Transcription
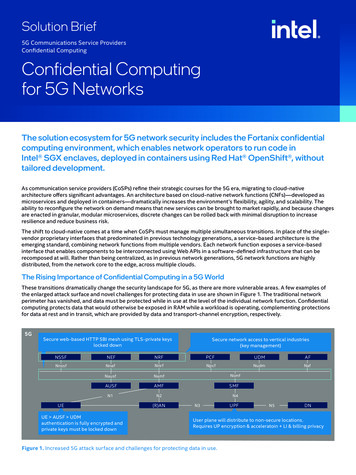
Solution Brief5G Communications Service ProvidersConfidential ComputingConfidential Computingfor 5G NetworksThe solution ecosystem for 5G network security includes the Fortanix confidentialcomputing environment, which enables network operators to run code inIntel SGX enclaves, deployed in containers using Red Hat OpenShift , withouttailored development.As communication service providers (CoSPs) refine their strategic courses for the 5G era, migrating to cloud-nativearchitecture offers significant advantages. An architecture based on cloud-native network functions (CNFs)—developed asmicroservices and deployed in containers—dramatically increases the environment’s flexibility, agility, and scalability. Theability to reconfigure the network on demand means that new services can be brought to market rapidly, and because changesare enacted in granular, modular microservices, discrete changes can be rolled back with minimal disruption to increaseresilience and reduce business risk.The shift to cloud-native comes at a time when CoSPs must manage multiple simultaneous transitions. In place of the singlevendor proprietary interfaces that predominated in previous technology generations, a service-based architecture is theemerging standard, combining network functions from multiple vendors. Each network function exposes a service-basedinterface that enables components to be interconnected using Web APIs in a software-defined infrastructure that can berecomposed at will. Rather than being centralized, as in previous network generations, 5G network functions are highlydistributed, from the network core to the edge, across multiple clouds.The Rising Importance of Confidential Computing in a 5G WorldThese transitions dramatically change the security landscape for 5G, as there are more vulnerable areas. A few examples ofthe enlarged attack surface and novel challenges for protecting data in use are shown in Figure 1. The traditional networkperimeter has vanished, and data must be protected while in use at the level of the individual network function. Confidentialcomputing protects data that would otherwise be exposed in RAM while a workload is operating, complementing protectionsfor data at rest and in transit, which are provided by data and transport-channel encryption, respectively.5GSecure web-based HTTP SBI mesh using TLS-private keyslocked downNSSFNnssfSecure network access to vertical industries(key amfNsmfAUSFAMFSMFN1N2N4UEUE AUSF UDMauthentication is fully encrypted andprivate keys must be locked down(R)ANN3UPFN5DNUser plane will distribute to non-secure locations.Requires UP encryption & acceleratoin LI & billing privacyFigure 1. Increased 5G attack surface and challenges for protecting data in use.
