Transcription
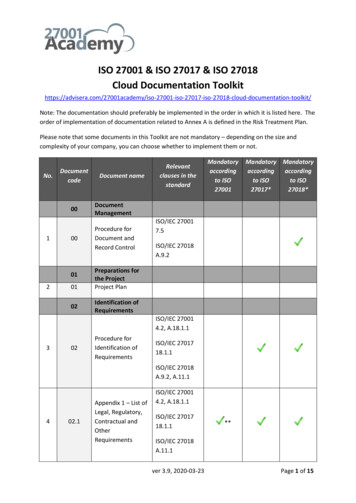
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 1 of 7PurposeThis document highlights where our documentation templates meet the requirements of ISO 27001:2013 and address thecontrols of Annex A and ISO 27002:2013.Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereDocument NameISO 27001Req.PrefixTypeDoc Ref.Context of OrganisationMSSDOC4.14.1Identification of Interested Parties ProcedureMSSDOC4.24.2Legislation and RegulationMSSREC4.24.2Scope StatementMSSREC4.34.3Integrated Management System PolicyMSSDOC5.25.2Information Security PolicyISMSDOC5.25.1-5.2Roles and Responsibilities Document Management ToolISMSREC5.35.3Risk Management ProcedureMSSDOC6.1ISMS PlanISMSDOC6Information Security Objectives and PlanningISMSDOC6.26.2Information Security ObjectivesISMSREC6.26.2Risk Management FrameworkRM-ISMSDOC6.1.16.1.1Risk Assessment ProcedureRM-ISMSDOC6.1.26.1.2Risk Assessment ToolRM-ISMSDOC6.1.2A6.1.2Statement of Applicability Work InstructionRM-ISMSDOC6.1.3D6.1.3DStatement of Applicability ToolRM-ISMSRisk Treatment PlanRM-ISMSAA Controls MappedSection 4Section 55.1.1/5.1.2Section 6SoA ToolREC66.1.3D6.1.36.1.3IT Governance Ltd.PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
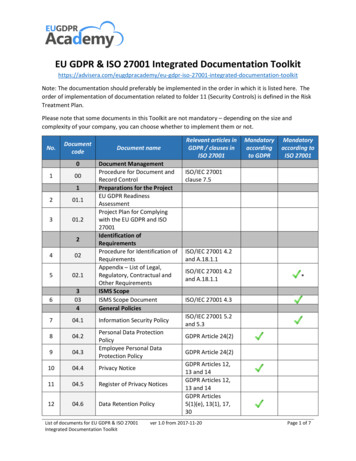
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 2 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereRisk ManagementControl A6 – Organisation of Information SecurityContact with AuthoritiesISMS-CDOC6.1.36.1.3/6.1.4Teleworker SecurityISMS-CDOC6.2.16.2.1Notebook Computer SecurityISMS-CDOC6.2.26.2.2Teleworker ChecklistISMS-CREC6.1.36.1.3/6.1.4Teleworker User AgreementISMS-CDOC6.2.2A6.2.2Schedule of Authorities and Key SuppliersISMS-CREC6.2.2B6.2.2HR Department RequirementsISMS-CDOC7.1Personnel Screening RequirementsISMS-CDOC7.1.17.1.1Employee TerminationISMS-CDOC7.3.17.3.1/8.1.4Termination ChecklistISMS-CREC7.3.17.3.1/8.1.4Asset Inventory & OwnershipISMS-CDOC8.1.18.1.1/8.1.2Internet Acceptable Use PolicyISMS-CDOC8.1.38.1.3Rules of Email UseISMS-CDOC8.1.3A8.1.3/13.2.1/13.2.3Email Box ControlISMS-CDOC8.1.3BPostal ServicesISMS-CDOC8.1.3CVoicemailISMS-CDOC8.1.3DFax sISMS-CDOC8.1.3F8.1.3/8.2.3Information Security ClassificationISMS-CDOC8.28.2.1/8.2.2/8.2.3Media & Handling of rmation Hardware AssetsISMS-CREC8.1.18.1.1/8.1.2Software LogISMS-CREC8.1.1A8.1.1/8.1.2Control A7 – Human Resource SecurityControl A8 – Asset ManagementIT Governance Ltd.8.1.3/8.2.3/8.3.3PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
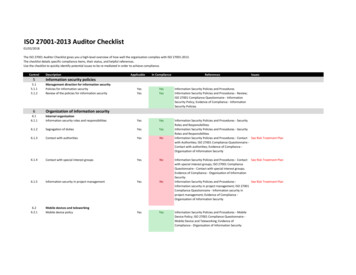
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 3 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereInformation Assets DatabaseISMS-CREC8.1.1B8.1.1/8.1.2Intangible AssetsISMS-CREC8.1.1C8.1.1/8.1.2Information Assets for RemovalISMS-CREC8.3.18.1.3/8.2.3/8.3.3Access Control PolicyISMS-CDOC9.1.19.1.1Access Control Rules & ndividual User AgreementISMS-CDOC9.2.1A9.3.1/11.2.9User Access 2.5/9.2.6/9.4.3Username AdministrationISMS-CDOC9.2.3A9.2.1/9.4.3Wireless User AddendumISMS-CDOC9.2.3BMobile Phone