Transcription
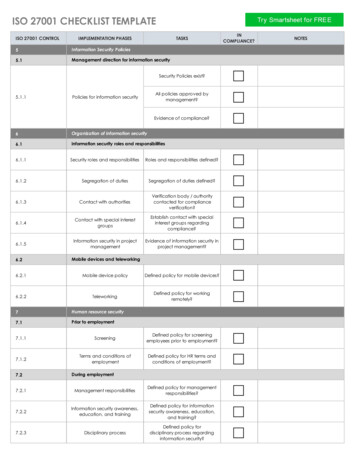
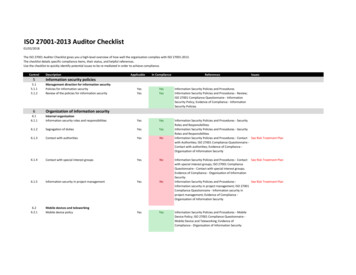
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve ableIn ComplianceReferencesIssuesInformation security policiesManagement direction for information securityPolicies for information securityReview of the policies for information securityYesYesYesYesInformation Security Policies and ProceduresInformation Security Policies and Procedures - Review;ISO 27001 Compliance Questionnaire - InformationSecurity Policy; Evidence of Compliance - InformationSecurity PoliciesInformation Security Policies and Procedures - SecurityRoles and ResponsibilitiesInformation Security Policies and Procedures - SecurityRoles and ResponsibilitiesInformation Security Policies and Procedures - Contact See Risk Treatment Planwith Authorities; ISO 27001 Compliance Questionnaire Contact with authorities; Evidence of Compliance Organisation of Information SecurityOrganization of information security6.16.1.1Internal organizationInformation security roles and responsibilitiesYesYes6.1.2Segregation of dutiesYesYes6.1.3Contact with authoritiesYesNo6.1.4Contact with special interest groupsYesNo6.1.5Information security in project managementYesNo6.26.2.1Mobile devices and teleworkingMobile device policyYesYesInformation Security Policies and Procedures - Contact See Risk Treatment Planwith special interest groups; ISO 27001 ComplianceQuestionnaire - Contact with special interest groups;Evidence of Compliance - Organisation of InformationSecurityInformation Security Policies and Procedures See Risk Treatment PlanInformation security in project management; ISO 27001Compliance Questionnaire - Information security inproject management; Evidence of Compliance Organisation of Information SecurityInformation Security Policies and Procedures - MobileDevice Policy; ISO 27001 Compliance Questionnaire Mobile Device and Teleworking; Evidence ofCompliance - Organisation of Information Security
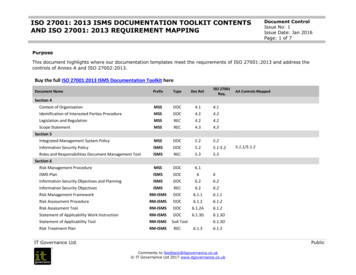
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve cableYesIn ComplianceYesReferencesInformation Security Policies and Procedures Teleworking; ISO 27001 Compliance Questionnaire Mobile Device and Teleworking; Evidence ofCompliance - Organisation of Information SecurityA.7Human resource security7.17.1.1Prior to employmentScreeningYesYes7.1.2Terms and conditions of employmentYesYes7.27.2.1During employmentManagement responsibilitiesYesYes7.2.2Information security awareness, education, and trainingYesNo7.2.3Disciplinary processYesYes7.37.3.1Termination and change of employmentTermination or change of employment responsibilitiesYesYesInformation Security Policies and Procedures - HumanResource SecurityAsset Inventory WorksheetAsset Inventory WorksheetInformation Security Policies and Procedures - AssetManagementInformation Security Policies and Procedures - AssetManagement; ISO 27001 Compliance Questionnaire Employee TerminationA.8Asset management8.18.1.18.1.28.1.3Responsibilities for assetsInventory of assetsOwnership of assetsAcceptable use of assetsYesYesYesYesYesYes8.1.4Return of assetsYesYes8.2Information classificationIssuesInformation Security Policies and Procedures - HumanResource Security; ISO 27001 Compliance Questionnaire- Human Resource SecurityInformation Security Policies and Procedures - HumanResource Security; ISO 27001 Compliance Questionnaire- Human Resource SecurityInformation Security Policies and Procedures - HumanResource SecurityInformation Security Policies and Procedures See Risk Treatment PlanInformation Security Awareness and Training; ISO 27001Compliance Questionnaire - Information SecurityAwareness and TrainingInformation Security Policies and Procedures - HumanResource Security
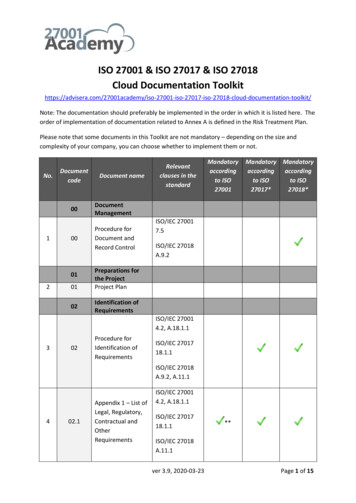
