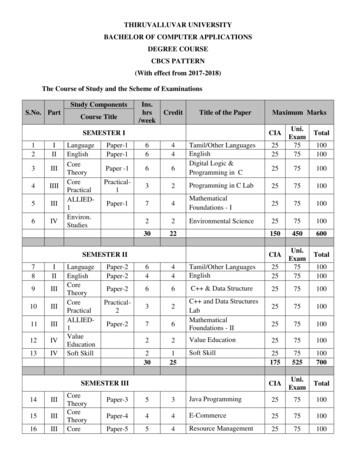
Transcription
Continue
Sistemas operativos deitel pdf download gratis para windows 10This technique provides high reliability and simplifies data regeneration but incurs substantial storage overhead, which increases cost. On an SVM system, when a process requests a page that is not in its processor's local memory, the operating system loads the page into local memory from another memory module (i.e., from a remote computer overa network) or from secondary storage (e.g., a disk). deadlock avoidance—Strategy that eliminates deadlock by allowing a system to approach deadlock, but ensuring that deadlock never occurs. SELinux replaces Linux's default discretionary access control policy with a mandatory access control (MAC) policy (see Section 19.4.2, Access Control Modelsand Policies). Van Riel, R., "Page Replacement in Linux 2.4 Memory Management" . NTFS does not delete the file until all hard links to the file are removed. Intrusion detection products are commercially available from companies such as Cisco (www.cisco.com/warp/public/cc/pd/sqsw/ sqidsz), Hewlett-Packard (www.hp.com/security/home.html) andSymantec 900 Security (www.symantec.com). AFS is a global file system that appears as a branch of a traditional UNIX file system at each workstation, ft is based on the client-server model and relies on RPCs for communication. To minimize the waiting time for threads that share resources and operate at the same average speeds, we know fromearlier in this chapter that we can implement a circular buffer that provides extra buffer slots into which the producer can place values at times when it is running faster than the consumer and from which the consumer can retrieve those values when it is running faster than the producer. system worker thread (Windows XP)—Thread controlled bythe system that sleeps until a kernel-mode component queues a work item for processing. Most devices that Linux supports belong to three primary categories: character devices, block devices and network devices. Once a weakness is discovered, a worm can produce network traffic sufficient to disable a single computer or a network of computers.www.pdl.emu.edu/RAID/ Overviews RAID and provides links to current RAID research. The count is decremented every time a thread acquires access to the pool of resources protected by the semaphore and incremented when a thread releases the semaphore. If the resource is available, the thread acquires the lock, accesses the resource, thenreleases the spin lock. 1o. invalidation—Memory-coherence protocol in which a process first invalidates—i.e., voids—all other copies of a page before writing to the page. 945 20.3.1 20.3.2 20.3.3 20.3.4 Development and Community. page replication—Technique in which the system maintains multiplecopies of a page at different nodes so that it can be accessed quickly by multiple processors. Venus located resources based on pathname. Linux kernel source code, version 2.5.56, . Many operating systems provide defragmentation (or disk reorganization) programs that can be used periodically to reorganize files. transitional fault (Windows XP)—Fault issued by the MMU when it tries to access a page that is in main memory, but whose page frame's status is set to standby, modified, or modified no-write. B., "Windows NT Page Replacement Policies," Computer Measurement Group, 1999, . Variables writerPosition and readerPosition (lines 4-5) indicate in which slot of the circular buffer thenext item is to be placed by a producer and from which slot of the circular buffer the next item is to be removed by a consumer, respectively. There are two primary security concerns in distributed file systems: ensuring secure communications and guaranteeing correct file access permissions. Justify your answers. page directory register—Hardwareregister that stores a pointer to the current process's page directory table. L., Modula-2 Programming, New York: McGrawHill, 1985. Some systems prevent indefinite postponement by increasing a process's priority gradually as it waits for a resource —this technique is called aging. 1066 21.7 Memory allocation stages. 