Transcription
International Journal of Pure and Applied MathematicsVolume 119 No. 12 2018, 13221-13231ISSN: 1314-3395 (on-line version)url: http://www.ijpam.euSpecial Issueijpam.euSECURE DEDUP WITH ENCRYPTED DATAN SENTHIL SELVAN, G ANJALI, B KESINI, V SUBRAMANIYASWAMY*School of computing, SASTRA Deemed To Be University, Thanjavur- 613401.*Corresponding AuthorABSTRACTCloud computing is one of the way of service provision over the internet today. Cloud computingis the developing a next level from the last decades. One of the drawbacks, cloud storage is aprivacy security at the CSP. So, the chunks users stored by the encrypted data for the purpose ofsecurity. Cloud storage vendors which allow to decreases chunked data and more efficientstorage saver. One of the best techniques is deduplication, duplicate data is stored only once .Inthis paper, propose a checksum algorithm for distributing objects to agents, in a way thatimproves our chances of identifying a leaker. We evaluate its performance based on effectiveand efficient storage level. Its support data access control and revocation at the same time.Keywords: privacy security, encrypted data, deduplication, checksum algorithm.independent devices, without the purpose of1. INTRODUCTIONCloud computing is the development of theresources can be efficient and allocated.existing technology. Users can take a lot ofVirtualization provides which requires thebenefits from all of these technologies, notagility to go faster IT operations andhaving the use of knowledge about withminimizethem. The cloud aims to reduce the costsinfrastructure utilization. The automaticand user-friendly in the main concentrationcomputing which automatically provisionto the business point in IT services.resources on request services. Main benefitsVirtualization is the most enabling techniqueof the virtualization by reducing userin cloud computing. Virtualization whichparticipation, process to go faster theseparates a physical computing device intoprocess, make less labor costs and lower thenumerous virtual devices, they can behuman errors as possible. Users practice asmanaged to perform computing tasks. Inmostoperating system-Level virtualization needsproblems.to creating a measurable system of business
International Journal of Pure and Applied MathematicsSpecial IssueDeduplication is basically a compressionmeans which check it through the systemtechnique for removing data.integrity, suppose if it will be failed, thereFile leveldeduplication takes into account the entirewill be no copied information file.file, thus even small update or append makes2. RELATED WORKthe file different from the existing version ofofIn the digital world, cloud storage is verydeduplication. In the case of each level datapopular today. Cloud storage providers areverificationarethe services providers to the user for the On-represented as deduplication. Deduplicationdemand services. Cloud storage having thecan be categorized into two types namely,providing as Drop Box [2], Google Driveclient-side deduplication and as source-side[3], Mozy [4], which helps to storage spacededuplication. Performing deduplication atreduce in the cloud storage by storing theclient side ensuring bandwidth saving sinceeach file only once of each uploaded file [7].only hash value of file is sent to server, ifFor example, Deduplication [11] efficientduplicatevariousmethod to avoid the duplicate file in themetadatastorage point of view, but it cannot bemanagement primary storage, etc., storagehandle encrypted data [9][10]. In Encryptedoptimization.data there are the numerous method sratiochunksexistsandalsolikebackup,Cloud service is one of the informationstorage service, the most important andpopular service today. Cloud users uploadindividual data to the center of a (CSP) [7]and allow it to maintaining the information.Cloud storage schemes in the outsourcingencrypted the data, one of the encryptedmethodisMessage-Lockedencryption(MLE) [7] and others [12]. CE wasintroduced by