudgmentsReduce / AvoidSystem CharacterizationQuantitative – Main termsTransferThreat IdentificationAV – Asset ValueAccept / RejectVulnerability IdentificationEF – Exposure FactorControl AnalysisARO – Annual Rate of Occurrenceas per NIST 800-30:Single Loss Expectancy AV * EFLikelihood DeterminationIdentity and Access ManagementSecurity OperationsSoftware Development SecuritySecurityGovernanceISO 17799 & 2700 SeriesRisk Value Probability * ImpactRisk DeterminationCommunications and Network SecuritySecurity Assessment and TestingBS 7799Annual Loss Expectancy SLE*AROImpact AnalysisSecurity EngineeringCOBIT & COSOControl RecommendationThe 6 Steps of the RiskManagement rizeITILMonitorResults DocumentationThreat Identification ModelsS.T.R.I.D.E.Spoofing - Tampering - Repudiation - Information Disclosure - Denial of Service - Escalation of PrivilegeD.R.E.A.D.Damage - Reproducibility - Exploitability - Affected - DiscoverabilityM.A.R.T.Mitigate - Accept - Reject - TransferDisaster Recovery /Business Continuity PlanTypes of LawCriminal lawContinuity plan goalsCivil LawStatement of importanceAdministrative LawStatement of prioritiesStatement of organizationresponsibilityStatement of urgency and timingRisk assessmentRisk acceptance / mitigationComprehensive Crime Control Act (1984)Computer Fraud and Abuse Act (1986)Computer Security Act (1987)Government Information Security Reform Act (2000)Federal Information Security Management Act (2002)Intellectual PropertyCopyrightTrademarksPatentsTrade SecretsLicensing
CISSP Cheat Sheet SeriesDomain 2: Asset SecurityClassification LevelsMilitary SectorPrivate SectorTop vateBusiness documents7 yearsInvoices5 yearsAccounts Payable / Receivable7 yearsHuman Resources - Hired7 yearsHuman Resources - Unhired3 yearsTax records4 yearsLegal e ata Security ControlsTypical Data Retention DurationsPublicData in UseScoping & tailoringData at RestEncryptionData in MotionSecure protocols e.g.httpsData OwnershipData OwnershipData CustodianSystems OwnersAdministratorsEnd UserGrant permissions on daily basisTop level/Primary responsibility fordataDefine level of classificationDefine controls for levels ofclassificationDefine baseline security standardsImpact analysisDecide when to destroyinformationEnsure compliance with data policy anddata ownership guidelinesEnsure accessibility, maintain andmonitor securityData archiveTake regular backups , restore to checkEnsure CIAData Classification CriteriaValue - Usefulness - Age - AssociationData Retention PoliciesThe State of Florida Electronic Records and Records Management Practices,2010The European Documents Retention Guide, 2012Security Policies, Standards & GuidelinesRequired by law and industrial standardsNot compulsory, but advisableInformativeAs guidance to othersInformationPolicyDefine best practices for information handling and usage-Security policies: Technical details of the policiesi.e. SYSTEM security policy: lists hardware / software inuse and steps for using policiesStandardsDefine usage levelsGuidelinesNon-compulsory standardsProceduresSteps for carrying out tasls and policiesBaselineSanitizingvalidationsImplement security controlsAdvisoryData RemanenceData documentationConduct user authorizationRegulatoryGrant permissionfor data handlingApply Security ControlsMinimum level of securityDegaussingErasingOverwritingZero fillSeries of processes that removes data,completelyErase form magnetic tapes etc to ensure notrecoverableDeletion of files or mediaWriting over files, shreddingOverwrite all data on drives with zerosDestructionPhysical destruction of data hardware deviceEncryptionMake data unreadable without special keys oralgorithmStandardsNISTNIST SP 800 Series800-14 NIST SP800-18 NIST800-27 NIST SPNational Institute of StandardsTechnologyComputer security in a variety of areasSecuring Information TechnologysystemsDevelop security plansBaseline for achieving security800-88 NISTGuidelines for sanitation and disposition,prevents data remanence800-137Continuous monitoring program: define,establish, implement, analyze and report800-145Cloud computing standardsFIPSFederal Information ProcessingStandards
CISSP Cheat Sheet SeriesDomain 3: Security EngineeringSecurity Models and ConceptsSecurity ModelsSecurity architecture frameworksZachman FrameworkSherwood AppliedBusiness SecurityArchitecture (SABSA)A 2D model considering interrogations such as what, whereand when with, etc. With various views such as planner, owner,designer etc.- Provides access rights including discretionary access controlMATRIXto subjects for different objects.(Access control model) - Read, write and execute access defined in ACL as matrixcolumns and rows as capability lists.To facilitate communication between stakeholdersInformation TechnologyInfrastructure Library Set of best practices for IT service management(ITIL)BELL-LAPADULA(Confidentiality model)Security architecture documentationISO/IEC 27000 SeriesEstablish security controls published by Standardization (ISO)and the Electrotechnical Commission (IEC)Control Objectives forDefine goals and requirements for security controls and theInformation and Relatedmapping of IT security controls to business objectives.Technology (CobiT)BIBA(Integrity model)Types of security modelsState Machine ModelsCheck each of the possible system state and ensure the propersecurity relationship between objects and subjects in eachstate.Allocate each security