Transcription
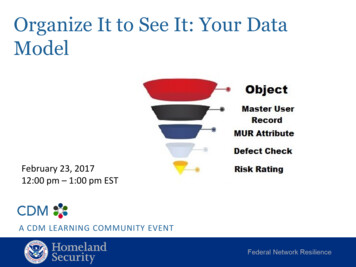
Organize It to See It: Your DataModelFebruary 23, 201712:00 pm – 1:00 pm ESTA CDM LEARNING COMMUNITY EVENT
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELToday’s Webinar GoalsProvide audience witha comprehensiveoverview of the CDMData ModelAnswer allaudience questionsduring the allottedquestion andanswer time2
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELWe’ll answer these questions What is the CDM Data Model? What is a common-schema? What is data interrogation? What objectives help drive the CDMData Model?3
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELToday’s Speaker: Richard A. Grabowski III Systems Engineer with the CDM Program Primarily supporting the CDM Dashboard Supported Task Order 2 Group C (TO2C) Supported source selection for Task Order 2 Group D (TO2D)CDM Program Management Office (PMO) since 20149 years with Lockheed Martin specializing in client/serverintegration VMware / Citrix / Cisco / NetApp Windows AdministrationCertifications RSA Certified Administrator (e.g., Archer)4
What is the CDM Data Model?“CDM Data Model” refers to:A Logical Data Model (LDM)A Data Model DocumentHomelandSecurityOffice of Cybersecurity and Communications5
CDM Principles Common-Schema: “To ensureconsistent results, data collected byCDM must be normalized into a dataschema that is common across allparticipating agencies.” Data Interrogation Actions: Usersinterrogate data collected by CDMthrough three methods:–––Defect checks to support risk managementand ongoing authorization,Cybersecurity performance metrics to supportFederal Information Security Management Act(FISMA) metric reporting, andAd-hoc federated queries to support securityoperations.HomelandSecurityOffice of Cybersecurity and Communications6
The CDM Data Model Defines a common baseline that can be implemented– Must be met – standardization across all CDM solutions– Flexible to allow agencies to supplement (within reason) Outlines data interrogation actions for the common-schema– “How can I use CDM?” Models CDM PMO data requirementsRepresents a joint effort between the CDM PMO and JohnsHopkins University, in concert with the CDM “Principles”Has an iterative process – never “final”– Phase 1 – v1.1 Current– Phase 2 – v2.0 To be released for comment soon Is not a physical data model (e.g., schema in a databasemanagement system (DBMS))HomelandSecurityOffice of Cybersecurity and Communications7
Common-Schema CDM will collect this data baseline CDM will create these relationshipsHomelandSecurityOffice of Cybersecurity and Communications8
Data InterrogationHomelandSecurityOffice of Cybersecurity and Communications9
Scenario: CVE-2017-0016HomelandSecurityOffice of Cybersecurity and Communications10
CDM Data Model Objectives?HomelandSecurityOffice of Cybersecurity and Communications11
Program Fundamentals – Dashboard InteroperabilityHomelandSecurityOffice of Cybersecurity and Communications12
Program Fundamentals – Summary Data“The contractor shall ensure that only summary level data is being sent fromthe D/A CDM Dashboard to the Federal CDM Dashboard”*What is “summary data”? Counts? (e.g., Common Vulnerabilities andExposures (CVEs) / Common PlatformEnumerations (CPEs) / Common ConfigurationEnumerations (CCEs)) Summary Scores? Others? Context?* Continuous Diagnostics and Mitigation (CDM), “Task Order GSQ0015AJ0097: Tools and Continuous Monitoring as aService (CMaaS) for Group C Phase 1 Implementation.”HomelandSecurityOffice of Cybersecurity and Communications13
Program Fundamentals – Attachment N Contains hundreds ofrequirements of varying specificityValidates product on the CDMBlanket Purchase Agreement(BPA)Facilitates product buy oncontracts or through DelegatedProcurement Authority (DPA)Each Integrator must submit toolsand have them approved beforetools can be included in thesolutionSubmission “attests” that toolcovers at least one of thefunctional requirementsHomelandSecurityOffice of Cybersecurity and Communications14
