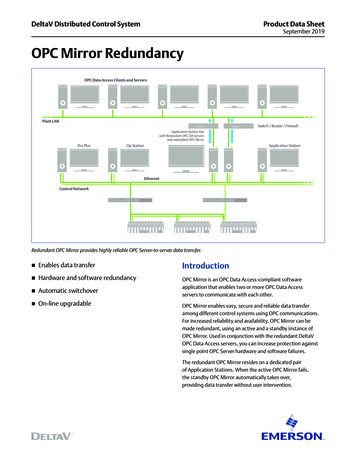
Transcription
”OPC UA Security Testing”(Brief introduction)OPC Day 18.10.2016 (Beckhoff, Hyvinkää)Pasi Ahonen & Sami NoponenVTT Technical Research Centre of Finland
07/10/20162Before starting, the penetration tester needs to knowWho is bad?Ref: “Reviewing a year of serious data breaches, major attacks and new vulnerabilities: Analysis of cyber attack and incident data fromIBM’s worldwide security services operations”, IBM X-Force Research, 2016 Cyber Security Intelligence Index.
07/10/20163The cybercrime business is now PROFESSIONAL SERVICES!Tester needs tounderstandwhat“services”attacker usesRef: TREND MICRO (2015), Russian Underground 2.0.
How to improve testing? – VTT industrial projectsTVOVTT WAR ROOMICS-1Turun seudunpuhdistamoSecureProductionDCS-1Secure Products& ServicesPLC-14Vendors &Service providersABBVALMET/METSOINSTA HELENPartnershipsORIONVALIOCustomer specificCyber securitytest environmentsPartnersNESAThe National CyberSecurity Centre FinlandTUTSynopsysRugged Tooling
07/10/20165Where to test without damages?At VTT Cyber Security War Room!What is the War Room? Includes a mini-Internet environment that is completely isolatedfrom all other telecommunicationsDevices or software can be subjected to highly realistic cyberattacks in a controlled wayWide range of attacks can be tried to test the performance ofvarious systemsPersonnel of over 30 researchers with extensive experience andknowhow on cyber securityEquipped with cutting edge technologies and devicesWar Room enables Conducting of attacks aimed at seizing systems, implementationof typical hacker attack strategies and botnet attacksIdentification of cyber attacks, threats and vulnerabilitiesMonitoring effective attacks and developing tools for cybersituational awarenessIn-depth cyber analyses from network traffic log informationSecurity testing of products and servicesSW security auditing07/10/20165
07/10/20166Cyber security testing is one part of a bigger pictureKYBER-TEO (2015) Participant CasesORION,TSPABB DrivesPROSYS,N.NNESTE,TVOVALMET,NIXU
07/10/2016Cyber security test developmentwith the customerProductsDefinition oftest targetsDeploymentto aluations,pilotsCurrenttestingTest methods &tools todayObjectives7
07/10/20168OPC UA SecurityOPC UA Authentication & Security ModesAuthentication User Authentication–Anonymous–User Name & Password–User Certificate (X.509)–External Tokens (e.g. Kerberos) Application Authentication–Application Instance CertificateSecurityModes MessageSecurityModeModes to record the– NoneOPC UA message– Signsequences!– Sign & Encrypt SecurityPolicy– Basic128Rsa15– Basic256– Basic256Sha256 (new, 1.02)– New policies can be defined Client application defines the used security modeReference: Prosys OPC
07/10/20169OPC UAsecurityevaluationalreadydone byBSI!https://opcfoundation.org/security/
07/10/201610Case: VTT Cyber security testing of PROSYS OPC UA products2014ProcessTogether:Test planningCycleeach yearVTT:testingProsys:FixingFound problemswere fixed!System Under Test (SUT): Prosys OPC UA Simulation Server.Test cases: Testing was conducted through fuzzing and manual vulnerabilityscanning. The SUT had default configurations. Anonymous clientaccess to SUT was used with no encryption.Findings under (something to fix): OPC UA TCP Binary encoding. OPC UA HTTP.Notes: Session handling related issue prevented performing efficient fuzzing.Therefore fuzzing was done only with small sample sets with messagetypes.Further works: Testing potential fixes for the findings. More comprehensive fuzz test cases. Client testing. Testing OPC UA HTTP transport more through.
