Transcription
One Identity StarlingSecurity Guide
ContentsIntroduction 3Architecture 4User Authentication 6Customer Data Security 7Overview of Data Handled by One Identity Starling7Location of Customer Data 7Privacy and Protection 7Separation of Customer Data 7PII / GDPR 7Product Security 8DevSecOps 8Starling Testing Strategy 8Third-party Assessments 9Encryption in Transit and at Rest9Infrastructure Security 10FIPS 140-2 Compliance 10Operational Security 11Access Restrictions 11Continuous Monitoring Program 11Incident Response Program 11Physical Security 13Datacenter Security 13Office Location Security 13Business Continuity / Disaster Recovery14Recovery Planning and Global Resiliency14Customer Data Backups 14Summary 15
IntroductionManaging information system security is a priority and challenge for every organization. Infact, the level of security delivered by software vendors has become a differentiating factorfor IT purchase decisions. And when an organization commits to leveraging vendor partnerswith cloud-based services and applications, security capabilities become even moreimportant.One Identity strives to meet the desired level of security, whether it relates to privacy, dataintegrity and authenticity, availability or protection against malicious users and attacks.One Identity Starling is our software as a service platform that delivers our innovative SaaSenabled products. Starling improves security and enables your organization to extend to thecloud confidently.For more information, visit: https://cloud.oneidentity.comThis document describes the security features of the One Identity Starling CloudPlatform and Products. It reviews access control, protection of customer data, securenetwork communication, and more. We hope it addresses all your security questions andconcerns. If you have additional questions, please don’t hesitate to reach out to your salesrepresentative.3
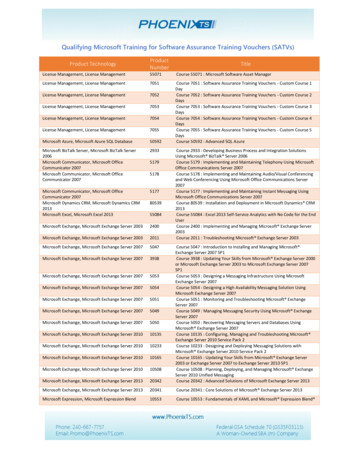
ArchitectureAzureAzure DatabasesApp Services Governance API Account Superv. API Governance UI Account UI 2FA Proxy API Connect Superv. API 2FA Proxy UI Connect UI Public UIExternal SystemsPostgreSQL Mongo AtlasCosmosDBMongoDBAzure FunctionsSQL Azure SendGrid SCIM Connectors: Service Now, Salesforce, etc. Scheduled JobsAzure K8s Service Authy Ubuntu LinuxCluster Charon/ZuoraAzure Services EventGrid Service BusSTS and IdentityBrokerIdPFederation Customer AAD Azure B2C AppInsightsNot pictured is the on-prem agent and its infrastructure.The diagram above illustrates the various Starling product deployments and theirassociations with Azure cloud service offerings. See also annotations below.By components and functional areas: Products: customer-facing Starling products (e.g., Two-Factor Authentication, etc.) aredeployed using Azure’s WebApps offering. Authentication: authentication and identity provider brokering are provided via theStarling STS which runs in a Kubernetes cluster deployed on Azure’s Kubernetes Service(AKS) Infrastructure: common “infrastructure glue” is implemented ad hoc using other Azureservice offerings such as EventGrid, Service Bus Queues, Storage Accounts, etc. SCIM Connectors: Connectors (part of Starling Connect) are individual purpose-builtSCIM transformers for various target systems. There is one Connector for each supportedtarget system, and these are implemented using Azure Functions which run server-lessstyle. Database: Database services are provided by CosmosDB, SQL Azure, PostgreSQL,and MongoDB. CosmosDB, SQL Azure, and PostgreSQL are provided by Azure, andMongoDB by Mongo’s Atlas hosting product. Back-office: Back-office integration including recurring billing, subscription modeling,and Quest licensing integration (TIMS) is handled via the Charon bridge (operated byQuest IT) to link to Zuora.4
Third-party services: Starling connects to external services for email delivery (SendGrid)and SMS messaging (Authy) Front-end Supported client browsers: mainstream browser support (IE, Chrome, Firefox) Programming Languages: JavaScript Frameworks: Angular 2 Platforms/OS: Platforms supported by browser providers Back-end Programming Languages: C#, PowerShell, Java Frameworks: ASP.net MVC Platforms/OS: Azure PaaS, Azure Kubernetes Service, Ubuntu-based containers, .NetCore Databases: Azure CosmosDB, MongoDB, PostgreSQL5
User AuthenticationStarling provides world-class identity protection by leveraging Azure’s strong identityfoundation. If your company already uses Azure Active Directory (AAD), you can use yourwork account to securely authenticate to Starling. For non-AAD users, One Identity Starlingalso supports the use of a personal account, which is based on Azure B2C.6