598 13.6 FileAllocation. Semaphore Semaphore's count rises above zero. Smaller strip sizes, also called fine-grained strips, tend to spread file data across several disks. When a packet arrives, the system awakens one of these threads to complete the I/O processing.311 Data Transfer TechniquesA driver can choose from three methods for transferring data between a device and a process's memory space by setting flags in the device object for that device.312 If the driver chooses buffered I/O, the I/O manager allocates system pages to form a buffer equal to the size of the requesting thread's buffer. Windows XP incorporates many of thefeatures that made the consumer line popular. The miniport driver also processes the NIC's interrupts and passes data that the NIC receives up the driver stack.415 21.11 Networking 1103 NDIS intermediate drivers are optional drivers that reside between a miniport driver and a higher-level driver. This scheme does not scale well to large systemsdue to communication cost and page size. Operating Systems and Database Systems. Although the system could still function w i t h only a single processor, having the extra processors yields better performance because the processors can all work in parallel. For example, a suspend/resume mechanism can beapplied to a system as a whole, allowing a user to shut down the entire system and start it later without loss of work. Lomet, D. Security groups can be nested and grouped to form larger security groups. 2) Because P2 is the only process whose current claim can be satisfied by the two available resources. kernel thread (Linux)—Thread that executeskernel code. 344- "Named Pipe Type, Read, and Wait Modes," MSDN Library, February 2003, m s d n . Brinch Hansen, P., "The Programming Language Concurrent Pascal," IEEE Transactions on Software Engineering, No. 2, June 1975,199-206. Mitchell; and X M. Further, a RAID 0 system with n disks performs reads and writes at a rate up to ntimes greater than that of a single disk. Instructions such as test-and-set can be inefficient when the data these instructions reference is located in remote memory. Hennessy, J., and D. Consider a search engine being used for an application where lives could be at stake, such as locating organs for transplant. If a page table entry is present in theswap cache, then its corresponding page exists in the swap file and does not need to be written to the swap file. Industry professionals must build real systems that work and meet the demanding cost, performance and reliability requirements of customers. com allows developers to build online stores that search its product databases and displaydetailed product information via Amazon.com Web Services (www.amazon.com/gp/aws/landing.html). For instructors, the Companion Web site includes a Syllabus Manager, which helps instructors plan courses interactively and create online syllabi. Russell, P., "Unreliable Guide to Hacking the Linux Kernel," 2000, . 18.15 Describe the three basictypes of entities of JXTA. In this case, each philosopher will hold exactly one fork, and no forks will remain available on the table. The second strategy requires the process to give up the resources it already has, possibly causing wasteful loss of work. HMD vividly recalls the excitement at Biographical Note Doug Engelbart Doug Engelbart inventedthe San Francisco, Engelbart and his NLS system was to create a system computer mouse and was one of coworkers displayed their com- that could help people solve prob- the primary designers of the origi- puter system, NLS (oNLine System) lems faster and enhance i n t e r - nal graphical displays and w i n - which featured Engelbart's com- gence.Similarly, instead of writing directly to the disk, a process writes new data to the cache entry (unless a flag is set).331 Fulfilling an I/O request without generating an IRP or accessing a device is called fast I/O.332 Dirty cache entries can be written to disk in several ways. However, transactions using PKI and digital certificates can be more securethan exchanging private information over public, unencrypted media such as voice phone lines, paying through the mail, or handing a credit card to a sales clerk. Proprietary systems, on the other hand, typically are installed with an appropriate security configuration by default. Space in the nonpaged pool is limited. Process migration allows theprogram to move to another machine to continue computation perhaps in a more stable environment. Error-correction codes (ECCs). 56 . Cyber Classrooms, Complete Training Courses and Web-Based Training Courses published by Prentice Hall Computer Science Series Operating Systems, 3/E How To Program Series Advanced Java 2 PlatformHow to Program C How to Program, 4/E C How to Program, 4/E C# How to Program e-Business and e-Commerce How to Program Internet and World Wide Web How to Program, 3/E Java How to Program, 5/E Perl How to Program Python How to Program Visual Basic 6 How to Program Visual Basic .NET How to Program, 2/E VisualC .NET How to Program Wireless Internet & Mobile Business How to Program XML How to Program Simply Series Simply C# :An Application-Driven Tutorial Approach Simply Java Programming: An Application-Driven Tutorial Approach Simply Visual Basic .NET: An ApplicationDriven Tutorial Approach (Visual Studio .NET2002 Edition)Simply Visual Basic .NET: An ApplicationDriven Tutorial Approach (Visual Studio .NET2003 Edition) CS1 Programming Series Java Software Design .NET How to Program Series C# How to Program Visual Basic .NET How to Program, 2/E Visual C .NET How to Program Visual Studio Series C# How to Program Getting Started withMicrosoft Visual C 6 with an Introduction to MFC Simply C# :An Application-Driven Tutorial Approach Simply Visual Basic .NET: An ApplicationDriven Tutorial Approach (Visual Studio .NET2002 Edition) Simply Visual Basic .NET: An ApplicationDriven Tutorial Approach (Visual Studio .NET 2003 Edition) Visual Basic 6 How to ProgramVisual Basic .NET How to Program, 2/E Visual C .NET How to Program Deitel Developer Series Java Web Services for Experienced Programmers Web Services A Technical Introduction For Managers Series e-Business and e-Commerce for Managers Interactive Web-Based Training Series Premium CourseCompass Version of Visual Basic .NET Multimedia Cyber Classroom, 2/E Premium CourseCompass Version of Java 2 Multimedia Cyber Classroom, 5/E Premium CourseCompass Version of C Multimedia Cyber Classroom, 4/E The Complete Training Course Series The Complete C Training Course, 4/E The Complete C# Training Course The Complete e-Business and eCommerce Programming Training Course The Complete Internet and World Wide Web Programming Training Course, 2/E The Complete Java 2 Training Course, 5/E The Complete Perl Training Course The Complete Python Training Course The Complete Visual Basic 6 Training Course The Complete Visual Basic .NET Training Course, 2/E TheComplete Wireless Internet & Mobile Business Programming Training Course The Complete XML Programming Training Course Interactive Multimedia Cyber Classroom Series C Multimedia Cyber Classroom, 4/E C# Multimedia Cyber Classroom e-Business and e-Commerce Multimedia Cyber Classroom Internet and World Wide WebMultimedia Cyber Classroom, 2/E Javam2 Multimedia Cyber Classroom, 5/E Perl Multimedia Cyber Classroom Python Multimedia Cyber Classroom Visual Basic 6 Multimedia Cyber Classroom Visual Basic .NET Multimedia Cyber Classroom, 2/E Wireless Internet & Mobile Business Programming Multimedia Cyber Classroom XML MultimediaCyber Classroom To follow the Deitel publishing program, please subscribe to the free Deitel Buzz Online e-mail newsletter at: www.deitel.com/newsletter/subscribe.html To communicate with the authors, send e-mail to: [email protected] For information on Deitel instructor-led, corporate training seminars offered worldwide visit: www.deitel.comFor continuing updates on Prentice Hall and Deitel publications visit: www.deitel.com, www.prenhall.com/deitel or www.InformIT.com/deitel Vice President and Editorial Director, ECS: Marcia J. We follow the development of key operating systems including CTSS, Multics, CP/CMS and Unix. Ans: 1) SSTF is most similar to the shortest-process-first(SPF) strategy. Though each method offers relative merits and pitfalls, both require attention to security and timely releases of patches to fix any security flaws that are discovered. Further, these early systems required that an entire program be loaded into memory for the program to run. —Heraclitus — Open sesame! - T h e History of Ali BabaChapter 1 Introduction to Operating Systems Objectives After reading this chapter, you should understand: what an operating system is. 1.13 Operating System Architectures 33 1.13 Operating System Architectures Today's operating systems tend to be complex because they provide many services and support a variety of hardware and softwareresources (see the Operating Systems Thinking feature, Keep It Simple (KIS) and the Anecdote,). Innovations in programming and hardware have led to more powerful and useful technologies, including object-oriented programming, distributed computing, Internet protocols and XML (Extensible Markup Language). ) claim) 7.8 Deadlock Avoidancewith Dijkstra's Banker's Algorithm 311 Self Review 1. 19.19 Design a penetration study for a large computer system with which you are familiar. If a graph cannot be reduced by all its processes, then the irreducible processes constitute the set of deadlocked processes in the graph. When a process holding the lock is executing inside its criticalsection, any process concurrently executing on a different processor that attempts to acquire the lock before entering its critical section is made to busy wait. Objectives Next, objectives tell you what to expect and give you an opportunity, after reading the chapter, to determine whether you have met these objectives. There are considerable overlapsas well as significant differences in what academics and industry professionals think about. Although the kernel often reduces seek time by sorting block device requests, in some cases the request list is detrimental to performance. "InterruptService," MSDN Library, June 6, 2003. RAID level 2 borrows from a technique that is commonly implementedin memory modules called Hamming error-correctins codes (Hamming ECCs), which uses parity bits to