Transcription
White paperCisco publicHow to BuyCisco Webex Meetings SecurityIntroductionCisco Webex Meetings helps enable global employees and virtual teams to collaborate in realtime as though they were working in the same room. Businesses, institutions, and governmentagencies worldwide rely on Cisco Webex Meetings solutions. These solutions help simplify businessprocesses and improve results for sales, marketing, training, project management, and support teams.For all these companies and agencies, security is a fundamental concern. Online collaboration mustprovide multiple levels of security for tasks that range from scheduling meetings to authenticatingparticipants to sharing documents.Cisco makes security the top priority in the design, development, deployment, and maintenance of itsnetworks, platforms, and applications. You can incorporate Cisco Webex Meetings solutions into yourbusiness processes with confidence, even with the most rigorous security requirements.This paper provides details about the security measures of Cisco Webex Meetings and its underlyinginfrastructure to help you with an important part of your investment decision.Note: The terms “Cisco Webex Meetings” and “Cisco Webex Meetings sessions” refer to theintegrated audio conferencing, Internet voice conferencing, and video conferencing used in allCisco Webex Meetings online products. Unless otherwise specified, the security features wedescribe pertain equally to all the Cisco Webex Meetings applications listed in this paper.What you will learnThis paper describes the security featuresof Cisco Webex applications and relatedservices. It discusses the tools, processes,and engineering that help customersconfidently collaborate on the Cisco WebexMeetings platform.Cisco Webex Meetings applications include:Cisco Webex MeetingsCisco Webex EventsCisco Webex TrainingCisco Webex Support (including CiscoWebex Remote Access) Cisco Webex Edge Cisco Webex Cloud Connected Audio 2019 Cisco and/or its affiliates. All rights reserved.
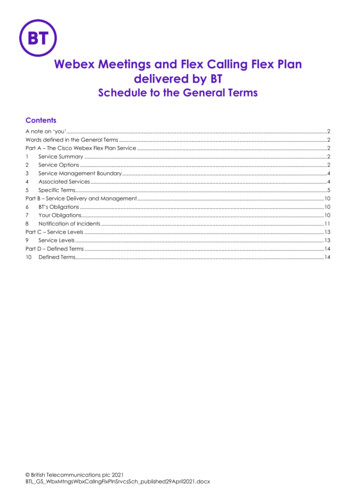
White paperCisco publicContentsIntroductionWhat You Will LearnCisco Webex Security ModelCisco Security and TrustCisco Webex Security ModelCisco remains firmly committed to maintaining leadership in cloud security.Cisco’s Security and Trust organization works with teams throughout ourcompany to build security, trust, and transparency into a framework thatsupports the design, development, and operation of core infrastructures tomeet the highest levels of security in everything we do.This organization is also dedicated to providing our customers with theinformation they need to mitigate and manage cybersecurity risks.Cisco security tools andprocessesThe Cisco Webex security model (Figure 1) is built on the same securityfoundation deeply engraved in Cisco’s processes.Internal and externalpenetration testsThe Cisco Webex organization consistently follows the foundational elementsto securely develop, operate, and monitor Cisco Webex services. We will bediscussing some of these elements in this document.Figure 1. Cisco Security ModelPhysical securityInfrastructure andplatform securityCisco Webex ApplicationSecurityCryptographyCisco WebexRole-Based AccessAdministrative CapabilitiesAdditional Cisco Webexfeatures and securityCisco Webex privacyIndustry standards andcertificationsConclusionFor More InformationMultilayer Security ModelApplication securityCryptographyadministrative controlsend-user controlsData center securityPhysical securityinfrastructure and platform securityCisco security and trustTools/Processes to securelydevelop, and operateOrganizational structure to instillsecurity in Cisco DNAISOCertified“Security and trust will differentiate Cisco as the number one IT company”Cisco Security and TrustCisco security tools and processesCisco secure development lifecycleAt Cisco, security is not an afterthought. It is a disciplined approach to buildingand delivering world-class products and services from the ground up. AllCisco product development teams are required to follow the Cisco SecureDevelopment Lifecycle. It is a repeatable and measurable process designed toincrease the resiliency and trustworthiness of Cisco products. The combinationof tools, processes, and awareness training introduced in all phases of thedevelopment lifecycle helps ensure defense in depth. It also provides a holisticapproach to product resiliency. The Cisco Webex Product Development teampassionately follows this lifecycle in every aspect of product development.Read more about the Secure Development Lifecyle. 2019 Cisco and/or its affiliates. All rights reserved.SOC 2Type IIOperational excellence and monitoringCisco Webex Data CenterSecurity
