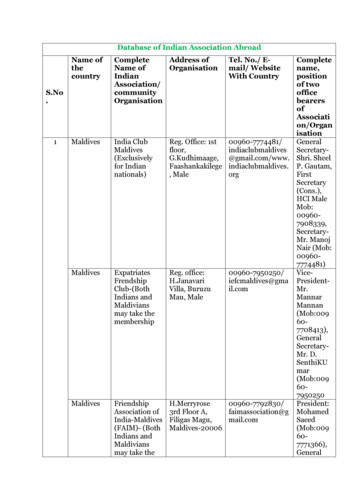
Transcription
White PaperThe Complete Guide to Log andEvent ManagementDr. Anton Chuvakin
The Complete Guide to Log and Event ManagementTable of Contents:2 Introduction3 Security Information and EventManagement Defining Features3 Log Management Defining Features4 High-level Comparison: SIEM vs. LogManagement5SIEM and Log Management Use Cases6 PCI DSS6 FISMA6 HIPAA6 Technology Trend7 Example SIEM and Log ManagementScenario7 Architecting Log Management and SIEM9 What to Do First? SIEM or LogManagement?10 Do All Companies Have to Graduatefrom Log Management to SIEM?11 After Log Management and SIEM:Maturity Curve13 Mistakes16Conclusions16About the AuthorSponsored Byp. 1
IntroductionSecurity information and event management(SIEM) technology has existed since the late1990s, but it has always been somewhatcontroversial in the security industry due toits initial promise of a “security single paneof glass” combined with slow adoptionacross smaller organizations. More recently,traditional SIEM has been joined by a broaduse log management technology that focuseson collecting a wide variety of logs for amultitude of purposes, from security incidentresponse to regulatory compliance, systemmanagement and application troubleshooting.In this paper we will analyze the relationshipbetween these two technologies—SIEM andlog management—focusing not only on thetechnical differences and different uses forthese technologies, but also on architectingtheir joint deployments. For example, if youneed to satisfy logging requirements ofPCI DSS, which one should you deploy?What technology is better suited to optimizeyour incident response and investigationprocedures? Which one will give you real-timeinsight about the attacks? In addition, we willprovide recommendations for companiesthat have deployed log management orSIEM in order for them to plot their roadmapto enhancing, optimizing and expandingtheir deployment. We will also recommenda roadmap for companies that have alreadydeployed both of these technologies.SIEM tools first appeared on the marketin 1997. Their original use was for reducingnetwork intrusion detection system (IDS) “falsepositives,” which plagued NIDS systems atthe time. The tools were complex to deployand use, so they were only used by thelargest organizations with the most maturesecurity programs. The market was sizedat a few million dollars in the late nineties,while now, some analysts report that themarket is on track to reach billions in thecoming years. Today’s SIEM tools, such asp. 2Novell Sentinel , are used by firms largeand small, from Fortune 1000 or Global2000 organizations to tiny SMBs—small andmedium businesses.Before beginning our analysis, it will be helpfulto define “SIEM” and “log management“andexplain the differences between them.SIEM covers relevant log collection,aggregation, normalization and retention;context data collection; analysis (correlation,prioritization); presentation (reporting,visualization); security-related workflow andrelevant security content. All the use cases forSIEM focus on information security, networksecurity, data security as well as regulatorycompliance.On the other hand, log managementincludes comprehensive log collection,aggregation, original (raw, unmodified) logretention; log text analysis; presentation(mostly in the form of search, but alsoreporting); related workflow and content.With log management, the use cases arebroad and cover all possible uses for log dataacross IT and even beyond.The key difference that follows from the abovedefinitions stems from the fact that SIEMfocuses on security—the first word in “securityinformation and event management”—anduse of various IT information for securitypurposes. On the other hand, logmanagement focuses on logs and wideranging uses for log data, both within andoutside the security domain.