Customer Data SecurityOverview of Data Handled by One Identity StarlingOne Identity Starling manages the following types of customer data: Limited contact information for users; contact information being name, email address,phone number, company address. End-user log-in behavior is routinely recorded in Microsoft App Insights logs for a shortretention period. These logs are stored on Microsoft servers in the US or the EU. The ServiceNow integration feature requires a customer to provide his or her ServiceNowAPI credentials to Starling so that Starling can create tickets on Starling users’ behalf.These credentials are stored using Azure Key Vault.Location of Customer DataOne Identity Starling is deployed in Azure datacenters for redundancy and high availability.One Identity Starling is currently deployed in the western U.S. and EU Regions with failoverprotection enabled in each region.Privacy and ProtectionCustomer data is differentiated using a unique organization identifier. This organizationidentifier is generated during customer sign-up. This organization identifier is passed to theuser interface via a tamper-proof (signed) JSON Web Token (JWT). This token is requiredfor all API requests and is used to provide the organization’s context to back-end Starlingservices. The JWT has a ‘time to live’ (TTL) of 5 minutes and must be refreshed and reauthorized by the code consuming an API via the Starling STS.Separation of Customer DataA common concern related to cloud-based services is the prevention of commingling of datathat belongs to different customers. One Identity Starling is designed to specifically preventsuch data commingling by logically separating customer data. Customer data is carefullysegregated during storage, use and retrieval to ensure isolation and confidentiality.PII / GDPRIn addition to being encrypted in motion and at rest, sensitive customer data, includingPII and PCI can never be viewed by Starling personnel and no customer data of any kindis viewed or copied by Starling personnel without express customer consent (exceptionsinclude suitably anonymized data for analytics purposes, as covered in the customeragreement).7
Product SecurityDevSecOpsMany are familiar with the term ‘DevOps’, which is the combination of Development Operations. This is a blended discipline where software development and operations teamswork in close partnership. This is a reality-focused cloud engineering process that allowsrapid development and deployment of needed customer functionality.DevSecOps takes DevOps one step further by mandating security in all parts of what iscommonly called DevOps. This allows One Identity to deliver Starling faster, more solid anda more secure cloud experience for customers. The graphic below illustrates the DevSecOpscycle (depicted in 2017 by Gartner) and is a general representation of the StarlingDevSecOps cycle.Starling DevSecOps cycle has other characteristics that make security part of the Starlingdelivery process. These include: Only authorized and authenticated One Identity employees have access to source controland build systems. When a One Identity Starling team member leaves the company, thatindividual is no longer be able to access One Identity Starling systems. Changes to One Identity Starling production services, databases, and infrastructure aretightly controlled. As changes flow through the system, they are recorded and audited. Adherence to OWASP and SANS Institute guidelines All Starling code is frequently scanned and tested against a wide variety of threats andknown vulnerabilitiesStarling Testing StrategyWe strive to deliver new and useful features but before we release them for public use, wetest each one to ensure they meet our standards of reliability and security. Starling usesa graduated testing strategy. This allows us to discover any issues as early as possiblein development process, and ultimately, to produce high quality solutions in an efficientmanner.8
Third-party AssessmentsNOTE: None of the testing or analysis described below occurs in the Starling productionenvironment.Annual Penetration Test / Code AnalysisOn an annual basis, One Identity Starling engages a world renowned firm who are expertsin cybersecurity and risk mitigation. This company is engaged to perform a sophisticatedpenetration test as well as conducting a focused code review with an eye towardsinformation and data security. Areas of coverage include important areas like strength ofcyphers used, weaknesses in application servers, etc.Daily SAST Testing (White Box Testing)SAST (Static Application Security Testing) examines the application from the inside,searching its source code for security vulnerabilities. These tools are constantly updated toscan for common weaknesses from the SANS and OWASP standard categories, as well asfrom new and emerging threats.Starling uses a well-established and credentialed security vendor’s product to perform staticanalysis of Starling code as well as scanning any third-party libraries built into Starling’scode. These static analysis (SAST) and third-party scans (SCA) are run each