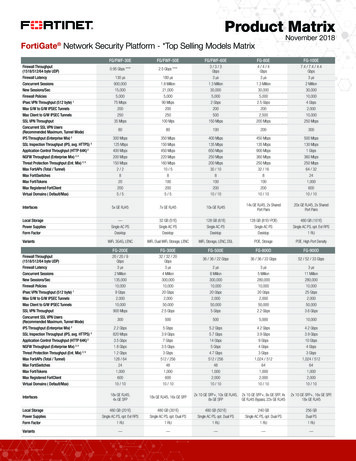
Transcription
Welcome to theFortinet’s Cyber Threat AssessmentProgram PlaybookGET STARTED
START DRIVING DEMANDOVERVIEWMARKET“CTAPs are selling our product.They have become a very powerfultool because we can quantifywhat we are talking about thecustomers can now see it.”SOLUTIONENABLEPROMOTESELLFortinet’s Cyber Threat Assessment ProgramFortinet Cyber Threat Assessment Program (CTAP) is a framework designed to assist youwith offering your prospects a quick, easy and free insight into their security posture. It helpsyou build credibility, establish yourself as a trusted advisor and create a strong businesscase to choose Fortinet solutions to mitigate threats. CTAP takes advantage of FortiGuardservices, independent 3rd party testing (Virus Bulletin, AV Comparatives, and NSS Labs) andvalidation of superior security intelligence and protection effectiveness.How CTAP Helps You“The CTAP report drove thisopportunity from a 20Kopportunity to a 200K opportunity. The report allowedmanagement to see that securitywas an area of need and theseprojects are now being moved tothe top of the list.” Demonstrate security expertise and establish yourself as a trusted advisorAccelerate prospect’s decision to buy when threats are uncoveredGain a foothold into accounts (bridges the “demonstrate value” to “purchase” gap)Quickly prove FortiOS/FortiGuard value specific to customer environmentEstablish Fortinet Security Fabric as something tangible, not just a vision Overcome common objections related to PoC difficulties (time, cost, manpower, etc.) Standardize your sales processes and manage the end-to-end sales cycleHow CTAP Helps Fortinet“At the start there was little interestin using the FortiGate for security.Within minutes we were seeingbotnets, viruses, P2P, etc. Thereport was sent up the chain andquickly became a hot topic.” By establishing a consistent run rate of opportunities through sales channel partnersUtilization of analytics gives Fortinet more marketing ammunition and thought leadershipExpect a close rate approaching 90% for CTAP enabled dealsMore management oversight and visibility into sales cycles all aroundPartners are more engaged and enjoy a more controlled sales methodologyStandardize our pre-sales tools and sales enablement processesEffectively, CTAP has become the de facto call to action at FortinetCyber Threat Assessment Program Playbook - Internal Use Only1
START DRIVING mer BenefitsYour customer’s network is a complex set of interactions between applications,users and content. It is at risk from sophisticated threats such as APTs, botnets andadvanced malware. To manage the complexities and block the threats requires greatervisibility and performance than traditional network firewalls can provide.RegisterAssessment inPortalWipeFortiGateThe Cyber Threat Assessment Program offers a FortiGate network security platformdeployed as internal segmentation firewall (ISFW) or next generation firewall (NGFW)to provide your customer with an unprecedented insight into security and threatprevention, user productivity and network utilization without compromising performanceor adding latency.CTAPLifecycleDiscussFindings &Close DealMost importantly, the Cyber Threat Assessment Report will translate this informationinto recommended actions your customer can take to mitigate security and threatconcerns, improve user productivity and optimize network utilization with FortiGate’sgranular control over applications, users and content.Organizations Who Run an Assessment Will Discover Their network is bombarded with more than 6,900 IPS attacks daily – those areall threats that are currently circumventing their existing gateway firewall! 3 pieces of freshly installed malware and/or botnets attempting to dial hometo various command and control servers around the world. About 192 applications are utilized per day on average – many of them areunknown to the prospect’s IT managers and include gaming, peer to peer, andremote access applications. More than 19 audio/video streaming applications which consume about 35%of their organizational bandwidth on any given day. 2 or more malicious “drive-by download” websites accessed per week; each ofthem attempting to install malware on their network hosts.Cyber Threat Assessment Program Playbook - Internal Use OnlyInstallFortiGateCollect Logs(2-3 ionTop-Level BenefitSecurity andThreat Prevention(includingAdvancedThreats)FortiGate NGFW FortiSandbox FortiAnalyzerDetects previouslyunknownattacks, highrisk applications,botnets, C&Cactivity, exploits,malware, etc.User ProductivityFortiGate NGFW FortiAnalyzerProvides insight intowhich applicationsare consumingnetwork bandwidth.NetworkUtilizationFortiGate NGFWClarifies when thenetwork is moreheavily utilized.2
