Transcription
SREDKey: Bringing Security toCard Not Present Transactions80137507-001Rev. B3/2/2018http://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USAVoice: (714) 761-6368 Fax: (714) 761-8880
2 2018 ID TECH. All rights reserved. 2018 International Technologies & Systems Corporation.The information contained herein is provided to the user as a convenience. While every effort has been madeto ensure accuracy, ID TECH is not responsible for damages that might occur because of unintentionalerrors or omissions. The information described herein was current at the time of publication, but is subject tochange at any time without prior notice.http://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
3Executive SummaryCard Not Present transactions pose special challenges that are not easily met by traditional creditcard readers and PIN pads. PCI-compliant handling of these transactions essentially requires theuse of a dedicated device that can encrypt keyed-in data in real time. But most credit cardreaders (even those that have a keypad) are not capable of complying with Card Not Presentrequirements. The SREDKey keypad by ID TECH is a PCI-PTS certified Secure Reading andExchange of Data (SRED) device that allows businesses to participate in phone and mail ordertransactions, and other Card Not Present situations; yet the device also has a physical magstripeslot, which can optionally be used for pickup-in-store, hotel check-in, and other scenarios inwhich the original order needs to be phoned in (for pre-authorization) but final settlementinvolves a physical card.Card Not Present: A Special ChallengeIn the majority of retail businesses, credit card transactions involve a customer presenting aphysical card, in person. But this is not the norm for all business types. In Mail-Order/TelephoneOrder (MOTO) businesses, and call-ahead businesses (where services or merchandise must bereserved in advance with a credit card number) – including car rental, hotel reservations, airlineticketing, mail-in bill payment, and other common scenarios – a physical credit card might neverbe presented, in person, by the customer.Card Not Present scenarios present a special challenge, in that Payment Card Industry (PCI) rulesforbid businesses from storing or transmitting credit card data. Under PCI rules, neither thePrimary Account Number (PAN) nor any accompanying sensitive data (such as the three-digit CVVcode on the back of the card) can be stored or transmitted in the clear. PCI rules, in fact, requirethat merchants render PANs and other sensitive data unreadable and unrecoverable through oneof the following methods: One-way hashes based on strong cryptography (hash must be of the entire PAN) Truncation (hashing cannot be used to replace the truncated segment of PAN) Index tokens and pads (pads must be securely stored) Strong cryptography with associated key-management processes and procedureshttp://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
4Even the mere act of manually typing a card number into an onscreen form (using an ordinary PCand keyboard, or a purpose-built POS system running on Android or Windows) places themerchant in "PCI scope," because manual key entry using a conventional keyboard can exposecardholder data to surreptitious logging or monitoring by malware. (For PCI purposes, a regularPC constitutes an untrusted execution environment.) Even if data entered into a computer is notsaved to disk, it may be cached in data buffers and/or logs (creating a vulnerability).To reduce security vulnerabilities (and stay within PCI rules regarding the handling of sensitivecardholder data), card data needs to be encrypted at the point of entry—and remain encryptedthroughout the transaction process, until it reaches an appropriate party (such as a remotegateway, or online payment processor that normally processes the merchant's transactions) whocan decrypt the data in a properly controlled setting, at the time of need. In this type of setup,the merchant is part of an "end-to-end encryption" scenario, where the data never exists in cleartext form (except upon reaching a trusted recipient).To achieve end-to-end encryption with a keypad-based manual entry device, the data must beencrypted as it is entered, at a hardware level. Since ordinary PCs and tablets aren't set up to dothis, it essentially means a purpose-built device is required. The SREDKey keypad by ID TECH issuch a device.Secure Reading and Exchange of DataID TECH's SREDKey is unique among handheld key-entry payment devices in that it meets PCI'sexacting standards for SRED (Secure Reading and Exchange of Data) products. No other device inthis class meets these standards.PCI's requirements around SRED go well beyond mere encryption of data at the time of entry.The requirements govern secure manufacture (including the provisioning of data encryption keys,by a certified Key Injection Facility, before the device enters service), self-check logic that mustexecute periodically (i.e., daily) when the device is in service, authentication-based upgrading offirmware, and documented procedures for secure decommissioning of devices when they'vereached end-of-life. In addition, SRED devices include anti-tamper features, so that if, forexample, a stolen device is ever disassembled (in an attempt to gain access to electroniccomponents), the device will automatically "zero out" its encryption keys and enter a state inwhich it is permanently disabled.All of this is in addition to normal DUKPT (derived unique key per transaction) security measures,whereby transaction data is never encrypted with the same key more than once. (A new key isderived, and used once, for each transaction; then the key is discarded.) Moreover, althoughhttp://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
