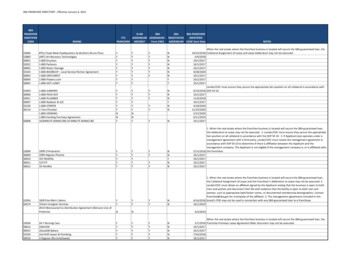
Transcription
CREDANTData Security Partner GuideFebruary 2012 Series
PrefaceWho Should Read This GuideHow to Read CommandsThis Cisco Smart Business Architecture (SBA) guide is for people who fill avariety of roles:Many Cisco SBA guides provide specific details about how to configureCisco network devices that run Cisco IOS, Cisco NX-OS, or other operatingsystems that you configure at a command-line interface (CLI). This sectiondescribes the conventions used to specify commands that you must enter. Systems engineers who need standard procedures for implementingsolutions Project managers who create statements of work for Cisco SBAimplementationsCommands to enter at a CLI appear as follows:configure terminal Sales partners who sell new technology or who create implementationdocumentationCommands that specify a value for a variable appear as follows: Trainers who need material for classroom instruction or on-the-jobtrainingCommands with variables that you must define appear as follows:ntp server 10.10.48.17class-map [highest class name]In general, you can also use Cisco SBA guides to improve consistencyamong engineers and deployments, as well as to improve scoping andcosting of deployment jobs.Commands shown in an interactive example, such as a script or when thecommand prompt is included, appear as follows:Release SeriesLong commands that line wrap are underlined. Enter them as one command:Cisco strives to update and enhance SBA guides on a regular basis. As wedevelop a new series of SBA guides, we test them together, as a completesystem. To ensure the mutual compatibility of designs in Cisco SBA guides,you should use guides that belong to the same series.All Cisco SBA guides include the series name on the cover and at thebottom left of each page. We name the series for the month and year that werelease them, as follows:month year SeriesFor example, the series of guides that we released in August 2011 arethe “August 2011 Series”.You can find the most recent series of SBA guides at the following sites:Customer access: http://www.cisco.com/go/sbaPartner access: http://www.cisco.com/go/sbachannelFebruary 2012 SeriesRouter# enablewrr-queue random-detect max-threshold 1 100 100 100 100 100100 100 100Noteworthy parts of system output or device configuration files appearhighlighted, as follows:interface Vlan64ip address 10.5.204.5 255.255.255.0Comments and QuestionsIf you would like to comment on a guide or ask questions, please use theforum at the bottom of one of the following sites:Customer access: http://www.cisco.com/go/sbaPartner access: http://www.cisco.com/go/sbachannelAn RSS feed is available if you would like to be notified when new commentsare posted.Preface
Table of ContentsWhat’s In This SBA Guide. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1Overview of Cisco Borderless Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2Business Benefits. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3CREDANT Product Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4CREDANT Deployment Workflow. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5How to Contact Us. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7ALL DESIGNS, SPECIFICATIONS, STATEMENTS, INFORMATION, AND RECOMMENDATIONS (COLLECTIVELY, "DESIGNS") IN THIS MANUAL ARE PRESENTED "AS IS," WITH ALL FAULTS. CISCO AND ITS SUPPLIERSDISCLAIM ALL WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OFDEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THE DESIGNS, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCHDAMAGES. THE DESIGNS ARE SUBJECT TO CHANGE WITHOUT NOTICE. USERS ARE SOLELY RESPONSIBLE FOR THEIR APPLICATION OF THE DESIGNS. THE DESIGNS DO NOT CONSTITUTE THE TECHNICALOR OTHER PROFESSIONAL ADVICE OF CISCO, ITS SUPPLIERS OR PARTNERS. USERS SHOULD CONSULT THEIR OWN TECHNICAL ADVISORS BEFORE IMPLEMENTING THE DESIGNS. RESULTS MAY VARYDEPENDING ON FACTORS NOT TESTED BY CISCO.Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposesonly. Any use of actual IP addresses in illustrative content is unintentional and coincidental. Cisco Unified Communications SRND (Based on Cisco Unified Communications Manager 7.x) 2012 Cisco Systems, Inc. All rights reserved.February 2012 SeriesTable of Contents
