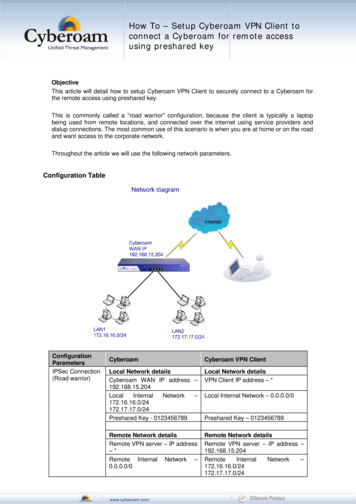
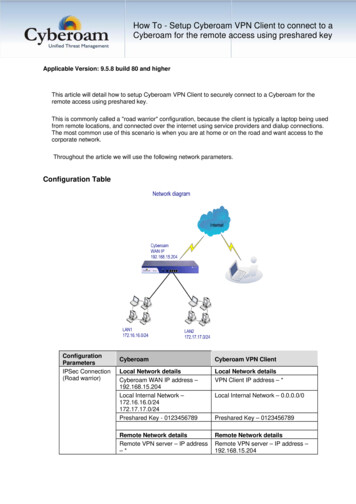
Transcription
Cyberoam UTM(CR Series)Vs.SonicWALL UTM(TZ , Pro , NSA Series)Cyberoam CertificationsWestcoast Labs Checkmark Certification:UTM Level 5Categories: Enterprise Firewall VPN Anti-Virus and Anti Spyware Gateway Premium Level Anti-Spam IPS URL FilteringICSA CertificationCategory:Corporate Firewall with Active- Active HighAvailabilityAwardsWinner of 2008/2009 ZDNet AwardCategory: IT Leader Asia's Most Promising AsianTechnoVisionariesProduct ReviewSonicWALL Anti Spam PC Pro Recommended UTM Techworld Recommended UTM SC Magazine : Cyberoam UTMOverall Rating: ÌÌÌÌÌ - 5 Stars SC Magazine : Best Buyservice charges permailbox rather than flatpricingCyberoam UTM is Certified byVirtual Private NetworkConsortium (VPNC) : Basic Interop AES Interop SSL Portal SSL Firefox SSL Java Script SSL Basic Network Extension SSL Advanced Network ExtensionCyberoam in NumbersHwww.cyberoam.comWorld wide PresenceDeployed in 90 countriesNumber of Anti Virus Signatures2 MillionVirus Detection Rate100%Spam Detection Rate98%False Positive Rate1 in One MillionNumber of URL categories82
Cyberoam’s Anti Virus vs. SonicWALL Anti Virus:Cyberoam has an OEM with Kaspersky Lab for Gateway Anti Virus, which is one of theindustries leading Anti Virus Solution.SonicWALL has a proprietary gateway anti virus engine.In 2009, public test of different anti-virus vendors all out to see how they really comparetook place.While Kaspersky topped with 100%, SonicWALL was dragging its feet with 81% detectionrate.Anti Virus %Virus Detection RateCyberoam (Westcoast Labs)SonicWALL(TZ 210) (Tolly)Cyberoam also has a User based Self Service Quarantine area for virus which SonicWALLdoes not have.Cyberoam’s Real-Time RPD Anti Spam TechnologyCyberoam’s RPD technology focuses on detecting recurrent message patterns inoutbreaks. Message patterns are extracted from the message envelope, headers, andbody. Patterns are extracted in real time from the message hashes being continuouslysent to the detection centers.Cyberoam has a User based Self Service Quarantine area, so that no business mails arelost to security.Anti Spam Statistics:1. Cyberoam’s Spam Detection Rate is industry’s best: 98%2. Cyberoam’s False Positive Rate is : 1 in 1 MillionSonicWALL: Poor Anti SPAMThe anti spam service being launched is now an admission by SonicWALL about the lack ofAnti Spam features on its appliances.The anti spam engine is still a combination of many engines such as AdversarialBayesian, image inference analysis etc which have their limitations and should be nowconsidered obsolete with respect to the RPD and IP reputation services being used in
Cyberoam.The worst thing about this Anti Spam service is that it is actually a service that is chargedper mailbox rather than flat pricing that is the norm today.Another fact to be considered is that the Anti Spam engines reside on the cloud ratherthan the appliance and most of the processing is done on the network, so appliance isjust a medium for the service rather than a subscriptionGiven below is comparison chart for anti spam service.SonicWALLCyberoamCheckmark certificationNoYes (Premium Level)Language and Content independentanti spam engineNoProtocol supportSMTPSMTP, POP3, IMAPDetection rate98%98%YesCyberoam Minimizes the Window of VulnerabilityCyberoam provides proactive protection against new email-borne virus outbreaks, hoursbefore the signatures are released. It has empowered with the proactive virus detectiontechnology which detects and blocks the new outbreaks immediately and accurately.It provides a critical first layer of defense by intelligently blocking suspicious mails duringthe earliest stage of a virus outbreak.
