Transcription
Revised ByApproved ByAnders StaafJohan ForsbergTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10OpenSecurity Target – Clavister cOS CorePage1/49
Revised ByApproved ByAnders StaafJohan ForsbergPageTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open2/49DOCUMENT HISTORYVersionStatusIssue dateRevision descriptionEdited byAApproved2016-10-07First versionAnders StaafB1Draft2016-10-21Clarified hardware crypto acceleratorAnders StaafB1-2Draft2017-03-06RSA key length corrected.Neal SutherlandBApproved2017-03-06QA performed.Anders StaafC1Draft2017-08-03Software version and crypto library changed.Minor corrections.Anders StaafC1-spDraft2017-08-04Editorial changes.Neal SutherlandC2Draft2017-08-14Adopted to CC version 3.1 revision 5.Anders StaafCApproved2017-08-15QA performed.Anders StaafD1Draft2017-08-29Addressed the evaluator’s comments. Addedbinary identifiersAnders StaafD1-1Draft2017-08-30Changed the hardware devices listed.Neal SutherlandD1-2Draft2017-08-30Changed the hardware devices build list.Johan ForsbergD1-3Draft2017-09-06Fixed the mis-aligned headerNeal SutherlandD1-4Draft2017-09-07CleanupJohan ForsbergDApproved2017-09-12QA performed.Anders StaafEApproved2017-11-08Addressed the evaluator’s comments. QAperformed.Mattias Fredriksson,Anders StaafFApproved2017-11-23Addressed the certifier’s comments. QAperformed.Johan Forsberg,Mattias Fredriksson,David Henriksson,Anders Staaf,G1Draft2017-11-28Added revision A and B for E80 and W20.Corrected CC reference.Anders StaafGApproved2017-11-28QA performed.Anders StaafHApproved2018-10-05Addressed certifier’s comment on NAT/SAT.Anders StaafIApproved2019-01-29Addressed certifier’s comment on virtualappliance.Anders StaafJApproved2019-06-10Addressed certifier’s comment on guidancereference.Anders Staaf
Revised ByApproved ByAnders StaafJohan ForsbergPageTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open3/49Contents1ST Introduction . 51.1ST Reference . 51.2TOE Reference . 51.3Document Overview . 51.4TOE Overview . 51.5TOE Description . 61.5.1Product Overview . 61.5.2System Overview . 61.5.3Physical Scope . 71.5.4Logical Scope . 81.5.5Physical/Logical Features and Functionality not Included in the TOE . 91.5.6Interfaces . 101.5.7Configuration and Modes. 101.5.8Roles . 102Conformance Claims . 112.1CC Conformance Claim . 112.2PP Conformance Claims . 112.3Package Conformance Claims . 113Security Problem Definition . 123.1Introduction . 123.2Threats . 123.2.1Assets . 123.2.2Threat Agents . 123.2.3Threats . 133.3Organizational Security Policies . 133.4Assumptions. 144Security Objectives . 154.1Introduction . 154.2Security Objectives for the TOE . 154.3Security Objectives for the Operational Environment . 164.4Security Objectives Rationale . 174.4.1Security Objectives Coverage . 174.4.2Security Objectives Sufficiency . 185Extended Components Definition . 206Security Requirements . 21
Revised ByApproved ByAnders StaafJohan ForsbergTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open6.1Page4/49Security Functional Policies . 216.1.1Access Rule SFP . 216.1.2IP Policy SFP . 216.1.3Authenticated Information Flow SFP . 226.2Security Functional Requirements . 226.2.1Conventions. 226.2.2Summary . 226.2.3Security Audit – FAU . 236.2.4Cryptographic Support – FCS. 266.2.5User data protection - FDP . 276.2.6Identification and authentication – FIA . 306.2.7Security management – FMT . 316.2.8Protection of the TSF - FPT . 336.2.9TOE access - FTA . 346.2.10Trusted path/channels – FTP . 346.3Security Assurance Requirements . 366.4Security Requirements Rationale . 376.4.1Security Functional Requirements Dependencies . 376.4.2Security Assurance Dependencies Analysis. 396.4.3Security Functional Requirements Coverage . 406.4.4Security Functional Requirements Sufficiency . 416.4.5Justification of the Chosen Evaluation Assurance Level. 4377.1TOE Summary Specification. 44TOE Security Functions . 447.1.1Security Audit . 457.1.2Trusted Channel . 457.1.3User Data Protection . 467.1.4Identification and Authentication . 467.1.5Security Management . 467.1.6Protection of the TOE Security Function (TSF) . 467.1.7TOE Access. 46Appendix A – Abbreviations and Acronyms . 47Appendix B - Referenced Documents . 49
