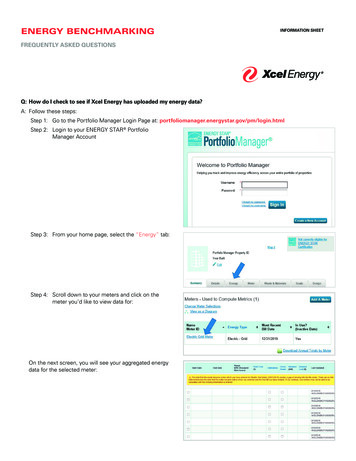
Transcription
Frequently Asked QuestionsCIP Version 5 StandardsConsolidated FAQs and AnswersVersion: October 2015This document is designed to provide answers to questions asked by entities as they transition to the CIP 5 Reliability Standards. It is notintended to establish new requirements under NERC’s Reliability Standards, modify the requirements in any existing reliability standards, orprovide an Interpretation under Section 7 of the Standard Processes Manual. Additionally, there may be other legitimate ways to fulfill theobligations of the requirements that are not expressed within this supporting document. Compliance will continue to be determined based onlanguage in the NERC Reliability Standards as they may be amended from time to time. Implementation of this lesson learned is not asubstitute for compliance with requirements in NERC’s Reliability Standards.This document consolidates several sets of FAQs that had been posted for stakeholder comment, reviewed and revised as appropriate, andapproved by the Standards Committee as follows: FAQs posted for stakeholder comment on November 25, 2014 FAQs posted for stakeholder comment on April 1, 2015 FAQs posted for stakeholder comment on May 1, 2015Note: The “number” column in the table below is not relevant to stakeholders and is only included as an organizational tool for NERC.CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-002-5.1Requirement R1Attachment 1QuestionHow is 1500 MW determined under CIP-0025.1, Attachment 1, criterion 2.1?AnswerIt is the net Real Power capability, which is the grossReal Power capability less any auxiliaries, stationservice, or other internal use of the output ofNumber45
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumbergeneration units. The following are examples that couldbe used for determination of Net Real Power: CIP-002-5.1Requirement R1Attachment 1What is a “shared” BES Cyber System?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015Any method approved by a TransmissionPlanner or Reliability CoordinatorIndustry accepted engineering studies of netgeneration output, such as may be required ofmarket participants.The highest aggregate net generation output(e.g., from an entity's energy accountingsoftware, NERC standard MOD-024-1, MOD025-2).Shared BES Cyber Systems are those that are associatedwith any combination of units in a singleinterconnection, as referenced in CIP-002-5.1,Attachment 1, impact rating criteria 2.1 and 2.2. Forcriteria 2.1 “BES Cyber Systems that could, within 15minutes, adversely impact the reliable operation of anycombination of units that in aggregate equal or exceed1500 MW in a single interconnection.” For criteria 2.2:“BES Cyber Systems that could, within 15 minutes,adversely impact the reliable operation of anycombination of units that in aggregate equal or exceed1000 MVAR. Also refer to the Lesson Learned for CIP02-5.1 Requirement R1: Impact Rating of GenerationResource Shared BES Cyber Systems for furtherinformation and examples.492
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard t R1Attachment 1How can we show that there is not a 15 minute CIP-002-5.1, R1 requires Responsible Entities toimpact on BES (what evidence needs to beconsider a listed set of assets and identify each of thesupplied)?high, medium, or low impact BES Cyber Systems usingAttachment 1. The standard does not require entities toidentify Cyber Assets (or provide evidence on CyberAssets) that are not BES Cyber Systems. The measurefor R1, M1, provides examples of acceptable evidenceto meet the R1 identification of high and mediumimpact BES Cyber Systems, including dated electronic orphysical lists of the high and medium impact BES CyberSystems.”52CIP-002-5.1Requirement R1Attachment 1Should entities who receive an XML feed from[their ISO/RTO] as a backup to their ICCP (BESCyber Asset) consider that as an in-scoperesource for CIP Version 5? Is that part of aMedium Impact BES Cyber System?58Redundancy is not an exclusionary consideration inidentifying BES Cyber Assets and by extension BESCyber Systems. If the Cyber Asset, including CyberAssets that receive backup XML feeds, has an impact onthe BES, consistent with the definition of a BES CyberAsset, then it must be classified and protected as a BESCyber Asset regardless of other Cyber Assets thatperform the same function as this Cyber Asset.Each system should be considered separately for itsimpact on the BES, including backup/redundantsystems.CIP-002-5.1Requirement R1Attachment 1Where do tie line meters with dial-up modemsfall under CIP V5?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015Applicability under CIP V5 depends on thecharacteristics of the assets (Transmission substations)where the metering equipment is installed and theoperating voltage of the tie line the meter is reporting.773