Bandwidth Management vs. Bandwidth ControlCyberoam gives Bandwidth Management that is a full fledge user–based policy levelmanagement designed to provide:1.2.3.4.5.6.Guaranteed or burst-able bandwidthFlexible, prioritized, bidirectional rulesRules for Users, Groups, IP addressesWeb Category based bandwidth managementTransparency for end usersDetailed and comprehensive bandwidth reportsSonicWALL UTM on the other hand provided preconfigured options from Firewall QoSMapping option. The options are not self explanatory.Cyberoam’s User-based Multiple IPS PoliciesUser-based flexible multiple policies are supported by Cyberoam UTM only and not bySonicWALL.SonicWALL does not support Custom IPS signatures.Cyberoam Reporting – Free User FriendlyIn SonicWALL, the customer needs to purchase and deploy ViewPoint software to getdetailed reporting. This is a steep escalation in terms of Capital Expenditure andOperational Expenditure.Cyberoam’s On-Appliance Plug-and-Play reporting provides detailed reports.Some unique Cyberoam Reports include:1. User-wise reports of all types (Web Filtering, Internet Surfing, IPS)2. User-wise Data Transfer3. User-wise Search Keywords (reports of web searches)4. Web Surfing Trends reports as per: User, Organization, Site, Category(graphicalreports)5. Compliance reporting comprising of: HIPAA, GLBA, SOX, PCI, FISMA
Cyberoam iView - Open Source Logging and Reporting SolutionTaking a step ahead of competitors, Cyberoam also provides external reporting forCyberoam as well other products with the help of Cyberoam iView.Cyberoam iView is an open source logging and reporting solution that providesorganizations with visibility into their networks across multiple devices for high levels ofsecurity, data confidentiality while meeting the requirements of regulatory compliance.Enabling centralized reporting from multiple devices across geographical locations,Cyberoam iView offers a single view of the entire network activity with the help of 1000 unique reports.Refer to www.cyberoam-iview.org for further details.
Head-to-Head Comparison:Points to PonderSonicWALL UTMCyberoam UTMEnhanced FirewallDecision Matrix:SonicWALL UTM does notuse identity as aparameter in the firewalldecision matrix.Cyberoam extends thefirewall’s rule matching criteriato include schedule and theuser’s identity.Firewall is a primary securitycomponent in networksecurity.Similarly, the firewall actionsare extended to includecomplete policy based controlover all the security solutionslike, content filtering, IPS,Internet access management,bandwidth management andanti-virus and anti-spam scan.A normal decision matrix ina firewall stops at the IPaddress of a machine.In the blended threatscenario, social engineeringis used to target the weakestlink – end user. So a user’sidentity becomes animportant decision andcontrol parameter in thefirewall matrix.State-of-Art Identitybased AccessManagement:IAM is a combination ofIdentity, time schedulingand access management.This is a powerful controlmechanism which reachesdown to all the securityfeatures in a UTM. Identityand time schedule are thetwo dimensions used todefine a user’s real timeidentity in a securitysolution.Centralized point of UTMManagement:Aggregation of securitysolutions is not enough. AUTM should be easilymanageable. This makes ituser friendly and thelearning curve of the enduser remains low.SonicWALL UTM does notuse Identity as aparameter in the firewalldecision matrix.Cyberoam’s Identity-basedaccess management featureprovides unparalleled flexibility,security and control to thenetwork administrator over theend user.Cyberoam also facilitates theuser to implement combinationof security parameters as IPAddress, Identity, and MACAddress, firewall decisionmatrix.SonicWALL UTM does nothave this flexibility andease of use.Cyberoam is manageablethrough its single firewall page.It is designed to provide acentral management of allmember security packages ofthe UTM. In a few clicks, youcan have custom policy to meetany security demand.
