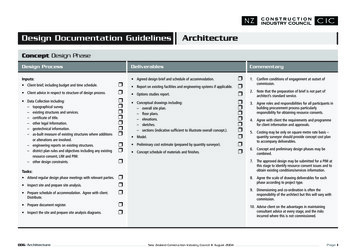
Transcription
PROTECT YOUR DATAAND PREPARE FOR THEEUROPEAN GENERAL DATAPROTECTION REGULATION
INSIGHTSThe EU’s new data protection regulation, known as the GDPR (General Data Protection Regulation), can impact yourorganisation significantly in terms of how to handle personal data. Your organisation will not only be responsible forensuring compliance with the regulation in terms of handling and protecting personal data, it could even be penalisedfor non-compliance and it will be liable for any damage resulting from data breaches.Trasys International provides expertise in GDPR and has developed a modular approach supported by a portfolio ofservices to guide you towards GDPR compliance at your own pace taking into account your organisation’s securitymaturity and your budgetary means.ABOUT GDPRThe General Data Protection Regulation wants to harmonise the data protection regulations throughout the EU andto strengthen and unify data protection. It addresses personal data security for EU citizens and individuals within theEU, but regulates also export of personal data outside the EU. The Commission’s primary objectives of the GDPRare to give citizens back the control of their personal data and to simplify the regulatory environment for internationalbusiness by unifying the regulation within the EU.The GDPR was adopted on the 27th of April 2016. It enters into application on the 25th of May 2018 after a two yeartransition period and will replace the current data protection directive 95/46/EC from 1995. Unlike a directive, it doesnot require any enabling legislation to be passed by governments.
WHY YOU SHOULD GET PREPARED FORTHE NEW REGULATION?The GDPR will supersede all current national data protection laws in the EU. Here is an overviewof the main expected changes that organisations will have to be aware of and adapt to:Expanded territorial reach:Role of subcontractors:The GDPR applies to organisations and theirOne of the key changes in the GDPR is that sub-subcontractors outside the EU. This means in practicecontractors have direct obligations. This includesthat a company outside the EU, that is targetingimplementing technical and organisational measuresconsumers in the EU, will be subject to the GDPR.and notifying your organisation without delay of databreaches.Accountability and Privacy by Design:Sanctions:The GDPR makes organisations fully accountable fordemonstrating compliance. This includes requiringThe GDPR establishes penalties for breach imposingthem to document compliance, conduct datafines for infringements of up to 4% of annual worldwideprotection impact assessments for risky dataturnover on data breach and up to 2% of annualprocessing and implement data protection by designworldwide turnover on non-compliance.and by default in their operational processes.Data Protection Officer (DPO):Consent:In specific circumstances organisations or subcontracA data subject’s consent to processing his or hertors must designate a Data Protection Officer. Thepersonal data must be given freely, and for sensitiveDPO will need sufficient expert knowledge. The DPOdata explicitly, either by a statement or a clear affirmativemay be employed or under a service contract.action stating agreement to the processing. Consentcan be withdrawn at any moment. The organisation isRight to be forgotten:required to be able to demonstrate that consent wasgiven.Individuals can require their personal data to be erasedwithout undue delay by the organisation. A goodData Breach Notification:example is where they withdraw consent and no otherlegal ground for processing applies.Organisations must notify data breaches to the DataPrivacy Authority. This must be done without delayand, where feasible, within 72 hours of awareness.A substantiated justification must be provided if thistimeframe is not met. The organisation must notify theaffected data subjects without delay when their datahas been compromised.