check for errors in data transmitted from disks and to correct them, if possible.68 Parity bits can be calculated as follows. For example, two threads may each hold a resource that the other thread is waiting to use. port of Linux—Version of theLinux kernel that is modified to support execution in a different environment. In these cases, threads use wait functions and treat these objects just like other dispatcher objects.183 Dispatcher Object Transitions from Unsignaled to Signaled State When Event Associated event occurs. A.; Fortier, M.; and Coffin, M., "Monitor Classification," ACMComputing Surveys,Vol. OS/2 also made significant improvements over DOS. A key problem with SPF is that it requires precise knowledge of how long a process will run, and this information usually is not available. Cherepov, M., et al., " H a r d Real-Time with Venturcom R T X on Microsoft Windows XP and Windows XP Embedded," MSDN Library,June 2002, m s d n . Processor-bound processes might use the processor for hours at a time if the system makes it available on a nonpreemptible basis. Remote file system drivers cooperate with the I/O manager, but instead of interacting with volume drivers, remote file system drivers interact with remote file system drivers on other computers. 532.1 2.2 Introduction. Real-time systems require that tasks be performed within a particular (often short) time frame. 254. denial of access to legitimate system users iii. Schiller, "Kerberos: An authentication service for open network systems," In Proceedings of the Winter 1988USENIX, February 1988, pp. Although not as fault tolerant as a crossbar-switch matrix, a 2-D mesh network is more so than other simple designs, such as a shared bus. In one context, the reserved memory acts as a cache, allowing processes quick access to data that would otherwise need to be fetched from disk. This strategy has been shown to beclose to the theoretical optimum and is relatively easy to implement. 815 18.1 Introduction. Thus, many RAID systems contain spe- Operating Systems Thinking Mission-Critical Systems There are systems where the cost of failure is so high that enormous investment must be madein resources to ensure that the systems do not fail and perform well enough to meet their requirements. The value of the seqlock's sequence counter is initialized to zero. 176. In some cases, the operating system must make extraordinary resource commitments to particular applications, far greater than what general-purpose applications wouldnormally receive. While the thread is in the monitor, other threads may not enter the monitor to acquire the resource. Using a search engine from a Web browser is an example of a client/server application. www.sun.com/software/solaris/trustedsolaris/ index.html Provides information about the trusted Solaris operating environment. For example,suppose a customer wishes to place an order with an online merchant. Write to disk. Linux implements shared memory as a virtual memory area that is mapped to a region of physical memory. Similarly, the algorithm requires that clients (i.e., processes) repay all loans (i.e., return all resources) within a "finite time." Again, much better guaranteesthan this are needed in real systems. 6.2.3 Monitor Example: Circular Buffer In this section we discuss the circular buffer (sometimes called the bounded buffer. Monitors are also the primary mechanism to provide mutual exclusion and synchronization in multithreaded Java applications. 1099 21.11.1 NetworkInput/Output. n e t / m i c h a l n / h i s tory/os220/index.html . Also, because all layers have unrestricted access to the system, layered kernels are also susceptible to damage from errant or malicious code. Each LAN can be connected to the Internet through a gateway, which typicallyincludes a firewall. Why might it be a worse policy? Spinning is not desirable when system load is high and the expected time before the resource is available is greater than context-switch time; in these cases, spinning uses valuable processor cycles. "Named Pipe Type, Read, and Wait Modes," MSDN Library, February 2003, . "Introduction toStandard Driver Routines," MSDN Library, June 6, 2003, m s d n . "Bus Drivers," MSDN Library, June 6, 2003, . A user can set security permissions for any security principal.471 It is often advantageous to place users with the same security privileges into a security group, then set security permissions based on the security group. 19.8 Polymorphicvirus. Alternatively, developers can layer NetBIOS over UDP and IP for connectionless communication using NBT. By 1994 the Web community had grown large enough that he started the World Wide Web Consortium (W3C; www.w3.org) to Berners-Lee graduated from Queen's College at Oxford University with a degree in Physics in 1976. If, over aperiod of time, we determine that the producer often produces as many as three more values than the consumer can consume, we can provide a buffer of three or more slots to handle the extra production. 