Transcription
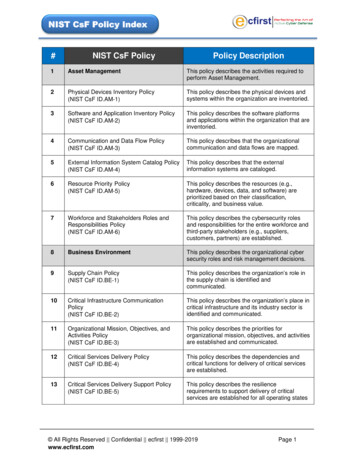
NIST CsF Policy Index#NIST CsF PolicyPolicy Description1Asset ManagementThis policy describes the activities required toperform Asset Management.2Physical Devices Inventory Policy(NIST CsF ID.AM-1)This policy describes the physical devices andsystems within the organization are inventoried.3Software and Application Inventory Policy(NIST CsF ID.AM-2)This policy describes the software platformsand applications within the organization that areinventoried.4Communication and Data Flow Policy(NIST CsF ID.AM-3)This policy describes that the organizationalcommunication and data flows are mapped.5External Information System Catalog Policy(NIST CsF ID.AM-4)This policy describes that the externalinformation systems are cataloged.6Resource Priority Policy(NIST CsF ID.AM-5)This policy describes the resources (e.g.,hardware, devices, data, and software) areprioritized based on their classification,criticality, and business value.7Workforce and Stakeholders Roles andResponsibilities Policy(NIST CsF ID.AM-6)This policy describes the cybersecurity rolesand responsibilities for the entire workforce andthird-party stakeholders (e.g., suppliers,customers, partners) are established.8Business EnvironmentThis policy describes the organizational cybersecurity roles and risk management decisions.9Supply Chain Policy(NIST CsF ID.BE-1)This policy describes the organization’s role inthe supply chain is identified andcommunicated.10Critical Infrastructure CommunicationPolicy(NIST CsF ID.BE-2)This policy describes the organization’s place incritical infrastructure and its industry sector isidentified and communicated.11Organizational Mission, Objectives, andActivities Policy(NIST CsF ID.BE-3)This policy describes the priorities fororganizational mission, objectives, and activitiesare established and communicated.12Critical Services Delivery Policy(NIST CsF ID.BE-4)This policy describes the dependencies andcritical functions for delivery of critical servicesare established.13Critical Services Delivery Support Policy(NIST CsF ID.BE-5)This policy describes the resiliencerequirements to support delivery of criticalservices are established for all operating states All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 1
NIST CsF Policy Index#NIST CsF PolicyPolicy Description(e.g. under duress/attack, during recovery,normal operations).14GovernanceThis policy describes the organizationalpolicies, processes, and procedures forinformation security and risk management.15Cybersecurity Policy(NIST CsF ID.GV-1)This policy describes the organizationalcybersecurity policy is established andcommunicated.16External Partners Cybersecurity Roles andResponsibilities Policy(NIST CsF ID.GV-2)This policy describes the cybersecurity rolesand responsibilities are coordinated and alignedwith internal roles and external partners.17Cybersecurity Legal and RegulatoryRequirements Policy(NIST CsF ID.GV-3)This policy describes the legal and regulatoryrequirements regarding cybersecurity, includingprivacy and civil liberties obligations, areunderstood and managed.18Governance and Risk Management Policy(NIST CsF ID.GV-4)This policy describes the governance and riskmanagement process.19Risk AssessmentThis policy describes the identify theorganizational asset vulnerabilities andcybersecurity risk to operations.20Asset Vulnerabilities Policy(NIST CsF ID.RA-1)This policy describes the asset vulnerabilitiesare identified and documented.21Cyber Threat Intelligence Policy(NIST CsF ID.RA-2)This policy describes the cyber threatintelligence received from information sharingforums and sources.22External and Internal Threats Policy(NIST CsF ID.RA-3)This policy describes the threats, both internaland external, are identified and documented.23Potential Business Impacts Policy (NISTCsF ID.RA-4)This policy describes the potential businessimpacts and likelihoods are identified.24Determining Risk Policy(NIST CsF ID.RA-5)This policy describes the threats, vulnerabilities,likelihoods, and impacts that are used todetermine risk.25Prioritize Risk Responses Policy(NIST CsF ID.RA-6)This policy describes the risk responses thatare identified and prioritized. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 2
