Transcription
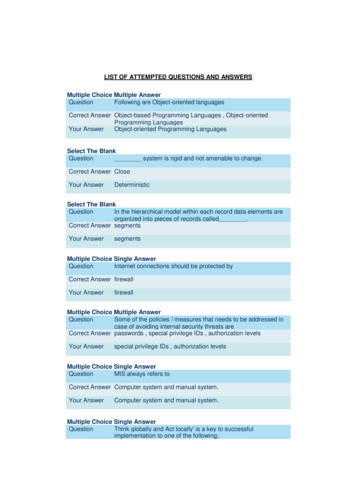
LIST OF ATTEMPTED QUESTIONS AND ANSWERSMultiple Choice Multiple AnswerQuestionFollowing are Object-oriented languagesCorrect Answer Object-based Programming Languages , Object-orientedProgramming LanguagesYour AnswerObject-oriented Programming LanguagesSelect The BlankQuestionsystem is rigid and not amenable to change.Correct Answer CloseYour AnswerDeterministicSelect The BlankQuestionIn the hierarchical model within each record data elements areorganized into pieces of records called .Correct Answer segmentsYour AnswersegmentsMultiple Choice Single AnswerQuestionInternet connections should be protected byCorrect Answer firewallYour AnswerfirewallMultiple Choice Multiple AnswerQuestionSome of the policies / measures that needs to be addressed incase of avoiding internal security threats areCorrect Answer passwords , special privilege IDs , authorization levelsYour Answerspecial privilege IDs , authorization levelsMultiple Choice Single AnswerQuestionMIS always refers toCorrect Answer Computer system and manual system.Your AnswerComputer system and manual system.Multiple Choice Single AnswerQuestionThink globally and Act locally' is a key to successfulimplementation to one of the following;
QuestionThe increased business complexities could be attributed totechnological changes , explosion of information , research and developmentInformation is a resource becauseit is scarce , it has cost , it has alternate usesData and storage instructions are stored for temporary period till processing is completed hereprimary storageThe business organization is normally designed in apyramid structureMIS as a function should be flexible enough to respond tochanging environmentA combination of human and computer based resources which result in collection and use of data for purpose ofefficient management and business planningmarketing information systemManufacturing as a functional sub - system will have the following functionsCost control analysis. , Sales forecasts. , Sales planning.FAV is the short form ofFixed Asset Voucher.Fixed Asset Voucher.One of the following is a required field in the Debit noteInward Freight.Inward Freight.Following are the types of Payment GenerationVoucher Generation , Bank Payment Voucher GenerationVoucher Generation , Bank Payment Voucher GenerationThe user department sends the indent directly to the purchase department.FALSEThe gives Transaction details to Account Payable SystemJournalOne of the following is the front end application in hospital industrypatient database , linked database , medical case history databaseThe returns in the manufacturing sector are immediate as compared to the service sector.FALSEThe choice of technology makes a significant difference in the service quality to the customer.TRUEThe computer hardware consists ofCentral processing unit. , Primary and secondary storage.
Some of the input devices are as underTouch screen. , Computer mouse. , Keyboard.Hard disk is a primary storage unit.FALSEThe second generation of computers used integrated circuits/chips.FALSEThe following principle of decision making technique refers to taking a number of decisions based on its own logicLogic and intuition.BSP is the short form ofBusiness Systems Planning.Decisions could be divided into following two categoriesProgrammed. , Non programmed.The techniques used for non programmed decisions areJudgment. , Intuition. , Business acumen.Decision trees could be represented in different ways such asBottom to top. , Left to right. , Top to bottom.End - Means analysis is a technique used for determining information requirement of the organization atdepartment or individual mangers level.TRUEThe science of communication and control is known as .Cybernetic.Objects can communicate with each other throughFunctionsConversion is possible only after the following procedures are completeTesting , File building , User trainingIn OOP inheritance refers to the ability to take more than one form.FALSEExecutive Support SystemIs a non-flexible systemSome of the tools of Expert Systems areWAX , Expert EaseEIS facilitates access from many places. This is characteristic.User-InterfaceEIS enables to address adhoc queries. This is its characteristic.