White paperCisco publicCisco foundational security toolsThe Cisco Security and Trust organization providesthe process and the necessary tools that give everydeveloper the ability to take a consistent position whenfacing a security decision.Having dedicated teams to build and provide suchtools takes away uncertainty from the process ofproduct development.Some examples of tools include: Product Security Baseline (PSB) requirements thatproducts must comply with Threat-builder tools used during threat modeling Coding guidelines Validated or certified libraries that developers can useinstead of writing their own security code Security vulnerability testing tools (for static anddynamic analysis) used after development to testagainst security defects Software tracking that monitors Cisco and thirdparty libraries and notifies the product teams when avulnerability is identifiedOrganizational structure that instills security inCisco processesCisco has dedicated departments in place to instilland manage security processes throughout the entirecompany. To constantly stay abreast of security threatsand challenges, Cisco relies on: Cisco Information Security (InfoSec) Cloud team Cisco Product Security Incident Response Team (PSIRT) Shared security responsibilityCisco InfoSec CloudLed by the chief security officer for cloud, this teamis responsible for delivering a safe Cisco Webexenvironment to our customers. InfoSec achieves this bydefining and enforcing security processes and tools forall functions involved in the delivery of Cisco Webex intoour customers’ hands.Additionally, Cisco InfoSec Cloud works with otherteams across Cisco to respond to any security threats toCisco Webex. 2019 Cisco and/or its affiliates. All rights reserved.Cisco InfoSec is also responsible for continuousimprovement in Cisco Webex’s security posture.Cisco Product Security Incident ResponseTeam (PSIRT)Cisco PSIRT is a dedicated global team that managesthe inflow, investigation, and reporting of security issuesrelated to Cisco products and services. PSIRT usesdifferent mediums to publishInformation, depending on the severity of the securityissue. The type of reporting varies according to thefollowing conditions: Software patches or workarounds exist to address thevulnerability, or a subsequent public disclosure of codefixes is planned to address high-severity vulnerabilities PSIRT has observed active exploitation of avulnerability that could lead to a greater risk for Ciscocustomers. PSIRT may accelerate the publication of asecurity announcement describing the vulnerability inthis case without full availability of patches Public awareness of a vulnerability affecting Ciscoproducts may lead to a greater risk for Ciscocustomers. Again, PSIRT may alert customers, evenwithout full availability of patchesIn all cases, PSIRT discloses the minimum amount ofinformation that end users will need to assess the impactof a vulnerability and to take steps needed to protecttheir environment. PSIRT uses the Common VulnerabilityScoring System (CVSS) scale to rank the severity of adisclosed issue. PSIRT does not provide vulnerabilitydetails that could enable someone to craft an exploit.Learn more about PSIRT online at cisco.com/go/psirt.Security responsibilityAlthough every person in the Cisco Webex group isresponsible for security, following are the main roles: Chief security officer, Cloud Vice president and general manager, Cisco CloudCollaboration Applications Vice president, engineering, Cisco CloudCollaboration Applications Vice president, product management, Cisco CloudCollaboration Applications
White paperCisco publicInternal and external penetration testsThe Cisco Webex group conducts rigorous penetrationtesting regularly, using internal assessors. Beyondits own stringent internal procedures, Cisco InfoSecalso engages multiple independent third parties toconduct rigorous audits against Cisco internal policies,procedures, and applications. These audits are designedto validate mission-critical security requirements forboth commercial and government applications. Ciscoalso uses third-party vendors to perform ongoing, indepth, code-assisted penetration tests and serviceassessments. As part of the engagement, a third partyperforms the following security evaluations: Identifying critical application and service vulnerabilitiesand proposing solutions Recommending general areas for architecturalimprovement Identifying coding errors and providing guidance oncoding practice improvementsThird-party assessors work directly with the CiscoWebex engineering staff to explain findings and validatethe remediation. As needed, Cisco InfoSec can provide aletter of attestation from these vendors.Cisco Webex Data CenterSecurityCisco Webex is a Software-as-a-Service (SaaS) solutiondelivered through the Cisco Webex Cloud, a highlysecure service-delivery platform with industry-leadingperformance, integration, flexibility, scalability, andavailability. The Cisco Webex Cloud is a communicationsinfrastructure purpose-built for real-time webcommunications.Cisco Webex meeting sessions use switching equipmentlocated in multiple data centers around the world. Thesedata centers are strategically placed near major Internetaccess points and use dedicated high-bandwidth fiberto route traffic around the world. Cisco operates theentire infrastructure within the Cisco Webex Cloud withindustry-standard enterprise security. 