Revised ByApproved ByAnders StaafJohan ForsbergTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open1ST Introduction1.1ST ReferenceTitle:Security Target – Clavister cOS CoreVersion:JDate:2019-06-10Editor:Anders Staaf, Combitech AB1.25/49TOE ReferenceTarget of Evaluation:Clavister cOS 0.00.34-31986Developer:Clavister AB1.3PageDocument OverviewThis is the Security Target for the Clavister cOS Core software.Chapter 1 gives a description of the ST and the TOE. This description serves as an aid to understand the securityrequirements and the security functions.Chapter 2 states the conformance claims made.In chapter 3, the security problem definition of the TOE is described. This includes assumptions about the environmentof the TOE, threats against the TOE, TOE environment and organizational security policies that are to be employed toensure the security of the TOE.The Security Objectives stated in chapter 4 describes the intent of the Security Functions. The Security Objectives aredivided into two groups of security objects, for the TOE and for the TOE environment.No extended components are defined so chapter 5 is empty.In chapter 6 the IT security functional and assurance requirements are stated for the TOE. These requirements are aselected subset of the requirements of part 2 and 3 of the Common Criteria standard.A brief description of how the security functional requirements are implemented in the TOE is described in chapter 7.1.4TOE OverviewThe TOE is the Clavister cOS Core, 12.00.00, the base software engine that drives and controls the range of ClavisterSecurity Gateway hardware products. cOS Core can also be deployed as a virtual machine on the customer’s preferred
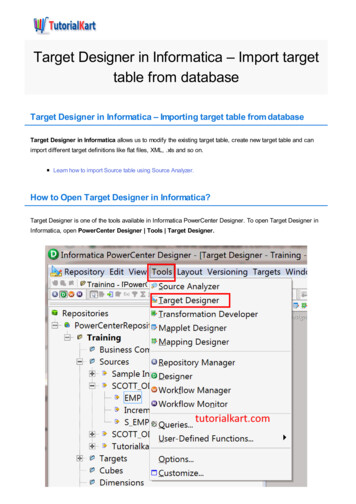
Revised ByApproved ByAnders StaafJohan ForsbergPageTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open6/49choice of server hardware. The TOE is a Next Generation Firewall software, offering stateful firewall with deep-packetinspection functionality.1.5TOE Description1.5.1Product OverviewDesigned as a network security operating system, cOS Core features high throughput performance with high reliabilityplus super-granular control.The TOE includes Next Generation stateful firewalling with packet inspection functionality, IP Policies with and withoutuser authentication, logging to a syslog server and secure remote management via HTTPS. cOS Core also offers otherfeatures not included in this evaluation, such as Application Control, Content Security Services, User IdentityAwareness, Dynamic Routing, Ipsec, SSL VPN, Intrusion Detection and Prevention, Anti-Virus, High Availability and acentralized management solution.1.5.2System OverviewThe system configuration is comprised of an internal, trusted network, external, untrusted network, managementnetwork, and a local management console, as illustrated in Figure 2.Figure 1, TOE configuration
Revised ByApproved ByAnders StaafJohan ForsbergTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open1.5.3Page7/49Physical ScopeThe TOE is the base software engine that drives and controls dedicated hardware appliances or as a virtual deploymentin a virtual machine environment. The TOE binary is pre-loaded or downloaded from Clavister’s web site.BinaryDeployment12.00.00-31984Vmware Virtual machine12.00.00-31985Clavister E20, E80 revision A, E80 revision B, W20 revision A, W20revision B, W30 and W4012.00.00-31986Clavister W50Table 1, Deployment of binariesGuidance DocumentationThe following guides are required reading and are a part of the TOE:-Clavister cOS Core Administration Guide, Version: 12.00.00-Clavister cOS Core CLI Reference Guide, Version: 12.00.00-Clavister cOS Core Log Reference Guide, Version: 12.00.00-Guidance Documentation - Clavister cOS Core, version HThe guides are available in pdf format to download from Clavister’s web site.1.5.3.1 Non-TOE Hardware/Software/FirmwareThe TOE environment consists of the components listed below in Table 2. Table 2 specifies the minimum systemrequirements for the proper operation of the TOE.ComponentRequirementManagement ConsoleGeneral purpose computer with serial interface (COM-port)Management Web interfaceGeneral purpose computer with web browser for HTTPSmanagement sessions.Syslog ServerGeneral purpose computer with Syslog server compliant with RFC5424 as a minimum.AppliancesClavister E20, E80 revision A, E80 revision B, W20 revision A, W20revision B, W30, W40, and W50Virtual deploymentVmware vSphere (ESXi)Table 1, Non-TOE hardware/software/firmwareVmware minimum specification: Vmware ESXi version 5.5. Version 6.5 recommended.1024MB guest RAM. 2048MB guest RAM recommended.
