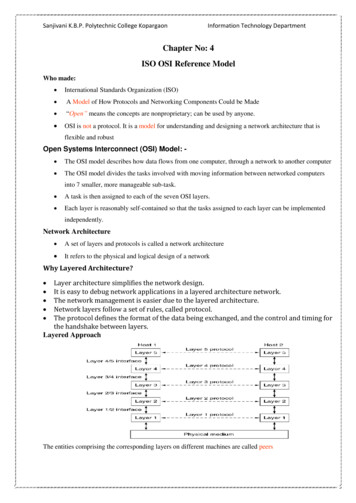
Magic Quadrant for Enterprise Network Firewalls
Magic Quadrant for Enterprise Network Firewalls Source: Gartner (July 2017) Vendor Strengths and Cautions AhnLab Headquartered in South Korea, AhnLab enjoys sizable in-country market share, especially in the government and financial verticals, but has only a limited presence in other East Asian nations. It has sold firewalls since 2007 under the TrusGuard product line. It offers 12 UTM and ...