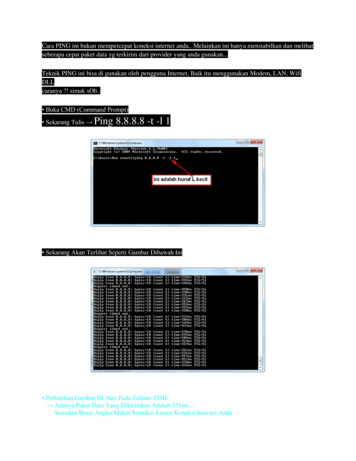
Transcription
CH A P T E R6Configuring the TLS Proxy onCisco Adaptive Security ApplianceJanuary 26, 2009NoteFor up to date release information on configuring the TLS proxy, please refer to theCisco Adaptive Security Appliance Configuration Guide at the following URL:http://www.cisco.com/en/US/products/ps6120/tsd products support configure.html TLS Proxy, page 6-1 Access List Configuration Requirements, page 6-2 Configuring the TLS Proxy Instances, page 6-3 Associating an Access List with a TLS Proxy Instance Using Class Maps, page 6-4 Enabling the TLS Proxy, page 6-5 Configuring Cisco Adaptive Security Appliance for an Intercluster Deployment, page 6-6TLS ProxyCisco Adaptive Security Appliance acts as a TLS proxy between the Cisco Unified Presence and theforeign server. This allows Cisco Adaptive Security Appliance to proxy TLS messages on behalf of theserver (that initiates the TLS connection), and route the TLS messages from the proxy to the client. TheTLS proxy decrypts, inspects and modifies the TLS messages as required on the incoming leg, and thenre-encrypts traffic on the return leg.NoteBefore configuring the TLS proxy, you must configure the Cisco Adaptive Security Appliance securitycertificates between Cisco Adaptive Security Appliance and Cisco Unified Presenceo, andCisco Adaptive Security Appliance and the foreign server. Complete the procedures in the followingsections to accomplish this: How to Configure Security Certificate Exchange Between Cisco Unified Presence andCisco Adaptive Security Appliance, page 4-1 How to Configure Security Certificate Exchange Between Cisco Adaptive Security Appliance andMicrosoft Access Edge (External Interface) Using a Microsoft CA, page 4-5Integration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-1
Chapter 6Configuring the TLS Proxy on Cisco Adaptive Security ApplianceAccess List Configuration RequirementsRelated TopicsCommon Cisco Adaptive Security Appliance Problems and Recommended Actions, page 10-1.Access List Configuration RequirementsTable 6-1 lists the access list configuration requirements for a single Cisco Unified Presencedeployment.NoteTable 6-1 For each access list, you must configure a corresponding class-map, and configure an entry in thepolicy-map global policy. You can check the peer auth listener port on Cisco Unified Presence by selectingCisco Unified Presence Administration System Application Listeners.Access List Configuration RequirementsDeployment ScenarioConfiguration RequirementConfiguration ExampleA Cisco Unified Presenceserver federating with one ormore foreign domainsConfigure the following two access lists foreach foreign domain thatCisco Unified Presence is federates with:access-list ent cup to foreign serverextended permit tcp host routing cupprivate address host foreign publicaddress eq 5061Configure an access list to allowCisco Unified Presence to sendmessages to the foreign domain on port5061.access-list ent foreign server to cupextended permit tcp host foreignpublic address host CUP publicaddress eq 5061 Configure an access list to allowCisco Unified Presence to receivemessages from the foreign domain onport 5061.Integration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-2
Chapter 6Configuring the TLS Proxy on Cisco Adaptive Security ApplianceConfiguring the TLS Proxy InstancesDeployment ScenarioConfiguration RequirementConfiguration ExampleIntercluster deploymentConfigure the following two access lists foreach intercluster Cisco Unified Presenceserver.access-listent intercluster cup to foreign serverextended permit tcp host interclustercup private address host foreignpublic address eq 5061(This also applies to amulti-node deployment) Configure an access list to allowCisco Unified Presence to sendmessages to the foreign domain on port(5061).Configure an access list to allowCisco Unified Presence to receivemessages from the foreign domain on thearbitrary port.There are two configuration options:Cisco Unified Presence toCisco Unified Presence For each interclusterFederation, where the foreignCisco Unified Presence server in thedomain has added one or moreforeign domain, configure an access listinterclusterto allow the localCisco Unified Presence serversCisco Unified Presence to sendmessages to the interclusterCisco Unified Presence on the arbitraryport. Note that if you use thisconfiguration option, you must retrievethe arbitrary port number from thesystem administrator of the foreignenterprise deployment. Configure an access list to allow thelocal Cisco Unified Presence serveraccess any port in the foreign domain.access-listent foreign server to intercluster cupextended permit tcp host foreignpublic address host cup publicaddress eq arbitrary port access-listent cup to foreign intercluster cupextended permit tcp host privaterouting cup host foreign companypublic cup address eq arbitraryport .access-listent cup to foreign interclustercupextended permit tcp host privaterouting cup host foreign public cupaddress Related Topics Sample Cisco Adaptive Security Appliance Configuration, page A-1 Configuring the TLS Proxy Instances, page 6-3 Associating an Access List with a TLS Proxy Instance Using Class Maps, page 6-4 Enabling the TLS Proxy, page 6-5Configuring the TLS Proxy InstancesFor this integration, you need to create two TLS proxy instances. The first TLS proxy handles the TLSconnections initiated by Cisco Unified Presence, where Cisco Unified Presence is the client and theforeign domain is the server. In this case, the Cisco Adaptive Security Appliance acts as the TLS serverfacing the "client" which is Cisco Unified Presence. The second TLS Proxy handles the TLS connectionsinitiated by the foreign domain, where the foreign domain is the client and Cisco Unified Presence is theserver.Integration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-3
