Transcription
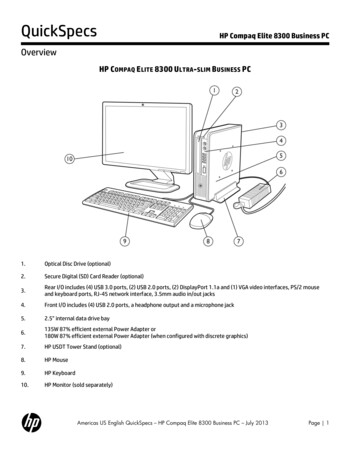
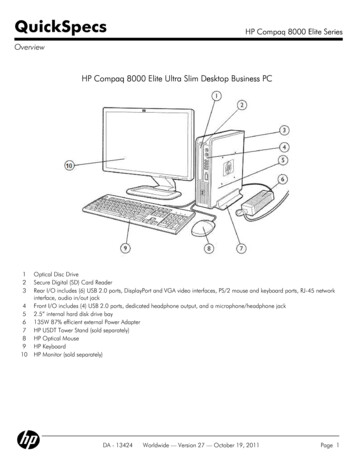
How Rugged Cultures DriveBiz & AppSec Value
Director of Security Intelligence for Akamai Technologies Former Research Director, Enterprise Security [The 451 Group]Former Principal Security Strategist [IBM ISS] Industry: Co-Founder of “Rugged Software” www.ruggedsoftware.orgFaculty: The Institute for Applied Network Security (IANS)2009 NetworkWorld Top 10 Tech People to KnowPonemon Institute FellowBLOG: www.cognitivedissidents.com Things I’ve been researching: DevOpsSecurity IntelligenceChaotic ActorsEspionageSecurity Metrics
PassionatePurposefulPrincipledProtectorProvider
HonestCourageousConsequential
UnreasonableA Fool
No
Is it getting better?Or do you feel thesame?
Will it make it easieron you now?You got someone toblame
How would youknow?By which criteria?
s12
WHYHOWWHATWHAThttp://www.ted.com/talks/simon sinek how great leaders inspire action.html
eplaceability-continuum/
PerformanceFungible AssetsIntellectualProperty & TradeSecretsRights & CivilitySafety & Human Life
Dependence
s/Software/Vulnerability/
s/Connected/Exposed/
Our challenges are nottechnical but cultural
OWASP Top 10“We can eliminateSQLi in our lifetime”
ActivityEffect
SymptomsRoot Causes
EasyImportant
Best Practicesaren’t
Good Enoughisn’t
Incentives
Pick one:Make ExcusesMake Progress
GET A MAP
HDMoore’s Law100Success Rate (%)90807060Adversary ClassesEspionageAPT/APA50OrganizedCrimeChaotic ActorsOrganized CrimeCasual A12345678Defender nts.com/2011/11/01/intro-to-hdmoores-law/
rastructureExcellenceAwareness
Operational astructureAwareness
Situational AwarenessOperational ExcellenceDefensibleCountermeasuresInfrastructure
CountermeasuresSituational AwarenessOperational ExcellenceDefensible Infrastructure
ExperimentationAn untested hypothesis is a wish
RUGGED SOFTWARE
FAST
AGILE
Are You Rugged?
HARSH
UNFRIENDLY
I recognize that my code will be used in ways Icannot anticipate, in ways it was not designed,and for longer than it was ever intended.
rg/issues/marchapril-2011.html
SECURITYCOSTINHIBITOR
Source: Wendy Nather (at the time, a CISO)
Vertical: Financial Business: Money management firm Implemented Rugged DevOps to quicken the changecycle and tighten the security Results: Increased from quarterly change cycle, to daily changes,46 average a month. Reduced failed changes from 17% to 4% Reduced IT audit exceptions to zero
A declaration ofintent &recognition
The RuggedSummit
We don’t all agree
PICTURE OF ASTRAWMANDorothy, why do some AppSec guru’s hate Rugged?
PICTURE OF ACampfire “story”
From the Rugged Handbook StrawMan
Executives CIO/CTO Security “Analysts” Architects Developers Testers Program Managers
CIOArchitectDeveloperQA
Buying and selling software Understanding the entire software supply chain Network security, physical security, database security,etc Other types of software projects, including legacycode, outsourced code, libraries, etc Enterprise level security as opposed to individualprojects
OldPurchasedNewPurchasedOld BuiltNew Built
ExperimentationAn untested hypothesis is a wish
Make it better
THANK YOUMy Collaborators
Joshua Corman[Knowledge Seeker Zombie Killer]Twitter: @joshcormanBLOG: http://blog.cognitivedissidents.com@RuggedSoftware @RuggedDevOpshttp://RuggedSoftware.org
Implemented Rugged DevOps to quicken the change cycle and tighten the security Results: Increased from quarterly change cycle, to daily changes, 46 average a month. Reduced failed c