AddendumISMS-CDOC9.2.3CSecure LogonISMS-CDOC9.4.29.4.1/9.4.2/13.1.1/13.1.2Use of System UtilitiesISMS-CDOC9.4.49.4.4User Deletion RequestISMS-CREC9.2.19.2.1User Replacement Password RequirementISMS-CREC9.4.2Cryptography Key ManagementISMS-CDOC10.1.210.1.2/18.1.5Required Cryptographic ControlsISMS-CREC10.1.118.1.5Physical Entry ControlsISMS-CDOC11.1.211.1.2/11.1.3/11.1.5Fire Door MonitoringISMS-CDOC11.1.2A11.1.1/11.1.2/11.1.3Fire Alarm MonitoringISMS-CDOC11.1.2B11.1.1/11.1.4Burglar Alarm MonitoringISMS-CDOC11.1.2C11.1.1/11.1.4Reception AreaISMS-CDOC11.1.2D11.1.1/11.1.2Public AccessISMS-CDOC11.1.611.1.6Equipment /11.2.8Control A9 – Access ControlControl A10 – CryptographyControl A11 – Physical and Environmental SecurityIT Governance Ltd.PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
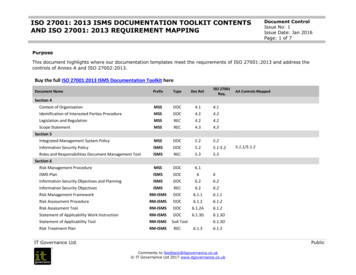
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 4 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereFire SuppressionISMS-CDOC11.2.1A11.1.4/11.2.1/11.2.4Air ConditioningISMS-CDOC11.2.1B11.2.4Standard ConfigurationISMS-CDOC11.2.4Removal of Information Security .2Storage Media DisposalISMS-CDOC11.2.711.2.7Physical Perimeter ation Security Assets for DisposalISMS-CREC11.2.711.2.7Documented ProceduresISMS-CDOC12.1.112.1.1Control of Operational SoftwareISMS-CDOC12.1.1A12.5.1Change Control 2System Planning and .9/14.3.1Operational Test and Development EnvironmentISMS-CDOC12.1.412.1.4Policy Against MalwareISMS-CDOC12.2.112.2.1Controls Against MalwareISMS-CDOC12.2.1A12.2.1Anti-Virus SoftwareISMS-CDOC12.2.1B12.2.1Backup ProceduresISMS-CDOC12.3.112.1.1/12.3.1Information Security .1Software InstallationISMS-CDOC12.5.1Vulnerability ManagementISMS-CDOC12.6.1System Auditing ProcedureISMS-CDOC12.7.112.6.1/12.7.1Log of Change RequestISMS-CREC12.1.2A12.1.2Change RequestISMS-CREC12.1.212.1.2Audit Log RequirementISMS-CREC12.7.112.6.1/12.7.1Monitoring RequirementISMS-CREC12.4.1Administration and Operational LogISMS-CREC12.4.3Control A12 – Operations SecurityIT Governance Ltd.12.4.3/12.6.2PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 5 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereControl A13 – Communications SecurityNetwork Controls and ServicesISMS-CDOC13.1.113.1.1/13.1.2Network Access Control PolicyISMS-CDOC13.1.39.1.2/13.1.1Network Access Control 3/13.2.1Telecommunications ProceduresISMS-CDOC13.2.113.2.1Confidentiality AgreementsISMS-CDOC13.2.413.2.4Control A14 – System Acquisition, Development and MaintenanceeCommerce & Online TransactionsISMS-CDOC14.1.214.1.2/14.1.3Secure Development PolicyISMS-CDOC14.2.114.2.1Secure Development ProcedureISMS-CDOC14.2.1AInformation Security Policy for Supplier RelationshipsISMS-CDOC15.1.1Third Party Service al 15.2.2Reporting Information Security Weaknesses & EventsISMS-CDOC16.1.2-3Responding to Information Security 16.1.6Collection of EvidenceISMS-CDOC16.1.716.1.7Information Security Event ReportISMS-CREC16.1.2-3A16.1.3/16.1.4Information Security Weaknesses and Events RecordISMS-CREC16.1.2-3B16.1.3/16.1.4Control A15 – Supplier RelationshipsControl A16 – Information Security Incident