capabilityEIS provides access to historical data. This is its .capabilityCriticism free idea generation is a factor of .GDSSThe information contained in the data dictionary isName of data item. , Source of data. , KeywordDatabase is pivotal to .MISDiscovering unknown associates is result of one of the following:Data MiningStructure of data inside the data warehouse consists of one of the following:Current detail dataData Mining is information tool.AnalysisData Mining is also known as database.Knowledge DiscoveryUnauthorized reading of data comes under one of the following:Information BreachDSS provides withraw data and status access , general analysis capabilities , representation modelsis a of data organized to service many users at the same time.DatabasecollectionBoth IT and business units must be involved in the data warehouse project for its successTRUEThe rules that govern how a network is setup is called itsTopologyBSPBusiness Systems PlanningSome of the major components that composes DSS arehardware , user system interface , database and its managementInformation requirement within organization aredifferent
This OS can provide mainframe-like computer power for new applications with massive memory and fileWindows NTData Miningall of the aboveEIS /ESS cannot utilize hypertext and hypermediaFALSEIt is the non-trivial extraction of implicit, previously unknown and potentially useful information from the dataoptions b and cconsists of , which enable end-users and programmers to extract data from database.DMLcommandsThe decides which computer resource will be used, which programs will be run and the inwhich activities will take place.operating systemsequencecompetition has increased and these standards are not static.Globalperformance standardsIDs that have not been used in a predefined period of time should be disabledTRUEThe different types of models used by DSS areOperations research model , Behavioral model , Management science modelprovides a generalized computing and telecommunications capacity that can be applied to a changingEISMIS need not be compatible with the organizations structure and culture.FALSEEIS facilitates aggregated and context data. This is its .benefitThe control system should be definite and determinable. This is done under one of the following:Objective.The are interactive information systems that rely on an integrated set of user friendly hardware andDSSOne of the following is the decision tool that helps in summarizing the interactions of various alternative actions ofPay off matrix.Expert systems lack human self-awareness and self analysis tool.
TRUEEIS enables to address adhoc queries. This is its characteristic.capabilityCharacteristics of GDSS are as followsAutomated record keeping , Parallel communication , Anonymous inputsThe is the component of communication to which information is transferredReceiverThe primary goal of one of the following system is to obtain data from a variety of sources, integrate andaggregate the data and display resultsESSData Warehousing is seen as a Data Arrangement technology adopting one of the following:Up-date approachThe Competitor Master Entry Screen consists of .Brand NameData Mining is information tool.AnalysisDecisions could be divided into following two categoriesProgrammed. , Non programmed.The product assurance discipline of the discipline triangle will includequality assurance , test and evaluation , configuration managementClasses are user defined data types.TRUEData warehouse is organized according to application.FALSEThe IDE was developed by GE under the leadership of Charles Babbage.FALSEA data warehouse typically starts with one of the following type of database:Very largeTrained facilitator is a of GDSS.ComponentAI is the short form ofArtificial Intelligence.One of the following consumes shelf space, has a shelf life and has a physical unit of measureproduct
The characteristics of EIS / ESS areInformation characteristics , User-interface / orientation characteristics , Managerial executive characteristicsCriticism free idea generation is a factor of .GDSSSelect, train and the employees to work for the customers is a principle stated by Tom Peters in "TheEmpowerThe strategy formulation and implementation depends a lot on the information onsocio-economic changes , new demands arising out of these changes , changing technologyThe software quality capabilities ensure that software is:reliable , doing what it is supposed to do , doing efficientlyData dictionary is the 3rd component of the DBMS.TRUEOne of the following sub-systems of the dialogue management component of the DSS programs checks the usercommands for correct syntax.User interfaceESS/ EIS is normally developed to assist the operation level decision making.FALSEDialogue management components of DSS program is a