9 STEPS GUIDE ON HOW TO GET STARTEDWITH GDPR Key to success towards GDPR compliance Align your GDPR compliance and datais stakeholder buy-in. Start with creating anprotection track with a security frameworkurgency at director or board level. Key stakeholdersuch as CIS, ISO27001, NIST, and integratebuy-in at C-level is a critical success factor toit in your security strategy and roadmap.engage the necessary resources and to haveInternational organisations should also keepGDPR compliance on the right position within thetheir branches and subsidiaries in mind. Eachcorporate priorities.country has its preference in terms of frameworkanddifferentgovernmentsrequiredifferent One of the first steps in the actual dataframeworks. Compliance framework mappingsprotection is knowing where your data resides.do exist and can be helpful to develop a globalPerform a data identification, ideally a combinedcompliance approach.exercise of manual interviews and automated datacrawling. Once data is identified properly classifying, Base your data protection strategy andlabelling and tagging data is a prerequisite towardsroadmap on a risk assessment. Protectingdefining a clear scope for your GDPR complianceyour personal data at 100% is simply impossiblegap analysis and compliance program.and attempting to, will saddle you with anenormous cost and effort. Concentrating on the Collaboration between IT and legal is critical.The regulation does not provide exact definitionsmost pressing topics will give you quick benefitsand provide focus.that can be applied out of the box. Interpretation,risk assessment, legal backing and corporate level Perform a GDPR compliance gap analysis,optionally combined with a data protection ordecision will be necessary all the way.security maturity assessment. In combination Stakeholdermanagementisnecessarywith a risk assessment this gives you all necessarythroughout your entire enterprise. Creating ainformation to establish a multi-year data protectionminimum of awareness and understanding aboutand security roadmap with strong justifiedthe regulation will raise the required attentionfoundation.and collaboration from the different businessunits. Awareness is not a one-time shot. Make Dataclassification,installationofdataawareness an integrated part of your complianceprotection and governance is not a one-program and repeat sessions and campaigns attime shot. Ensure the implementation of policyregular intervals.through automated data protection enforcement,specifically for sensitive or personal data. Hence Appoint a responsible for GDPR compliance.the need of clear accountability at director levelWhether your organisation is subject to theand a governance structure piloted by a Dataobligation of appointing a DPO or not, it isProtection Officer or equivalent.advised to assign a responsible that overseesthe compliance track towards May 25, 2018and assures continued compliance once GDPRbecomes in effect.
STEP 9CREATESTAKEHOLDERBUY-IN STEP 2DO A DATAIDENTIFICATIONEXERCISE IMPLEMENTAUTOMATEDENFORCEMENTSTEP 1STEP 8STEP 3GDPRGET LEGAL& IT TOGETHER PERFORM AGAP ANALYSISSTEP 7STEP 4PRIORITISETHROUGH A RISKASSESSMENTRAISEAWARENESSSTEP 5ADOPT A SECURITYFRAMEWORKAPPOINT A DPO(OR EQUIVALENT) STEP 6
HOW TRASYS INTERNATIONAL CAN HELP YOU Advisory services: Trasys International can assist Risk assessment services : Trasys Internationalin roadmap design and strategic development foris experienced in risk assessment services whichdata protection through consulting or throughcan be performed either with a broad scopestaff provisioning at different levels. Our team oftowards enterprise IT security risk either with aexperienced consultants provides services fromlimited scope specifically towards data protection ortechnical data automation to C-level advisory toGDPR compliance. A risk prioritisation and impactensure continuity and single accountability.analysis provides your company with an excellenttool to decide on your future investments, strategy DPO resources: many organisations do notand roadmap.have the required resources or competences tostaff a Data Protection Officer. Trasys International GDPR compliance assessment: is a focused wayprovides individuals with the required competencesand a short track towards identification of complianceand certifications to assist organizations in theirgaps and can be a tool where budget is limited andGDPR compliance track in a DPO, CISO (Chiefresources are scarce. Trasys International executesInformation Security Officer) or other role, ina Quick GDPR compliance assessment toproject mode or in operational mode. The consultantidentify the areas where an organisation is notcan ensure all DPO responsibilities and can assistcompliant. A high-level prioritisation can be definedthe organisation on a broader security context in ain order to develop a compliance roadmap.dedicated, shared, full or part time mode. If required,Trasys International can accompany the DPO with Automated data classification and protection:legal assistance through a recognised law firm toa critical step towards GDPR compliance isensure legal advice.the identification and classification of data.Trasys Awareness campaigns: they are key to hipclassificationandthroughatowards GDPR compliance. Trasys International doescombination of manual and automated methodsnot only provide awareness sessions concerningto ensure a full coverage. Data Classification is athe GDPR requirements, but extends awarenesshighly interactive exercise in collaboration with theprograms with practical sessions looking into theclient stakeholders, which are significantly involvedimpact on business processes and daily operations.in the decision making process. Trasys InternationalIn addition, awareness programs are focused towardspartners with different organisations such asacceptance of change with the objective to not onlyVaronis, Microsoft and others to automate dataraise awareness about data privacy but also towardsclassification and data protection. Throughthe necessity of the GDPR compliance asys International ensures reduced project- and Program and project management: will be keyimplementation costs. By enforcing and delegatingthroughout your entire data protection lifecycle.policies, operational data management costs canWhether you need a program manager to drivealso be significantly reduced.the compliance track on a high-level or you need atechnical project lead to implement an automatedsolution, Trasys International provides resources withbroad security competences, organisational andcommunication skills who are used to drive strategicchange programs. Staff provisionning: Trasys International canprovision security staff at different levels.