Revised ByApproved ByAnders StaafJohan ForsbergTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open 1.5.4Page8/492GB guest storage.Logical ScopeThe logical boundary of the TOE will be broken down into security functions describing the security features of the TSF.The security functional requirements are stated in chapter 6 and the security functions are further described in chapter7 of this ST.-Security Audit-Cryptographic Support-User Data Protection-Identification and Authentication-Security Management-Protection of the TOE Security Function (TSF)-TOE Access1.5.4.1 Security AuditThe TOE generates audit records for start-up and shutdown of the audit functions, blocked traffic, administrator accountactivity, firewall activity, firewall rule modification, network access, login attempts, etc.Audit records are stored locally in memory and are exported to a Syslog server.Administrators can select the severity level to be logged and include/exclude specific events.The oldest record in the local memory based audit trail is overwritten when the trail space is full.1.5.4.2 Cryptographic SupportThe TOE provides TLS functionality for HTTPS communication to the Management Web interface. The library MbedTLSis used for cryptographic operations.Hardware cryptographic acceleration may be enabled on the Clavister appliances or in the virtual machine environmenthosting the TOE. Hardware cryptographic acceleration is not included in the TOE.Keys and key material will be zeroized when no longer needed.1.5.4.3 User Data ProtectionThe TOE controls network traffic via Information Flow Control Security Functional Policies (SFPs). The Access RuleSFP filter network traffic based on IP addressed and network interfaces. The IP Policy SFP filter network traffic basedon source and destination network interfaces, source and destination IP networks and the Service (protocol) by statefulinspection. The Authenticated Information Flow SFP requires users to be authenticated to send information fromspecified source network addresses and/or access resources on destination network addresses.
Revised ByApproved ByAnders StaafJohan ForsbergPageTitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open9/491.5.4.4 Identification and AuthenticationAuthentication without identification is required for management through the local Console port. The Management Webinterface and the Management CLI interface requires identification and authentication using username and password.The Authenticated Information Flow SFP requires the user to identify and authenticate through username andpassword.1.5.4.5 Security ManagementThe TSF recognizes three roles: Admin, Audit and Authenticated User. The Admin and Audit roles have managementprivileges while the Authenticate User only have privileges related to the Authenticated Information Flow SFP. TheAdmin may query, modify, and delete attributes associated to the Information Flow SFPs, query and modify the TOEconfiguration and the set of events to be audited. The Audit may query the same entities. Both Admin and Audit mayquery TOE and device status information. The Admin may also restart the TOE.1.5.4.6 Protection of the TOE Security Function (TSF)The TOS shall perform self-tests at during initial start-up and tests of the operation of underlying device entities maybe initiated by administrators.A secure state shall be preserved when failures occurs and are discovered by self-tests or tests of external entities.1.5.4.7 TOE AccessOnly one Admin may be authenticated at the same time. Subsequent administrator authentications will grant Auditprivileges only. More than one Audit may be authenticated concurrently.User sessions may automatically be terminated after a configurable time of inactivity and/or total session lifetime1.5.5Physical/Logical Features and Functionality not Included in the TOEFeatures/Functionality that are not part of the evaluated configuration of the TOE are:-Authentication using other methods than local username and password validationSSH based Management CLI interfaceSecure Copy, SCPClavister InControl management interfaceSMTP and InControl log receivers, SNMP trapsSNMPSoftware updateHigh Availability (HA) configurationVPNIntrusion Detection & PreventionAnti-VirusAnti-Spam
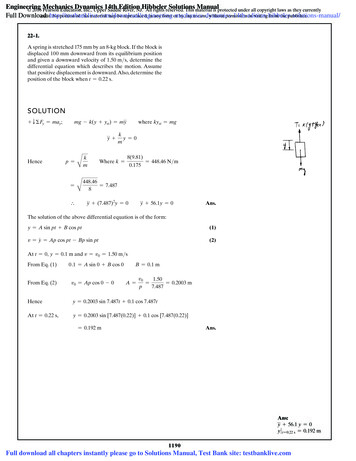
-Revised ByApproved ByPageAnders StaafJohan Forsberg10/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10OpenTraffic/Bandwidth ManagementRootingHardware crypto accelerator1.5.6InterfacesFigure 2 illustrates the TOE interfaces. Management can be performed by authenticated administrators locally, throughthe Console port, or remote over HTTPS for the Web interface.Figure 2, TOE interfaces1.5.7Configuration and Modes1.5.8RolesThere are three roles with privileges in the TOE:Admin -Has full management authority with read/write privileges on the TOE configuration. Admin isauthenticated through the Console or the remote management interfaces.Audit -The Audit role is for monitoring purposes only and has read-only privileges. Audit isauthenticated through the Console or the remote management interfaces.Authenticated User -Has privileges to send and receive user data information through the TOE according to rulesset up in a Security Functional Policy.The Admin and Audit roles are collectively called administrators further on in this document.
