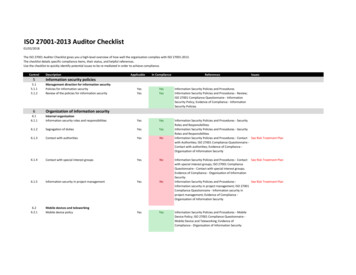
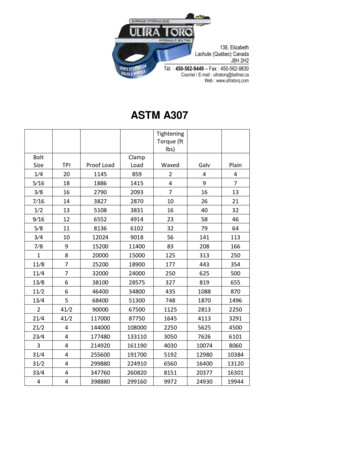
Transcription
NetworkAssessmentRisk ReportCONFIDENTIALITY NOTE: The information contained in this report documentis for the exclusive use of the client specified above and may containconfidential, privileged and non-disclosable information. If the recipient of thisreport is not the client or addressee, such recipient is strictly prohibited fromreading, photocopying, distributing or otherwise using this report or its contentsin any way.Scan Date: 10/25/2016Prepared for:Your Customer / ProspectPrepared by:Your Company Name10/27/2016
Risk ReportNETWORK ASSESSMENTTable of Contents1 - Discovery Tasks2 - Risk Score3 - Issues Summary4 - Internet Speed Test5 - Assessment Summary6 - Server Aging7 - Workstation AgingPROPRIETARY & CONFIDENTIALPAGE 2 of 20
Risk ReportNETWORK ASSESSMENTDiscovery TasksThe following discovery tasks were performed:TaskDescription Detect Domain ControllersIdentifies domain controllers and online status. FSMO Role AnalysisEnumerates FSMO roles at the site. Enumerate Organization Units andSecurity GroupsLists the organizational units and security groups (with members). User AnalysisLists the users in AD, status, and last login/use, which helps identifypotential security risks. Detect Local Mail ServersDetects mail server(s) on the network. Detect Time ServersDetects server(s) on the network. Discover Network SharesDiscovers the network shares by server. Detect Major ApplicationsDetects all major apps / versions and counts the number ofinstallations. Detailed Domain Controller Event LogAnalysisLists the event log entries from the past 24 hours for the directoryservice, DNS server and file replication service event logs. SQL Server AnalysisLists the SQL Servers and associated database(s). Internet Domain AnalysisQueries company domain(s) via a WHOIS lookup. Password Strength AnalysisUses MBSA to identify computers with weak passwords that maypose a security risk. Missing Security UpdatesUses MBSA to identify computers missing security updates. System by System Event Log AnalysisDiscovers the five system and app event log errors for servers. External Security VulnerabilitiesLists the security holes and warnings from External VulnerabilityScan.PROPRIETARY & CONFIDENTIALPAGE 3 of 20
Risk ReportNETWORK ASSESSMENTRisk ScoreThe Risk Score is a value from 1 to 100, where 100 represents significant risk and potential issues. Thescore is risk associated with the highest risk issue.Several critical issues were identified. Identified issues should be investigated and addressed accordingto the Management Plan.PROPRIETARY & CONFIDENTIALPAGE 4 of 20
Risk ReportNETWORK ASSESSMENTIssues SummaryThis section contains a summary of issues detected during the Network Assessment process, and isbased on industry-wide best practices for network health, performance, and security. The Overall IssueScore grades the level of issues in the environment. An Overall Issue score of zero (0) means no issueswere detected in the environment. It may not always be possible to achieve a zero score in allenvironments due to specific circumstances.Overall Issue Score: Risk Score x Number of Incidents Total points: Total percent (%)4160User password set to never expire (80 pts each)Current Score: 80 pts x 52 4160: 48.59%Issue: User accounts with passwords set to never expire present a risk of use byunauthorized users. They are more easily compromised than passwords that are routinelychanged.Recommendation: Investigate all accounts with passwords set to never expire and configurethem to expire regularly.1335Inactive computers (15 pts each)Current Score: 15 pts x 89 1335: 15.59%Issue: 89 computers have not checked in during the past 30 daysRecommendation: Investigate the list of inactive computers and determine if they should beremoved from Active Directory, rejoined to the network, or powered