Transcription
SOLUTION OVERVIEWSingle-pane-of-glass cloud consoleproviding centralized visibility, managementand insight across all OSes
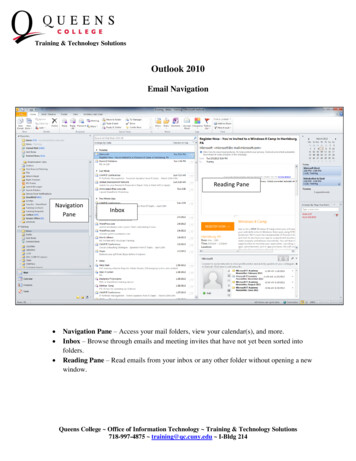
What is anendpointsecuritymanagementconsole?ESET PROTECT is a cloud console, offeredas a service, that ensures real-timevisibility for on-premise and off-premiseendpoints as well as full reporting andsecurity management for all OSes.It is a single pane of glass over all ESET securitysolutions deployed in the network. It controlsendpoint prevention, detection & responselayers across all platforms—covering desktops,servers, virtual machines and even managedmobile devices.
Why ORTINGZero-days, advanced persistentthreats, targeted attacks andbotnets are all concerns forindustries across the world. Havingvisibility into these threats inreal-time is extremely importantto allow the IT staff to respondpromptly and mitigate any riskthat may have developed. Due to acontinued emphasis on companiesto add a mobile workforce,visibility is not just needed onpremise but off-premise as well.Today’s cybersecurity landscapeis constantly evolving with newattack methods and never-beforeseen threats. When an attack ordata breach occurs, organizationsare typically surprised that theirdefenses were compromised orare completely unaware that theattack even happened. After theattack is discovered, organizationsmay then want to execute specifictasks across devices, such asscans. This may lead organizationsto completely change theirconfiguration policies to betterprotect against a future attack.On top of having to meet datacompliance regulations, mostorganizations have their internalrequirements related to reporting.No matter the organization, therewill be reports that need to begenerated at scheduled intervalsand provided to relevant parties orstored for future use.ESET PROTECT provides up-to-dateinformation to inform IT staff aboutthe status of all endpoints whetherthey are on-premise or off-premise.It also provides visibility into allOSes that a company might have,not just a limited few. In mostinstances, visibility is also enhancedto show device-level informationsuch as hardware or softwareinventories to ensure completesituational awareness.ESET PROTECT comes withpowerful and smart predefinedpolicies but allows organizationsto fine-tune the policies orconfigurations of endpoint securityproducts at any time. In addition,tasks can be automated to saveIT admins the time from manuallyhaving to execute them on eachindividual computer.ESET PROTECT can generatereports at scheduled intervals andsaved to specific folders or emaileddirectly to someone who requestedit. There are dozens of usefulreport templates, and these canbe used right away or customizedto provide the requestor withwhat they need. This process isparamount to saving IT adminstime in the busy work associatedwith on-going reporting.“The major advantage of ESET is that you have allusers on one console and can manage and properlyreview their security status.”— Jos Savelkoul, Team Leader ICT-Department;Zuyderland Hospital, Netherlands, 10,000 seatsHaving visibility intoNo matter thethese threats inorganization, therereal‑time is extremelywill be reports thatimportant to allowneed to be generatedIT staff to respondat scheduled intervalspromptly andand provided tomitigate any risk thatrelevant parties ormay have developed.stored for future use.