Solution Brief Confidential Computing for 5G NetworksIntel Platform Support for 5G Use CasesTogether with other hardware security measures such as crypto acceleration, Intel SGX enables a range of 5G use cases,including the following: Confidential communication for service-based architecture Secure authentication and secure converged edge Secure federated multitenant content delivery Secure communication edge-to-core and between networks Assured integrity of billing information with an audit trailConfidential computing is chiefly concerned with isolatingdata from other workloads operating in their sharedmulti-tenant, multicloud infrastructure, preventing bothinadvertent and malicious leaks. A prevalent approach is toprovide an isolated trusted execution environment (TEE),where code can be run beyond the reach of outside software.CoSPs use TEEs to help meet challenges associated withprotecting data in use by highly distributed 5G services infunctional areas such as the following:CPU PACKAGERAMCORESAMEX: 3224134584-26864Jco3lks937wENCLAVE Service-based architecture web-based integrationof network functions, protected using transport layersecurity (TLS) Key management for secure network access extendedto in dustry partners and customersSnoop Authentication with the Authentication Server Function(AUSF) and unified data management (UDM)Snoop Distributed user plane, including to non-secure physicallocationsIn addition to isolation, TEEs provide assurance to outsideentities that the code running inside them has not beencorrupted or tampered with through the process ofattestation. By attesting to the authenticity of its workload,a TEE can therefore give the CoSP’s remote partnersand customers confidence that the destination they areconnecting to is legitimate and trustworthy, as well as beingprotected from interception by third parties.Figure 2. Data and code protection in Intel SGX enclaves.EnclaveAPPAPPProtected Enclaves with Intel Software GuardExtensions (Intel SGX)Intel SGX is a set of processor instructions supported by3rd Gen Intel Xeon Scalable processors that is used forpartitioning a region of memory as a secure enclave thatisolates and protects specific data and code, as shown inFigure 2. The contents of the enclave are encrypted using acryptographic key generated within the CPU, and likewise,the data and code are only decrypted inside the CPU. Thisarrangement protects data and code from compromise withinRAM or in transit between the CPU and RAM.The enclave prevents data from being leaked to othersoftware running on the same platform, including otherworkloads as well as processes running at high privilegelevels, such as the OS, hypervisor, BIOS, or firmware. The useof enclaves therefore dramatically reduces the attack surface,as shown in Figure 3.APPOSHYPERVISORHARDWAREConventional Attack SurfaceAttack Surface with Intel SGXFigure 3. Reduced attack surface.2
Solution Brief Confidential Computing for 5G NetworksThe native method of adapting software for use with IntelSGX is for the developer to identify the sensitive portionof the application—designated the trusted portion—anddefine an enclave for it to operate within by using the IntelSGX SDK. The Intel SGX enclave is deployed as a sharedlibrary. The remaining, untrusted portion of the applicationoperates outside the enclave, and Intel SGX treats it ascompromised by default. The trusted and untrusted portionsof the application communicate with each other using specificIntel SGX instructions. The Intel Attestation Service plays avital role in establishing and maintaining the trusted status ofcode by enabling applications to verify the following factorscryptographically: The code is running as-built in a genuine enclave The hardware is a secure Intel SGX-capable platform withall needed microcode updates applied All necessary Intel SGX hardware and softwareconfigurations are made correctlyFortanix solutions help streamline the implementationof confidential computing based on Intel SGX for 5Gapplications, including efficient attestation for 5G virtualizednetwork functions (VNFs) at scale.Platform Capabilities that ComplementIntel SGX3rd Gen Intel Xeon Scalable processors incorporatemultiple hardware-resident security features that workin conjunction with Intel SGX. The following features areof particular interest to CoSPs as they deploy 5G networkfunctions: Built-in crypto acceleration. To help CoSPs handlethe performance impact of pervasive encryption in 5G,platform results include up to 4.2x higher TLS encryptedconnections per second.1 Intel Platform Resilience. To protect fundamentalplatform firmware components, this Intel FPGA-basedsolution establishes a chain of trust and verifies firmwareimages before execution.Data Security Manager Data Security ManagerData Security Manager provides