subject a security label defining thehighest and lowest boundaries of the subject’s access to theMultilevel Lattice Modelssystem. Enforce controls to all objects by dividing them intolevels known as lattices.Matrix Based ModelsArrange tables known as matrix which includes subjects andobjects defining what actions subjects can take upon anotherobject.CLARK WILSON(Integrity model)Consider the state of the system at a point in time for aNoninterference Models subject, it consider preventing the actions that take place atone level which can alter the state of another level.Information Flow ModelsTry to avoid the flow of information from one entity to anotherwhich can violate the security policy.Read and Write are allowed or restricted using a specificmemory location, e.g. Sandboxing.ConfinementData in UseScoping & tailoringSecurity ModesUse a single classification level. All objects can access allDedicated Security Mode subjects, but users they must sign an NDA and approved priorto access on need-to-know basisSystem High SecurityModeAll users get the same access level but all of them do not getthe need-to-know clearance for all the information in thesystem.VirtualizationGuest operating systems run on virtual machines and hypervisors run on one or morehost physical machines.Virtualization securitythreatsBrewer and Nash(A.K.A Chinese wallmodel)Lipner ModelMemory ProtectionDirectly access inbuilt CPU memory to access CPU and ALU.Stack Memory Segment Used by processors for intercommunication.Identification of memory locations by the processor.Register AddressingCPU access registry to get information.Immediate AddressingPart of an instruction during information supply to CPU.Direct AddressingActual address of the memory location is used by CPU.Indirect AddressingSame as direct addressing but not the actual memory location.Base Offset Addressing Value stored in registry is used as based value by the CPU.Commercial mode (Confidentiality and Integrity,) -BLP BibaSQL Injections:Injection / SQL Injection, Broken Authentication, Sensitive DataExposure, XML External Entity, Broken Access Control, SecurityMisconfiguration, Cross-Site Scripting (XSS), InsecureDeserialization, Using Components with Known Vulnerabilities,Insufficient Logging and MonitoringAttackers try to exploit by allowing user input to modify theback-end/server of the web application or execute harmfulcode which includes special characters inside SQL codesresults in deleting database tables etc.SQL Injection prevention: Validate the inputs and parameters.Cross-Site Scripting(XSS)Cross-Request Forgery*Citation CISSP SUMMARY BY Maarten De FrankrijkerAttacks carryout by inputting invalidated scripts insidewebpages.Attackers use POST/GET requests of the http web pages withHTML forms to carry out malicious activity with user accounts.Prevention can be done by authorization user accounts to carrythe actions. Eg. using a Random string in the form, and store iton the server.Cryptographic TerminologyEncryptionConvert data from plaintext to cipher text.DecryptionConvert from ciphertext to plaintext.KeyCryptographyA value used in encryption conversion process.SynchronousEncryption or decryption happens simultaneously.AsynchronousEncryption or decryption requests done subsequently or after awaiting period.SymmetricCryptography Goals(P.A.I.N.)AsymmetricalKey pair use for encrypting and decrypting. (One private andone public key)Digital SignatureUse to verify authentication and message integrity of thesender. The message use as an input to a hash functions forvalidating user authentication.HashA one-way function, convert message to a hash value used toverify message integrity by comparing sender and receivervalues.Classical CiphersDigital CertificateAn electronic document that authenticate certification owner.Modern CiphersPlaintextSimple text message.Normal text converted to special format where it is unreadablewithout reconversion using keys.CiphertextCryptosystemThe set of components used for encryption. Includesalgorithm, key and key management functions.CryptanalysisBreaking decrypting ciphertext without knowledge ofcryptosystem used.Use of CryptographyThe science of hiding the communication messages fromunauthorized recipients.CryptologyCryptography CryptanalysisDecipherConvert the message as readable.EncipherConvert the message as unreadable or meaningless.One-time pad (OTP)Encipher all of the characters with separate unique keys. Confidentiality Integrity Proof of origin Non-repudiation Protect data at rest Protect data in transitSubstitution cipher, Transposition cipher, Caesar Cipher,Concealment.Substitution CiphersUses a key to substitute letters or blocks of letters withdifferent letters or block of letters. I.e. One-time pad,stenography.Reorder or scramble the letters of the original message wherethe key used to decide the positions to which the letters aremoved.Common AlgorithmsSymmetric/Algorithm Asymmetric Key lengthSymmetric64 bitDifferent encryption keys generate the same plaintextmessage.Key ClusteringKey SpaceEvery possible key value for a specific algo
Domain 3: Security Engineering CISSP Cheat Sheet Series Security Models and Concepts Security architecture frameworks Zachman Framework A 2D model considering interrogations such as what, where and when with, etc. With various views such as planner, owner, designer etc. Sherwood Applied Business Security Architecture (SABSA)