762 16.7.1 Internet Protocol (IP) . The problem requires the programmer to ensure thata set of n philosophers at a table containing n forks, who alternate between eating and thinking, do not starve while attempting to acquire the two adjacent forks necessary to eat. Falling technology costs also led to an increase in the number of home computers, which were used both for work and for entertainment. device special file (Linux)—Entryin the /dev directory that provides access to a particular device. The LaTeX Project, "LaTeX Project home page," January 27. A survey of cryptography and the related problem of computability is provided in Jorg Rothe's "Some Facets of Complexity Theory and Cryptography: A Five-Lecture Tutorial."151 The problem of access control is activelydiscussed in the literature; a survey of access control can be found in Sandhu and Samarati's "Access Control: Principles and Practice."152 and publications have emerged since the 1990s. Later, another low-priority thread zeroes the bits of pages on the Free Page List and moves the pages to the Zeroed Page List. 35 The Multics project eventually ledto the creation of the UNIX operating system in 1969. 86. DPCs are software interrupts that execute at the DPC/dispatch IRQL109 and which run in the context of the currently executing thread. Multiprocessing is common, and parallel computation will be prevalent. Network Basic Input/Output System (NetBIOS) (Windows XP)—API used to supportNetBEUI and now used with NBT. 18.21 Prepare a research paper for Web services. Discuss the advantages and disadvantages of such a scheme. For example, the processor and high-speed cache memories are managed designer must be aware of trends that could affect the relative value of system resources and people time and must respondsystems need to manage particu- much more intensively than sec- quickly to change. But consider what happens when a request for additional resources cannot be satisfied. In AFS-2 and AFS-3, the server becomes responsible for ensuring each client has the most up-to-date copy of its riles. Also, because parity is distributed throughout the array,data regeneration is more complicated than in other RAID levels.85 Despite its limitations, RAID level 5 is frequently adopted due to its effective balance of performance, cost and reliability. 360 Part 3 Physical and Virtual Memory. Recommended Reading 329 7.43 (Deadlock Avoidance Simulation Project) Writea simulation program to examine the performance of a system of n identical resources and m processes operating under banker'salgorithm resource allocation. Chapter 12—Disk Performance Optimization—focuses on the characteristics of moving-head disk storage and how the operating system can optimize its performance. Maximize resourceutilization. 6778. 502 11.10 Page Size. Windows XP provides spin locks to address this problem. This example illustrates that even when communications are kept among neighboring processors, load balancing can effectively distribute processing responsibilities throughoutthe system. Servicing requests that will soon expire reduces the number of times the scheduler will be interrupted from servicing requests at the head of the list, which improves throughput. To reduce the possibility of such a situation occurring, Linux provides the LSM Capabilities module to implement capabilities (see Section 19.4.3, Access ControlMechanisms). However, most user processes do not call native API functions directly; rather, they call API functions exposed by user-mode system components called environment subsystems. To transmit a message, WEP first appends a checksum to the message to enable the receiver to verify message integrity. Multiprocessors that allow only onecopy of a page to be resident in the system at a time (such as UMA and small NUMA systems) must still ensure cache coherence —reading a cache entry reflects the most recent update to that data. Thus, many operating systems provide interprocess communication (IPC) and synchronization mechanisms to simplify such concurrent programming. Forexample, consider a system in which a running process is almost complete and a new process with a small estimated service time arrives. Several methods for providing secure transactions have been developed in recent years. Some systems also feature hot swappable disk drives that can to be replaced while the system is online. Shepler, S., et al.,"NFS Version 4 Protocol," December, 2000, . Buffering and Caching To reduce the number of block I/O operations for disk devices, the kernel buffers and caches I/O requests. 