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve compliance.Control8.2.1DescriptionClassification of informationApplicableYesIn ComplianceYes8.2.2Labeling of informationYesNo8.2.3Handling of assetsYesYes8.38.3.1Media handlingManagement of removable mediaYesNo8.3.2Disposal of mediaYesNo8.3.3Physical media transferYesYesReferencesInformation Security Policies and Procedures Information Classification and LabelingInformation Security Policies and Procedures Information Classification and Labeling; ISO 27001Compliance Questionnaire - Information Classificationand LabelingInformation Security Policies and Procedures Information Classification and LabelingIssuesInformation Security Policies and Procedures Management of removable media; Site WalkthroughChecklistInformation Security Policies and Procedures Management of removable media; Site WalkthroughChecklistInformation Security Policies and Procedures Management of removable media; ISO 27001Compliance Questionnaire - Media HandlingSee Risk Treatment PlanA.9Access controlA.99.1.1Responsibilities for assetsAccess control policyYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User Access9.1.2Access to networks and network servicesYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User Access9.29.2.1Responsibilities for assetsUser registration and de-registrationYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User Access9.2.2User access provisioningYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User Access9.2.3Management of privileged access rightsYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User AccessSee Risk Treatment PlanSee Risk Treatment Plan
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve compliance.Control9.2.4DescriptionManagement of secret authentication information of usersApplicableYesIn ComplianceYesReferencesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User AccessIssuesSee Risk Treatment Plan9.2.5Review of user access rightsYesNoInformation Security Policies and Procedures - Accesscontrol policy; User Access Rights Review Worksheet;Evidence of Compliance - User Access Management9.2.6Removal or adjustment of access rightsYesYesInformation Security Policies and Procedures - Accesscontrol policy; Evidence of Compliance - User Access9.39.3.1User responsibilitiesUse of secret authentication informationYesYesInformation Security Policies and Procedures - Userresponsibilities9.49.4.1System and application access controlInformation access restrictionsYesNo9.4.2Secure log-on proceduresYesYes9.4.3Password management systemYesNo9.4.4Use of privileged utility programsYesNo9.4.5Access control to program source codeYesNoInformation Security Policies and Procedures - AccessControl Policy; Evidence of Compliance - User accessmanagementInformation Security Policies and Procedures - AccessControl Policy; Evidence of Compliance - User accessmanagementInformation Security Policies and Procedures - AccessControl Policy; Evidence of Compliance - User accessmanagementInformation Security Policies and Procedures - AccessControl Policy; Evidence of Compliance - User accessmanagementInformation Security Policies and Procedures - AccessControl Policy; ISO 27001 Compliance Questionnaire Access control to program source; Evidence ofCompliance - User access managementA.10Cryptography10.1Cryptographic controlsSee Risk Treatment PlanSee Risk Treatment PlanSee Risk Treatment PlanSee Risk Treatment Plan
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve compliance.Control10.1.1DescriptionPolicy on the use of cryptographic controls10.1.2Key managementApplicableYesIn ComplianceNoReferencesInformation Security Policies and Procedures Cryptography; ISO 27001 Compliance Questionnaire Cryptography; Evidence of Compliance - CryptographyIssuesSee Risk Treatment PlanYesNoInformation Security Policies and Procedures Cryptography; ISO 27001 Compliance Questionnaire Cryptography; Evidence of Compliance - CryptographySee Risk Treatment PlanA.11Physical and environmental security11.111.1.1Secure areasPhysical security perimeterYesNoInformation Security Policies and Procedures - Physical See