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberIf the data reported by the metering system is used forreal-time situational awareness, the Cyber Assetsassociated with the metering will likely be eithermedium or low impact BES Cyber Assets or BES CyberSystems, based upon the application of Impact RatingCriteria 2.4, 2.5, 3.2, and potentially 2.6 and 2.8. Oncecategorized as medium or low impact, the applicableCIP Standards requirements are determined by theapplicability statements in each requirement. Certainrequirements will be applicable regardless of how themetering BES Cyber Systems communicate with theControl Center. If the BES Cyber Asset is connected to aroutable network, even if the routable network is localonly to the substation, an Electronic Security Perimeterand Electronic Access Point is required. If the meteringBES Cyber Systems are connected serially, the BESCyber Systems are not required to reside within an ESP.If the metering BES Cyber Systems are dial-upaccessible, authentication of the dial-up connection isrequired where technically feasible.CIP-002-5.1Requirement R1Attachment 1If the same PACS system is used for both highand medium locations, do the protectionsneed to be provided at the high level for alllocations?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015The definition of the Physical Access Control Systems(PACS) is "Cyber Assets that control, alert, or log accessto the Physical Security Perimeter(s), exclusive of locallymounted hardware or devices at the Physical SecurityPerimeter such as motion sensors, electronic lockcontrol mechanisms, and badge readers." PACS are alsoassociated with providing protections of BES Cyber894
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberSystems. If the same PACS system is used to controlphysical access to both high and medium impact BESCyber Systems, then all of the requirements for highand medium impact BCS that include their associatedPACS would apply to that single PACS system regardlessof the facility at which the PACS may reside. However,requirements for high and medium impact BCS wherePACS is not listed as an associated Applicable Systemwould not apply to that single PACS system.CIP-002-5.1Requirement R1When identifying BES Cyber Assets, howshould entities approach the term “misuse”?If one Cyber Asset can be misused whichimpacts another Cyber Asset which thenimpacts the BES, do all the Cyber Assets needto be considered BES Cyber Assets?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015The term “misuse” means that the Cyber Asset is beingused for a purpose other than its designed use. Ifmisuse of the Cyber Asset would, within 15 minutes ofits required operation, misoperation, or non‐operation,adversely impact one or more Facilities, systems, orequipment, which, if destroyed, degraded, or otherwiserendered unavailable when needed, would affect thereliable operation of the Bulk Electric System, then theCyber Asset should be classified as a BES Cyber Asset.Referring to the question, each Cyber Asset should beconsidered individually for inclusion as a BES CyberAsset based on the definition of a BES Cyber Asset. If aCyber Asset is determined to not be a BES Cyber Asset,the Cyber Asset should be analyzed to determine if anyother classification (i.e., EACMS, PACS, or PCA) iswarranted.365
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-002-5.1Requirement R1Attachment 1QuestionAnswerNumberWhat should be considered when determiningwhether a Transmission Scheduling System is aBES Cyber System, and if so, is it a medium orhigh impact BES Cyber System?A Transmission Scheduling System may contain BESCyber Assets depending on its functionality and how itis used by the Responsible Entity to support the reliableoperation of the BES. In order to determine if theTransmission Scheduling System is composed of BESCyber Assets, assume the data associated with thesystem is rendered unavailable, degraded, or misused,and if this would adversely impact the reliability of theBES within 15 minutes.53If the Transmission Scheduling System is determined tobe a BES Cyber System, its impact rating will bedetermined by the Control Center or other Facilitywhere the Transmission Scheduling System is located asprovided in Reliability Standard CIP-002-5.1Requirement and Attachment 1.CIP-002-5.1Requirement R1Attachment 1In Attachment 1 of CIP‐002‐5.1, impact ratingcriterion 1.4 states “Each Control Center orbackup Control Center used to perform thefunctional obligations of the GeneratorOperator for one or more of the assets thatmeet criteria 2.1, 2.3, 2.6, or 2.9.” The phrase“one or more of the assets for criterion 2.1 ”is unclear as the criterion 2.1 identifies“groups” of generators. Are the “assets” incriterion 1.4 the “groups” in 2.1 or thegenerators within the groups?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015Impact rating criterion 2.1 references groups ofgenerating units at a single plant location. For theseimpact rating criteria, each individual generating unit isnot considered an asset.61The asset described in impact rating criterion 2.1 is thecommissioned generation with an aggregated net RealPower capability of 1500 MWs at a single plant location.The group of generating units could range from oneunit to many units, but it is the single plant location that6