NIST CsF Policy Index#NIST CsF PolicyPolicy Description26Risk Management StrategyThis policy describes the organizational risktolerance and established operational riskdecisions.27Risk Management Process Policy (NISTCsF ID.RM-1)This policy describes the risk managementprocesses that are established, managed, andagreed to by organizational stakeholders.28Determine Risk Tolerance Policy(NIST CsF ID.RM-2)This policy describes the organizational risktolerance is determined and clearly expressed.29Risk Tolerance Policy(NIST CsF ID.RM-3)This policy describes the organization’sdetermination of risk tolerance informed by itsrole in critical infrastructure and sector specificrisk analysis.30Supply Chain Risk ManagementThis policy describes the identify the process forsupply chain risk management and toimplement contract with suppliers and thirdparty partners.31Supply Chain Risk Management ProcessesPolicy(NIST CsF ID.SC-1)This policy describes the cyber supply chainrisk management processes identified,established, assessed, managed, and agreed toby organizational stakeholders.32Third Party Services Policy(NIST CsF ID.SC-2)This policy describes the suppliers and thirdparty partners of information systems,components, and services are identified,prioritized, and assessed using a cyber supplychain risk assessment process.33Cyber Supply Chain Risk ManagementPlan Policy(NIST CsF ID.SC-3)This policy describes the contracts withsuppliers and third-party partners are used toimplement appropriate measures designed tomeet the objectives of an organization’scybersecurity program and Cyber Supply ChainRisk Management Plan.34Audit Third Party Partners Policy(NIST CsF ID.SC-4)This policy describes the suppliers and thirdparty partners routinely assessed using audits,test results, or other forms of evaluations toconfirm they are meeting their contractualobligations.35Response and Recovery Plan TestingPolicy(NIST CsF ID.SC-5)This policy describes the response andrecovery planning and testing are conductedwith suppliers and third-party providers. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 3
NIST CsF Policy Index#NIST CsF PolicyPolicy Description36Identity Management, Authenticationand Access ControlThis policy describes the management forlimited access to facilities and organizationassets.37Identity Management Policy(NIST CsF PR.AC-1)This policy describes the identities andcredentials issued, managed, verified, revoked,and audited for authorized devices, users andprocesses.38Access Management for Assets Policy(NIST CsF PR.AC-2)This policy describes the physical access toassets are managed and protected.39Remote Access Management Policy(NIST CsF PR.AC-3)This policy describes the remote accessmanaged.40Access Authorization Policy(NIST CsF PR.AC-4)This policy describes the access permissionsand authorizations that are managed,incorporating the principles of least privilegeand separation of duties.41Network Integrity Policy(NIST CsF PR.AC-5)This policy describes the network integrity isprotected (e.g., network segregation, networksegmentation).42Proofed Identities Policy(NIST CsF PR.AC-6)This policy describes the identities that areproofed and bound to credentials and assertedin interactions.43Authentication Policy(NIST CsF PR.AC-7)This policy describes the users, devices, andother assets are authenticated (e.g., singlefactor, multi-factor) commensurate with the riskof the transaction (e.g., individuals’ security andprivacy risks and other organizational risks).44Awareness and TrainingThis policy describes the cyber securityawareness and training to organizationalpersonnel covering their jobs andresponsibilities.45User Training Policy(NIST CsF PR.AT-1)This policy describes that all users are informedand trained.46Privileged Users Policy(NIST CsF PR.AT-2)This policy describes the privileged usersunderstand their roles and responsibilities.47Third Party Stakeholders Policy(NIST CsF PR.AT-3)This policy describes the third-partystakeholders (e.g., suppliers, customers,partners) understand their roles andresponsibilities. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 4