What’s In This SBA GuideAbout SBACisco SBA helps you design and quickly deploy a full-service businessnetwork. A Cisco SBA deployment is prescriptive, out-of-the-box, scalable,and flexible.About This GuideThis additional deployment guide includes the following sections: Business Overview—The challenge that your organization faces.Business decision makers can use this section to understand the relevance of the solution to their organizations’ operations.Cisco SBA incorporates LAN, WAN, wireless, security, data center, applicationoptimization, and unified communication technologies—tested together as acomplete system. This component-level approach simplifies system integrationof multiple technologies, allowing you to select solutions that solve yourorganization’s problems—without worrying about the technical complexity.For more information, see the How to Get Started with Cisco ons/Enterprise/BorderlessNetworks/Smart Business Architecture/SBA Getting Started.pdf Technology Overview—How Cisco solves the challenge. Technicaldecision makers can use this section to understand how the solutionworks. Deployment Details—Step-by-step instructions for implementing thesolution. Systems engineers can use this section to get the solution upand running quickly and reliably.This guide presumes that you have read the prerequisites guides, as shownon the Route to Success below.Prerequisite GuidesENTYou are HereBNDesign OverviewInternet EdgeDeployment GuideCisco Data SecurityDeployment GuideCREDANT Data SecurityPartner GuideRoute to SuccessTo ensure your success when implementing the designs in this guide, youshould read any guides that this guide depends upon—shown to the leftof this guide on the route above. Any guides that depend upon this guideare shown to the right of this guide.For customer access to all guides: http://www.cisco.com/go/sbaFor partner access: http://www.cisco.com/go/sbachannelFebruary 2012 SeriesWhat’s In This SBA Guide1
Overview of CiscoBorderless NetworksThe Cisco Smart Business Architecture—Borderless Networks forEnterprise Organizations offers partners and customers valuable networkdesign and deployment best practices; helps organizations to deliver superior end-user experiences using switching, routing, security and wirelesstechnologies; and includes comprehensive management capabilities for theentire system. Customers can use the guidance provided in the architectureand deployment guides to maximize the value of their Cisco network in asimple, fast, affordable, scalable and flexible manner.Figure 1 - CREDANT Data Security Integrated into the SmartBusiness Architecture—Borderless Networks for EnterpriseOrganizationsFebruary 2012 SeriesModular design means that technologies can be added when the organization is ready to deploy them. Figure 1 shows how the CREDANT data security solution integrates into the Borderless Networks architecture.This guide is part of a comprehensive data security system designed tosolve customers’ business problems, such as protecting intellectual property and sensitive customer information assets, and meeting compliancerequirements. The guide focuses on Cisco’s partnership with CREDANTTechnologies to deliver affordable endpoint encryption as a part of Cisco’sbroader data security system.Overview of Cisco Borderless Networks2
Business BenefitsThe globalization of information has forever changed the security landscape.Information is exchanged in less than a millisecond. Financial services companies process transactions involving billions of customer financial records.Healthcare providers store and access information on life-threateningillnesses and confidential patient records. For better or worse, our new, moredigitized world exposes sensitive corporate, personal, and employee datato loss or theft at the corporate endpoint. As a result of this profound shift incomputing, the regulatory and compliance landscape has evolved as fast asthe technological landscape.In the United States, Canada, and Europe, national regulatory standardsincreasingly supplement local reforms as the government pressures industries and businesses of all sizes to protect consumers’ personal information. Inmany cases, the penalties for non-compliance can be crippling. No companyor industry is exempt from data tampering. And without proper measures,none can escape the risk of fines, loss of reputation, or possible bankruptcy.Data encryption isn’t just a best practice. It is an imperative for survival in theglobal, digitized marketplace. Companies failing to meet their compliancerequirements and adequately protect against a data breach face fines andother costs extending into the tens of millions of dollars. Yet every organization is unique. The right combination of data encryption solutions must bedefined by the existing infrastructure, regulatory requirements and business practices. By partnering with Cisco and CREDANT, organizations canbegin to adopt a holistic approach to data security—encrypting data on thenetwork, at the gateway, via VPN, or at rest at the endpoint.February 2012 SeriesProtecting sensitive information is critical, and with CREDANT, organizations