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberdefines the applicable asset in the case of impact ratingcriterion 1.4.CIP-002-5.1Requirement R1CIP-003-6Requirement R2Some of the systems not previously coveredunder the CIP Standards before may fall underthe assessment process under CIP V5. Do weassess the systems that could cause the EMS(BES Cyber Assets) to fail such as UPS, HVAC(building power control system and cooling forcomputer room)?If a device meets the definition of a Cyber Asset, asdefined in the NERC Glossary of Terms, then it is subjectto consideration as a BES Cyber Asset as defined in theNERC Glossary of Terms.Is RFC 1490 Protocol considered serial?Routable?RFC 1490 is an encapsulation method for carryingnetwork interconnect traffic over a Frame Relaybackbone. If IP traffic is encapsulated in this protocol (ifthe traffic leaves the ESP as routable and is routable atthe destination network), then it would be consideredto be a routable protocol.CIP V5 FAQs – Consolidated FAQs and Answers – October 20153-2014HVAC, UPS, and other support systems are not thefocus of the CIP Standards and will not be the focus ofcompliance monitoring, unless any such supportsystems, including HVAC and UPS, are within an ESP. Ifsuch support systems are within an ESP, these systemswould be a PCA inheriting the highest impact ratingwithin the ESP.227
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-003-6Requirement R2QuestionIs IEC 61850 a routable protocol (for purposesof high and medium impact)?AnswerNumberIEC 61850 is an Ethernet-based standard for the designof electrical substation automation and the abstractdata models can be mapped to a number of protocols,including MMS (Manufacturing Message Specification,the underlying communication architecture for ICCP),GOOSE, and Web Services. IEC 61850 is not a data linkor network layer protocol, thus declaring IEC 61850 tobe a routable or non-routable protocol is notappropriate. Time-critical messages, such as GOOSEmessages for direct inter-bay communication, typicallyrun on a flat Layer 2 network without the need forLayer 3 IP addresses. Other non-time-critical messages,including MMS and web services, typically run on aLayer 3 network, such as TCP/IP, with addressing androuting. The registered entity should carefully evaluatethe communication environment supporting the IEC61850 data protocol to determine if routablecommunication exists. If the IEC 61850 data is beingcommunicated over a TCP/IP network, then thatnetwork connectivity is considered routable and shouldbe protected per the CIP Standards accordingly.23Note: Low impact requirements exempt 61850 from itsscope as stated in the Guidelines and Technical Basis forCIP-003-6 R2: “The defined terms LERC and LEAP areused to avoid confusion with the similar terms used forhigh and medium impact BES Cyber Systems (e.g.,CIP V5 FAQs – Consolidated FAQs and Answers – October 20158
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberExternal Routable Connectivity (ERC) or ElectronicAccess Point (EAP)). To future-proof the standards, andin order to avoid future technology issues, specificallyexclude “point-to-point communications betweenintelligent electronic devices that use routablecommunication protocols for time-sensitive protectionor control functions between Transmission station orsubstation assets containing low impact BES CyberSystems,” such as IEC 61850 messaging.”CIP-004-6In the event of a CIP Exceptional Circumstance,Requirement 4 Part 4.1 does an entity have to meet all of the CIPrequirements that do not specifically mentionCIP Exceptional Circumstance?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015Yes, unless specifically called out in therequirement part with the phrase “except during CIPExceptional Circumstances”, compliance to the CIPversion 5 standards and requirements must bemaintained. Note that CIP-004-6 R4 Part 4.1 includesCIP Exceptional Circumstances for authorizingelectronic access, unescorted physical access andaccess to designated storage locations for BES CyberSystem Information. Consequently, an entity mayconsider specific procedures surrounding a CIPExceptional Circumstance in its CIP-011-2 R1 Part 1.2procedure for protecting and securely handling BESCyber System information, including storage, transitand use. Access to BES Cyber System Information maybe controlled in accordance with the requirements ofCIP-004-6, which provides for a CIP ExceptionalCircumstance, that CIP-011-2 does not allow.629