Points to PonderSonicWALL UTMCyberoam UTMEnhanced ApplicationFirewallSupports applicationfirewallApplication Firewall ispart of IPS with 3500 SignaturesApplication basedBandwidth Management ispart of productroadmap deliverable inApplication firewall monitors,controls and blocksapplications and services(input, output, or systemservice calls) which do notmeet the configured policy ofthe firewall.April.To secure the organization’snetwork from blendedinternal and externalthreats, company needsapplication firewallWorld Wide Honey PotBack BoneRequirement to secure thenetwork from blendedInternet threats is rising dayby day.Network security companiesneed access to malware andspam outbreaksinstantaneouslyTo achieve this there is aneed of world wide honeypot network.SonicWALL machinesworld wide acts as securityagents.Cyberoam has installation in 90different countries and allCyberoam appliances updatethe information about newvirus and spam attacks tocentral office.
Points to PonderSonicWALL UTMCyberoam UTMPurpose built HardwareSonicWALL supports VPNaccelerators and multicorearchitectures.Cyberoam supports 64 bithardware platforms based onbusiness purpose.Purpose built hardwarestrengthens and speeds upthe security softwareinstalled on it.Cyberoam provides flash-basedUTM appliances series withHDD based appliances.A SOHO appliance andenterprise appliance mighthave different security needsand the hardware shouldreflect the business purposeof security.Cyberoam SOHO appliancescome with VPN accelerator toprovide higher performance.Cyberoam higher endappliances are based onmulticore threat scalablearchitecture.The key feature of theCyberoam architecture is itsability to adapt to new threatswhile maintaining a predictablelevel of performance and highlevel of security.Business Friendly AntiVirus /Anti Spam Scans:For most users, missing alegitimate email is an orderof magnitude worse thanreceiving spam or virus.SonicWALL UTM does notprovide any such controlover its AV and AS scans.Cyberoam UTM has an OEMlicense from Kaspersky’sGateway AV. Similarly,Commtouch RPD Anti-spamtechnology (OEM) is used inCyberoam.To avoid such an unpleasantsituation you need to controlthe parameters used toclassify a mail as spam orvirus infected and thenecessary action.No separate AMCs are levied.User-based customizedscans can ensure that not asingle mailed businessopportunity is lost tosecurity.You have the flexibility toconfigure a scan as per yourneeds, rather than adjustingyourself to the way a securitysolution operates.Using Cyberoam UTM you candefine custom scan rules basedon sender or recipient, IPaddress, mime header andmessage size.
Points to PonderSonicWALL UTMCyberoam UTMSelf-service Anti Virus/Anti Spam QuarantineArea:SonicWALL UTM does nothave this feature.The Self-service quarantinearea from Cyberoam UTMenables individual mailrecipients to view and managetheir infected / Spammessages.Quarantine area is a safeholding area for allsuspicious/ infected files.This allows organizations toremove infected files fromgeneral circulation withoutdeleting them.The self-service featureremoves user’s dependency onadministrator to managequarantine mails.A gateway quarantine areashould be self-service asthere are a large number ofusers involved. So the usersought to get notified that amail has been quarantinedand he can access and dealwith it without depending onthe administrator.Superior Spam Filtering:In 2007, the spamproliferation has increasedby 35% per year and 99% ofall emails was spam. Imageand Instant Messagingbased spam (spim) canprove to be a major drain onmail storage and employeeproductivity. Spim blockagerequires specialized antispam filters.SonicWALL UTM has permail box based anti spamengine using almostobsolete technologies asAdversarial Bayesian,image inference analysisetcCyberoam has an OEM withCommtouch Software Ltd.Recurrent Patterns Detection(RPD) technology, based on theidentification and classificationof message patterns deliversthe industry’s best and highestspam and threat detectioncapabilities providing protectionfrom all types of email-bornethreats.Cyberoam watches over SMTP,POP3 and IMAP protocols forSpam. This providescomprehensive anti-spamcover.