Douceur et al. [7].CE issubject to hybrid security drawbacks andalso others [14],[15].data is kept never changed in the servers. InIn the Existing system, they actually storagethe storage, users can store their informationspace, security and also the brute forceand no longer time to kept in the locallyattack related information are proposed the[13]. Thus, the available of the multiple dataDupLESS based on the Bellare et al.files storing in the guaranteed distributed[1],[14],[15].We are not know about thecloud services. In existing system, brute-extant plan to try the satisfied the available,force attack [7] used to avoid numerousby the way of decreasing the duplicated datasame data in the CSP. For the verificationrevaluation[16]. Encryption of data ismultiplying data having same information13222
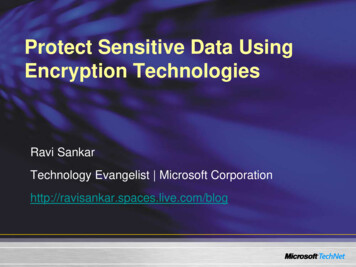
International Journal of Pure and Applied MathematicsSpecial Issueinsufficient to achieve the security andIn this paper to demonstrate that theprivacy policy.proposed scheme out of performing theFortheexampleoftheduplicationinformation in the identifying the plaintextsidentification, if we checked the identical inthe storage data which not privacy securityimplications [7][1].In existing g the limitation of the existingsystem in the terms of the computation,security, storage and privacy policy. Andalso we used rich efficient logarithmic timeto search the duplicate data in the cloudstorage, by reducing the time complexity aswell. We improved the security of the storeddisclosure to the multiple data storage.data, easy to handle the account of user andThis paper main objective to resolve thedata owner and also the data available.leaked out privacy information from theCSP to unauthorized people or outsourcing3. PROPOSED SYSTEMwebsite. And also to minimize the storageThis paper propose History Alert Rewritingspace in the cloud in practical by avoiding(HAR) algorithm to avoid de-duplicatethe deduplication data [13]. It also clearlyencrypted data stored in the CSP. It non-reduce the more limitation from the existingsegregated information such stored in thesystem based on the privacy security andavailability of the data owner [10].In the organization, or concerns to achievethe trending fore scalable things [1][7]. Thisis actually not a new thing to the todaydigitization society. Because today weimprove and achieving new technology withsuccessful outcomes. Whatever the societyreached the peak of point, but we are notensuring privacy policy, security, minimumstoragespacerequirementareFig.1. Proposed Techniquemorechallenging to us. So, we try to solve theeffective way to reducing the storage spaceand increasing the bandwidth in the CSP.We analyzed the security of individualcloud with allow to access. Intention of thispaper with a scheme hinge on confrontationwith data-owner and Traditional Encryptionto control the store with encrypted data bydeduplication. Focus to finding an effectiveinformation.way to reducing the issues in the time of13223
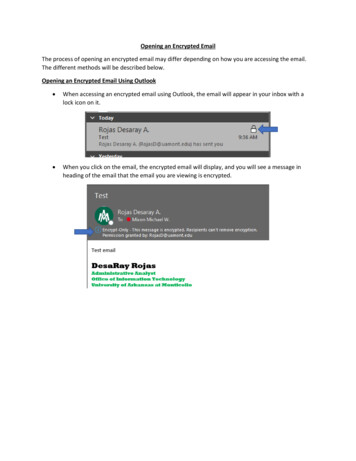
International Journal of Pure and Applied MathematicsSpecial Issuedata owner not able to be present. In this3.1. USER REGISTRATION AND CLOUDmethod using double encryption key forACCESS:encrypted data storing in the CSP. First theinformation owner provide the secret key todata user then authorized party (AP) sendthe secret key to data owner. Both AP keyand private key generate the encrypted keythatkeyusingforencryption.AESalgorithm using the encrypt content stored incloud. Figure 1 shows the proposed method.Step 1: Input: pkj, Policy (ui), Policy(AP)Step 2: CSP requesting AP todataowner and grant access to duplicateddata for uj by providing pkj.Step 3: After ensuring dataownership through challenge, AP checksPolicy (AP) and issues CSP rkAP ui RG(pkAP; skAP; pkj) if the check is positive.Fig.2. User registration and cloud accessAccess users only to have authenticationprocess before registration, AuthenticationStep 4: CSP transfering the