2019 Cisco and/or its affiliates. All rights reserved.Additionally, Cisco operates network Point-of-Presence(PoP) locations that facilitate backbone connections,Internet peering, global site backup, and cachingtechnologies to enhance performance and availability forend users.Physical securityPhysical security at the data center includes videosurveillance for facilities and buildings and enforcedtwo-factor identification for entry. Within Cisco datacenters, access is controlled through a combinationof badge readers and biometric controls. In addition,environmental controls (for example, temperaturesensors and fire-suppression systems) and servicecontinuity infrastructure (for example, power backup)help ensure that systems run without interruption.Within the data centers are also “trust zones,” or segmentedaccess to equipment based on infrastructure sensitivity. Forexample, databases are “caged”: the network infrastructurehas dedicated rooms and racks are locked. Only Ciscosecurity personnel and authorized visitors accompanied byCisco personnel can enter the data centers.Cisco’s production network is a highly trusted network:only very few people with high trust levels have accessto the network.Infrastructure and platform securityPlatform security encompasses the security of the network,systems, and the overall data center within the CiscoWebex Cloud. All systems undergo a thorough securityreview and acceptance validation prior to productiondeployment, as well as regular ongoing hardening, securitypatching, and vulnerability scanning and assessment.All systems undergo a thorough security review andacceptance validation prior to production deployment.Servers are hardened using the Security TechnicalImplementation Guidelines (STIGs) published by theNational Institute of Standards and Technology (NIST).Firewalls protect the network perimeter and firewalls.Access Control Lists (ACLs) segregate the differentsecurity zones. Intrusion Detection Systems (IDSs) arein place, and activities are logged and monitored on a
White paperCisco publiccontinuous basis. Daily internal and external securityscans are conducted of Cisco Webex Cloud. All systemsare hardened and patched as part of the regularmaintenance. Additionally, vulnerability scanning andassessments are performed continuously.Service continuity and disaster recovery are criticalcomponents of security planning. The Cisco datacenters’ global site backups and high-availability designhelp enables the geographic failover of Cisco Webexservices. There is no single point of failure.Cisco Webex Application SecurityCryptographyEncryption at run timeAll communications between Cisco Webex applicationsand Cisco Webex Cloud occur over encrypted channels.Cisco Webex uses TLS 1.2 protocol and uses highstrength ciphers (for example, AES 256).1After a session is established over TLS, all mediastreams (audio VoIP, video, screen share, and documentshare) are encrypted.2User Datagram Protocol (UDP) is the preferred protocolfor transmitting media. In UDP, media packets areencrypted using AES 128. The initial key exchangehappens on a TLS-secured channel. Additionally, eachdatagram uses Hashed- Based Message AuthenticationCode (HMAC) for authentication and integrity.End-to-end encryptionMedia streams flowing from a client to Cisco Webexservers are decrypted after they cross the Cisco Webexfirewalls. Cisco can then provide network- basedrecordings, and all media streams can be recordedfor future reference. Cisco Webex then re-encryptsthe media stream before sending it to other clients.However, for businesses requiring a higher level ofsecurity, Cisco Webex also provides end-to-endencryption. With this option, Cisco Webex Cloud doesnot decrypt the media streams. As it does for normalcommunications, it establishes a TLS channel for clientserver communication.Additionally, all Cisco Webex clients generate keypairs and send the public key to the host’s client.The host generates a random symmetric key usinga Cryptographically Strong Secure Pseudo-RandomNumber Generator (CSPRNG), encrypts it using thepublic key that the client sends, and sends the encryptedsymmetric key back to the client.The traffic generated by clients is encrypted using thesymmetric session key. In this model traffic cannot bedeciphered by the Cisco Webex server.This end-to-end encryption option is available for CiscoWebex Meetings and Cisco Webex Support. Note thatwhen end-to-end encryption is enabled, the followingfeatures are not supported: Web App Network-based recordings Join Before Host Video EndpointsDifferent ciphersCisco Webex supports following cipher suites forsecured communications. Cisco Webex will allowthe strongest possible cipher for the customer’senvironment. Table 1 outlines cipher suites and eachsuite’s bit length.1 Actual encryption protocol and strength depend on the OS and browser settings, based on which a host negotiates connections with Cisco Webex.2 sers connecting to a cloud meeting using a third-party video endpoint may be sending and receiving unencrypted media streams. ConfiguringUyour firewall to prevent unencrypted traffic to and from Cisco Webex helps keep your meetings safe. However, allowing attendees outside yourfirewall to join your meeting using third-party devices can still send your meeting data unencrypted on the Internet. 2019 Cisco and/or its affiliates. All rights reserved.