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberConsider also, for example, that the measures columnfor CIP-004-6 R2 Part 2.2 includes the phrase,“documentation of when CIP Exceptional Circumstanceswere invoked.”CIP-004-6Does the CIP-004-6 standard require separatetraining for each role, function, orresponsibility? "No, the CIP-004-6 standard does not require separatestraining for each role, function, or responsibility. Allnine elements have to be addressed collectively acrossall the training but the entity has flexibility to determinewhich content areas are appropriate for each role.Refer to the Guidelines and Technical Basis in CIP-004-6for more information.63CIP-004-6For access revocations due to a termination,reassignment, or transfer, when does the clockstart for revocation obligations and when mustrevocation be complete?From the CIP-004-6 Guidelines and Technical Basisstates “the timing of the termination action may varydepending on the circumstance” and goes on to specifypossible processes associated with terminationscenarios.64For terminations, the 24-hour clock starts when theentity takes action to terminate according to theirprocess. As an example, the action to terminate couldbe the notification to the individual of theirtermination, and then removal of unescorted physicalaccess and Interactive Remote Access must completewithin 24 hours after notification.CIP V5 FAQs – Consolidated FAQs and Answers – October 201510
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberFor reassignments or transfers, the entity mustestablish a date when the individual no longer needsaccess. Revocation must then occur by the end of thenext calendar day after this entity established date.Business days are not taken into consideration for thisrequirement. Entities should be careful to observethese timeframes even on weekends and holidays.CIP-005-5Requirement R1If Part 1.4 (Dial Up Connectivity) applies, whatother requirements apply to that system andtheir associated PCA?Refer to the “Applicable Systems” column for eachrequirement to determine what other requirementsapply. For example, if the system is a medium impactBES Cyber System (not at a Control Center and withoutExternal Routable Connectivity), many otherrequirements apply. Applicable requirements areidentified by referring to the “Applicable Systems”column for “medium impact BES Cyber Systems.”80Dial‐up connectivity is a specific connection mechanismapplied to High and Medium Impact BES Cyber Systemsunder CIP‐005-5 R1 Part 1.4. All other CIP V5 standardsapplicable to High and Medium Impact BES CyberSystems would apply, depending on impactclassification of the specific BES Cyber System and a lackof unique criteria on the "Applicable Systems" columnto specifically exclude the BES Cyber System.CIP V5 FAQs – Consolidated FAQs and Answers – October 201511
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionCIP-005-5Requirement R1If a Responsible Entity implements a vendorappliance as the perimeter firewall, can theoptional module to perform the monitoringfunction reside on the same appliance?CIP-005-5Requirement R2When a desktop/laptop is used to log in to ajump box (Intermediate System) should thedesktop/laptop have the same physicalcontrols as the assets it is accessing?CIP-005-5Requirement R1Can there be Protected Cyber Assets (PCAs)associated with medium impact BES CyberSystems at transmission substations wherethere is no External Routable Connectivity?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015AnswerNumberYes, the module can reside on the same appliance.Reliability Standard CIP-005-5 Requirement R1.5requires “one or more methods for detecting known orsuspected malicious communications for both inboundand outbound communications”. This requirement doesnot specify that two or more physical devices be usedto monitor inbound and outbound communications.Ref. the Guidelines and Technical Basis in CIP-005-5 foradditional information.In this example, the desktop/laptop is not part of a BESCyber System, as it is outside of the ESP and usesappropriate measures for Interactive Remote Access.The jump box (Intermediate System) would beconsidered an EACMS and must meet the requirementsthat apply to an EACMS. It would not be necessary forthe desktop/laptop to also meet the requirements.76Reliability Standard CIP-005-5, R1 Part 1.1 requires thatmedium impact BES Cyber System(s) that are connectedto a network via a routable protocol, even if they haveno external routable connectivity, must reside within adefined ESP. A PCA is any Cyber Asset that resides onthe routable network contained within the ESP, but isnot otherwise classified as a BES Cyber Asset or EACMS.This designation of PCA is without consideration ofExternal Routable Connectivity. There are severalrequirements in the reliability standards that are217312