dataE(pkAP; DEKi) into E(pkj; DEKi) if Policy(ui) authorizes uj to share similarinformation M encrypted by DEKi:R(rkAP ui; E(pkAP; DEK)) E(pkj; DEKi)process is priority based to movableStep 5: Data holder uj obtains DEKiby decrypting E (pkj; DEKi) with skj: DEKiresources and preventing from unauthorised D(skj;E(pkj; DEKi)), and then it canaccess data M at CSP.managementprocessincludesregistrations and deliverylocatingservices and itauthorized by the clients with ensuringsources.Beforeregistrationofcloudservices to ensure whether the client is anauthenticated or not to access cloud server.Can ensure the information stored in theSchemes:cloud is used judiciously by the responsible User Registration and Cloudstakeholders as per the service levelaccessagreements. The process shown in figure 2 Indexing the Cloud Data Finding similarity and avoiding13224
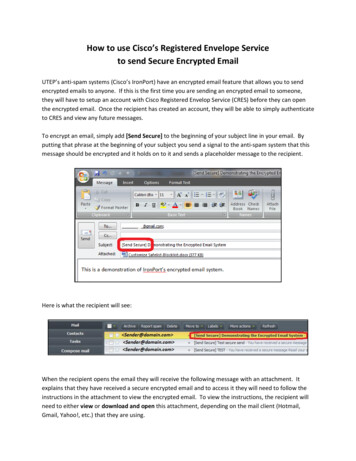
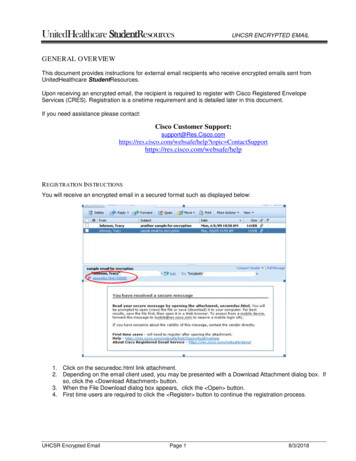
International Journal of Pure and Applied al Issue3.3.FINDING THE SIMILARITY ANDAVOIDING DEDUPLICATION:ThetoIn the deduplication process, which isprepare the dataset in avoid de-duplicationdivided into content-static and content-content. Indexing is nothing but consists ofdynamic. If the static category separate thestructuredformat.details of input information into same levelan unarrangeddata, which are comparing with one another.format. Sparse Indexing is based on theThe duplicates identify among the data thenreference format and capturing the repeatedbest way to eliminate by static method fromwordsthedisarrangement issues. Comparison betweenunarranged format into structured arrangedthe spare indexing pairs belonging to theformat. This may be avoiding the problem ofsimilar information and try to stopping thedelay during searching. Actually Sparededuplicationindexing are used to rapidly locating thetechniques. It is decreasing the user loadingdata without search the database in row-wisein the major tasks by deduplication. Thisin all time a database table is accessing. Thisprocess shown in uredformat isqueries.Indexingconvertsprocessusingnovelprocess shown in figure 3.Fig.4. Find similarity and avoiding.4. RESULTS AND DISCUSSION:4.1. USER REGISTRATION FORM:Users register for the cloud by the dataFig.3. Indexing the Cloud Dataowner and cloud service provider. In fig.5shows user needs to register their details for13225
International Journal of Pure and Applied Mathematicsaccessing the system, if the user registrationis successfully, user details saved inSpecial Issue4.3. Data User request to upload and download afile:database. Then only user can access theData user select the option request to uploadsystem with the unique public key for eachthe file that shown on figure 7. Then useruser.should select the file through the browse andsend request to data owner. Data owner viewthe request list and give the secret key touser and verified the keys. After the keyverified AP generates the secret key to thedata owner, once again check the keyverification and the select the upload optionfile upload to the cloud successfully.Fig.5. Data User Registration form4.2. User Login Form:After the successful registration, user canlogin for the cloud by the data owner andCSP. In fig 6 data Owner needs to login thecloud to access the system. Data Ownerenters their id and password to sign in thecloud. After the login process, to check thelogin id and password given by the user. If itis authorized means data owner to allow theuser access the cloud.Fig.7. Data User Upload formSame process for the download the file ,check the data owner and select which filegoing to download and the request the key tothe data owner and check that key areidentical or not. Then download the filefrom the cloud by the permission throughthe data owner shown in the fig.8.Fig.6. Data User Login formFig.8. Data User Download form13226