acloud-ready unified HSM, KMS, andKMIP solution with FIPS 140-2 Level3 certification.Confidential Computing with Fortanix SolutionsFortanix technologies implement Intel SGX across a rangeof confidential computing functions, as illustrated in Figure4. The Fortanix Data Security Manager implements IntelSGX in its key-management service (KMS), which providessecure generation, storage, and use of cryptographic keys,certificates, and secrets. Runtime Encryption Technologyprovides a comprehensive environment for developing,operating, and maintaining Intel SGX enclaves.Enclave OS is the runtime environment for code to run insideenclaves, based on simply repackaging existing imageswithout requiring any changes to application binaries.The ability to run existing software without modificationdramatically reduces the time, cost, and complexityassociated with deploying it in a confidential computingenvironment. Enclave OS operates a root of trust establishedin the CPU to create a region of memory that is inaccessibleto any process outside the application itself, regardless ofprivilege level. The CPU autonomously generates the keythat it uses to encrypt this memory on the fly, using a secretprovisioned at the time of manufacture, so the key is neverexposed outside the CPU itself.The Confidential Computing Manager is a cloud-native SaaSenvironment that provides a single pane of glass for managingsecure enclaves and confidential computing nodes, onprem or in any cloud or hosted environment (on nodes thatsupport Intel SGX). It controls the enclave lifecycle, includingenablement for policy enforcement measures on runningapplications. For example, whitelisting allows applicationsto run only on a predefined list of hosts, providing addedassurances of integrity and protection. Geofencing restrictsthe geographic area within which an application can run in amulticloud environment, for regulatory and audit purposes.The Confidential Computing Manager also performs highlyefficient attestation services, with minimal burden placed ondevelopers and network operators.The Enclave Development Platform (EDP) is an open sourceenvironment for writing Intel SGX enclaves from scratch,using the Rust programming language. The design of theEDP is optimized by years of in-house use by Fortanix todevelop various products, making it exceptionally efficientand developer-friendly. Rust combines high computationalperformance with built-in code safety measures, especiallyfor safe concurrency and memory safety. The Rust compilerRuntime Encryption Technology ENCLAVE OSConfidential ComputingManagerRuntime Encrytion allows you torun any application unmodifiedinside Intel SGX.Figure 4. Fortanix technology portfolio for confidential computing.EDPThe Enclave Development Platformbrings best of Rust and Intel SGX.3
Solution Brief Confidential Computing for 5G Networksallows for code to be compiled specifically for Intel SGX andincorporates static code analysis to provide another level ofverification for code safety.OS and container runtime, hardened by Red Hat securityengineers, as well as networking, monitoring, registry, andauthentication and authorization components.The Fortanix Node Agent software runs on physical or virtualcompute nodes, as an intermediary between unmodifiedapplications and Fortanix services. It enables computenodes to register with the Confidential Computing Managerand manages the workloads operating in secure enclaves.The Node Agent is instrumental in the establishment oftrusted compute pools, validating compute-node hardwareand platform software. It also assists with applicationattestation and visibility for the Confidential ComputingManager. Fortanix is working with the cloud ecosystem toenable deployment of the Node Agent through a varietyof platforms, including Microsoft Azure and Red Hat OpenShift Container Platform.OpenShift encapsulates discrete capabilities as Operators,which are software entities that automate and acceleratemanagement tasks. Functionally, OpenShift Operators arecustom, application-specific Kubernetes controllers runningon the Kubernetes master nodes that commonly fill rolessuch as dynamic configuration and tuning of compute andnetwork parameters.Automated Deployment on Red Hat OpenShiftRed Hat OpenShift is an enterprise Kubernetes platform,shown in Figure 5, that automates management functionsfor hybrid cloud, multicloud, and edge deployments, helpingCoSPs increase operational efficiency. It incorporates a LinuxAdvancedClusterManagementMulti-Cluster ManagementDiscovery Policy Configuration WorkloadsBuild Cloud-Native AppsManage WorkloadsOpenShift ContainerPlatformRed Hat sustains the open source Operator Frameworkproject to provide tooling and support to the Operatorecosystem. This includes the Operator SDK, which abstractsaway Kubernetes API