NIST CsF Policy Index#NIST CsF PolicyPolicy Description48Senior Executives Responsibilities Policy(NIST CsF PR.AT-4)This policy describes the senior executivesunderstand their roles and responsibilities.49Cybersecurity Personnel’s ResponsibilitiesPolicy(NIST CsF PR.AT-5)This policy describes the physical andcybersecurity personnel understand their rolesand responsibilities.50Data SecurityThis policy describes the risk strategy to ensurethe confidentiality, integrity, and availability(CIA) of information assets.51Data at Rest Policy(NIST CsF PR.DS-1)This policy describes that data-at-rest isprotected.52Data in Transit Policy(NIST CsF PR.DS-2)This policy describes that data-in-transit isprotected.53Asset Management and Disposition Policy(NIST CsF PR.DS-3)This policy describes that assets are formallymanaged throughout removal, transfers, anddisposition.54Availability Policy(NIST CsF PR.DS-4)This policy describes the adequate capacity toensure availability is maintained.55Data Leaks Protection Policy(NIST CsF PR.DS-5)This policy describes the protections againstdata leaks are implemented.56Integrity Checking Mechanisms Policy(NIST CsF PR.DS-6)This policy describes the integrity checkingmechanisms used to verify software, firmware,and information integrity.57Segregation in Development and TestingEnvironment(s) Policy(NIST CsF PR.DS-7)This policy describes the development andtesting environment(s) separate from theproduction environment.58Hardware Integrity Policy(NIST CsF PR.DS-8)This policy describes the integrity checkingmechanism used to verify hardware integrity.59Information Protection Processes andProceduresThis policy describes that maintain policies,processes, and procedures to manageprotection of information systems and assets.60Baseline Configuration Policy(NIST CsF PR.IP-1)This policy describes the baseline configurationof information technology/industrial controlsystems is created and maintainedincorporating security principles (e.g. concept ofleast functionality). All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 5
NIST CsF Policy Index#NIST CsF PolicyPolicy Description61System Development Life Cycle Policy(NIST CsF PR.IP-2)This policy describes the System DevelopmentLife Cycle to manage systems is implemented.62Configuration Change Control Policy(NIST CsF PR.IP-3)This policy describes the configuration changecontrol processes in place.63Backup Management Policy(NIST CsF PR.IP-4)This policy describes that backups ofinformation are conducted, maintained, andtested.64Physical Operating Environment Policy(NIST CsF PR.IP-5)This policy describes the policy and regulationsregarding the physical operating environmentfor organizational assets are met.65Disposal Policy(NIST CsF PR.IP-6)This policy describes that the data is destroyedaccording to policy.66Protection Improvement Policy(NIST CsF PR.IP-7)This policy describes that the protectionprocesses are improved.67Protection Technologies Policy(NIST CsF PR.IP-8)This policy describes that the effectiveness ofprotection technologies is shared.68Response Plans Availability Policy(NIST CsF PR.IP-9)This policy describes that the response plans(Incident Response and Business Continuity)and recovery plans (Incident Recovery andDisaster Recovery) are in place and managed.69Testing of Response and Recovery PlansPolicy(NIST CsF PR.IP-10)This policy describes that the response andrecovery plans are tested.70Cybersecurity and Human ResourcesPolicy(NIST CsF PR.IP-11)This policy describes the cybersecurity isincluded in human resources practices (e.g.,deprovisioning, personnel screening).71Vulnerability Management Policy(NIST CsF PR.IP-12)This policy describes the vulnerabilitymanagement plan developed and implemented.72MaintenanceThis policy describes to maintain policies andprocedures for the maintenance and repairs oforganizational assets.73Asset Maintenance and Repair Policy(NIST CsF PR.MA-1)This policy describes the maintenance andrepair of organizational assets are performedand logged, with approved and controlled tools.74Remote Maintenance Policy(NIST CsF PR.MA-2)This policy describes the remote maintenanceof organizational assets is approved, logged, All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 6