International Journal of Pure and Applied MathematicsSpecial Issue4.4. Cloud Service provider access upload the file:username, dataowner, filename and also theRegister for the cloud by the CSP needs tofile path.register their details for accessing thesystem. Login for the cloud with a secretkey. After the login process to access thefile. Then, choose the file and AESalgorithm using encrypted content andselected file is encrypted. The Encrypted fileis stored into the cloud. AF crawleralgorithm using to avoid the de-duplication.If the information wants to uploading theFig.10. File upload detailsfile with encrypted into the CSP. To avoidthe de-duplication file from the uploaded fileare stored into the cloud. If the informationIn the file count details are shown in theuser uploading that file into CSP to checkFig.11. in the cloud storage stored the filethe duplication file and intimates the de-only once by the CSP. This is our aim toduplication file. Process shown on figure 9.store the data only once but multiple usercan stored the same file in the cloud bymany times. CSP works to avoid theduplicate save again as a tag count only.Fig.9. CSP formFile uploading details are shown in Fig.10.The sql management where works in theback end. In the sql management whichstores the details about what are the processFig.11.File countdoing in the front end are stored. File uploadComparing of the effort and efficient way ofand File download details stored with thethe results in the process of deduplication13227
International Journal of Pure and Applied MathematicswithT3S-SVM.Usingthechecksumalgorithm its deviation values much lowerthan the previous algorithm. Using the highperforming clusters it can be reduced thereport is labeled pairs of average. Thistraining set for T3S-SVM and checksum ofthis experiment value is better illustrated.Evaluation of checksum with flexible anddatasets are shown empirically comparingwithbasic.Thisalgorithmabletorepresenting increasing the user-friendlywith good effectively.CONCLUSION AND FUTURE WORK:This technique is helps to upgrade thestorage usage level and also it on to reducing the lines of bytesthat must be sent. In the deduplication,unique a section of information or data, areidentified and storing during the progress ofanalysis. As the process, other informationor data is comparing to the storage identicaland whenever they are copied occurs, theredundant information or data is substitutewith a referral of stored data.In future work, information comesout as a type of security. This securityinformation can be digitally converted viathrough Gmail, Websites, spreadsheets, etc.all are not know about technology. Will beincrease the performance and more securedata transfer.13228Special IssueREFERENCES1.Bellare, M., Keelveedhi, S., &Ristenpart, T. (2013). DupLESS: ServerAidedEncryptionforDeduplicatedStorage. IACRCryptologyePrintArchive, 2013, 429.2.Dropbox, A file-storage and le: http://drive.google.com4.Mozy, Mozy: A File-storage andSharingService.(2016).[Online].Available: http://mozy.com/5.Douceur, J. R., Adya, A., Bolosky,W. J., Simon, P., & Theimer, M. (2002).Reclaiming space from duplicate files in aserverlessdistributedfilesystem.In Distributed Computing Systems, 2002.Proceedings. 22nd International Conferenceon (pp. 617-624). IEEE.6.Wu, T., Dou, W., Hu, C., & Chen, J.(2017). Service mining for trusted servicecompositionincross-cloudenvironment. IEEE Systems Journal, 11(1),283-294.7.Yan, Z., Ding, W., Yu, X., Zhu, H.,& Deng, R. H. (2016). Deduplication onencrypted big data in cloud. IEEEtransactions on big data, 2(2), 138-150.8.Wu, T. Y., Pan, J. S., & Lin, C. F.(2014). Improving accessing efficiency ofcloud storage using de-duplication andfeedbackschemes. IEEESystemsJournal, 8(1), 208-218.9.Fan, C. I., Huang, S. Y., & Hsu, W.C.(2012,August).Hybriddatadeduplication in cloud environment.In Information Security and nce on (pp. 174-177). IEEE.10.Z. Sun, J. Shen, and J. M. Yong,―DeDu: Building a deduplication storagesystem over cloud computing,‖ in Proc.IEEE Int. Conf. Comput. SupportedCooperative Work Des., 2011, pp. 348–355,doi:10.1109/CSCWD.2011.5960097.