START DRIVING PROMOTESELLCOMPETITORSWhat is the output of a CTAP? Duration to run a CTAP typically takes 3-7 business days Assessment report available within 2 days after receiving log files Report output is in PDF format Report can be branded with Partner LogoCyber Threat Assessment Program Playbook - Internal Use Only3
START DRIVING PROMOTESELLCOMPETITORSFortinet supports FortiGate 100D, FortiGate 300D, or FortiGate 1500D modelswith CTAP. While we are evaluating other hardware models, there is an inherentcomplexity in supporting multiple models on new builds.In general, it’s better to OVERSIZE a network environment in order to capturelogs properly. On the upper end, most large environments (which require morehorsepower than a 1500D) have specialized qualification requirements whichare more conducive to a custom evaluation.Cyber Threat Assessment Program Playbook - Internal Use Only4
START DRIVING PROMOTESELLCOMPETITORSHere are some of the key differentiators when it comes to ourassessments versus other security vendors:Sample CTAP Report Performance section - We have an entire report section dedicated tonetwork utilization/performance. Obviously, that’s great for us since1. performance plays to our strengths and 2. it will force prospectsgetting assessments from competitors to ask about missing sections. At risk hosts chart – We can utilize client reputation to determine thetrustworthiness of individual hosts. Competitive programs do notprovide similar insight. FortiGuard – We inherit all of the content security advantages ofFortiGuard. This includes our 3,300 application sensors (less than2,000 for most competitors), 8,100 IPS signatures, etc. Deployment flexibility - We allow streaming logs directly to a remotelogging server OR uploading them to the portal. In addition, wesupport two deployment modes: sniffer and inline. Use of FortiAnalyzer - We use a FortiAnalyzer on the backend (eatour own dog food, so to speak). Most competitors use a separatetool entirely (and this is a great way to upsell a FortiAnalyzer unit!). Sandboxing included – There is no need to run firewall and sandboxreports separately. CTAPs can include sandboxing by choosing acheckbox, which demonstrates our Security Fabric in action.Cyber Threat Assessment Program Playbook - Internal Use Only5
START DRIVING DEMANDOVERVIEWMARKETSOLUTIONQUALIFYENABLEOBJECTION HANDLINGPROMOTESELLROLESCTAP is meant to be a quick deployment and status check of a prospect’s network. Typically, these are greenfield (net new) opportunities, but existingcustomers (especially in upgrade/replacements scenarios) are also eligible. Generally speaking, CTAP is not meant for custom FortiGate configurations,integrations with other products (either Fortinet or third party), or RFP bake-offs. Extreme low-end (partner investment vs. return) and high-end opportunities(customization and high performance FortiGates) are generally not conducive to CTAP.ConcernRisk of BreachUserProductivityUpgradeFirewall RefreshConsolidation and SecurityServices RenewalsPerformanceQuestionAre youconcernedabout gettingbreached?Do you havethe visibilityyou need intoyour usersproductivity?Are you lookingto upgrade froma traditionalfirewall to anext generationfirewall?Are you lookingat refreshingyour firewallssoon, or addingadditional firewallsto your growingorganization?Do you have to managemultiple point securityproducts? Do you have a webfiltering or IPS service renewalcoming up?Is your current firewall deliveringthe performance you need tokeep up with the speed of yournetwork?AnswerGet a sneak peak into how FortiGate will provide better security and more controlwithout disrupting your existing infrastructure. It’s easy, no legal documents tosign or purchase orders to cut. Risk of data breach in today’s threat landscapeis high, get visibility into your risk with a free assessment. (Gartner predicts that90% of new enterprise firewall purchases will be NGFW by the end of 2018)See how you can simplify yourmanagement load by replacingyour point security productswith a FortiGate NGFW or do agraduated rollout by replacingpoint products with a bettervalue FortiGate and turn onadditional capabilities as youneed them over time.The FortiGate platformdelivers 5x faster throughputperformance compared toother similar NGFW solutions inthe market today. Our highspeed performance is basedon the Fortinet Optimum PathProcessing architecture and ourcustom FortiASICs.Engaging and Qualifying Prospects: Does your team regularly brief exec staff on your security status?Are you looking to upgrade to a NGFW?Have you ever been breached or do you have a breach response plan in the event your network is compromised?Do you know which applications are being used on your network?Do you think your firewall can keep up with bandwidth demands?When is your next firewall maintenance renewal?What are your corporate policies on P2P, proxy or gaming usage?Cyber Threat Assessment Program Playbook - Internal Use Only6