5SREDKey supports industry-standard Triple DES encryption and also AES encryption, it containsno decryption logic whatsoever. Thus, it is impossible to make the device decrypt sensitivecardholder data once it has been encrypted.P2PECompanies that require the ultimate protection against data breaches inevitably end up lookingat a full PCI-validated P2PE (Point-to-Point Encryption) solution. But the cost of independentlycertifying such a solution is prohibitive for many (indeed, most) businesses. That's wherePhiladelphia-based FreedomPay comes into play. As a provider of PCI-validated P2PE paymentsolutions, FreedomPay provides a best-in-class P2PE solution for companies that might nototherwise be able to justify the expense of a one-off PCI Validated system. Merchants who utilizethe FreedomPay Commerce Platform can choose from a variety of pre-approved card readers,then leverage FreedomPay's PaaS (Platform as a Service), FreeWay, to route paymentselectronically to their back end of choice, without worrying about "on premise" storage ofcardholder data, or interception of cardholder data "in flight" (since all data is encrypted)."All of FreedomPay's solutions are PCI-validated P2PE," explains company president ChrisKronenthal, "and ID TECH's SREDKey is our go-to device when it comes to any scenario involvingback-office order-intake or Card Not Present transactions, which are still quite common in ticketsales, college admissions, health care, lodging, rentals, and storage—not to mention businessesthat might have a limited retail presence backed by a much larger online experience." In many ofthese sorts of enterprises, customers might call ahead to reserve an item, then pay in personwith a credit card, "which is where SREDKey really shines," says Kronenthal, "because you canuse the device's manual key-entry mode to get pre-authorization, then run a card physically,using SREDKey's MSR slot, when the customer arrives in person to pay."SREDKey Data Entry ModesID TECH's SREDKey supports six standard data-entry modes, including: Card Number, plus Expiration DateCard Number, Expiration Date, and ZIP CodeCard Number, Expiration Date, and Security Code (CVV)Card Number, Expiration Date, Street Number of Address, ZIP CodeCard Number, Expiration Date, Security Code, ZIP CodeCard Number, Expiration Date, Security Code, Street Number, ZIP Codehttp://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
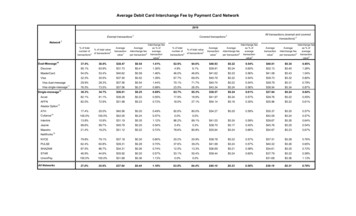
6SREDKey data captured by a call center (top diagram) can be sent to FreedomPay's cloud-based processingplatform, then forwarded to the merchant's bank for clearing. From the moment of capture, sensitivecardholder data is encrypted. When used in a Virtual Terminal environment (lower diagram), SREDKey can keepthe merchant out of PCI scope, since keystrokes are not captured in the clear but are encrypted at the momentof key entry, before reaching the merchant's computer. (Source: FreedomPay)http://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
7The most common use case for merchants who process on FreedomPay’s Commerce Platform iswithin the lodging industry. Since FreedomPay can offer P2PE with over 200 POS/PMSintegrations, solving for the entire payments ecosystem of a hotel/resort, there are thousands ofSREDKey devices deployed in Las Vegas and across the US to solve for over-the-phone credit cardpayments. Hotels and casinos utilize PMS (property management systems) that record andmanage both Card Present and Card Not Present transactions; by utilizing the P2PEFreedomPay/SREDKey integration, merchants can securely book reservations over the phone tobe settled at the front desk upon checkout.Higher education is another Card Not Present "industry" served by FreedomPay in whichSREDKey plays a critical role. "At this point, we serve over fifty percent of the Division Oneschools," FreedomPay's Chris Kronenthal notes. "It's incredible how many Ivy League tuitionoffices we're in, not to mention alumni offices that rely on being able to capture orders over thephone as well as in person."Some retail businesses want to add phone-in/in-store-pickup capability, but quickly learn thatMOTO (mail-order/telephone-order) is not as easy as simply hooking a PIN-pad up to a PC. "If youtry to bring a non-validated device into your system," FreedomPay's Chris Kronenthal points out,"you can find yourself facing a full PCI-DSS 3.2 Level 1 security audit, if the device you're addingisn't [PCI] Validated. Whereas if you're bringing in SREDKey, you can remain out of scope for PCI,which will greatly simplify any audit." (Note: Regular yearly on-site security audits are required byPCI and card brands, for Level 1 businesses; and fresh audits must be conducted whenever thesystem changes.)The Ultimate High-Security Industry: Health CareFew industries are subject to as many security restrictions and statutory requirements as HealthCare. In the U.S., HIPAA laws specify stringent requirements for the protection of patient data (instorage, as well as in transit), and most health care enterprises qualify as Level 1 businesses forPCI security, which means yearly on-site audits as well as quarterly audits of computer networksand data transmission systems.Southern California based TrustCommerce—a payment solutions provider well known for itsemphasis on security—serves customers in diverse industries, including non-profit, municipality,insurance, transportation, education, and retail. It's also among the most experienced of allgateways when it comes to the health care industry. In health care, TrustCommerce solutionsintegrate with Interactive Voice Response (IVR) systems, online payments, front and back office,mobile payments, kiosks, e-statements/billing services, and patient portals.http://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