OUR SERVICES FOR PROGRAM &PROJECTMANAGEMENTRISK D DATACLASSIFICATION ANDPROTECTIONSTAFFPROVISIONINGOUR UNIQUE SELLING ETHODOLOGIESFOR IMPLEMENTATIONPRODUCT& VENDORINDEPENDANT
OUR KEY DIFFERENTIATORS Trasys International can rely on a rich pool ofapproach is well-structured and methodological,resources, covering a very broad range of securitybut flexible and adapted to your organisationalservices from very technical competences toneeds, to your organisation’s capacity to changeC-level advisors. Having a competent team ofand to the objectives set by your management.experts at its disposition is a major advantageprovide. Our relations with vendors and partners extendTrasys International prefers to service you withbeyond national boundaries and provide anthe most ‘fit for purpose’ experts within a diverseunmatched pool of expertise, product supportproject team to maximise the right expertise at theand competences. Trasys International is de factoright level at the right time.a services company and is product and vendorthatnotmanyorganisationscanindependent. With our service-approach backed Our client base extends throughout all sectors onup by our partnerships we are able to providea national scale. We have worked with a broadyou with an independent advice on automationspectrum of organisational cultures and maturitysolutions and we offer a vast range of productlevels. This experience gives us an empathicimplementation services with our own people ortouch which is crucial to succeed in implementingthrough our partners.strategic change within an organisation. OurTRASYS INTERNATIONAL SECURITY PRACTICECyberSecurity is more than a few new productsobjective: connecting security to business agility. Ouror gadgets. It’s about a complete, integrated mindexperts base their approach on the NIST (Nationalset, involving both proactive and reactive measures,Institutepeople, processes and technology. CyberSecurity isOrganizationalso about understanding the business and aligningframeworks for best practices. The main advantageany project to the critical assets of the organisation. Itof the NIST and ISO approaches consists in usingis about monitoring, testing, building and maintainingbusiness drivers to guide CyberSecurity activitiesa process and about creating a platform that lets youand in considering CyberSecurity risks as part oftruly manage your risks in a world where the cost andthe organisation’s risk management processes.damages of breaches continue to rise.Our extensive portfolio of solutions and rnationalCybersecuritycan strengthen the prevention and management ofThe Trasys International team of Information andCyberSecurity professionals plays the key role oftrusted advisor to help the customer achieve hisCyberSecurity for critical data.
G - Security GovernanceR - Security Risk ManagementC - Security ComplianceISO 27001 Audit & ImplementationIT Security Strategy & Roadmap, CIO/CISOAdvisoryGRC & TRAININGIndustrial Control Systems (SCADA)SecurityData Security GovernanceData ClassificationData Privacy & ProtectionGeneral Data Protection Regulation(EU-GDPR)INFORMATION &DATA SECURITYData Leakage Protection Data LeakageDetectionIdentity Access GovernanceIdentity Access ManagementWeb Access ManagementSingle Sign-OnIDENTITY & ACCESSMANAGEMENTPrivileged Account SecurityInfrastructure Security ArchitectureFirewall ManagementPenetration TestingVulnerability ScanningEthical HackingEndpoint SecurityINFRASTRUCTURE &APPLICATION SECURITYApplication Security TestingSecurity Incident & Event ManagementSecurity Operations CenterSIEM & SECURITYINTELLIGENCESecurity Threat Intelligence
Charles DelhayeConsulting Division Executivee. charles.delhaye@trasysinternational.comm. 32 (0)499 05 85 84Kris VansteenwegenHead of Securitye. kris.vansteenwegen@nrb.bem. 32 (0)470 20 71 trasysinternational 32(0)2 893 12 11info@trasysinternational.comTrasys International OfficesHeadquartersOperational officesRue d’Arlon / Aarlenstraat 53Chaussée de La Hulpe / Terhulpsesteenweg 6C1040 Bruxelles/Brussel - Belgium1560 Hoeilaart - BelgiumDesigned at NRB 10/01/2017
and a governance structure piloted by a Data Protection Officer or equivalent. STEP 6 ADOPT A SECURITY FRAMEWORK STEP 7 PRIORITISE THROUGH A RISK ASSESSMENT STEP 8 PERFORM A GAP ANALYSIS STEP 9 IMPLEMENT AUTOMATED ENFORCEMENT STEP 2 DO A DATA IDENTIFICATION EXERCISE STEP 3 GET LEGAL & IT TOGETHER STEP 4 RAISE AWARENESS STEP 5 APPOINT A DPO (OR EQUIVALENT) STEP 1 CREATE STAKEHOLDER BUY-IN GDPR .