Points to PonderSonicWALL UTMCyberoam UTMProtection AgainstPhishing and Pharming:SonicWALL does not havePharming protection.Cyberoam UTM protectsagainst Phishing and Pharming,both. Its Anti Spam technologyand WEBCat databaseeffectively mitigate Phishingthreats.Phishing and Pharming arethe next generation threatsinstigating the end users tobreech the network securityfrom within. Phishing is apassive baiting through mailand Pharming is an activeprocess of host filecorruption which leads theuser unknowingly to amalicious site.Security Readiness:Security is not a solution foryesterday’s problems. It isall about present and future.So a UTM should havefrequent proactive updatesto secure the network fromsmart attacks. It shouldutilize both – push and pulltechnologies to keep itupdated.Define Multiple IPSPolicies and Custom IPSSignatures:Blanket policies, over timeforce the administrator toopen security loop holes.Customized policies provideyou the comfort to deploycustomized IPS policies asper your needs.Custom IPS signatures reachdeeper than a firewall andantivirus to protect thenetwork from blendedthreats.In case of a host file corruptiondue to a Pharming attack, theDNS configured in CyberoamUTM makes sure that the useris not directed to a malicioussite.SonicWALL does notprovide timely securityupdates.Dependent on external AVSonicWALL UTM does nothave Custom IPS Policies.Cyberoam UTM empowers theuser by providing regularupdates of various securitysolutions: Virus and Spywareupdates: Every 30minutes. Spam updates: Everyminute. IPS updates: Every 7days Instant OutbreakupdatesCyberoam UTM provides theadministrator with the ability toattach an individual IPS policyto a combination of source,destination, application,identity and schedule.This ensures customized IPSpolicy as per your needs.Cyberoam UTM also providesyou the facility to use customIPS signatures.These features ensure thatyour network security is gearedup meet any exceptions as wellas general threat conditions.
Points to PonderSonicWALL UTMCyberoam UTMIdentity-based IPSPolicies and ReportingEnsures Transparency:SonicWALL UTM does nothave identity based IPSreporting.Cyberoam UTM provides IPaddress and User-basedreports. Providing completevisibility, it thwarts anonymityin DHCP, Wireless andComputer sharingenvironments.To deploy security policiesthe administrator has toknow his target. IPaddresses are not targetenough.In case of threat detection; itreduces the administrator’sreaction time. Theadministrator can personallycontact the erring user.The most harmful intrusionattempts are attemptedfrom inside a network. In IPaddress based IPS policiesand reporting the identitygets lost.Identity based policies alsolends unprecedentedgranularity to the IPS policies.To ensure completetransparency in a network,the IPS policies andreporting should also takethe user’s identity into itsambit.Clean VPNTo ensure complete securityof the network, it isnecessary to scan traffictraveled through VPNtunnels for virus, spywareand other malwarePractical Approach toBandwidth Management:Percentile based bandwidthmanagement is not practicalas, if a VoIP applicationneeds 128Kbps; you cannotassign 10% of thebandwidth.Moreover back calculatingbandwidth on percentagebasis is cumbersome.Cyberoam’s IPS module alsoprovides mail alerts.Supports VPN trafficscanningEnsures security of company’snetwork by scanning trafficthrough and from VPN tunnels.SonicWALL UTM’sbandwidth managementpolicy is not very effectivein the practicalimplementation because itallocates bandwidth onpercentile basis.Using Cyberoam you canprovide QoS to a combinationof source, destination andservice/service group bycommitting bandwidth to users,applications, Web categoriesand servers based on timeschedules.It lacks user specificbandwidth allocation anddoes not have the Priorityfeature.You can manage interactiveapplications like VoIP, VideoConferencing, SSH, telnet etc.better by assigning higherpriority to get better andinstant results
Points to PonderSonicWALL UTMCyberoam UTMSecure Vital Informationby Rule based Applicationand IM Controls:SonicWALL UTM does notsupport granular controlover IM.Unmonitored content leavingan organization through anIM application introducessecurity, legal andcompetitive risk. It isdifficult for the ITdepartment to discoverpotential breaches of policyor to hold individualsaccountable.They are either fully allowor are deny an application,there is no granularcontrol over it.Cyberoam UTM’s applicationfiltering solutions is powerfulenough to control file transferover any IM application.Identity can be used as acontrol parameter in thesecontrol policies.Automated Single SignOn Ensures hassle freeTransparentAuthentication :SonicWALL UTM does nothave automated SSO.Authentication often givesadministrators nightmaresas they involve a lot ofhassles and changes in theexisting setup.The SSO promotes a one stop,transparent entry into thenetwork, reducingadministrative maintenance.SSO ensures that the user’sauthentication is seamlessand transparent. It alsoensures that the user hashis well-defined securemicrocosm.Data Transfer Accountingand Control:Data transfer accounting andcontrol helps you to see theactual internet consumptionby an individual user or anapplication.This feature also helps whenyou want to find the exactcosting of Internet usage incase if an ISP is charging forthe amount of datatransferred.Cyberoam SSO ensures thatthe UTM remains transparentand it seamlessly blends intothe network. The user is neverexplicitly aware of itsexistence. Only in case oftreading on forbidden paths, heis reminded of the UTM’spresence.SonicWALL does not havethis feature.Cyberoam provides acomprehensive, application anduser based data transferaccounting and control.This feature comes in handy ineducational institutions whereInternet consumption perindividual is important.