8For Card Not Present scenarios, TrustCommerce offers ID TECH's SREDKey , because, accordingto Preisdent of Technical Operations Chris Gowins: "It's durable, it's easy to use, it's secure—it'sthe best device of its kind out there."For large call centers like mail service pharmacies or customers adding MOTO (MailOrder/Telephone Order) to an existing, conventional "Card Present" solution, SREDKey isrelatively easy to integrate—not just at system design time, but at audit time. According toGowins, Qualified Security Assessors "are definitely more comfortable when they see, during anaudit, that a new addition to the system is a PCI-validated SRED device." Devices that are not PCIlisted as SRED-qualified are potentially subject to detailed physical examination to determineintrusion resistance and security characteristics. "With SREDKey, there's no question as to itssecurity," Gowins points out. "It's already validated. It's PCI-listed."But What About EMV?Most card readers (including most of those manufactured by ID TECH) incorporate a chip-cardbezel, for EMV transactions. ID TECH's SREDKey , on the other hand, has a magstripe slot—butno EMV slot. "The point of the chip on a chip card is to prove that the card was physicallypresent," explains ID TECH Product Manager Vince Steffano. "With Card Not Presenttransactions, it's a given that no card is present, hence the EMV slot is superfluous. To keep costsdown, we eliminate it. But there are still situations where a transaction that was pre-authorizedas Card Not Present goes to settlement with a card present, and for that we offer the MSRcapability."Lack of EMV capability normally means the merchant is liable for chargebacks in the event offraud. But as TrustCommerce's Chris Gowins points out: "That turns out to be a non-issue formany of our healthcare customers. I mean, if someone has a surgical procedure at a hospital andthey want to put the co-pay on their credit card, it's not likely they're using a stolen card."FreedomPay's Chris Kronenthal echoes that sentiment. "In higher education, and many otherplaces where we see SREDKey used, there's just not a fraud problem, because cardholders tendto provide lots of identifying information up front.""EMV is about validating the card," says TrustCommerce's Chris Gowins, "whereas encryptionprotects cardholder information so that it is not sent in the clear exposing the cardholder toidentity theft and fraudulent transactions. SREDKey encrypts transaction data from the point ofentry, securing and safeguarding customer data—for both cardholders and merchants."http://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
9Ergonomic DesignErgonomic design is an important factor in SREDKey's success, especially in high-volume call centers. Toensure that users are able to enter keystroke data quickly yet positively, SREDKey is precisely weightedand sits on non-skid rubber feet to maximize stability and eliminate slippage. Also, unlike conventionalcredit-card PIN pads (which are telephone-like in key layout), the numeric keys on SREDKey arearranged "calculator style," with 7, 8, and 9 on the top row of keys—a layout that's familiar tobookkeepers, spreadsheet users, and data-entry professionals. As a safeguard against accidental misentry of credit card data, the device automatically runs a Luhn checksum on PAN (primary accountnumber) data and will flag as incorrect any credit card number that has been entered with (for example)two digits flipped, or a digit missing.ConclusionID TECH's SREDKey allows merchants to conduct Card Not Present transactions with totalsecurity, in compliance with all applicable PCI requirements. As a PCI-validated SRED (SecureReading and Exchange of Data) device, SREDKey meets the industry's highest standards forencryption-enabled payment devices, and incorporates anti-tamper features not found in lesserdevices. SREDKey's ergonomic design, ruggedness, compact form factor, and driverless USBcompatibility (with power supplied solely by the USB connection), combined with the unit's lowTotal Cost of Ownership and ease of use, make SREDKey a unique solution for merchants intelemarketing, health care, higher education, hospitality, and other industries where Card NotPresent transactions are often the norm rather than the exception.For More InformationFor more information on SREDKey , be sure to visit http://idtechproducts.com.For a full list of P2PE validated solution providers certified with ID TECH’s SREDKey , see the PCI's listingof Validated P2PE solutions at:https://www.pcisecuritystandards.org/assessors and solutions/point to point encryption solutions.Written by Kas Thomashttp://www.idtechproducts.com10721 Walker Street, Cypress, CA 90630, USA Voice: (714) 761-6368 Fax: (714) 761-8880 2018 ID TECH. All rights reserved.
gateway, or online payment processor that normally processes the merchant's transactions) who can decrypt the data in a properly controlled setting, at the time of need. In this type of setup, . FreedomPay/SREDKey integration, merchants can securely book reservations over the phone to