Transcription
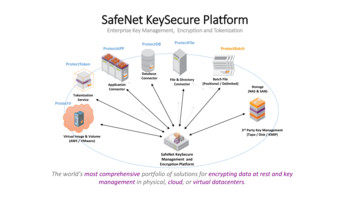
SafeNet KeySecure PlatformEnterprise Key Management, Encryption and torProtectVFile & DirectoryConnectorBatch File(Positional / Delimited)Storage(NAS & SAN)TokenizationService3rd Party Key Management(Tape / Disk / KMIP)Virtual Image & Volume(AWS / VMware)SafeNet KeySecureManagement andEncryption PlatformThe world’s most comprehensive portfolio of solutions for encrypting data at rest and keymanagement in physical, cloud, or virtual datacenters.
SafeNet KeySecure & Encryption ConnectorIntegration Portfolio Support DetailIBMBEASunApacheOracleJavaJboss SafeNetProtectAppWeb &Application ServersIBM DB2 Oracle Microsoft SQL racleJavaJbossCassandra SafeNetTokenizationApplicationServersGemalto offers the world’s most certifiedand widely deployed portfolio of cryptomanagement solutions for securing andmanaging encryption keys and alsoexecuting cryptographic functions.IBM DB2OracleMicrosoft SQL ServerLinuxSambaWindows ServerNovellApache HadoopCassandramongoDBMicrosoft SharePointAmazon EC2 & S3ChefDockerSafeNetProtectFileFile Servers& Shares KMIP EnabledHitachiNetAppHPIBMQuantumNutanixDellOthers Amazon Web ServicesMicrosoft Azure VMware IBM SoftLayer StoragePartnersSafeNetProtectVNetwork AttachedStorageMultiple programminglanguagesSOAP and REST interfacesOPEN XML interfaceKMIP interfaceTape LibrariesStorageCloud inesApps GW TapeDisk KMIP TDEKey and crypto engineAuthentication and authorizationKey lifecycle managementSNMP, NTP, SYSLOG SafeNet KeySecure PlatformDistributed Key Management
How Information flows .Source (Inception)Application/WebSecurity Bespoke 3rd PartyDatabases OLTP DW reporting Batch processing XMLFile/Directories File Servers (shared storage) Client machines (laptop) prop/log file , App/DB files, xml,word, excel, pdf Storage Full Disk encryption (FDE) backup encryptionUnstructured DataDestinationDeployment EffortStructured Data
SafeNet KeySecure Platform ComponentsKey Management Appliance Secure operating system – hardened CentOSScalable / Built-in clustering / hardware redundancySelection of models – Physical and Virtual (FIPS Level 3)Administration and key policy / access through GUICentralized key managementCentralized Auditing and LoggingConnectors Software component that communicate with the KeySecure Appliance Provides a point of integration into an end point via ProtectAPP,ProtectDB, ProtectFile, ProtectToken, ProtectV and StorageSecure & 3rdparty key management - KMIP Provides load balancing, health checking, connection pooling Secure SSL connection to SafeNet Appliance4
SafeNet KeySecure ProvidesCentralized Key Management & Crypto Engine ApplianceCentralized Key ManagementCentrally manages symmetric, asymmetric keys and certificates Generate, Export, Import, Destroy, Backup/Restore etc. Support KMIP Standard Built-in key rotation – versioned keys - Automation Crypto Offload EngineEncryption & Decryption Services Configurable for offload or local crypto Authentication & AuthorizationMulti-factor system-to-system authentication and access control Certificate based mutual authentication Embedded username or IP within client certificate Support for LDAP/AD user authentication Granular, key-based cryptographic policy Time limit policies Rate limit policies Dual Administrative Control Multiple credentials for sensitive operation
SafeNet Platform yAvailabilityHardware-based, centralized key and policy management FIPS/CC certified solution Authentication and authorization High performance encryption offload, over 100K TPS Batch processing for massive amounts of data Efficient backup/restore capabilities, local encryption option Support for heterogeneous environments (app, db, file) Support for open standards and APIs Range of enterprise deployment models Intuitive, easy-to-use administration Separation of duties Centralized policy management Enterprise clustering and replication Load balancing, health checking, and failover Geographically distributed redundancy
Built-in Granular Key Control SecurityCentralized key and policy EnforcementSecurity administrators control data protection policyKeys created and stored in a single locationDual Administrative Control (M of N approvals)Separation of DutiesLogging, Auditing and Alerts FIPS & Common Criteria Certified SolutionFIPS 140-2 Level 2 & CC EAL2 Certified Hardware and SoftwareKeys stored separately from sensitive dataAES, 3DES, RSA and others – Standard Algorithms and Modes!!Built-in Certificate Authority Authentication & AuthorizationMulti-factor system-to-system authentication and access control Granular, key-based, cryptographic policy Support for LDAP
PerformanceBuilt-in High PerformanceEncryption OffloadOptimized, high-performance hardware Frees up database and application servers Latency less than 200 microseconds per request More than 100K TPS per appliance Local Encryption Option (works when key manager is on or off)Configurable for hardware offload or local encryption on client servers Batch ProcessingPerform batch encrypts/decrypts for high performance 10K of thousands of operations a second Batch tools include: Transform Utility ICAPI Easy integration into existing applications
FlexibilityBuilt-in to be a ServiceHeterogeneous Integration EnvironmentsWeb, Application, Database, Mainframe or File Server and disks Encryption and Format Preserving Tokenization (FPT) Data Center or Distributed Environments Open Standards-based APIs, cryptographic protocols Key Management for 3rd party applications ScalabilityYou can start small and roll across as you grow. Become key management standard, rollout across the enterprise.Models with capacity from 2,500 TPS to 100,000 TPS Clustering further increases capacity and redundancy Licensing structure enables cost-effective build-out
ManageabilityBuilt-in GUI for AdministrationIntuitive Administration and AutomationGraphical and command line interfaces Point-and-click policy management Encryption rights management Key management Network and system management Simple configuration, analogous to a switch or router Separation of DutiesSecurity administrators administrate security Maximize productivity, minimize liability Keys, policies separate from data Extensible Management PlatformCohesive, consistent elements across the enterprise Common management protocols, processes Standard implementation, integration methodology
AvailabilityBuilt-in Availability & RedundancyClusteringActive-Active clustering deployment DataCenter AKeys and policies are shared and automatically replicated among KeySecures ina global clusterLoad BalancingConnectors can load balance across a group of appliancesMulti-tier load balancing enables transparent fail over to alternatedatacentersDataCenter BKeySecure Cluster
KeySecure: Enterprise Key ManagementCentrally Manage Keys for partner solutions
4 SafeNet KeySecure Platform Components Key Management Appliance Secure operating system -hardened CentOS Scalable / Built-in clustering / hardware redundancy Selection of models -Physical and Virtual (FIPS Level 3) Administration and key policy / access through GUI Centralized key management Centralized Auditing and Logging Connectors