The ESETdifferencePREVENTION TORESPONSEDYNAMIC ANDCUSTOM REPORTINGWithin a single console,ESET PROTECT combines themanagement of multiple ESET’ssecurity solutions. From threatprevention to detection andresponse, they cover your entireorganization in a multilayeredfashion for the best levelof protection.ESET PROTECT provides over170 built-in reports and allows youto create custom reports fromover 1000 data points. This allowsorganizations to create reportsto look and feel exactly as theymight want. Once created, reportscan be set up to be generated andemailed at scheduled ONFRAMEWORKFrom the main dashboard,an IT admin can quickly assessthe situation and respond toissues. Actions such as create anexclusion, submit files for furtheranalysis or initiate a scan areavailable within a single click.Exclusions can be made by threatname, URL, hash or combination.ADVANCED RBACStarting with MFA-protectedaccess, the console is equippedwith an advanced Role-BasedAccess Control (RBAC) system.Assign admins and console usersto specific network branches,groups of objects, and specifypermission sets with a high degreeof granularity.FULLY CUSTOMIZABLENOTIFICATION SYSTEMThe notification system featuresa full “what you see is what youget” editor, where you will be ableto fully configure notificationsto be alerted on the exactinformation you want to benotified about.Dynamic groups can sortcomputers based on currentdevice status or defined inclusioncriteria. Tasks can then beset up to trigger actions suchas scans, policy changes orsoftware installs /uninstallsbased off dynamic groupmembership changes.FULLY AUTOMATEDVDI SUPPORTA comprehensive hardwaredetection algorithm is used todetermine the identity of themachine based on its hardware.This allows automated re-imagingand cloning of non-persistenthardware environments.Therefore, ESET’s VDI supportrequires no manual interactionand is fully automated.PROVEN AND TRUSTEDESET has been in the securityindustry for over 30 years, and wecontinue to evolve our technologyto stay one step ahead of thenewest threats. This has led usto be trusted by over 110 millionusers worldwide. Our technology isconstantly scrutinized and validatedby third-party testers who showhow effective our approach is atstopping the latest threats.MSP READYIf you’re a Managed ServiceProvider (MSP) taking care ofyour clients’ networks, you’llappreciate the full multi-tenancycapabilities of ESET PROTECT.MSP licenses are automaticallydetected and synced with thelicensing server, and the consolelets you do advanced actions suchas install/remove any 3rd partyapplication, run scripts, remotecommands, list running processes,HW configurations, etc.* Please note that the support of ESETPROTECT and ESET PROTECT Cloudfor MSPs will become available inJanuary 2021“Outstanding company, superb technical support,provides strong threat protection and centralmanagement.”— Dave, Manager of IT, Deer Valley Unified School District, USA,15,500 seats
Not on a cloudconsole? This willhelp you decide.SAVE ON LOWER TOTAL COST OFOWNERSHIP (TCO)When deciding whether to move from on-prem securityconsole, cloud may seem expensive first. But thinkagain—you’ll no longer need to maintain a server, andspend time with regular upgrades, patches, or restarts.Let alone server licenses and backups; which makescloud console a better deal within a short time span.GET STARTED WITHIN MINUTESWith a cloud console, time to protection is significantlyshorter. No longer burning resources waiting forcomponents to install, or even scheduling theinstallation on a server in the first place. Just open youraccount with ESET, and add all the endpoints to beprotected—it is as simple as that.YOU’RE ALWAYS ON THE LATESTVERSIONLeave the updating of the console up to us. We’ll do itin the background, and you’ll always be on the latestversion with the latest components. That way yourorganization will benefit from the latest features, andthe admins can enjoy the most recent user experienceimprovements straight from our roadmap.CONNECT ANYTIME, ANYWHEREAll you need is your favorite web browser. Indeed, moston-prem consoles can be accessed that way already. Butwith the cloud, no firewall exclusions or complicated VPNsetups are required anymore. You can also rely on therobust cloud infrastructure for maximum possible uptime.RESOLVE ISSUES FASTEROn the cloud console, ESET experts will be able toprovide more effective support or troubleshooting ifnecessary—which is given by the simple fact that therewill be no time wasted finding out what version you’recurrently on, because you’re always on the latest one.