on.846Anti-spyware not installed (94 pts each)Current Score: 94 pts x 9 846: 9.88%Issue: Anti-spyware software was not detected on some computers. Without adequate antivirus and anti-spyware protection on all workstations and servers, the risk of acquiringmalicious software is significant.Recommendation: Assure that anti-spyware is deployed to all possible endpoints in order toprevent both security and productivity issues.846Anti-virus not installed (94 pts each)Current Score: 94 pts x 9 846: 9.88%Issue: Anti-virus software was not detected on some computers. Without adequate anti-virusand anti-spyware protection on all workstations and servers, the risk of acquiring malicioussoftware is significant.Recommendation: To prevent both security and productivity issues, we strongly recommendPROPRIETARY & CONFIDENTIALPAGE 5 of 20
Risk ReportNETWORK ASSESSMENTensuring that anti-virus is deployed to all possible endpoints.533User has not logged on to domain 30 days (13 pts each)Current Score: 13 pts x 41 533: 6.23%Issue: 41 Users that have not logged in in 30 days could be from A user that has not loggedin for an extended period of time could be a former employee or vendor.Recommendation: Disable or remove user accounts for users that have not logged on toactive directory in 30 days.272Potential disk space issue (68 pts each)Current Score: 68 pts x 4 272: 3.18%Issue: 4 computers were found with significantly low free disk space.Recommendation: Free or add additional disk space for the specified drives.200Insecure listening ports (10 pts each)Current Score: 10 pts x 20 200: 2.34%Issue: 20 computers are to be using potentially insecure protocols.Recommendation: There may be a legitimate business need, but these risks should beassessed individually. Certain protocols are inherently insecure since they often lackencryption. Inside the network, their use should be minimized as much as possible to preventthe spread of malicious software. Of course, there can be reasons these services are neededand other means to protect systems which listen on those ports. We recommend reviewingthe programs listening on the network to ensure their necessity and security.194Unsupported operating systems (97 pts each)Current Score: 97 pts x 2 194: 2.27%Issue: 2 computers found using an operating system that is no longer supported.Unsupported operating systems no longer receive vital security patches and present aninherent risk.Recommendation: Upgrade or replace computers with operating systems that are no longersupported.85Lack of redundant domain controller (85 pts each)Current Score: 85 pts x 1 85: 0.99%Issue: Only one domain controller was found on the network. There is a heightened risk ofbusiness downtime, loss of data, or service outage due to a lack of redundancy.Recommendation: Evaluate the risk, cost, and benefits of implementing a redundant DomainController.80Operating system in Extended Support (20 pts each)Current Score: 20 pts x 4 80: 0.93%PROPRIETARY & CONFIDENTIALPAGE 6 of 20
Risk ReportNETWORK ASSESSMENTIssue: 4 computers are using an operating system that is in Extended Supported. ExtendedSupport is a warning period before an operating system is no longer supported by themanufacturer and will no longer receive support or patches.Recommendation: Upgrade computers that have operating systems in Extended Supportbefore end of life.10Un-populated organization units (10 pts each)Current Score: 10 pts x 1 10: 0.12%Issue: Empty organizational units (OU) were found in Active Directory. They may not beneeded and can lead to misconfiguration.Recommendation: Remove or populate empty organizational units.PROPRIETARY & CONFIDENTIALPAGE 7 of 20
Risk ReportNETWORK ASSESSMENTInternet Speed Test ResultsDownload Speed: 55.29 Mb/sUpload Speed: 15.16 Mb/sAsset Summary: Total Discovered AssetsPROPRIETARY & CONFIDENTIALPAGE 8 of 20