NIST CsF Policy Index#NIST CsF PolicyPolicy Descriptionand performed in a manner that preventsunauthorized access.75Protective TechnologyThis policy describes the technical securitysolutions to ensure the security and protectionof systems and organizational assets.76Audit Records Management Policy (NISTCsF PR.PT-1)This policy describes the audit/log records aredetermined, documented, implemented, andreviewed in accordance with policy.77Removable Media Protection Policy (NISTCsF PR.PT-2)This policy describes that the removable mediais protected and its use restricted according topolicy.78Configuring Essential Capabilities Policy(NIST CsF PR.PT-3)This policy describes the principle of leastfunctionality is incorporated by configuringsystems to provide only essential capabilities.79Network Protection Policy(NIST CsF PR.PT-4)This policy describes the communications andcontrol networks are protected.80Mechanism to Achieve ResilienceRequirements Policy(NIST CsF PR.PT-5)This policy describes the mechanisms (e.g.,failsafe, load balancing, hot swap) implementedto achieve resilience requirements in normaland adverse situations.81Anomalies and EventsThis policy describes the detection ofanomalous activities and events in a timelymanner.82Network Operations Baseline Policy(NIST CsF DE.AE-1)This policy describes the baseline of networkoperations and expected data flows for usersand systems established and managed.83Event Detection and Analysis Policy(NIST CsF DE.AE-2)This policy describes that the detected eventsare analyzed to understand the attack targetsand methods.84Event Data Collection Policy(NIST CsF DE.AE-3)This policy describes the event data collectedand correlated from multiple sources andsensors.85Event’s Impact Policy(NIST CsF DE.AE-4)This policy describes that the impact of eventsis determined.86Incident Notification Policy(NIST CsF DE.AE-5)This policy describes the incident alertthresholds established. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 7
NIST CsF Policy Index#NIST CsF PolicyPolicy Description87Security Continuous MonitoringThis policy describes the monitoring of thephysical environment and information systemand assets at discrete intervals to identifycybersecurity events.88Network Monitoring Policy(NIST CsF DE.CM-1)This policy describes the network monitored todetect potential cybersecurity events.89Physical Environment Monitoring Policy(NIST CsF DE.CM-2)This policy describes the physical environmentis monitored to detect potential cybersecurityevents.90Personnel Activity Monitoring Policy (NISTCsF DE.CM-3)This policy describes the personnel activity ismonitored to detect potential cybersecurityevents.91Malicious Code Detection Policy(NIST CsF DE.CM-4)This policy describes the malicious code isdetected.92Unauthorized Mobile Code DetectionPolicy(NIST CsF DE.CM-5)This policy describes the unauthorized mobilecode is detected.93External Service Provider ActivityMonitoring Policy(NIST CsF DE.CM-6)This policy describes that the external serviceprovider activity is monitored to detect potentialcybersecurity events.94Software and Device Monitoring Policy(NIST CsF DE.CM-7)This policy describes the monitoring forunauthorized personnel, connections, devices,and software performed.95Vulnerability Scans Policy(NIST CsF DE.CM-8)This policy describes the vulnerability scansthat are performed.96Detection ProcessesThis policy describes the awareness onanomalous events and test detection activities.97Event Detection Roles and ResponsibilitiesPolicy(NIST CsF DE.DP-1)This policy describes the roles andresponsibilities for detection that are welldefined to ensure accountability.98Detection Activities Policy(NIST CsF DE.DP-2)This policy describes the detection activitiescomply with all applicable requirements.99Detection Process Test Policy(NIST CsF DE.DP-3)This policy describes the detection processesare tested.100Event Communication Policy(NIST CsF DE.DP-4)This policy describes the event detectioninformation is communicated. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 8