07/10/201611Case: VTT Cyber security testing of PROSYS OPC UA products2015ProcessTogether:Test planningCycleeach yearVTT:testingProsys:FixingFound problemswere fixed!Test target: Prosys OPC UA Simulation Server and OPC UA SDK ClientServer (Evaluation)Test tool: Codenomicon Defensics OPC UA Server Test Suite.About testing: With the OPC-UA Test suite we tested Prosys OPC-UA Binary TCPprotocol with model based methods (OPC UA modelled). Selected test cases were only run. Running of all tests cases typically takes several hours (overnight).Test target behaviour under testing: Generally, the target survived well during the fuzzing and was able tocontinue correct operation. Testing of encryption and certificate handling was also touched a bit. Some slowdown of the services was typical reaction.Other notes: Tenable Nessus -vulnerability scanner was useless here. hping3 DoS tool was also used to flood the test target with messages:Test target was able to automatically recover after the attacks. VTT developed threat modelling tool MVS was used to visualize thefound threats.
07/10/201612Case: VTT Cyber security testing of PROSYS OPC UA products2016ProcessTogether:Test planningCycleeach yearVTT:testingProsys:FixingFound problemswere fixed!Test target: Prosys OPC UA Simulation server (Linux, Windows and SDKversions).Test type: DoS-testing.Test tools: nmap: port scanning. hping3: network flood testing. A tool for interactive packet manipulation with selected OPC UAmessages. Codenomicon Defensics Traffic Capture Fuzzer: OPC UA protocolfuzzing based on recorded OPC UA packets.Test target behaviour under testing: Generally, the target survived well and was able to continue correctoperation. Log handling: Prosys had surely improved the log handling to correctlevel. High overload was found problematic to survive (Defensics). Only few test cases were found which repeatedly jammed the testtarget.
07/10/201613ULTIMATE GOAL:To integrate Automated Cyber Security Testing to ICSapplication designer’s daily tools!OPC UA has an advantage because of its built-in security!
07/10/2016Examples of expandedVTT cyber security testing14
07/10/201615Example tools used in the War RoomUsed tools are selected for each caseCommercial:- Codenomicon Defensics TCF- Nessus- Metasploit- Burp Suite ProfessionalFree / Open source:- CrypTools- IDA Free- Scapy- OWASP ZAP- Maltego- Nikto- Hydra- sslyze- Armitage- Stompy- Radamsa- Nmap- Wireshark- Jack the Ripper- Valgrind- !Exploitable- Xplico- Bro NSM- Snort
07/10/201616BATTLEFIELD- Scout/intelligence- AttackNetworkmonitoring toolsSecurity testing toolsTools for theattack- Monitor- Defence actionsNetworksIllegal admissionLog rmsNetwork rks1. Find vulnerable targets2. Select targets and goals for theattack3. Implement attacks by using readyconfigured dels/practiceRequirementsApplicable vulnerable networkand device environments are usedin the workshopsSecureplatformsSecuresettings1.2.3.4.Set loggingMonitor trafficFind attacksConsider bestdefence mechanismAuditsWork rightsChangecontrolWe also arrange ”Cyber defence” hands-on Workshops
07/10/201617THANK YOU!This was part of KYBER-TEO ”Improving cyber security for industry”(National program 2014 - 2016)Developing and testing SERVICES in the participatingcompanies to ensure the cyber security and continuity ofFinnish industrial productionWP 1: Cyber security practices and mappingsWP 2: Deploying the cyber security to industrial productionWP 3: Cyber security monitoring services for automation networksGOAL: To disseminate results and experiences between companies.Focus on co-operation Participating companies Company specific cases Project work (technology, services)Other industrial companies (e.g. through dedicated NESA HUOVI-portal project area) Wide company reviews Result dissemination seminarsState authority & Research co-operation: (Advice, quality, development, dissemination, education) National Emergency Supply Agency (Project owner) VTT (Project lead & execution) TUT - Tampere University of Technology (Project subcontractor) Finnish Communications Regulatory Authority - The National Cyber Security Centre (NCSC)
07/10/2016Contact pointPasi Ahonen, Principal Scientist, VTTProject Manager: TITAN, TEO-TT, COREQ-VE,COREQ-ACT, TEO-SUMMARY, KYBER-TEO pasi.ahonen@vtt.fi18
scanning. The SUT had default configurations. Anonymous client access to SUT was used with no encryption. Findings under (something to fix): OPC UA TCP Binary encoding. OPC UA HTTP. Notes: Session handling related issue prevented performing efficient fuzzing. Therefore fuzzing was done only with small sample sets with message types.