Chapter 6Configuring the TLS Proxy on Cisco Adaptive Security ApplianceAssociating an Access List with a TLS Proxy Instance Using Class MapsThe TLS proxy instance defines “trustpoints” for both the server and the client. The direction from whichthe TLS handshake is initiated determines the trustpoint defined in the server and client commands: If the TLS handshake initiates from Cisco Unified Presence to the foreign domain, the servercommand specifies the trustpoint that contains the Cisco Adaptive Security Appliance self-signedcertificate. The client command specifies the trustpoint that contains theCisco Adaptive Security Appliance certificate that is used in the TLS handshake betweenCisco Adaptive Security Appliance and the foreign domain. If the handshake initiates from the foreign domain to Cisco Unified Presence, the server commandspecifies the trustpoint that contains the Cisco Adaptive Security Appliance certificate the TLShandshake uses between Cisco Adaptive Security Appliance and the foreign domain. The clientcommand specifies the trustpoint that contains the Cisco Adaptive Security Appliance self-signedcertificate.Before You Begin Complete the steps in Access List Configuration Requirements, page 6-2.ProcedureStep 1Enter config mode: Enable password config tStep 2Create a TLS proxy instance for TLS connections initiated by Cisco Unified Presence. This examplecreates a TLS proxy instance called cup to foreign:tls-proxy ent cup to foreignserver trust-point cup proxyclient trust-point trustpoint name client cipher-suite aes128-sha1 aes256-sha1 3des-sha1 null-sha1Step 3Create a TLS proxy instance for TLS connections initiated by a foreign domain. This example creates aTLS proxy instance called foreign to cup:tls-proxy ent foreign to cupserver trust-point trustpoint name client trust-point cup proxyclient cipher-suite aes128-sha1 aes256-sha1 3des-sha1 null-sha1What To Do NextAssociating an Access List with a TLS Proxy Instance Using Class Maps, page 6-4Associating an Access List with a TLS Proxy Instance UsingClass MapsUsing the class map command, you need to associate a TLS Proxy instance to each of the foreign domainaccess lists you defined previously.Integration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-4
Chapter 6Configuring the TLS Proxy on Cisco Adaptive Security ApplianceEnabling the TLS ProxyBefore You BeginComplete the steps in Configuring the TLS Proxy Instances, page 6-3ProcedureStep 1Enter config mode: Enable password config tStep 2Associate each of your access lists with the TLS proxy instance that the class map uses. The TLS proxyyou select depends on whether the class-map is for messages from Cisco Unified Presence to a foreigndomain, or from a foreign domain to Cisco Unified Presence.In the example below, the access list for messages sent from Cisco Unified Presence to a foreign domainis associated with the TLS proxy instance for TLS connections initiated by Cisco Unified Presencecalled “ent cup to foreign”:class-map ent cup to foreignmatch access-list ent cup to foreignStep 3If you are have an intercluster Cisco Unified Presence deployment, configure a class map for eachCisco Unified Presence server, and associate this with the appropriate access-list for the server that youdefined previously, for example:class-map ent second cup to foreignmatch access-list ent second cup to foreignWhat To Do NextEnabling the TLS Proxy, page 6-5Enabling the TLS ProxyUsing the policy map command, you need to enable the TLS proxy for each class map you created in theprevious section.NoteYou cannot use a High security sip-inspect policy map on Cisco Adaptive Security Appliance for afederated deployment because the configuration will fail. You must use a Low/Medium security policymap.Before You BeginComplete the steps in Associating an Access List with a TLS Proxy Instance Using Class Maps, page 6-4ProcedureStep 1Enter config mode: Enable password config tIntegration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-5
Chapter 6Configuring Cisco Adaptive Security Appliance for an Intercluster DeploymentStep 2Configuring the TLS Proxy on Cisco Adaptive Security ApplianceDefine the sip-inspect policy map, for example:policy-map type inspect sip sip inspectParameters!SIP Inspection ParametersStep 3Define the global policy map, for example:policy-map global policyclass ent cup to foreigninspect sip sip inspect tls-proxy ent cup to foreignConfiguring Cisco Adaptive Security Appliance for anIntercluster DeploymentFor an intercluster Cisco Unified Presence deployment, you must perform the following configurationon the Cisco Adaptive Security Appliance for each additional Cisco Unified Presence server.ProcedureStep 1Create an additional access list for the Cisco Unified Presence server.Step 2Generate and import the Cisco Adaptive Security Appliance security certificate onto theCisco Unified Presence server.Step 3Generate and import the Cisco Unified Presence security certificate ontoCisco Adaptive Security Appliance.Step 4Configure a class map for each foreign domain.Step 5Include the class maps in the global policy map.Related Topics How to Configure Security Certificate Exchange Between Cisco Unified Presence andCisco Adaptive Security Appliance, page 4-1 How to Configure Security Certificate Exchange Between Cisco Unified Presence andCisco Adaptive Security Appliance, page 4-1 Associating an Access List with a TLS Proxy Instance Using Class Maps, page 6-4 Enabling the TLS Proxy, page 6-5 Intercluster and Multi-node Deployment, page 1-2Integration Guide for Configuring Cisco Unified Presence Release 7.0 for Interdomain Federation6-6
TLS Proxy Cisco Adaptive Security Appliance acts as a TLS proxy between the Cisco Unified Presence and the foreign server. This allows Cisco Adaptive Security A ppliance to proxy TLS messages on behalf of the server (that initiates the TLS connec tion), and route the TLS messages from the proxy to the client. The