Revised ByApproved ByPageAnders StaafJohan Forsberg11/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open2Conformance Claims2.1CC Conformance ClaimThis Security Target is CC part 2 conformant and CC part 3 conformant to Common Criteria version 3.1, revision 5.–Part 1: Introduction and general model, April 2017, Version 3.1, Revision 5, CCMB-2017-04-001–Part 2: Security Functional Components, April 2017, Version 3.1, Revision 5, CCMB-2017-04-002–Part 3: Security Assurance Components, April 2017, Version 3.1, Revision 5, CCMB-2017-04-003The guidance from ISO/IEC JTC 1/SC 27 N 2449 Information technology – Security techniques – Guide for theproduction of protection profiles and security targets has been used when developing this Security Target.2.2PP Conformance ClaimsThis Security Target does not claim compliance to any Protection Profile.2.3Package Conformance ClaimsThis Security Target claims conformance to assurance requirement package EAL4 augmented by ALC FLR.1.
Revised ByApproved ByPageAnders StaafJohan Forsberg12/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open3Security Problem Definition3.1IntroductionThe security problem definition described below includes threats, organizational security policies and security usageassumptions.3.2ThreatsThreats are described by an adverse action performed by defined threat agents on the assets that the TOE has toprotect. The assets and their protection needed, the threat agents and their attack potential, and the threat adverseactions are described below.3.2.1AssetsThe following types of Assets are protected by the TOE.AssetDescriptionUser DataUser information and IT resources, within the network perimeterof the TOE.TSF DataThe TOE software, configuration files and other system files.Table 2, Assets3.2.2Threat AgentsThe following types of Threat Agents are foreseen.Threat AgentDescriptionAttackerPersons or external IT entities unauthorized to use the TOE. TheAttacker possess:– Public knowledge of how the TOE operates and of potentialmethods of attacking the TOE.– Not unlimited resources.– No physical access, but unlimited access to the TOE externalnetwork interface.TOE UsersPersons authorized to use the TOE. The TOE Users possess:– Extensive knowledge of how the TOE operates.– High skill level.– Physical access to the TOE.However TOE Users are not willfully hostile, educated, followstheir guidance, but still capable of doing mistakes.Table 3, Threat agents
Revised ByApproved ByPageAnders StaafJohan Forsberg13/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open3.2.3ThreatsThe threats against the TOE are identified according to Table 4.ThreatAssetsDescriptionT.NETWORK ACCESSUser Data,TSF DataAn Attacker may attempt to bypass the informationflow control policy by sending information throughthe TOE, which results in exploitation and/orcompromise of protected resources on the internalnetwork.T.UNDETECTEDUser Data,TSF DataAn Attacker may attempt to compromise the assetswithout being detected. This threat includes theAttacker causing audit records to be lost or preventfuture records from being recorded by takingactions to exhaust audit storage capacity, thusmasking the Attacker’s actions.T.ADMIN ACCESSTSF DataThe Attacker may attempt to gain administratoraccess to the TOE through illicit authentication.T.ADMIN COMMUNICATIONTSF DataThe Attacker may be able to view, modify, and/ordelete security related information sent between aremotely located authorized administrator and theTOE.T.BYPASSUser Data,TSF DataThe Attacker may attempt to bypass, deactivate, ortamper with TOE security functions to causeunauthorized access to TOE functions, user or TSFdata, or to deny access to legitimate users.T.HALTTSF DataThe Attacker may attempt to compromise thecontinuity of the TOE functionality by haltingexecution of the TOE.T.FAILUREUser Data,TSF DataA component of the TOE or in TOE operationalenvironment may fail during start-up or duringoperations, or a TOE User may involuntarilycausing a compromise or failure in the securityfunctionality and leaving the TOE susceptible toattackers.Table 4, Threats against the TOE3.3Organizational Security PoliciesOrganizational security policies, OSPs, for the TOE are stated according to Table 5.OSPDescriptionP.MANAGEThe TOE shall be manageable only by authorizedadministrators.P.ACCOUNTABLEThe TOE shall provide audit records to hold administratorsaccountable for their actions.Table 5, Organisational Security Policies for the TOE