gain flexibility in how they choose to protect sensitive information.Encryption technology is built on well established standard algorithms, butthe solutions built on that technology include a variety of software- andhardware-based encryption options to meet different business needs.As there is a wide range of options to secure critical corporate data, thereis also a wide range of criteria to consider when deciding how to bestprotect your business. Power users or developers tend to be very sensitive to even the smallest impact on system performance. Less technicallysavvy end users will likely inundate the help desk with calls for assistanceif they encounter a solution that forces them to change the way they work.Executives may carry more sensitive information than end users and thusrequire different security policies. Traveling employees naturally incur morerisk of data loss for a number of reasons than do employees working on adesktop system in a secure office. These are just a few of the criteria thatorganizations must navigate when choosing the right solution or solutionsfor their business.Business Benefits3
CREDANT ProductOverviewCREDANT offers both hardware and software encryption with centrallymanaged or unmanaged options, depending on your needs. All managedsolutions include extensive reporting to satisfy compliance needs and toease deployment and day-to-day use. Products can be mixed and matchedto find an overall solution that best fits your needs: CREDANT Mobile Guardian provides software encryption and securityfor Windows or Mac OS X laptops and desktops, removable media,and PDAs and Smartphones. Windows systems are protected withCREDANT’s Intelligent Encryption and full disk encryption (FDE) is usedto protect Mac computers. External media encryption is provided forboth Windows and handhelds. Windows protection is available in bothmanaged and unmanaged varieties. CREDANT FDE DriveManager technology fortifies the SeagateMomentus self-encrypting 2.5” hard drives with remote management,strong authentication, and extensive auditing and reporting features, thusallowing companies to more easily implement Seagate hardware encryption. FDE DriveManager can be configured during installation to run as amanaged or unmanaged client.Figure 3 - CREDANT Drive ManagerFigure 2 - CREDANT Mobile Guardian CREDANT Protector offers fine-grained port control capabilities toorganizations wishing to control data at the device or file level. CREDANT FDE for Windows provides full disk software encryption forWindows laptops and desktops. All data on the local drive is encryptedat the sector level, including any blank space on the drive. This fullymanaged solution includes mandatory, pre-boot authentication andAES-256 encryption. CREDANT’s network-aware pre-boot authentication allows the end user to access the system via an existing domainlogin. Administrators avoid the high overhead setup and maintenance ofproprietary pre-boot user and administrator accounts.February 2012 SeriesAs business environments differ, so do the options CREDANT offers tosecure critical data in those environments. All CREDANT solutions aredesigned to provide the most comprehensive security available for datastored on laptops, desktops, removable media and mobile devices. Eachsolution ensures mandatory authentication and provides industry-standardencryption so organizations can select a product or a combination ofproducts that best fit their needs without having to go to multiple vendors.CREDANT’s broad range of solutions helps to keep corporate data securewhile allowing users to focus on doing their jobs.CREDANT Product Overview4
CREDANT DeploymentWorkflowFigure 4 - CREDANT Policy DefinitionThis section presents an overview of the tasks involved in deployingCREDANT data security products.Phase 1: Environment Planning and ReviewThis phase of the deployment workflow involves a review of the organization’s current environment, including software deployment, client types,encryption requirements, and authentication methods. This environmentalreview is necessary to determine how the software will be deployed, whichclient types should be considered (software FDE, hardware FDE, file-basedencryption, and/or removable media), the number of servers that arerequired, and what authentication methods will be used.Phase 2: Server Software InstallationThis phase involves the installation of the server software that will providethe management of the various endpoint encryption solutions. This processincludes the creation of the database, which will be used to escrow theencryption keys, configuration of the authentication and directory systems,and the installation of the policy server. Most deployments