night; anydiscovery of Starling code or third-party issues automatically open items requiring softwaredeveloper review / remediation before the code is considered acceptable.Weekly DAST Testing (Black Box Testing)DAST (Dynamic Application Security Testing) is a black box methodology in which anapplication is tested from the outside. This means DAST testing tools examine an applicationwhen it is running and look for vulnerabilities that might be available to a hacker.Starling uses a well-established and credentialed security vendor’s product to performpenetration testing of Starling web applications. This penetration test takes place once aweek. The tool used by Starling detects over 4,500 vulnerabilities and produces very fewfalse positives. The results of this DAST test are examined by an experienced Starling staffmember and when needed, items are opened that require remediation before the Starlingapplication is considered to be acceptable.Encryption in Transit and at RestAll communications to and from One Identity Starling are secured by HTTPS, and the SSLcertificates are issued by trusted certificate authorities.One Identity Starling protects all customer data at rest using industry standard encryption.9
Infrastructure SecurityChange ControlNecessary personnel access is controlled via industry-standard automated credentialprocedures and automated, real-time provisioning/de-provisioning of personnel and access.Privileged access to production infrastructure is limited to the smallest possible group ofbackground-checked Operations personnel, and is tightly controlled and audited. Duringsecurity review cycles associated with the SDL noted earlier, no third parties have directaccess to the One Identity Starling infrastructure.Malware ProtectionBy running our services on Microsoft Azure, we are able to take advantage of Microsoft’sreal-time anti-malware protection capability to identify and remove viruses, spyware andother malicious software.Network SecurityThe One Identity Starling infrastructure leverages network security best practices. MicrosoftAzure network security groups allow us to restrict network access to an isolated, privatevirtual network. Access to the production network is limited to a small number of Operationspersonnel (see Change Control).All internal network communication within Azure among Starling services and componentsis secured with HTTPS and is not visible to the external public internet. There are nounsecured external HTTP calls within Starling. Starling communicates with all Azure servicesover HTTPS connections. Starling also communicates with MongoDB and Twilio’s Authy andSendGrid services via secure HTTPS connections.FIPS 140-2 ComplianceThe One Identity Starling product’s cryptographic usage is based on Azure FIPS 140-2compliant cryptographic functions. Starling uses FIPS 140-2 compliant encryption providedin Microsoft Azure Cloud services. Additional information: Microsoft and FIPS: ance/fips Encryption in the Microsoft Cloud: -cloud-overview Azure Storage: mon/storagesecurity-guide10
Operational SecurityAccess RestrictionsAccess to Starling’s production (customer facing) environment is restricted to Starling’s OPSteam members and the OPS team must obtain permission to access the Starling productionarea. No Starling developer or QA person has access to the customer production area anddata.Continuous Monitoring ProgramThe One Identity Starling team has procedures in place to monitor the health of the systemand ensure any degradation of the service is promptly identified and resolved.There are two Starling status pages – one for the Americas and one for the EU. Those arelocate atus.cloud.oneidentity.eu/The Starling OPS team makes use of monitoring tools that use hundreds of automated testsand telemetry to detect even small anomalies so an appropriate response is made:The Starling OPS team also has configured alerts that are raised as a result of the monitoringprogram. Various severities are used to ensure the appropriate response is marshaled – seethe graphic below.11
Incident Response ProgramThe One Identity Starling team has established a formal process of preparation, detection,analysis, containment, eradication, recovery and post-incident activities. In accordancewith international privacy laws, One Identity has also established a Security Breach Noticeprocess. This process aligns with the common Quest Incident Management System (SIIM).Quest’s Legal department immediately gets involved when there are security breachesStarling is composed of two different environments – the cloud environment (MS Azure,MongoDB, Authy and SendGrid) and a back office environment where non-Starling systemsare hosted. These back office systems are shared with other Quest and One Identityproducts and include services like billing, customer support, etc. These are not maintainedby the One Identity business unit. For these back office systems, the common Quest IncidentManagement System (SIIM) is used for escalation and delegation.One Identity Starling relies on Microsoft Azure and MongoDB infrastructure and as such, issubject to the possible disruption of these services. The Starling Operations team has accessto status pages for both Microsoft Azure and MongoDB should an incident occur with eitherof these two infrastructure p://status.mongodb.com/12