Program Fundamentals – FISMA Reporting Key Input into the CDM DataModelSeparate “FISMAQuestionnaires” (e.g., Chiefinformation officer (CIO)) intotheir respective phasesGoal: “Automate and Minimize”HomelandSecurityOffice of Cybersecurity and Communications15
Program Fundamentals – Risk Scoring Key element of the dashboard and CDM Can drive changes to the data model Development still pendingHomelandSecurityOffice of Cybersecurity and Communications16
Program Challenges – Technology Different commercial off-theshelf tools (COTs) with differentcapabilities (and objectives)within the CMaaS solutionInherent limitations in vendorproducts Build to scaleComplexity to implementAbility to customizeHomelandSecurityOffice of Cybersecurity and Communications17
Program Challenges – ExpectationsHomelandSecurityOffice of Cybersecurity and Communications
Program Challenges – Catchup Contract Awards (TO2,Dashboard)– Modeling effort ideally would haveoccurred before integration efforts(or at least simultaneously)– Program has been working to getahead– TO2 contracts are nearing theirend; how to continue to provideneeded integration effort Changes in Design– Proposed designs might have to befine-tuned, altered to accommodatethese specific data requirementsHomelandSecurityOffice of Cybersecurity and Communications19
Program Needs – Common LanguageBuzzwords: “Authorized” “Managed” “Approved” “Misconfiguration” “Vulnerability”HomelandSecurityOffice of Cybersecurity and Communications20
Program Needs – GuidanceConstructs: Master Device Record (MDR) Master User Record (MUR) CVE / CCE DictionariesHomelandSecurityOffice of Cybersecurity and Communications21
Program Needs – GuidanceContext: Organizational UnitContainers FISMA ContainersHomelandSecurityOffice of Cybersecurity and Communications22
Program Needs – GuidanceDefineCorrelation:HomelandSecurityOffice of Cybersecurity and Communications23
Program Needs – Flexibility “Find all endpoints where software product Adobe FlashPlayer deployed within the last 30 days”HomelandSecurityOffice of Cybersecurity and Communications24
Program Needs – Addressing the Future Future integration with other U.S. Department of Homeland Security(DHS) cybersecurity programs:– CyberScope / Einstein / United States Computer Emergency Readiness Team(US-CERT) Other CDM Program “use cases” (e.g., Office of Management and Budget(OMB) 16-12)Feedback– Understand nuances at agencies– Solicit needs (e.g., Formal Enhancement Request form) Changes to any of the “3 Critical Inputs– FISMA data gathering New metrics, new Cross-Agency Priority (CAP) Goals, new priorities?– Risk scoring strategy updates– New Attachment N requirements overlays (Phase 2, 3, 4, etc.) Technology Changes – Swaps / UpdatesHomelandSecurityOffice of Cybersecurity and Communications25
Questions?References:––––––CDM Agency Dashboard Practitioner’s GuideCDM Data Model v1.1CDM LDM v1.1FY 2016/2017 CIO FISMA MetricsCDM Architecture Principles DocumentConfiguration Management Guidance for the CDM Agency Dashboardplatform (DRAFT)HomelandSecurityOffice of Cybersecurity and Communications26
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELAudience Q&APlease use thequestion box on thetop right of yourscreen to askquestions.27
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELGet Involved with the CDMLearning Program!Visit our website:https://www.us-cert.gov/cdmEngage with our weekly its-bytesJoin our mailing list:cdmlearning@hq.dhs.gov28
THE FE BRUARY CDM WE BIN AR:ORGANIZ E IT TO SEE IT: YOUR DATA M ODELThank you for attending today’sCDM webinar! A certificate of attendance will be available to downloadat www.us-cert.gov/cdm/training within one week oftoday’s event. Please help us provide better learning content bycompleting the short questionnaire. Your feedbackmatters!29
23.02.2017 · Primarily supporting the CDM Dashboard . – Cybersecurity performance metrics to support Federal Information Security Management Act (FISMA) metric reporting, and – Ad-hoc federated queries to support security operations. 6. Homeland Security. Office of Cybersecurity and Communications. The CDM Data Model Defines a . common baseline . that can be implemented –