Points to PonderSonicWALL UTMCyberoam UTMCentralized Management:SonicWALL supports harddisk drive based GlobalManagement System.Cyberoam’s CCC appliancehandles multiple Cyberoamappliances from a single point.SonicWALL providesrudimentary diagnostictool.Cyberoam provides multipleways to analyze the problem.Cyberoam HTTP diagnosticprovides enormous deeppacket level information totrouble shoot the problem.SonicWALL UTM comeswith limited reportingfacilities. However, if theorganization needsextensive reporting, it hasto buy and install aseparate proprietaryapplication SonicWALLViewpoint.Cyberoam has an integratedplug-and-play reporting modulewhich provides IP address anduser identity based in-depthreports.After paying an extra costalso, the user is forced tobear unacceptable gapbetween the event andactual report.As a value added featureCyberoam reports arecomplimentary to CIPA, HIPAA,GLBA, SOX, PCI, FISMAcompliances.The applications alsoneeds separate hardwareplatform.Cyberoam also providesexternal reporting with the helpof Indigenously Designed OpenSource Logging and ReportingSolution: Cyberoam-iView,Provides In-depth logging andTo reduce hassles ofmaintaining multipleappliances and ensureconsistency, a UTM shouldsupport centralizedmanagement.Network Diagnosis:A UTM should have somediagnosis tools to analyzethe problem for providingnetwork transparency. This,in result proves as a greataid to troubleshooting.User Identity BasedComprehensiveReporting:Reports are an integral partof any security solution asthey are the tools to providevisibility.Clear and precise reports arethe most valuable tools thatmakes sure thatorganization’s resources arefocused on maximumproductivityAll reports are HTTP/HTTPSbased, and so are platform,location and clientindependent.reporting for multiple devicesapart from Cyberoam
Overview of Cyberoam’s Security Approach: Whom do you give access to: An IP Address or a User? Whom do you wish to assign security policies: User Name or IP Addresses? In case of an insider attempted breach, whom do you wish to see: User Name or IPAddress? How do you create network address based policies in a DHCP and a Wi-Fi network? How do you create network address based policies for shared desktops?Cyberoam UTM approaches the Security paradigm from the identity perspective. Theblended threats circumvent the perimeter defense and launch an attack from within. Thenetwork’s own resources are used to subvert it. The main target is thus the end user whoknowingly or unknowingly breaches the perimeter defense.While providing a robust perimeter defense, Cyberoam UTM’s Identity-based accesscontrol technology ensures that every user is encapsulated in a tight, yet granular securitypolicy that spans across Cyberoam UTM’s Firewall/VPN, Gateway Anti Virus, Anti-Spam,Web Filtering, Intrusion Prevention System (IPS) and Bandwidth Management solutions.Cyberoam Product PortfolioDisclaimer:1.This document is strictly confidential and intended for private circulation only.The features of any of the products are likely to change without prior notice.2.The comparison is based on publicly available information only.3.Document Version: 5.4 – 96078 – 08/03/2010
Virtual Private Network Consortium (VPNC) : Basic Interop . Cyberoam has an OEM with Kaspersky Lab for Gateway Anti Virus, which is one of the industries leading Anti Virus Solution. SonicWALL has a proprietary gateway anti virus engine. In 2009, public test of different anti-virus vendors all out to see how they really compare .