complexities from developers, aswell as the Operator Lifecycle Manager, which oversees thelifecycles of all Operators on a Kubernetes cluster, includinginstallation, configuration, and updates. Red Hat alsovalidates the functionality and soundness of Operators onOpenShift, providing developers and cluster administratorswith a library of workloads as a service in the form of Red HatOpenShift Certified Operators.Developer ProductivityPlatform ServicesApplication ServicesDeveloper ServicesService Mesh, Serverless, BuildsCI/CD Pipelines, Full Stack LoggingChargebackDatabases, Languages, Runtimes,Integration, Business Automation,100 ISV ServicesDeveloper, VS Code Extensions,IDE Plugins, Code-ReadyWorkspaces and ContainersCluster ServicesAutomated Ops, Over-The-Air Updates, Monitoring, Registry, Networking, Router, KubeVirt, OLM, HelmOpenShift KubernetesEngineKubernetesRed Hat Enterprise Linux and RHEL CoreOSAny InfrastructurePublic CloudPrivate CloudManaged CloudEdgePhysicalVirtualIntel Memory and Storage TechnologiesIntel Ethernet AdaptersFigure 5. CoSP implementation of Red Hat OpenShift .4
Solution Brief Confidential Computing for 5G NetworksConclusionCasa Systems: Deploying 5G Services withFortanix on OpenShift Intel, Fortanix, and Red Hat are working with Casa Systemsto enable 5G network services—including the 5G SACore—to be deployed on OpenShift using the FortanixNode Agent Operator. This proof of concept solutionprovides a blueprint for the industry to operate CNFs onOpenShift that benefit from protection by Intel SGXsecure enclaves.The Fortanix Confidential Computing Manager Node Agentis now offered as a Red Hat OpenShift Certified Operatorthrough the Red Hat Embedded Operator Hub, which isincluded in Red Hat OpenShift. This simple deploymentpath allows for quick installation and helps streamlinemaintenance. The Operator is a key contributor to the abilityto easily provide confidential computing for 5G workloads.In addition to the need to protect data at rest and in flight,the 5G Standalone (SA) core creates new imperatives for theprotection of data while in use, from the edge to the networkcore. Confidential computing rises to this challenge, withIntel SGX providing secure enclaves that define isolatedmemory space for data and executing code. Fortanix enablesexisting applications to operate in secure enclaves withoutmodification, making the adoption and utilization of Intel SGXsignificantly easier.To help streamline the process of packaging, deploying, andmanaging applications that make use of Intel SGX, Fortanixoffers the Confidential Computing Manager as a Red HatOpenShift Operator. This combination of technologies makesit easy for CoSPs to deploy CNFs that execute using Intel SGXsecure enclaves, without added development burden.More InformationIntel SGX: ology/software-guard-extensions.htmlFortanix Confidential Computing: ting/Red Hat OpenShift : ftFortanix Red Hat Operator: 90772a23a5230f9d1a2Casa Systems: ity.pdfSolution provided by:See [70], [90], [71], and [69] at 3rd Generation Intel Xeon Scalable Processors - 1 - ID:615781 Performance Index. Testing by Intel as of August 4, 2020. Performance comparisons relative to2nd Gen Intel Xeon Scalable processors using a single buffer algorithm versus multi-buffer algorithms for 3rd Gen Intel Xeon Scalable processors. Results have been estimated based on preproduction tests at iso core count and frequency as of August 2020. Performance gains are shown for individual cryptographic algorithms.Performance varies by use, configuration and other factors. Learn more at www.intel.com/PerformanceIndex.Performance results are based on testing as of dates shown in configurations and may not reflect all publicly available updates. See configuration disclosure for configuration details. No productor component can be absolutely secure.Intel does not control or audit third-party data. You should consult other sources to evaluate accuracy.Your costs and results may vary.Intel technologies may require enabled hardware, software, or service activation.You may not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to grant Intel anonexclusive, royalty-free license to any patent claim thereafter drafted which includes subject matter disclosed herein.The products described may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are availableon request. Intel Corporation. Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.1021/RKM/MESH/346428-001US15
Fortanix technologies implement Intel SGX across a range of confidential computing functions, as illustrated in Figure 4. The Fortanix Data Security Manager implements Intel SGX in its key-management service (KMS), which provides secure generation, storage, and use of cryptographic keys, certificates, and secrets. Runtime Encryption Technology