White paperCisco publicTable 1. Cipher suites and bit lengthsCipher suitesBit lengthTLS RSA WITH AES 256 CBC SHA256 (0x3d)256TLS ECDHE RSA WITH AES 256 CBC SHA384 (0xc028)256TLS ECDHE RSA WITH AES 256 GCM SHA384 (0xc030)256TLS RSA WITH AES 128 GCM SHA256 (0x9c)128TLS RSA WITH AES 256 GCM SHA384 (0x9d)256TLS ECDHE RSA WITH AES 128 GCM SHA256 (0xc02f)128TLS RSA WITH AES 128 CBC SHA256 (0x3c)128TLS ECDHE RSA WITH AES 128 CBC SHA256 (0xc027)128TLS RSA WITH AES 256 CBC SHA (0x35)256TLS RSA WITH AES 128 CBC SHA (0x2f)128TLS ECDHE RSA WITH AES 256 CBC SHA (0xc014)256TLS ECDHE RSA WITH AES 128 CBC SHA (0xc013)128Protecting data at restCisco Webex Role-Based accessWhen configured by the customer to do so, CiscoWebex Meetings stores meeting and user data that maybe critical to your business. Cisco Webex Meetings usesthe following safeguards to protect data at rest:Cisco Webex application behavior is built from theground up around five roles, each of which is granteddifferent privileges. They are described below. Stores all user passwords using SHA-2 (one-wayhashing algorithm) and saltsThe host schedules and starts a Cisco Webex meeting.The host controls the meeting experience for everyoneand makes relevant decisions while scheduling themeeting and during it. Encrypts other passwords such as for meetingsor recordings Encrypts stored Network Based Recordings. Webexrecordings are encrypted both at the file level andat the logical volume level. The file key is a 256-bitblock AES GCM key. This file key is then encryptedwith a master key based on AES HmacSHA256 that isrotated based on policy and saved to a DB. During theplayback and download flow, the encrypted recordingfile is then decrypted before or during the operation.Cisco maintains these keys for the customer.HostThe site administrator (a role described later) canmandate many of these controls. If they are notmandated, then the host can make choices on how tosecure meetings.Alternate hostWhile scheduling, the host can assign alternate hosts,who can start the meeting in lieu of the host andessentially have the same set of privileges as the host.A host can also pass on his or her privileges to anotheruser during the meeting. With respect to security, thereis no difference between the host and alternate host. 2019 Cisco and/or its affiliates. All rights reserved.
White paperCisco publicPresenterThe site administrator can carry out the following actions:A presenter can share presentations, specificapplications, or an entire desktop. The presenter controlsthe annotation tools. From a security standpoint, thepresenter can grant and revoke remote control over theshared applications and desktop to individual attendees. Lock out an account after a configurable number offailed login attemptsPanelist (in training and events only) Require a user to change the password at the next loginA panelist is primarily responsible for helping the hostand presenter keep the event running smoothly. Anynumber of attendees can be panelists. The host mayask panelists to serve as subject matter experts, viewingand answering attendee questions in a Q and A session;respond to public and private chat messages; annotateshared content; or manage polls as the polling coordinator.AttendeeAttendees have no security responsibilities or privilegesunless they are assigned the presenter or host role.Ultimately, the site administrator and the host can allowan attendee to grab the Cisco Webex ball (presenterrole) anytime in the course of the meeting. This setting isoff by default.Site administratorThis role is authorized for managing accounts as well asfor managing and enforcing policies on a site basis orper-user basis. The administrator can choose the CiscoWebex capabilities that are available to all other rolesand users.Administrative capabilitiesCisco Webex has granular site administration capabilitiesto effectively align your Cisco Webex site with yourbusiness needs. This section describes the mainsecurity-related features. For further information on allsecurity features, please refer to the Cisco Webex siteadministration guide here.Account managementYou can integrate your identity management technologywith Cisco Webex to allow single sign-on and giveyou full control over account management and accesspolicies. When your accounts are kept in Cisco Webex,a number of site administration capabilities allow you tomanage accounts accordi
Webex engineering staff to explain findings and validate the remediation. As needed, Cisco InfoSec can provide a letter of attestation from these vendors. Cisco Webex Data Center Security Cisco Webex is a Software-as-a-Service (SaaS) solution delivered through the Cisco Webex Cloud, a high