270 7 Deadlock and Indefinite Postponement. filter driver—WDM (Windows Driver Model) driver that modifies thebehavior of a hardware device (e.g., providing mouse acceleration) or adds some extra services (e.g., security checks). Ans: 1) Timesharing scheduling executes related processes simultaneously, improving performance for processes that interact frequently because processes can react to messages or modifications to shared memory immediately. Wecannot predict the relative speeds of asynchronous concurrent processes. Have each process generate a set of resources that it wants (e.g., 3 of resource A, 1 of resource B and 5 of resource C). defragmentation— Moving parts of files so that they are located in contiguous blocks on disk. Now imagine that many research assistants and only oneprincipal investigator are using the system. H., "Proving Monitors," Communications of the ACM, Vol. int[] a v a i l a b l e ) that determines whether the system is in a safe state. This edition omits that material, recognizing that operating systems is for the most part not a mathematical field. Jens Axboe, SUSE Labs Dibyendu Baksi, ScientificTechnologies Corporation Columbus Brown, IBM Fabian Bustamante, Northwestern University Brian Catlin, Azius Developer Training Stuart Cedrone, Hewlett-Packard Randy Chow, University of Florida Alan Cox, Red Hat UK Matthew Dobson, Independent Consultant Ulrich Drepper, Red Hat, Inc. 8.3, process P1 is dispatched to a processor, whereit executes either until completion, in which case it exits the system, or until its time slice expires, at which point it is preempted and placed at the tail of the ready queue. What is one drawback to this strategy? The configuration manager is also responsible for managing registry storage in system memory and in the hives.83 21.5.2 Object ManagerWindows XP represents physical resources (e.g., peripheral devices) and logical resources (e.g., processes and threads) with objects. 26. The next time a thread begins writing, the thread can reset the event object to the unsignaled state. Wegner, P., and S. 2) The low-level scheduler should remain resident in main memory because it executesfrequently, requiring it to respond quickly to reduce scheduling overhead. 18.7.4 Java Management Extensions (JMX) . 12.10.2 Level 0 (Striping) RAID level 0 uses a striped disk array with no redundancy. Public Key Infrastructure (PKI) provides a solution by integrating public-key cryptography with digitalcertificates and certificate authorities to authenticate parties in a transaction. The I/O manager sends the IRP to the Multiple UNC Provider (MUP), which is a file system driver that determines the appropriate redirector to which to send the request (3). The I/O manager interface enables Windows XP to support multiple file systems. Cesati,Understanding the Linux Kernel, O'Reilly, 2001. .NET is aimed at transforming computing from an environment where users simply execute applications on a single computer to a fully distributed environment. (T/F) An unsafe state is a deadlocked state. core file (Linux)—File that contains the execution state of a process, typically used for debuggingpurposes after a process encounters a fatal exception. Chapter 3—Process Concepts—begins our discussion of operating system primitives by defining the fundamental notion of process. This is because the cache manager caches by mapping files into the system's virtual address space, rather than managing the cache from physical memory.Schedulers employ algorithms that make choices about preemptibility, priorities, running time and other process characteristics. This means that write requests must be performed one at a time, creating a write bottleneck. Ans: 1) Read/write locks are more efficient than spin locks when multiple processes read a memory location, but do not write toit. Let claim(Pi) be the current claim of a process, where a process's claim is equal to its maximum need minus its current loan. When a client receives a callback, it knows that its cached version is no longer valid and requests the newest version from the server. "Protection and Security," h t t p : / / c s . 17.2.6 Distributed Operating Systems. 6-13. One common variation of the multilevel feedback queuing mechanism is to have a process circulate round-robin several times through each queue before it moves to the next lower queue. This process, which degrades performance because the system must access the array twice for each write,is called a read-modify-write cycle. The two men had written the compiler in just eight weeks and had never tested it on the computer for which it was inten
Visual Basic .NET How to Program, 2/E Visual C .NET How to Program Deitel Developer Series Java Web Services for Experienced Programmers Web Services A Technical Introduction For Managers Series e-Business and e-Commerce for Managers Interactive Web-Based Training Series Premium CourseCompass Version of Visual Basic .