include a singlepolicy server, one active database and connectivity to Active Directory.Management is accomplished using either a web browser or MicrosoftManagement Console plug in.Phase 4: Client InstallationThis phase of the deployment workflow involves the deployment of the clientto the endpoint. There are several different client types to choose from,and in most cases the client can be deployed using the customer’s normalsoftware delivery systems. After the client is deployed to the endpointand activated, the encryption keys are created by the server, stored in thedatabase, and passed to the client. The policies created in phase three arethen consumed by the client and the encryption process takes place.Figure 5 - Client Configuration OptionsPhase 3: Policy DefinitionThis phase involves the creation of the security policy. As customers tendto have a wide variety of encryption requirements, this part of the processhelps ensure that those requirements are met. CREDANT works closely withthe customer to build a policy that meets the growing number of governmentregulations and industry standards that require encryption. These mightinclude HIPAA, PCI, SOX, and various Federal and State Breach Laws. Thepolicies are designed to meet these requirements while having very littleimpact to the end user. Figure 4 shows the policy management interface:February 2012 SeriesCREDANT Deployment Workflow5
Figure 6 - Client Policy ConfigurationPhase 5: Auditing and ReportingThis phase of the deployment workflow involves the installation and configuration of the Audit and Reporting tools. This involves the installation ofsoftware on the policy server, and the configuration of a connection to thedatabase. The software has many pre-defined reports, as shown in Figures 7and 8, but most customers will want to customize these reports to meet theirindividual needs. Reports are customized and then scheduled during thisphase. Configuration of the audit and reporting system also includes roledefinition for auditors, and setting up reports to be emailed to various users.Figure 7 - Per-Device Statistics in the Reporting InterfaceFigure 8 - Predefined ReportsPhase 6: Data Lifecycle Protection withCisco AnyConnect and RSA Endpoint DLPCREDANT Mobile Guardian, Cisco AnyConnect VPN, and RSA Endpoint DLPtogether provide comprehensive protection of data in at rest, in use, andin motion. Deployment and use of CREDANT Mobile Guardian is transparent, and works seamlessly when used with RSA DLP Endpoint and CiscoAnyConnect VPN.Cisco AnyConnect provides a secure transmission pipe to protect information as it travels between enterprise environments and end users.Sensitive data stored on the user’s notebook hard drive is protected viaCREDANT’s encryption solution. Data written to USB drives may be monitored and logged via RSA Endpoint DLP, and simultaneously encrypted withCREDANT’s USB encryption capabilities. To that end, administrators may setappropriate DLP Endpoint policies to log all transfer events to have a clearunderstanding of what is being written to external media, Credant encryption policies to ensure that all data is encrypted on USB drives.Taken together, these three solutions enable mobility while offering thehighest degree of data security.Products Verified with Cisco Smart BusinessArchitectureCREDANT Mobile Guardian Enterprise Server 6.7.0.188 and CREDANTMobile Guardian Shield 6.7.0.1402 are validated across Cisco SmartBusiness Architecture with Cisco AnyConnect 2.5.0.217.February 2012 SeriesCREDANT Deployment Workflow6
How to Contact UsEnd Users Please contact CREDANT via http://www.credant.com/cisco forany questions. Submit an inquiry about CREDANT and the Cisco Smart BusinessArchitecture—Borderless Networks for Enterprise Organizations.Resellers Please contact CREDANT via http://www.credant.com/partners.html.February 2012 SeriesHow to Contact Us7
SMART BUSINESS ARCHITECTUREAmericas HeadquartersCisco Systems, Inc.San Jose, CAAsia Pacific HeadquartersCisco Systems (USA) Pte. Ltd.SingaporeEurope HeadquartersCisco Systems International BVAmsterdam, The NetherlandsCisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco Website at www.cisco.com/go/offices.Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use ofthe word partner does not imply a partnership relationship between Cisco and any other company. (1110R)C07-608456-03 02/12
CREDANT FDE for Windows provides full disk software encryption for Windows laptops and desktops. All data on the local drive is encrypted at the sector level, including any blank space on the drive. This fully managed solution includes mandatory, pre-boot authentication and AES-256 encryption. CREDANT's network-aware pre-boot authentica -