Risk ReportNETWORK ASSESSMENTAsset Summary: Active ComputersActive Computers are defined as computers that were either actively responding at the time of the scan orhave checked in with Active Directory within the past 30 days.Operating SystemTotalPercentWindows 10 Pro2341.8%Windows 8.1 Enterprise712.7%Windows Server 2012 R2 Standard610.9%Windows Server 2012 R2 Datacenter59.1%Windows 10 Enterprise35.5%Total - Top Five4480%Windows 8 Enterprise23.6%Windows 8.1 Pro23.6%Windows Server 2008 R2 Enterprise23.6%Windows 2000 Server11.8%Windows 7 Enterprise11.8%Windows 7 Professional11.8%Windows Server 200311.8%Windows Server 2012 Standard11.8%1120%55100%Top FiveOtherTotal - OtherOverall TotalPROPRIETARY & CONFIDENTIALPAGE 9 of 20
Risk ReportNETWORK ASSESSMENTPROPRIETARY & CONFIDENTIALPAGE 10 of 20
Risk ReportNETWORK ASSESSMENTAsset Summary: All ComputersThe list of all computers includes computers that may no longer be active but have entries in ActiveDirectory (in a domain environment).Operating SystemTotalPercentWindows 10 Pro3524.3%Windows Server 2012 R2 Standard1611.1%Windows 8 Enterprise139%Windows 8.1 Enterprise139%Windows 8.1 Pro106.9%8760.4%Windows 7 Enterprise96.2%Windows Server 2012 R2 Datacenter96.2%Windows 7 Professional74.9%Windows Server 200353.5%Windows 10 Enterprise42.8%Windows 2000 Server32.1%Windows Server 2008 R2 Datacenter32.1%Unidentified OS21.4%Windows 10 Pro Insider Preview21.4%Windows 8 Pro21.4%Windows Server 2008 R2 Enterprise21.4%Top FiveTotal - Top FiveOtherPROPRIETARY & CONFIDENTIALPAGE 11 of 20
Risk ReportNETWORK ASSESSMENTOperating SystemTotalPercentWindows Server 2008 R2 Standard21.4%Hyper-V Server 201210.7%Windows 8.1 Pro with Media Center10.7%Windows Server 2012 Datacenter10.7%Windows Server 2012 Standard10.7%Windows Server 2016 Technical Preview 310.7%Windows Server 2016 Technical Preview 3 Standard10.7%Windows Technical Preview for Enterprise10.7%5739.6%144100%Total - OtherOverall TotalPROPRIETARY & CONFIDENTIALPAGE 12 of 20
Risk ReportNETWORK ASSESSMENTAsset Summary: Inactive ComputersInactive computers are computers that could not be scanned or have not checked into Active Directory inthe past 30 days.Operating SystemTotalPercentWindows 10 Pro1213.5%Windows 8 Enterprise1112.4%Windows Server 2012 R2 Standard1011.2%Windows 7 Enterprise89%Windows 8.1 Pro89%4955.1%Windows 7 Professional66.7%Windows 8.1 Enterprise66.7%Windows Server 200344.5%Windows Server 2012 R2 Datacenter44.5%Windows Server 2008 R2 Datacenter33.4%Unidentified OS22.2%Windows 10 Pro Insider Preview22.2%Windows 2000 Server22.2%Windows 8 Pro22.2%Windows Server 2008 R2 Standard22.2%Hyper-V Server 201211.1%Top FiveTotal - Top FiveOtherPROPRIETARY & CONFIDENTIALPAGE 13 of 20
Risk ReportNETWORK ASSESSMENTOperating SystemTotalPercentWindows 10 Enterprise11.1%Windows 8.1 Pro with Media Center11.1%Windows Server 2012 Datacenter11.1%Windows Server 2016 Technical Preview 311.1%Windows Server 2016 Technical Preview 3 Standard11.1%Windows Technical Preview for Enterprise11.1%4044.9%89100%Total - OtherOverall TotalPROPRIETARY & CONFIDENTIALPAGE 14 of 20
Risk ReportNETWORK ASSESSMENTAsset Summary: UsersPROPRIETARY & CONFIDENTIALPAGE 15 of 20
Risk ReportNETWORK ASSESSMENTPROPRIETARY & CONFIDENTIALPAGE 16 of 20
Risk ReportNETWORK ASSESSMENTServer AgingPROPRIETARY & CONFIDENTIALPAGE 17 of 20
Risk ReportNETWORK ASSESSMENTWorkstation AgingPROPRIETARY & CONFIDENTIALPAGE 18 of 20
Risk ReportNETWORK ASSESSMENTAsset Summary: StoragePROPRIETARY & CONFIDENTIALPAGE 19 of 20
Risk ReportNETWORK ASSESSMENTPROPRIETARY & CONFIDENTIALPAGE 20 of 20
NETWORK ASSESSMENT PROPRIETARY & CONFIDENTIAL PAGE 5 of 20 Issues Summary This section contains a summary of issues detected during the Network Assessment process, and is based on industry-wide best practices for network health, performance, and security. The Overall Issue Score grades the level of issues in the environment. An Overall Issue score of zero (0) means no issuesFile Size: 588KBPage Count: 20