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberapplicable to "medium impact BES Cyber Systems andtheir associated PCA".CIP‐005-5Requirement R1Regarding CIP‐005‐5, page 16 in the Guidelinesfor R1, what is required of the ESP defined fora standalone network (Medium Impact BCS ata substation that meets CIP‐002-5.1Requirement R1, Attachment 1, Criterion 2.5that has no External Routable Protocol)?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015As required under CIP‐005-5, R1, Part 1.1, "allapplicable Cyber Assets connected to a network via aroutable protocol shall reside within a defined ESP."Each of the CIP V5 requirements must be reviewed bythe Entity to determine their applicability to a mediumimpact BES Cyber System. Some of the requirementsfurther qualify the "applicable systems," and others donot, making them applicable to those medium impactBES Cyber Systems without External RoutableProtocol. If there is dial-up connectivity to the mediumimpact BCS, then CIP-005-5, R1, Part 1.4 applies as well.If it's truly standalone (no ERC), then the Entity shoulddocument the perimeter to prove the components ofthe BCS are within the ESP.8113
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-006-6Requirement R1QuestionFor a substation with Medium Impact BESCyber Systems, can the ESP be extended toinclude two control houses with buried cablebetween the two? Will this communicationrequire alarms, encryption, or something elseto meet the draft CIP-006-6 requirements forthe revisions to CIP-006-6?AnswerNumberEntities can determine how they want to define theirESPs. For the CIP-006-6 R1 Part 1.10 revisions, entitiesare required to physically protect cabling that extendsoutside the Physical Security Perimeter for high impactand medium impact Control Centers. Burying the cablesor running continuous conduit can be an approach torestricting physical access. Additionally, applyingencryption over the connection is also an approach thatcan be used.83CIP-006-6 R1 Part 1.10 revisions do not apply tosubstations.CIP-006-6Requirement R1What are the options for utilizing two or moredifferent physical access controls for HighImpact BES Cyber System Physical SecurityPerimeters?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015The Guidelines and Technical Basis for CIP-006-6, R1states: "The FERC Order No. 706, Paragraph 572,directive discussed utilizing two or more different andcomplementary physical access controls to providedefense in depth. It does not require two or morePhysical Security Perimeters, nor does it exclude theuse of layered perimeters. Use of two-factorauthentication would be acceptable at the same entrypoints for a non-layered single perimeter. For example,a sole perimeter’s controls could include either acombination of card key and pin code (something youknow and something you have), or a card key andbiometric scanner (something you have and somethingyou are)."8614
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-006-6Requirement R3QuestionAnswerNumberWhat does the testing requirement in CIP-0066, R3, Part 3.1 mean for PACS workstations andservers? Does that need to be documented thesame way the card readers/door alarms are?PACS workstations and servers should be tested in sucha way to demonstrate "they function properly" asrequired in Part 3.1. Since these Cyber Assets do notperform the same functions as the card readers/dooralarms, the actual testing and documentation maydiffer. Sufficient evidence should be documented todemonstrate the Cyber Assets were tested and"function properly". Functional tests may include, butare not limited to, granting, revoking, monitoring, andlogging of access.90One method of accomplishing this would be to: (a)create a set of test scripts for the Cyber Assets(collectively or individually) to demonstrate they arefunctioning properly, (b) execute them as required, (c)and document the results of the executed tests.Verification of the PACS functioning under normaloperations would also suffice.CIP-006-6Requirement R1Is CIP-006-6 R1 Parts 1.6 and R1.7 intended toincluding monitoring and alerting on guard andbadging workstations?CIP V5 FAQs – Consolidated FAQs and Answers – October 2015Yes, CIP-006-6 R1 Parts 1.6 and 1.7 are intended tomonitor and alert on potential unauthorized physicalaccess to the PACS systems. In accordance with CIP006-6, R1, Part 1.6, devices that make up the PACSsystem including servers, controllers, and workstationsshould be brought into scope for this requirement.Depending on the configuration, some guard andbadging workstations may not be PACS associated withhigh or medium impact BES Cyber Systems and,9115