START DRIVING DEMANDOVERVIEWMARKETSOLUTIONQUALIFY“I already have a Next-Gen firewall.”ENABLEPROMOTEOBJECTION HANDLINGSELLROLESPROSPECT CONCERNS OR NEEDSBENEFITS OF CTAPPerfect! Let’s find out how effective it iswithout disrupting your network.Unsure of current firewall’s threateffectivenessGenerated CTAP Report uses FortiGuard todemonstrate superior detection capabilities& also shows what is bypassing their existingfirewall“I don’t have any security budget.”Unable to properly evaluate firewall forrefresh due to limited resourcesNo time and limited personnel neededCannot afford disruption during assessmentFortiGate can be deployed as either a sniffer(no disruption) or inline (minimal disruption)No budget available for external assessmentThere is no charge to run a CTAP assessmentIncrease in unmanaged/untrackable activity(cloud or SSL)Generated CTAP Report will determine whichcloud/SaaS applications are being used andactual HTTP/HTTPS ratioTargeted attacks and potential zero daythreatsCTAPs can also demonstrate the value ofsandboxing without requiring a CPE basedFortiSandboxComparison to similar companiesCTAP Reports can show how the prospect’snetwork security stacks up relative to otherorganizations in the same industryThere is no cost for running a CTAP; thatsaid, maybe this would help expand yoursecurity budget for next year if we uncoverany potentially malicious activity.“I don’t have time I’m too busy.”CTAP will literally only take 30 minutesto setup. And if we uncover a breach orattack vector, you’d probably rather knowabout it than not.Cyber Threat Assessment Program Playbook - Internal Use Only7
START DRIVING DEMANDOVERVIEWMARKETSOLUTIONQUALIFYENABLEOBJECTION . Login to: ctap.fortinet.com (using your network credentials)2. Read through the tutorial dialog that first pops up3. Then read through supporting materials & FAQSuggested Materials List - Specific sales roles should understand these materialsMAM/RAMCAM/PartnersSales EngineeringBDR/ISRVertical SalesNSE TrainingNSE TrainingNSE TrainingNSE TrainingNSE TrainingSample CTAP ReportPartner ToolkitSample CTAP ReportSample CTAP ReportSample CTAP ReportPortal Training VideoSample CTAP ReportTalking Points for SEsPrezoTalking Points for InsideSales PrezoPortal Training VideoThreat Landscape ReportPartner Overview VideoPortal Training VideoThreat Landscape ReportThreat Landscape ReportProspecting FlyerPortal Training VideoConfiguration ChecklistProspecting FlyerRelevant blog entriesTest Your MetalPartner 250 RewardFirst-time Portal TutorialTest Your MetalProspecting FlyerProspecting VideosRelease NotesFAQProspecting VideosProspecting VideosSupplementary SlidesSupplementary SlidesSupplementary SlidesSupplementary SlidesSupplementary SlidesCyber Threat Assessment Program Playbook - Internal Use Only8
START DRIVING te the SolutionAwarenessEngagementConsiderationCTAP FortiGate Configuration ChecklistCTAP Customer FlyerCTAP Partner ToolkitCTAP Full Page Print AdCTAP Sales PresentationCTAP Campaigning: Talking Points forInside SalesCTAP Report: Talking Points for SEsCTAP Customer Pitch Video #1 (KineticTypography)CTAP Customer Pitch Video #2 ("Meet Ed"Series)CTAP Partner 250 RewardCTAP Partner Overview VideoCTAP 3.1 Release NotesCTAP Portal Training VideoCTAP Customer Supplementary SlidesCTAP Threat Landscape Infographic(1H 2016)Cyber Threat Assessment Program Playbook - Internal Use OnlyCTAP Threat Landscape ExecutiveSummary (1H 2016)CTAP Threat Landscape Full Report (1H2016)9
START DRIVING DEMANDOVERVIEWMARKETSOLUTIONENABLEPROMOTESELLREADY TO FOLLOW UP?Cash RewardProspect MaterialsEarn 250 for every completed customer Cyber Threat Assessment.Applies to Fortinet Sales and Partners.Sample CTAP Report w/ Sandboxing (Informata College) - EnglishWho to ContactReview the CTAP portal Tutorials, FAQs, and Downloads. Any questions?Contact ctap@fortinet.comSample CTAP Report w/ Sandboxing (Informata College) - FrenchThe Websitehttps://ctap.fortinet.comHow to1. Login to: ctap.fortinet.com (using your network credentials)To initiate a CTAP with a customer, you need to acquire a FortiGate.2. Read through the tutorial dialog that first pops upFortiGate acquisition 3. Then read through supporting materials & FAQ Internal unitsRelevant Blogs1. Initiate an ITF through t-assessment-threatlandscape-report2. Review instructions on setting up a FortiGate in a lab (be sure to CTAPtest prior to deploying at an actual omise Partner units1. Certain partners qualify for complimentary units2. Others must order discounted NFR units3. Some distributors maintain pools of FortiGates for CTAPs4. Work with your Channel Account ManagerCyber Threat Assessment Program Playbook - Internal Use et-threat-landscapereport10
Fortinet Cyber Threat Assessment Program (CTAP) is a framework designed to assist you with offering your prospects a quick, easy and free insight into their security posture. It helps you build credibility, establish yourself as a trusted advisor and create a s