The Complete Guide to Log and Event ManagementSecurity Information and EventManagement Defining FeaturesLet’s further discuss what features can becalled “defining” SIEM features; most userswill look for most of these features whilechoosing a SIEM product. The features are: Log and context data collection: Thisincludes being able to collect logs andcontext data (such as identity informationor vulnerability assessment results) using acombination of agentless and agent-basedmethods. Normalization and categorization: Thiscovers being able to convert collectedoriginal logs into a universal format for useinside the SIEM product. The events arealso categorized into useful bins such as“Configuration Change,” ”File Access” or“Buffer Overflow Attack.” Correlation: This is used to describe rulebased correlation, statistical or algorithmiccorrelation, as well as other methods thatinclude relating different events to eachother and events to context data. Correlationcould be in real time, but not all toolssupport real-time correlation and insteadfocus on correlating historical data from theirdatabases. Other log analysis methods aresometimes bundled under the correlationlabel as well. Notification/alerting: This includes beingable to trigger notifications or alerts tooperators or managers. Common alertingmechanisms include e-mail, SMS, or evenSNMP messages. Prioritization: This includes differentfeatures that help highlight the importantevents over less critical security events.This may be accomplished by correlatingsecurity events with vulnerability dataor other asset information. Prioritizationalgorithms would often use severityinformation provided by the original logsource as well. Real-time views: This covers securitymonitoring dashboards and displays, usedfor security operations personnel. Suchdisplays will show collected information aswell as correlation results to the analystsin near real time; they can also be fed byhistorical, archived data. Reporting: Reporting and scheduledreporting covers all the historical viewsof data collected by the SIEM product.Some products also have a mechanism fordistributing reports to security personnel orIT management, either over e-mail or usinga dedicated secure Web portal. Security role workflow: This coversincident management features such asbeing able to open cases and performinvestigative tasks, as well as automaticallyor semi-automatically perform typical tasksfor security operations. Some productsalso include collaborated features thatallow multiple analysts to work on the samesecurity response effort.The above functionality can be found in mostcommercial SIEM products on the markettoday. However, most products have strongand weak points, as well as additional “secretsauce” features.Log Management Defining FeaturesLet’s start by considering the defining featuresof a log management system. These include: Log data collection: This covers beingable to collect all logs using agent-based oragent-less methods, or a combination of thetwo. Efficient retention: While collecting andsaving log data does not sound like a bigengineering challenge, being able to collectgigabytes and even terabytes of log dataefficiently—and retaining it while providingfast searching and quick access to it—is nottrivial. Given that many regulations mandatespecific terms for log data retention(ranging all the way to multiple years),this functionality is critical to a logmanagement system.p. 3
can make or break the log managementsolution. Reporting should be fast,customizable and easy to use for a broadrange of purposes. The distinction betweensearches and reports is pretty clear: Searchgoes across all available, collected logs inraw, original form (like Google goes throughWeb pages), while report operates on logswhich are parsed into a database (like anExcel spreadsheet). Carefully evaluate howeasy it is to create a custom report in a logmanagement tool. This is where a lot ofsolutions fall short by requiring that theiroperators study the esoteric aspects of theirlog storage data structures before they cancustomize the reports. Searching is the primary way to accessinformation in all of the logs, includinglogs from custom applications. Search isindispensable for investigative use of logs,log forensics, and finding faults while usinglogs for application troubleshooting.A clean and responsive interactivesearch interface is thus essential for a logmanagement system. Log indexing or parsing is a key componentof a log management system. Indexing canspeed up searches literally by a factor ofa hundred. Indexing technology creates adata structure called an index that allowsvery fast keyword type searches andBoolean type searches across the logstorage. Sometimes indexing is used toenable other full text analysis techniques.Think about this as “Google for logs.” Notall log management tools support indexing,or advertise log collection rates that don’taccount for indexing, so be careful withvendor claims here. Reporting and scheduled reporting cover allthe data collected by the log managementproduct and are similar to SIEM reporting.The strength of reporting, whether forsecurity, compliance or operational reasons,Now let’s perform a high-level comparisonbetween functions and features of SIEM andlog management.High-level Comparison: SIEMvs. Log ManagementIn the table below, we show key areas offunctionality and explain how SIEM and logmanagement are different.Functionality AreaSecurity Information andEvent Management (SIEM)Log ManagementLog collectionCollect security relevant logsCollect all logs including operationallogs and custom application logsLog retentionRetain limited parsed andnormalized log dataRetain raw and parsed log data forlong periods of timeReportingSecurity focused reporting,real-time reportingBroad use reporting, historicalreportingAnalysisCorrelation, threat scoring,event prioritizationFull text analysis, taggingAlerting andnotificationAdvanced security focusedreportingSimple alerting on all logsOther featuresIncident management, othersecurity data analysisHigh scalability for collection andsearchingp. 4