International Journal of Pure and Applied Mathematics11.Ali, M., Khan, S. U., & Vasilakos,A. V. (2015). Security in cloud computing:Opportunities and challenges. Informationsciences, 305, 357-383.12.J. Pettitt, ―Hash of plaintext nks.venona.com/date/1996/02/msg02013.html13.C. W. Tsai, C. F. Lai, H. C. Chao,and A. V. Vasilakos, ―Big data analytics: Asurvey,‖ J. Big Data, vol. 2, no. 1, pp. 1–32,2015, doi:10.1186/s40537-015-003014.D. Perttula, B. Warner, and Z.Wilcox-O’Hearn, ―Attacks on convergentencryption.‖ (2016). [Online]. Available:http://bit.ly/yQxyvl.15.M. Bellare, S. Keelveedhi, and T.Ristenpart, ―Message-locked encryption CRYPT,2013,pp.296312.16.J. Paulo and J. Pereira, ―A surveyand classification of storage deduplicationsystems,‖ ACM Comput. Surveys, vol. .Z. Yan, W. X. Ding, and H. Q. Zhu,―A scheme to manage encrypted datastorage with deduplication in cloud,‖ inProc.ICA3PP2015, Zhangjiajie, China, Nov.2015, pp. 547–561.18.Logesh, R., Subramaniyaswamy, V.,Vijayakumar, V., Gao, X. Z., &Indragandhi, V. (2017). A hybrid quantuminduced swarm intelligence clustering forthe urban trip recommendation in smart city.Future Generation Computer Systems, 83,653-673.19.Subramaniyaswamy, V., & Logesh,R.(2017).AdaptiveKNNbasedRecommender System through Mining ofUser Preferences. Wireless PersonalCommunications, 97(2), 2229-2247.20.Logesh, R., & Subramaniyaswamy,V. (2017). A Reliable Point of InterestRecommendation based on Trust ns, 97(2), 2751-2780.13229Special Issue21.Logesh, R., & Subramaniyaswamy,V. (2017). Learning Recency and InferringAssociations in Location Based SocialNetwork for Emotion Induced Point-ofInterest Recommendation. Journal ofInformation Science & Engineering, 33(6),1629–1647.22.Subramaniyaswamy, V., Logesh, R.,Abejith,M.,Umasankar,S.,&Umamakeswari, A. (2017). SentimentAnalysis of Tweets for EstimatingCriticality and Security of Events. Journal ofOrganizational and End User Computing(JOEUC), 29(4), 51-71.23.Indragandhi, V., Logesh, R.,Subramaniyaswamy, V., Vijayakumar, V.,Siarry, P., & Uden, L. (2018). Multiobjectiveoptimizationandenergymanagement in renewable based Subramaniyaswamy, V., Manogaran,G., Logesh, R., Vijayakumar, V.,Chilamkurti,N.,Malathi,D.,&Senthilselvan, N. (2018). An ontologydriven personalized food recommendation inIoT-based healthcare system. The Journal ofSupercomputing, 1-33.25.Arunkumar, S., Subramaniyaswamy,V., & Logesh, R. (2018). Hybrid Transformbased Adaptive Steganography Schemeusing Support Vector Machine for CloudStorage. Cluster Computing.26.Indragandhi,V.,Subramaniyaswamy, V., & Logesh, R.(2017). Resources, configurations, and softcomputingtechniquesforpowermanagement and control of PV/wind hybridsystem. Renewable and Sustainable EnergyReviews, 69, 129-143.27.Ravi, L., & Vairavasundaram, S.(2016). A collaborative location based travelrecommendation system through enhancedrating prediction for the group of users.Computationalintelligenceandneuroscience, 2016, Article ID: 1291358.28.Logesh, R., Subramaniyaswamy, V.,Malathi, D., Senthilselvan, N., Sasikumar,A., & Saravanan, P. (2017). Dynamic