Use casesRansomwareCode developersA user opens a malicious email containing a new formof ransomware.Programmers who work with code on their workcomputers might tend to create false positives due tocompiling software.Non-persistent hardware environments typicallyrequire manual interaction from an IT department andcreate reporting and visibility nightmares.SOLUTIONSOLUTION IT department receives a notification via email and After deploying a master image to computersSOLUTION IT department receives a notification via email andtheir SIEM that a new threat was detected on acertain computer. A scan is initiated with a single click on theinfected computer. The file is submitted to ESET Dynamic ThreatDefense with another click. After confirming the threat has been contained,warnings in the ESET PROTECT console arecleared automatically.its SIEM that a new threat was found. The notification shows the threat came froma developer’s computer. With one click, the file is submitted to ESET DynamicThreat Defense to confirm the file is not malicious. IT department, with one click, puts an exclusion inplace to prevent future false positives from beingdisplayed on this folder.VDI deployments Hardwareand softwareinventoryalready present in ESET PROTECT, computers willcontinue reporting to the previous instance despitea complete re-image of the system. Machines returning to their initial state at the end ofa work shift will not cause duplicate machines andinstead will be matched into one record. On deployment of non-persistent images, youcan create an image that includes the agent, sowhenever a new machine is created with anotherhardware fingerprint, it automatically creates newrecords in ESET PROTECT.Organizations need to know what software is installedon each computer, as well as how old each computer is.SOLUTION View every installed piece of software, includingversion number, in the computer record. View every computer’s hardware details, suchas device, manufacturer, model, serial number,processor, RAM, HD space and more. Run reports to view a more holistic view of anorganization in order to make budgetary decisionson hardware upgrades in future years based oncurrent makes and models.Software remediationOrganizations need to know when unapprovedsoftware has been installed, and to remediate thesoftware afterwards.SOLUTION Set up a dynamic group within ESET PROTECT toESET PROTECT dashboard—incidents overviewlook for a specific unwanted piece of software. Create a notification to alert the IT departmentwhen a computer meets this criterion. Set up a software uninstall task in the ESETPROTECT console to execute automatically whena computer meets the dynamic group criteria. Set up a user notification that automatically pops upon the user’s screen, indicating that they committeda software installation violation by installing thesoftware in question.
Multi-tenancyESET PROTECTcan be installed onWindows, Linuxor deployed asa Virtual Appliance.support and 2FAsecured logins allowfull streamliningof responsibilitiesacross largeenterprise teams.“Centrally managed security on all endpoints, serversand mobile devices was a key benefit for us.”— IT Manager, Diamantis Masoutis S.A., Greece,6,000 seatsTechnicalfeaturesSINGLE PANE OF GLASSCOMPLETELY MULTITENANTAll ESET endpoint products can be managed from a singleESET PROTECT console. This includes workstations,mobiles, servers, and virtual machines and the followingOSes: Windows, macOS, Linux, and Android.Multiple users and permission groups can be created toallow access to a limited portion of the ESET PROTECTconsole. This allows full streamlining of responsibilitiesacross large enterprise teams.FULL DISK ENCRYPTON (FDE)Full Disk Encryption is native to ESET PROTECT,managing encryption of data on both Windows andMac (FileVault) endpoints, improving data securityand helping organizations solving the problem of dataregulation compliance.CLOUD SANDBOXThe support for cloud sandbox greatly improvesdetection of zero-day threats such as ransomwareby quickly analyzing suspicious files in the powerfulESET cloud sandbox.HARDWARE/SOFTWARE INVENTORYNot only does ESET PROTECT report on all installedsoftware applications across an organization, it alsoreports on installed hardware.This allows you to do more from a single location bydynamically grouping computers based on make, model,OS, processor, RAM, HD space and many more items.GRANULAR POLICY CONTROLOrganizations can set up multiple policies for the samecomputer or group and can nest policies for inheritedpermissions. In addition, organizations can configurepolicy settings as user-configurable, so you can lockdown any number of settings from the end users.SIEM AND SOC SUPPORTESET PROTECT fully supports SIEM tools and canoutput all log information in the widely accepted JSONor LEEF format, allowing for integration with SecurityOperations Centers (SOC).Dashboard of ESET PROTECT