Risk Treatment Planand environmental security; Site Walkthrough Checklist11.1.2Physical entry controlsYesNoInformation Security Policies and Procedures - Physical See Risk Treatment Planand environmental security; Site Walkthrough Checklist11.1.3Securing offices, rooms and facilitiesYesNoInformation Security Policies and Procedures - Physical See Risk Treatment Planand environmental security; Site Walkthrough Checklist11.1.4Protection against external and environmental threatsYesYes11.1.5Working in secure areasYesYes11.1.6Delivery and loading areasYesYesInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physicaland environmental security11.211.2.1EquipmentEquipment siting and protectionYesYesInformation Security Policies and Procedures - Physicaland environmental security; Site Walkthrough Checklist11.2.2Supporting utilitiesYesYes11.2.3Cabling securityYesNoInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physical See Risk Treatment Planand environmental security; Site Walkthrough Checklist11.2.4Equipment maintenanceYesYesInformation Security Policies and Procedures - Physicaland environmental security
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve compliance.Control11.2.5DescriptionRemoval of assetsApplicableYesIn ComplianceYes11.2.6Security of equipment and assets off-premisesYesYes11.2.7Secure disposal or re-use of equipmentYesYes11.2.8Unattended user equipmentYesNo11.2.9Clear desk and clear screen policyYesNoReferencesInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physicaland environmental securityInformation Security Policies and Procedures - Physicaland environmental security; Evidence of Compliance Screen Lock SettingsInformation Security Policies and Procedures - Physicaland environmental security; Evidence of Compliance Screen Lock Settings; Site Walkthrough ChecklistA.12Operations security12.112.1.1Operational procedures and responsibilitiesDocumented operating proceduresYesYes12.1.2Change managementYesYes12.1.3Capacity managementYesYes12.1.4Separation of development, testing and operationalenvironmentsYesYes12.212.2.1Protection from malwareControls against malwareYesNoInformation Security Policies and Procedures Protection from malware; Evidence of Compliance Endpoint Security12.312.3.1BackupInformation BackupYesYesInformation Security Policies and Procedures - Backup;Evidence of Compliance - Backup12.4Logging and MonitoringIssuesSee Risk Treatment PlanSee Risk Treatment PlanInformation Security Policies and Procedures Documented operating procedures; ISO 27001Compliance Questionnaire - Documented operatingproceduresInformation Security Policies and Procedures Documented operating proceduresInformation Security Policies and Procedures Documented operating proceduresInformation Security Policies and Procedures Documented operating procedures; Asset inventoryworksheetSee Risk Treatment Plan
ISO 27001-2013 Auditor Checklist01/02/2018The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013.The checklist details specific compliance items, their status, and helpful references.Use the checklist to quickly identify potential issues to be re-mediated in order to achieve compliance.Control12.4.1DescriptionEvent loggingApplicableYesIn ComplianceNo12.4.2Protection of log informationYesNo12.4.3Administrator and operator logYesNo12.4.4Clock synchronizationYesNo12.512.5.1Control of operational softwareInstallation of software on operational systemsYesYesInformation Security Policies and Procedures - Controlof operational software12.612.6.1Technical vulnerability managementManagement of technical vulnerabilitiesYesNo12.7.2Restriction on software installationYesNoInformation Security Policie
ISO 27001-2013 Auditor Checklist 01/02/2018 The ISO 27001 Auditor Checklist gives you a high-level overview of how well the organisation complies with ISO 27001:2013. The checklist details specific compliance items, their status, and helpful references.File Size: 372KBPage Count: 9