Management16.1.1/16.1.2/16.1.3/18.2.3Control A17 – Information Security Aspects of Business Continuity ManagementInformation Security Continuity tion Security Continuity n Security Risk AssessmentISMS-CDOC17.1.217.1.1Information Security Continuity TestingISMS-CDOC17.1.317.1.3/17.1.1Control A18 – ComplianceIT Governance Ltd.PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 6 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereIntellectual Property RightsISMS-CDOC18.1.2A18.1.2IPR ComplianceISMS-CDOC18.1.2B18.1.2Control of RecordsISMS-CDOC18.1.3Retention of RecordsISMS-CDOC18.1.3A18.1.3Data Protection & PrivacyISMS-CDOC18.1.418.1.4Organisational PrivacyISMS-CDOC18.1.4A18.1.4Terms and Conditions of Website UseISMS-CDOC18.1.4B18.1.4Internal Independent ReviewISMS-CDOC18.2.118.2.1Compliance and Checking ProcedureISMS-CDOC18.2.218.2.2/18.2.3Obligations ScheduleISMS-CREC18.1.118.1.1Competence ProcedureMSSDOC7.27.2Hiring and New Starters ProcedureMSSDOC7.2.27.2Training and Development ProcedureMSSDOC7.2.37.2Leavers ProcessMSSDOC7.2.47.2Awareness ProcedureMSSDOC7.37.3Communication ProcedureMSSDOC7.47.4Document ControlMSSDOC7.5.37.5.3Information Security Manager Job DescriptionISMSREC7.2.1A7.2.1Head of Risk Job DescriptionISMSREC7.2.1B7.2.1Chief Information Security Officer Job DescriptionISMSREC7.2.1C7.2.1Competence MatrixMSSREC7.2Job DescriptionMSSREC7.2.17.2.1Induction ChecklistMSSREC7.2.27.2.2Training Record MatrixMSSREC7.2.37.2.3Master List of ProceduresMSSREC7.5.3A7.5.37.5.318.1.3Section 77.2IT Governance Ltd.PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
ISO 27001: 2013 ISMS DOCUMENTATION TOOLKIT CONTENTSAND ISO 27001: 2013 REQUIREMENT MAPPINGDocument ControlIssue No: 1Issue Date: Jan 2016Page: 7 of 7Buy the full ISO 27001:2013 ISMS Documentation Toolkit hereMaster List of RecordsMSSREC7.5.3B7.5.3MSSDOC8.18.1Performance Evaluation ProcedureMSSDOC9.19.1Internal Audit ProcedureMSSDOC9.29.2Management Review of the Information Security PolicyMSSDOC9.39.3Monitoring and Measurement RegisterMSSREC9.19.1Internal Audit ScheduleMSSREC9.2.19.2Internal Audit Report Lead SheetMSSREC9.2.29.2Management Review RecordMSSREC9.39.3Non Conformity ProcedureMSSDOC10.110.1Continual ImprovementMSSDOC10.210.2Corrective Action ReportMSSREC10.1.110.2Non Conformance ReportMSSREC10.1.1A10.1Section 8Operational ControlSection 95.1.1/5.1.2Section 10Non Conformance Report LogMSSREC10.1.1B10.1For more information on how to buy this ISO 27001:2013 ISMS Documentation Toolkit and see how it benefits yourorganisation contact us viaE-mail: servicecentre@itgovernance.co.ukPhone: 44 (0) 8450 701 750IT Governance Ltd.PublicComments to feedback@itgovernance.co.uk IT Governance Ltd 2017 www.itgovernance.co.uk
This document highlights where our documentation templates meet the requirements of ISO 27001:2013 and address the controls of Annex A and ISO 27002:2013. Buy the full ISO 27001:2013 ISMS Documentation Toolkit here Document Name Prefix Type Doc Ref. ISO 27001 Req. AA Controls Mapped Section 4 Context of Organisation MSS DOC 4.1 4.1File Size: 444KBPage Count: 7