WANT TO HOST THE CONSOLEIN‑HOUSE?For some organizations, hosting software in‑houseis a requirement for various internal or legal reasons.Besides the cloud console, ESET PROTECT isavailable as a full‑featured on-premise solution forin‑house deployments.FLEXIBLE INSTALLESET PROTECT can be installed on Windows, Linux orvia Virtual Appliance. After installation, all managementis done via a web-console, allowing easy access andmanagement from any device or operating system.SUPPORT FOR EDR*To further improve situational awareness and obtainvisibility in the network, ESET PROTECT supportsour EDR (Endpoint Detection & Response) solution,ESET Enterprise Inspector. EEI is multiplatform(Windows and macOS), enables advanced threathunting and remediation, and can seamlessly integratewith your Security Operation Center.*EDR support is only available for on-premESET PROTECT deployments
Your next stepsHow to buy:Simply purchaseany of thesolutions forbusinesses directlyfrom our dedicatedwebsite.Start your30‑days trial nowUnlock your 30-dayfree trial to test outthe fully functionalsolution, includingprotection forendpoints.Migration from on-premise ESET console:Do you currently use ESET’s on-prem console?Contact an ESET partner in your area to assistyou with r/find/
ESET is privately owned. With no debtsdeveloping industry-leading IT securityand no loans, we have the freedom to dosoftware and services, delivering instant,what needs to be done for the ultimatecomprehensive protection againstprotection of all our customers.CERTIFICATI OEMIS O/ Ievolving cybersecurity threats forTYSNFor more than 30 years, ESET has beenWhychoose ESETSAbout ESETECbusinesses and consumers worldwide.270 01ESET AWARDSESET IN NUMBERS110m usersworldwide400k businesscustomersESET is compliant with ISO/IEC 27001:2013, an internationally recognized andapplicable security standard in implementing and managing information security.The certification is granted by the third-party accredited certification body SGSand demonstrates ESET’s full compliance with industry-leading best practices.200 countries &territories13global R&DcentersSOME OF OUR CUSTOMERSprotected by ESET since 2017protected by ESET since 2016more than 14,000 endpointsmore than 9.000 endpointsprotected by ESET since 2016ISP security partner since 2008more than 4,000 mailboxes2 million customer baseANALYST RECOGNITIONESET was named the onlyChallenger in 2019 GartnerMagic Quadrant for EndpointProtection Platforms, for thesecond year running.ESET was rated a StrongPerformer in the ForresterWave(TM): Endpoint SecuritySuites, Q3 2019.ESET was rated ‘Top Player’in the 2019 Radicati EndpointSecurity report according totwo main criteria: functionalityand strategic vision.Gartner Inc, Magic Quadrant for Endpoint Protection Platforms, Peter Firstbrook, Lawrence Pingree, Dionisio Zumerle, Prateek Bhajanka, Paul Webber, August20, 2019. Gartner does not endorse any vendor, product or service depicted in its research publications. Gartner research publications consist of the opinions ofGartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to thisresearch, including any warranties of merchantability or fitness for a particular purpose.Gartner Peer Insights is a free peer review and ratings platform designed for enterprise software and services decision makers. Reviews go through a strictvalidation and moderation process to ensure information is authentic. Gartner Peer Insights reviews constitute the subjective opinions of individual end users basedon their own experiences, and do not represent the views of Gartner or its affiliates.
ESET PROTECT is a cloud console, offered as a service, that ensures real-time visibility for on-premise and off-premise endpoints as well as full reporting and security management for all OSes. It is a single pane of glass over all ESET security solutions deployed in the network. It controls endpoint prevention, detection & response