NIST CsF Policy Index#NIST CsF PolicyPolicy Description101Detection Process Improvement Policy(NIST CsF DE.DP-5)This policy describes the detection processesare continuously improved.102Response PlanningThis policy describes the maintain a responseplan to ensure timely response to detectedcybersecurity events.103Execute Response Plan Policy(NIST CsF RS.RP-1)This policy describes the response plan isexecuted during or after an incident.104Communications (Respond)This policy describes the coordinate responseactivities with stakeholders consistently toachieve broader cybersecurity situationalawareness.105Response Roles and ResponsibilitiesPolicy(NIST CsF RS.CO-1)This policy describes the personnel know theirroles and order of operations when a responseneeded.106Reporting Incident Policy(NIST CsF RS.CO-2)This policy describes the incidents are reportedconsistent with established criteria.107Response Plan Policy(NIST CsF RS.CO-3)This policy describes that the information isshared consistent with response plans.108Response Plan Policy(NIST CsF RS.CO-4)This policy describes the coordination withstakeholders occurs consistent with responseplans.109Cybersecurity Awareness for StakeholdersPolicy(NIST CsF RS.CO-5)This policy describes the voluntary informationsharing occurs with external stakeholders toachieve broader cybersecurity situationalawareness.110AnalysisThis policy describes the conduct analysis tounderstand response and recovery activities.111Notification Investigation Policy(NIST CsF RS.AN-1)This policy describes the notifications fromdetection systems are investigated.112Understanding incident Impact Policy(NIST CsF RS.AN-2)This policy describes that the impact of theincident is understood.113Incident Forensics Policy(NIST CsF RS.AN-3)This policy describes the forensics areperformed.114Incidents Categorization Policy(NIST CsF RS.AN-4)This policy describes the incidents arecategorized consistent with response plans. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 9
NIST CsF Policy Index#NIST CsF PolicyPolicy Description115Internal and External Vulnerability Policy(NIST CsF RS.AN-5)This policy describes the processes areestablished to receive, analyze and respond tovulnerabilities disclosed to the organization frominternal and external sources (e.g. internaltesting, security bulletins, or securityresearchers).116MitigationThis policy describes the perform activities tomitigate incident and newly identifiedvulnerabilities.117Contained Incidents Policy(NIST CsF RS.MI-1)This policy describes that the incidents arecontained.118Mitigate Incidents Policy(NIST CsF RS.MI-2)This policy describes the incidents aremitigated.119Vulnerabilities Documentation Policy (NISTCsF RS.MI-3)This policy describes the newly identifiedvulnerabilities are mitigated or documented asaccepted risks.120Improvements (Respond)This policy describes the improve the responseplan by incorporating lessons learned from allresponse activities.121Response Plan Lesson Learned Policy(NIST CsF RS.IM-1)This policy describes the response plansincorporate lessons learned.122Response Strategies Policy(NIST CsF RS.IM-2)This policy describes the response strategiesare updated.123Recovery PlanningThis policy describes the timely restoration ofsystems or assets affected by cybersecurityevents.124Execute Recovery Plan Policy(NIST CsF RC.RP-1)This policy describes that recovery plan isexecuted during or after a cybersecurityincident.125Improvements (Recover)This policy describes the improve recoveryplanning and processes by incorporatinglessons learned.126Recovery Plan Lesson Learned Policy(NIST CsF RC.IM-1)This policy describes the recovery plansincorporate lessons learned.127Recovery Strategies Policy(NIST CsF RC.IM-2)This policy describes the recovery strategiesare updated. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 10
NIST CsF Policy Index#NIST CsF PolicyPolicy Description128Communications (Recover)This policy describes the communicate recoveryactivities to internal stakeholders and repair thereputation after an event.129Public Relations Policy(NIST CsF RC.CO-1)This policy describes that the public relationsare managed.130Repair Policy(NIST CsF RC.CO-2)This policy describes that the reputation isrepaired after an incident.131Recovery Activities Communication Policy(NIST CsF RC.CO-3)This policy describes the recovery activities arecommunicated to internal and externalstakeholders as well as executive andmanagement teams. All Rights Reserved Confidential ecfirst 1999-2019www.ecfirst.comPage 11
71 Vulnerability Management Policy (NIST CsF PR.IP-12) This policy describes the vulnerability management plan developed and implemented. 72 Maintenance This policy describes to maintain policies and procedures for the maintenance and repairs of organizational assets. 73 Asset Maintenance and Repair Policy (NIST CsF PR.MA-1)