Physical SecurityDatacenter SecurityMicrosoft Azure datacenters have the highest possible physical security and are consideredamong the most secure and well protected datacenters in the world. They are subject toregular audits and certifications, including Service Organization Controls (SOC) 1, SOC 2 andISO/IEC 27001:2005. Relevant references with additional information about the WindowsAzure datacenter security can be found here: Azure Trust Center Microsoft Trust Center Compliance Microsoft’s submission to the Cloud Security Alliance STAR registry Whitepaper: Standard Response to Request for Information – Security and Privacy Microsoft Global Datacenters: Security & Compliance Azure data-at-rest Encryption Best PracticesOffice Location SecurityOne Identity has a security program that manages visitors, building entrances, CCTVs,and overall office security. All employees, contractors and visitors are required to wearidentification badges.One Identity Starling is completely in the cloud, so all employees working on Starling act asremote employees, even for those who work from an office location.13
Business Continuity /Disaster RecoveryRecovery Planning and Global ResiliencyOne Identity Starling has a regularly reviewed and updated disaster recovery plan to ensurethat we can respond to a disaster or other emergency that affects information systemsand minimize the impact on the operation of the business and our customers. The plan isdesigned to be resilient to, or recover quickly from, a disaster or disruption beyond the OneIdentity Starling team’s control. The plan consists of several layers of protection, includingmonitoring, failover, backup and restoration.Through monitoring, we aim to detect incidents quickly to prevent or minimize damage.Redundancy and automatic failover are in place to ensure resiliency to failure of individualservice nodes. In the case of a regional datacenter failures across our current topology, wehave the capability to quickly and automatically deploy to another Azure datacenter that isunaffected.Finally, in case of a more significant event, there is a database recovery plan in placeleveraging regular data backups that can be implemented in minutes with little to no dataloss. Qualified Operations personnel are monitoring the services 24x365 and have accessto additional qualified resources on call to respond to incidents promptly, whenever theymay occur. Operations and extended engineering teams leverage a distributed, multi-modalcommunications approach, such that no one telecommunications channel represents asingle point of failure.Customer Data BackupsAll Starling data is backed up automatically multiple times per day to facilitate recovery,should a disaster or another emergency require it. Backups are encrypted and aged-outregularly.The Starling SaaS solution depends heavily on the following third-party (cloud) services forits operation: Microsoft Azure Authy MongoDB SendGridThe above services are considered critical to the delivery of Starling SaaS, however OneIdentity has no direct control over the infrastructure sustaining these services, thus thebackup and archiving functions provided by the respective cloud service provider is used.For both backup and disaster recovery purposes, the following applies: Azure Cosmos DB and Azure SQL: Provided by MS Azure for backup and recoverycapabilities Mongo DB: Backup and recovery (hosted by Atlas in Azure) Authy and SendGrid: Backup and recovery provided by Twilio (owner of these cloudproducts)The Starling OPS group can configure the timing of Starling backups, what type of backupstake place and what backups are restored and when. However, as stated previously, StarlingOPS has no direct control of backup and recovery of these services.14
SummaryOne Identity Starling SaaS offerings enhance security and simplify compliance whileproviding organizations the agility and affordability of cloud-based IAM. Our securitymechanisms to protect physical, network and application components of the platform, alongwith transparent and mature security practices, provide a foundation for extending to thecloud with confidence.15
This means DAST testing tools examine an application when it is running and look for vulnerabilities that might be available to a hacker. Starling uses a well-established and credentialed security vendor's product to perform penetration testing of Starling web applications. This penetration test takes place once a week.