set of programs that manages user interface.TRUEThe Stock Value details are given to by KardexAccountsIf the central hub in star topology breaks down thenThe network stops working.Type of system which is practical, specific and operational is one of the following:Empirical.Social and machine are types of systems.TRUEThe marketing service system will provide the facility of re-opening enquiries received from distributors orTRUESome of the advantages of prototyping areTrying out ideas without incurring large costs , Reduced application development time , Reduced maintenanceThe different forms of authorization for access of database areread authorization , index authorization , update index authorizationOne of the following is a core application of Back OfficeHospital billing and recovery
Following are the components of communicationSender. , Receiver. , Medium.CASE tools canGive standardization based on single method , Generate data modelsFor arriving at the CSF the technique usually used isPersonal interview.Data miningIs an information analysis tool that evolves the automated discovery of patterns and relationships in a datawarehouse. , Encompasses a number of technical approaches such as clustering, data summarization . , Is theprocess of discovering meaningful, new correlation patterns and trends.One of the following person's signature is required on the "Goods Receipt Note"Stores In-Charge.The functions of the data dictionary areIt defines data elements. , It permits users to know which data is available. , It helps in scheduling and control.The is the component of communication through which information is transferred.MediumThe commands received from the management components are delivered either to the model basemanagement system or the mode execution system.dialogueInternet connections should be protected byfirewallOne byte is made ofEight bits.The weakness of pay off matrix is that itDepends on decision makers judgment.One of the following is the first component of DBMSDDLFollowing statements are true with the ALUArithmetic processing is done by it. , Logical decisions are taken by it.Logical decisions are taken by it. , Arithmetic processing is done by it.One of the following reference models has served as one of the most basic yet essential elements of computerOSIEIS/ESS cannot utilize hypertext and hypermedia.FALSEInformation and information technology help create / spawn business within old ones.
TRUEInterpreter translates each source code one at a time into machine code.TRUEWhile developing programs and procedures due attention is paid to .DocumentationEIS/ESS improves user productivity.TRUEThe user interface characteristics of EIS/ ESS will includeGUI , Access from many places , Secure reliable and confidential accessThe back bone of any organization isinformationSome of the factors that influence the success of GDSS are:Improved pre-planning , Access to external information , Increased participationprocess is one of the process in Data WarehousingAgingThe data bus transmits signals for locating a given address.FALSEEncapsulation refers to wrapping of data and functions into Class.TRUEThe formal language used by the computer professionals to specify the contents and structure of the databaseDDLSome of the storage devices areMagnetic tape. , Magnetic drum. , Optical disk.The integrated circuits / chips were made by printing thousands of tiny transistors on small silicon chips,semi-conductors.The feasibility mainly examines whether the proposed solution is desirable within the availableOperationalWhat denotes the hierarchy of and organizationorganization structureOne of the following is the non-trivial extraction of implicit, previously unknown and potentially useful informationData warehousing.The database model that represents data in a pyramidal or tree like structure is .Hierarchical
The layer of the OSI is an end user application and functions for particular application services such asfile transfer, remote file access.applicationThe aims of the purchase management system areReduce book keeping efforts. , Provides better interface with other systems. , Maintains an organizational levelES is the short form ofExpert SystemsThe goods receipt report generated by the inventory management system isItem wise goods receipt. , Supplier wise goods receipt.The specialized language used by end users and programmers to manipulate data in the database is .DMLData processing steps would involveRead. , Sort. , Compare.The flow of information through MIS isneed dependentData dictionary provides withReport facility. , Control facility. , Expert facility.Data wareh
The information contained in the data dictionary is Name of data item. , Source of data. , Keyword Database is pivotal to_. MIS Discovering unknown associates is File Size: 2MBPage Count: 964