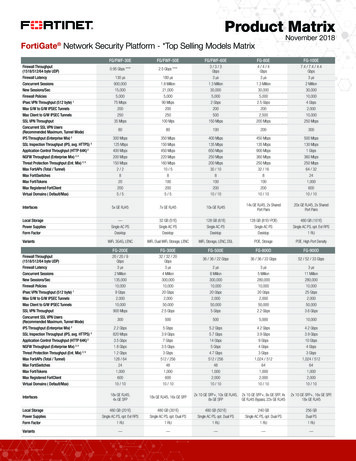
Transcription
DEPLOYMENT GUIDEFortinet FortiSIEM andCyberArk Integration
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationFortinet FortiSIEM and CyberArk IntegrationOverview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Deployment Prerequisites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Architecture Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3FortiSIEM Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
OverviewFortinet (NASDAQ: FTNT) secures the largest enterprise, service provider, and governmentorganizations around the world. Fortinet empowers its customers with intelligent, seamlessprotection across the expanding attack surface and the power to take on ever-increasingperformance requirements of the borderless network - today and into the future. Only theFortinet Security Fabric architecture can deliver security features without compromise toaddress the most critical security challenges, whether in networked, application, cloud ormobile environments. Fortinet ranks #1 in the most security appliances shipped worldwideand more than 400,000 customers trust Fortinet to protect their businesses. Learn more athttps://www.fortinet.com, the Fortinet Blog, or FortiGuard Labs.Deployment Prerequisites1. Fortinet FortiSIEM version 4.6.1 ornewer (tested with version 5.0.1)2. CyberArk Application IdentityManager version 9.9.5Credential ProviderThe Application Identity Manager (AIM), part of CyberArk’s Privileged Account Securitysolution, eliminates the need to store App2App passwords in applications, scripts orconfiguration files, and allows these highly-sensitive passwords to be centrally stored, loggedand managed with CyberArk’s patented Vaulting Technology . Using AIM, organizationscan comply with internal and regulatory requirements for regularly replacing passwords andsecurely monitoring privileged access across all systems, databases and applications. AIMfully addresses the need to assure the highest availability for applications running the enterprisebusiness, independent of network availability and with the highest performance.To address the needs of large enterprises, AIM supports a variety of systems, applications, Application Servers, scripts, jobs and more. It providessimple and intuitive tools for eliminating hard coded passwords, as well as a structured framework for addressing the challenges of App2Appprojects based on CyberArk’s vast experience with large enterprise deployments.3
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationFortiSIEM Configuration Install CyberArk Credential PowerInstall the redhat-lsb package on FortiSIEM before installing the Credential Provider.Note: you may also be required to install Dependencies prior to redhat-lsb.Download the Credential Provider Software from CyberArk. The installation files will look like this:Create a new directory for the installation files.Copy the following installation files to this directory:CARKaim-9.50- build number .i386.rpm – The Linux installation packagesCreateCredFile – The CyberArk utility that creates credentials filesVault.ini – The Vault parameter fileaimparms.sample – A sample of the parameter file used for installationEULA – The Credential Provider end user license agreement.icudt42b.dat – A file required to run the CreateCredFile utilityOpen Vault.ini and enter the correct Address and Port, similar to the example below. Save the file when done.4
Deployment guide Fortinet ForitSIEM and CyberArk IntegrationEdit the aimparms.sample file as follows.AcceptCyberArkEULA should be set to yesUncomment (remove the # symbol) from the beginning of the CreateVaultEnvironment lineLicensedProducts should be set to AIMCredFilePath should be set to the full path of the admin.cf file (created in the next step)VaultFilePath should be set to the full path of the Vault.ini fileSave the aimparms.sample file. It should look something like this:Copy the aimparms.sample file to /var/tmp/aimparms:5
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationEnter the following to specify the administrative user that will create the Vault environment during installation:./CreateCredFile admin.cf PasswordEnter the Username and Password when prompted.Install the Credential Provider for RHELinux x64FortiSIEM Configuration – Device Discovery ExampleFrom the FortiSIEM GUI go to Admin Setup Credentials and click New6
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationGive it a Name. Select the Device Type from the drop-down menu, in this example a Windows Server. Set the Access Protocol to WMI.For the Password config change from the default of Manual to CyberArk.You must configure the App ID, Safe, Folder and Object specific to your CyberArk account. Note that the Object is referred to as aName in CyberArk.Click Save.Test Credential Retrieval in Step 2 – First click New.7
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationEnter the Name, IP Address or IP Range of a device you want to test. In this example it’s a single IP address, 10.101.32.68.For Credentials select the Name defined in the previous step.Click Save.Note: The username, password and type of device should already be configured in CyberArk.Highlight the new entry and click Test Test Connectivity.Click Close.Congratulations, you’re done!8
Deployment guide Fortinet FortiSIEM and CyberArk IntegrationConclusionYou are now ready to use the CyberArk Application Identity Manager with FortiSIEM. Use CyberArk to securely provide admin credentialswhen FortiSIEM is discovering network devices.FortiSIEM User Guide: isiem-5-0-1-user-guide-html.pdfFortiSIEM External Systems Configurations 0/fortisiem-external-systems configurationguide.pdfFortiSIEM User Guide: isiem-5-0-1-user-guide-html.pdfCyberArk Credential Provider and ASCP Implementation s.ashx?pageid downloadfile&Safe CyberArk Documentation&Folder Root%5cPAS and SIM%5cRelease-Specific%5cV9.9%5cPAS&Name Credential Provider and ASCP Implementation Guide.pdfwww.fortinet.comCopyright 2019 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common lawtrademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and otherresults may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied,except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, insuch event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internallab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the mostcurrent version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise thispublication without notice, and the most current version of the publication shall be applicable.July 10, 2019 1:04 AM440593-0-0-END:\Fortinet\Deployment Guide\CyberArk\DG - Fortinet and CyberArk V1
Download the Credential Provider Software from CyberArk. The installation files will look like this: Create a new directory for the installation files. Copy the following installation files to this directory: CARKaim-9.50- build number .i386.rpm – The Linux installation packages CreateCredFile – The CyberArk utility that creates credentials .