The Complete Guide to Log and Event ManagementNow let us review how SIEM and logmanagement technologies are used.SIEM and Log ManagementUse CasesBefore discussing the joint architecture ofSIEM and log management, we need tobriefly present typical use cases that call fordeployment of a SIEM product by a customerorganization. We will start from the very highlevel of three main types of use cases:1. Security, both detective and investigative:Sometimes also called threat management,this focuses on detecting and respondingto attacks, malware infection, data theft andother security issues.2. Compliance, regulatory (global) and policy(local): This focuses on satisfying therequirement of various laws, mandatesand frameworks as well as local corporatepolicy.3. Operational, system and networktroubleshooting and normal operations:Specific mostly to log management, thisuse case has to do with investigatingsystem problems as well as monitoring theavailability of systems and applications.On a more detailed level, security andcompliance use cases fall under severalscenarios. Let’s review them in detail.The first usage scenario is a traditionalSecurity Operations Center (SOC). It typicallymakes heavy use of SIEM features suchas real-time views and correlation. A SIEMcustomer organization will have analystsonline 24x7 and have them “chase” securityalerts as they “pop up.” This was the originalSIEM use case when SIEM technology startedin the 1990s; today it is relegated to thelargest organizations only.The next use case is sometimes called the“mini-SOC” scenario. In this case, the securitypersonnel will use non real-time, delayedviews to check for security issues (“analystscome in the morning”). The analysts are onlineRecently, traditional SIEM has beenjoined by a broad-use log managementtechnology that focuses on collecting a widevariety of logs for a multitude of purposes,from security incident response to regulatorycompliance, system management andapplication troubleshooting.maybe a few hours each day and only reviewalerts and reports as needed and not innear-real time—unless the events happenedwhile they were logged in to the product.The third scenario is an “automated SOC”scenario where an organization configurestheir SIEM to alert based on rules and then“forgets” it until the alert. The analysts neverlog in unless there is a need to investigatealerts, review reports weekly/monthly orperform other rare tasks. This is the use casethat many smaller organizations want and fewSIEM products can deliver, at least not withoutextensive customization. It is worthwhile toadd that a lot of SIEM products are sold withan expectation of being an automated SOC,but such expectations are rarely realized.Log management technologies have a rolein other scenarios outside of security as well.Application troubleshooting and systemadministration are two additional importantuse cases for log management systems.When the application is deployed and itslogging configured, the log managementsystem is used to quickly review errors andexception logs. It will also review summariesof normal application activity in order todetermine application health and troubleshootpossible irregularities.Another scenario is “compliance statusreporting.” Here analysts or securitymanagers review reports with a focus oncompliance issues. The review occursweekly or monthly or as prescribed by aspecific regulation. There is not necessarilyp. 5
Today’s SIEM tools, such as Novell Sentinel,are used by firms large and small, fromFortune 1000 or Global 2000 organizations totiny SMBs—small and medium businesses.a security or operations focus. This usecase is commonly a transition phase andthe organization will likely later mature toone of the aforementioned use cases. Logmanagement tools are most often deployedfor this scenario, but it is not uncommon touse a SIEM product for compliance as well.In the latter case, long-term log retentionrequirements often challenge the deployment.Given that logs are very important for meetingcompliance mandates, let’s consider a fewregulations in detail.PCI DSSThe Payment Card Industry Data SecurityStandard (PCI DSS) applies to organizationsthat handle credit card transactions.It mandates logging specific details, logretention and daily log review procedures.Even though logging is present in all PCIrequirements, PCI DSS also containsRequirement 10, which is dedicated to loggingand log management. Under this requirement,logs for all system components must bereviewed at least daily. Further, PCI DSS statesthat the organization must ensure the integrityof its logs by implementing file integritymonitoring and change detection software onlogs. It also prescribes that logs from in-scopesystems are stored for at least one year.FISMAFederal Information Security ManagementAct of 2002 (FISMA) emphasizes the need foreach federal agency to develop, documentand implement an organization-wide programto secure the information systems thatsupport its operations and assets. NIST SP800-53, “Recommended Security Controlsfor Federal Information Systems,” describesp. 