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumbertherefore, monitoring and alerting would not berequired for the workstations not considered PACS.CIP-007-6Requirement R5What are examples entities may use wheninventorying all known enabled default orgeneric account types?Some of the ways to identify default and/or genericaccounts include: CIP-007-6Requirement R5Are password safes recommended?CIP V5 FAQs – Consolidated FAQs and Answers – October 201592Vendor provided lists of the required accountson a system.Tools that can be run to identify user accountscreated on a local system.Tools such as AD (or LDAP Queries) may have alisting of accounts with access to systems.Review the device/application web sites orsupport to identify if there are default accounts.A password safe is a utility application that is used tosecurely store a set of passwords and pass phrases.While the ERO Enterprise (NERC and the RegionalEntities) cannot recommend or endorse the use of anyparticular technology, password safes can be aneffective tool in an organization’s overall cybersecurityprogram when used properly, and their use, providingany information contained within the password safemeets the definition of BES Cyber System Information,should adhere to the entity’s CIP-011-2 InformationProtection program. In addition as a best practice, thepassword safe’s passphrase should require periodicchange and meet defined password criteria. Forexample, an entity may consider CIP-007-6, Parts 5.59316
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberand 5.6, and if shared with multiple individuals, CIP007-6, Part 5.3.CIP-007-6Requirement R1Signage for physical port protection (CIP-007-6,R1.2) – is it acceptable to place signs at the PSPdoors, rather than on each individual deviceport?Signage is explicitly allowed as a measure ofcompliance. If a sign is used, then its placement and thelanguage used on the sign are both considerations fordetermining whether it conveys that the port shouldnot be used without proper authorization. TheGuidelines and Technical Basis for CIP-007-6 R1 states“In essence, signage would be used to remindauthorized users to “think before you plug anything intoone of these systems” which is the intent. This control isnot designed primarily for intruders ”.94In addition, the requirement does not requiredemonstrating that a protected, physical input/outputport that is unnecessary for network connectivity,console commands, or removable media has not beenused. For more details, refer to the measures column,the guidelines and technical basis, and violation severitylevel in the standard for this requirement. For example,the guidelines and technical basis for the requirementstates: “this control, with its inclusion of means such assignage, is not meant to be a preventative controlagainst intruders signage would be used to remindauthorized users to “think before you plug anything intoone of these systems which is the intent.CIP V5 FAQs – Consolidated FAQs and Answers – October 201517
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceQuestionAnswerNumberNote that this FAQ replaces the draft lesson learned“CIP-007-6 R1 Part 1.2: Protecting Physical Ports:Tamper Tape, May 27, 2014”.CIP-007-6Requirement R5How should an entity treat the devices that do Include devices that utilize passwords without annot have accounts but use separate passwords associated user ID in the CIP-007-6 R5 Part 5.2to delineate the role of the user? (substations). inventory of known enabled default or other genericaccount types. In these cases, a null account name mayWhat about situations where there are nobe used. It may be advisable to include a field in theaccounts, only passwords, but the users don'tinventory where additional identifying details can behave access to the passwords?associated with the null account name, such as a briefdescription of the user role associated with thatpassword.101For those BES Cyber Assets identified as beingaccessible by such a password, access to a Cyber Assetwith only a password should be considered a "genericaccount type," and individuals who have authorizedaccess to these shared type of accounts should bedocumented as such. Entities are not expected todocument the passwords themselves for these “genericaccount types.”Caution: Evaluate if these are default passwords.CIP V5 FAQs – Consolidated FAQs and Answers – October 201518
CIP Version 5 FAQs – Consolidated FAQs and AnswersStandard ReferenceCIP-007-6Requirement R3QuestionAnswerNumberFor the implementation of malicious codeprevention, should entities choose to deter,detect, or prevent malicious code? If an entitychooses to deter, how should they plan oncomplying with CIP-007-6, R3, Part 3.2 sincethere would be no mechanism to detect? Isthere an implicit requirement in Part 3.2 todeploy detective controls?Part 3.2, in and of itself, does not have an implicitrequirement to deploy detective controls; rather, Part3.2 works in concert with other CIP requirements, suchas CIP-007-6, R4, Part 4.1.3 which requires logging formalicious code.1-2014Under Part 3.2, Responsible Entities have an obligationto mitigate malicious code whenever it is detec
This document is designed to provide answers to questions asked by entities as they transition to the CIP 5 Reliability Standards. It is not intended to establish new requirements under NERC's Reliability Standards, modify the requirements in any existing reliability standards, or provide an Interpretation under Section 7 of the Standard Process.