International Journal of Pure and Applied Mathematicsparticle swarm optimization for lographyfeedback.Biomedical Research, 28(13), 5646-5650.29.Arunkumar, S., Subramaniyaswamy,V., Karthikeyan, B., Saravanan, P., &Logesh, R. (2018). Meta-data based secretimage sharing application for different ravasundaram, S., Varadharajan,V., Vairavasundaram, I., & Ravi, L. (2015).Data mining‐based tag nary Reviews: Data Mining andKnowledge Discovery, 5(3), 87-112.31.Logesh, R., Subramaniyaswamy, V.,& Vijayakumar, V. (2018). A personalisedtravel recommender system utilising socialnetwork profile and accurate GPS data.Electronic Government, an InternationalJournal, 14(1), 90-113.32.Vijayakumar,V.,Subramaniyaswamy, V., Logesh, R., &Sivapathi, A. (2018). Effective KnowledgeBased Recommeder System for TailoredMultiple Point of Interest Recommendation.International Journal of Web Portals.33.Subramaniyaswamy, V., Logesh, R.,& Indragandhi, V. (2018). Intelligent sportscommentary recommendation system forindividual cricket players. s, 10(1-2), 103-117.34.Indragandhi,V.,Subramaniyaswamy, V., & Logesh, R.(2017). Topological review and analysis ofDC-DC boost converters. Journal ofEngineering Science and Technology, 12(6), 1541–1567.35.Saravanan, P., Arunkumar, S.,Subramaniyaswamy, V., & Logesh, R.(2017). Enhanced web caching using bloomfilter for local area networks. InternationalJournal of Mechanical Engineering andTechnology, 8(8), 211-217.13230Special Issue36.Arunkumar, S., Subramaniyaswamy,V., Devika, R., & Logesh, R. (2017).Generating visually meaningful encryptedimage using image splitting technique.International Journal of MechanicalEngineering and Technology, 8(8), 361–368.37.Subramaniyaswamy, V., Logesh, R.,Chandrashekhar, M., Challa, A., &Vijayakumar, V. (2017). A personalisedmovie recommendation system based oncollaborative filtering. International Journalof High Performance Computing andNetworking, 10(1-2), 54-63.38.Senthilselvan, N., Udaya Sree, N.,Medini, T., Subhakari Mounika, G.,Subramaniyaswamy, V., Sivaramakrishnan,N., & Logesh, R. (2017). Keyword-awarerecommender system based on userdemographic attributes. International Journalof Mechanical Engineering and Technology,8(8), 1466-1476.39.Subramaniyaswamy, V., Logesh, R.,Vijayakumar, V., & Indragandhi, V. (2015).Automated Message Filtering System inOnline Social Network. Procedia ComputerScience, 50, sh,R.,&Indragandhi, V. (2015). Unstructured dataanalysis on big data using map reduce.Procedia Computer Science, 50, sh,R.,&Indragandhi, V. (2015). Intelligent travelrecommendationsystembyminingattributes from community contributedphotos. Procedia Computer Science, 50,447-455.42.Vairavasundaram, S., & Logesh, R.(2017). Applying Semantic Relations forAutomatic Topic Ontology Construction.Developments and Trends in IntelligentTechnologies and Smart Systems, 48.
13231
13232
[3], Mozy [4], which helps to storage space reduce in the cloud storage by storing the each file only once of each uploaded file [7]. For example, Deduplication [11] e fficient method to avoid the duplicate file in the storage point of view, but it cannot be handle encrypted data [9][10] . In Encrypted