Revised ByApproved ByPageAnders StaafJohan Forsberg14/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open3.4AssumptionsAssumptions on the TOE operational environment are made according to Table 6.AssumptionDescriptionA.NO GENERAL PURPOSEThe TOE underlying platform is assumed not to provide generalpurpose computing capabilities.A.TRUSTEDADMINISTRATORAuthorized administrators are assumed to be non-hostile and toact in the best interest of security for the organization. Thisincludes being appropriately trained, following given policies, andadhering to guidance documentation. However, they are capableof making mistakes.A.PHYSICAL SECUREThe TOE is operated in a physically secure environment, i.e., nounauthorized person has physical access to the TOE or itsunderlying platform.A.SINGLE CONNECTIONInformation cannot flow among the internal and externalnetworks unless it passes through the TOE.A.AUDIT SERVERIt is assumed that an external audit server can receive and storeaudit events from the TOE.A.TIMEThe TOE environment provides the TOE with a reliable timestamp.A.VIRTUAL DEPLOYMENTOnly one instance of the TOE is executing as a guest in thevirtual deployment. No other applications are running as guestsin the TOE virtual deployment.Table 6, Assumptions on the TOE environment
Revised ByApproved ByPageAnders StaafJohan Forsberg15/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open4Security Objectives4.1IntroductionThe statement of security objectives defines the security objectives for the TOE and its environment. The securityobjectives intend to address all security environment aspects identified. The security objectives reflect the stated intentand are suitable to counter all identified threats and cover all identified organizational security policies and assumptions.The following categories of objectives are identified: The security objectives for the TOE shall be clearly stated and traced back to aspects of identified threats to becountered by the TOE and/or organizational security policies to be met by the TOE. The security objectives for the environment shall be clearly stated and traced back to aspects of identifiedthreats countered by the TOE environment, organizational security policies or assumptions.4.2Security Objectives for the TOEThe following security objectives for the TOE are defined.Security ObjectiveDescriptionO.RESTRICTED ACCESSThe TOE must mediate the flow of all information and upheld theinformation flow control policy between the internal and externalnetworks governed by the TOE.O.AUDITThe TOE must be able to provide an audit trail of security relevantevents. An authorized administrator must be allowed to configurethe security relevant events to be audited.O.AUTHENTICATIONThe TOE must be able to identify and authenticate authorized usersprior to allowing access to TOE security management functions.O.SECURE COMMThe TOE must protect the confidentiality and integrity and ensurethe authenticity of data passed between itself and an authorizedadministrator.O.BYPASS PROTECTIONThe TOE must protect itself against attempts by attackers tobypass, deactivate, or tamper with TOE security functions in such away as to cause unauthorized access to TOE functions, User orTSF data, or to deny access to legitimate users.O.FAILURE PROTECTIONThe TOE must protect the assets against security breaches causedby accidental failures of the TOE security functions or componentsin the operational environment upon which the TOE depend.O.MANAGEThe TOE shall be manageable only by authorized administrators.Table 7, Security objectives for the TOE
Revised ByApproved ByPageAnders StaafJohan Forsberg16/49TitleDocument TypeLast EditedSecurity ClassSecurity Target Clavister cOS CoreSecurity Target2019-06-10Open4.3Security Objectives for the Operational EnvironmentSecurity ObjectiveDescriptionOE.NO GEN PURPOSEThe TOE underlying platform must not to provide generalpurpose computing capabilities.OE.TRUSTED ADMINAuthorized administrators must be non-hostile and to act in thebest interest of security for the organization. This includes beingappropriately trained, following given policies, and adhering toguidance documentation. However, they are capable of makingmistakes.OE.PHYSICAL SECUREThe TOE must be operated in a physically secure environment,i.e., no unauthorized person shall have physical access to theTOE or its underlying platform.OE.SINGLE CONNInformation must not flow among the internal and externalnetworks unless it passes through the TOE.OE.AUDIT SERVERAn external audit server must be able to receive and store auditevents from the TOE.OE.TIMEThe TOE environment must provide the TOE with a reliable timestamp
Security Target Clavister cOS Core Security Target 2019-06-10 Open 1 ST Introduction 1.1 ST Reference Title: Security Target -Clavister cOS Core Version: J Date: 2019 - 06 1 Editor: Anders Staaf, Combitech AB 1.2 TOE Reference Target of Evaluation: Clavister cOS Core Version: 12.00.00.34-31984 12.00.00.34-31985 12.00.00.34-31986