6log management controls including thegeneration, review, protection and retention ofaudit records, plus steps to take in the eventof audit failure.NIST 800-92, “Guide to Computer SecurityLog Management,” also created to simplifyFISMA compliance, is fully devoted to logmanagement. It describes the need for logmanagement in federal agencies and waysto establish and maintain successful andefficient log management infrastructures—including log generation, analysis, storageand monitoring. NIST 800-92 discusses theimportance of analyzing different kinds oflogs from different sources and of clearlydefining specific roles and responsibilities ofthose teams and individuals involved in logmanagement.HIPAAThe Health Insurance Portability andAccountability Act of 1996 (HIPAA) outlinesrelevant security standards for healthinformation. NIST SP 800-66, “An IntroductoryResource Guide for Implementing the HealthInsurance Portability and Accountability ActSecurity Rule”, details log managementrequirements for the securing of electronicprotected health information. Section 4.1 ofNIST 800-66 describes the need for regularreview of information system activity, suchas audit logs, access reports and securityincident-tracking reports. Also, Section 4.22specifies that documentation of actions andactivities need to be retained for at least sixyears. Logs are sometimes considered partof that. Recent HITECH Act of 2009 promisesto boost HIPAA implementations in thecoming years.Technology TrendsAs we mentioned before, SIEM technology ismore than 10 years old; it has gone throughmultiple phases which we could write anentirely new white paper about. We willhighlight a few of the SIEM technology trends.
The Complete Guide to Log and Event ManagementWhile SIEM started as a technology for largeglobal companies and sensitive governmentagencies, it continues a march down market.Many observers predict that 2010 or 2011will be the year of the major SIEM vendors’mid-market battle for dominance. As a result,smaller customers will get much improvedtools for security management.Another trend is acceptance of separate rolesfor SIEM and log management. Now, mostSIEM vendors offer log management solutionsas well. This also supports expanding usesfor SIEM tools including IT operations, fraudanalysis, application troubleshooting, goingall the way up to IT GRC uses for high-levelgovernance and risk measuring goals.We’re also witnessing the beginning ofconvergence between IT operations and ITmanagement and security management.While analysts have predicted this trend forseveral years, it has failed to fully materializeuntil now. Despite that fact, many predict thetrend of convergence of security managementand IT operations management will continue,and security tools will have more linkage intoIT operational tools such as network andsystem management.Example SIEM and LogManagement ScenarioThis case study covers a deployment scenarioof a SIEM and log management solutionto satisfy PCI-DSS requirements at a largeretail chain. The retailer decided to deploya commercial log management solutionwhen its PCI assessor suggested it wouldbe required to pass an assessment. A logmanagement vendor suggested that theretailer get both log management and SIEMsolution at the same time. So, it progressedfrom not doing anything with its logs directlyto running an advanced log managementsystem and real-time correlation capability.The project took a few months following aphased approached. The retailer’s IT staffdecided to implement it from the outsidein, based on an initial risk assessment.They started from their DMZ firewalls andthen progressed by feeding additionallogs into a log management system, whilesimultaneously defining correlation rules andrunning reports from the vendor’s PCI DSScompliance package. As they learned torespond to alerts, their processes maturedand they started making use of more of theSIEM functionality.Overall, the project represented a successfulimplementation of PCI logging requirements.The organization passed the PCI assessmentwith flying colors and was commended ontheir comprehensive approach to loggingand security monitoring. In addition, thesecurity team built a case that their PCI SIEMimplementation actually addresses additionalcompliance mandates since PCI DSS goesinto a deeper level of details while coveringessentially the same areas of IT governance.At the same time, log management tools alsobolstered their operational capabilities andoverall IT efficiency, while SIEM gave them thecorefor their future real-time detection andresponse capability.Architecting Log Managementand SIEMGiven the differences between technologies,many organizations have deployed both SIEMand log management, or are consideringenhancing an existing deployment of oneof the technologies with the other. What aresome of the common joint
p. 1 The Complete Guide to Log and Event Management Table of Contents: SponSorEd By 2 Introduction 3 Security Information and Event Management defining Features 3 Log Management defining Features 4 High-level Comparison: SIEM vs. Log Management 5 SIEM and Log Management Use Cases 6 pCI dSS 6 FISMA 6 HIpAA 6 Technology Trend 7 Example SIEM and Log Management Scenario 7 File Size: 2MB