Transcription
The Complete ISMS ToolkitThe ISMS solution from your ISMS partner
What is Information Security? The use of an ISMS (Information Security Management System)for the systematic preservation, in an organization, of �All information systems have vulnerabilities that can be exploited bythreats in ways that can have significant impacts on theorganization‟s effectiveness, profitability, value and long termsurvivalOf its information (and its information systems)Information risk External threats (hackers, terrorists, viruses, spam,competitors, cyber-criminals, Acts of God, etc)Internal threats – fraud, error, unauthorized or illegalsystem use, data theftSystem failure – hardware failure, power outages, suppliersAlso significant regulatory & compliance issues6 May 2008 IT Governance Ltd 2005 -20082
What is an ISMS? A defined, documented management system (within a definedorganization, the „scope‟)––––A board information security policyA corporate risk treatment planAn inventory of information assets (data and systems) that fall within the scopeAn assessment of vulnerabilities, threats and risks („risk assessment‟) to thoseassets– A Statement of Applicability identifying a set of controls (responses to/countersfor risks) that respond to the risks– A comprehensive suite of processes, policies, procedures & work instructions The ISMS must be– Implemented and managed– Reviewed, audited and checked– Continuously improved Certification––––Valuable but not always essentialThe final stageCarried out by a third party certification bodyEvidence as to the completeness and quality of the ISMS6 May 2008 IT Governance Ltd 2005 - 20083
What are BS7799 and ISO17799? Two interlinked standards– ISO27001 specifies how to design an Information SecurityManagement System („ISMS‟) How the ISMS should work, not what should be in it Replaced BS7799– ISO27002:2005 is an international code of practice for informationsecurity best practice that supports and fleshes out ISO27001 What should be in the ISMS, not how it should work Management system standards ––––Technology y similar to ISO9000Internationally understoodCapable of external certificationCommonly accepted best practice200 new ISO27001 certifications/month8 May 2008 IT Governance Ltd 2005 - 20084
Business drivers1. Implement information security best practice Security of corporate information assetsProtection of corporate reputationMeet governance and regulatory compliance requirementsImprovement in effectiveness of corporate ITinfrastructureCorporate quality assurance2. Drive for certification Demonstrating best practiceCorporate positioningCustomer/partner requirementGovernment/funder requirement3. A combination of the above 8 May 20081 & 2 are not incompatible! IT Governance L td 2005 - 20085
How do we create an ISMS? PDCAPLAN Identify assets, scope, carry out riskassessment, create policies,processesACTCHECKPLANDODO Implement the defined and agreedprocesses No action required for acceptedrisksCHECK Assess performance against definedpoliciesACT Take corrective and preventiveaction to continually improve theoperation of the ISMS8 May 2008 IT Governance Ltd 2005 - 20086
The ISMS Project Roadmap8 May 2008 IT Governance Ltd 2005 - 20087
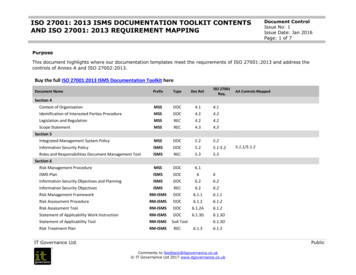
ISMS Documentation Requirements Must be company-wideMust be cross-functionalMust be management-ledWill have significant internal linkages and cross-references Must comply with ISO27001specificationMust reflect ISO27002:2005 guidanceRequires four levels of documentation ––Essential for effectiveness, internal coherence and consistencyMust ensure there are no information security gaps–Board approves level 1: Corporate policy, risk treatment plan, Statement of Applicability (134controls), ISMS manualExecutive approves level 2: proceduresLine managers approve level 3: operations/work instructionsLevel 4 documents are records that do not need approval–––Must reflect Plan-Do-Check-Act (PDCA) cycleMust be continuously improved8 May 2008 IT Governance Ltd 2005 - 20088
Two project approaches Sequential mini-PDCA cycles– Massively parallel implementation– Tackling either sub-units (divisions, geographies, etc) of the whole organization or specificcontrol areas (prioritized through a high level risk assessment)Designed to get the whole organization to project completion quickly and completelyIssues:–Procedure overlap, procedure and work instruction cross-referencing –one work instruction or procedure may need to meet the requirements of a number of controlsOne control may require a range of procedures and work instructions that affect a diversity of functionalareas within the organizationEach procedure and work instruction needs to be aligned with all the others, for coherence and consistencyand to ensure there are no security gapsOnly the ITG Complete ISMS Toolkit enables an organization to proceed safely witheither approach 8 May 2008Overlaps identified and dealt withCross references already in-builtAll policies, procedures and work instructions are alignedInternal coherence and consistency is assuredAll tools designed to be interoperable IT Governance Ltd 2005 - 20089
Time to certification/completion In a mid-size company that already has areasonable security posture Massively parallel approach Assuming management commitment, projectprioritization, training and adequate resourcing– „DIY‟ approach Time required: 14 – 19 months– Consultant-led approach Time required: 10 – 14 months– ITG Fast Track approach Time required: 8 – 12 months8 May 2008 IT Governance Ltd 2005 - 200810
„DIY‟ Methodology: trial and errorAverage time to completion: 14-19 months –understanding requirements: 1 monthProject planning: 1 monthDrafting corporate policy and project team training: 1 monthRisk assessment and Statement of Applicability: 2 monthsDrafting procedures: 3-5 monthsDrafting operations/work instructions: 4-8 monthsImplementation (Do), audit and review (Check) and improvement (Act): part parallel, plus 2monthsTime requirementAbsence of best practiceUncertain PDCA cycleLikely to be inadequately led, not cross-functional, not company-wideHigh likelihood of project failureContinuing, real Information Security exposures8 May 2008 IT Governance Ltd 2005 - 200811
Consultant-led Methodology: deploy external expertiseAverage time to certification: 10-14 months Advantages: –––––––––Understand policy: 1 weekProject planning: 1 weekDrafting corporate policy and project team training: 1 monthRisk assessment and Statement of Applicability: 2 monthsDrafting procedures: 2-4 monthsDrafting operations/work instructions: 3-5 monthsImplementation (Do), audit and review (Check) and improvement (Act) in parallel, plus 2 months–FasterWill contain some best practicePDCA cycle and cross-functional, company-wide requirements should be metReduced likelihood of project failure–––Extensive consultant time, expenseNo continuous improvementContinuing, real information security exposuresDisadvantages:8 May 2008 IT Governance Ltd 2005 - 200812
ITG Fast Track Methodology: deploy IIT Governance Complete ISMS ToolkitAverage time to certification: 8-12 months Advantages:–––––––Understand policy: 1 weekProject planning: 1 weekDrafting corporate policy and project team training: 1-2 weeksRisk assessment and Statement of Applicability: 2-4 weeksDrafting procedures: 4- 6 weeksDrafting operations/work instructions: 2-4 monthsImplementation (Do), audit and review (Check) and improvement (Act) in parallel–Fit for purpose – designed to meet ISO27001/ISO27002 requirements from the outset––––––Fast to deployVery cost-effective (with low TCO and high ROI)Full of best practiceWill be cross-functional, company-wide, with correct PDCA cycleVery low likelihood of project failureContinuous improvement built in from the start How? Additional support:–––Massively parallel documentation draftingMultiple mini-PDCA cycles made possible by interlinked documentsNo trial and error –very little review, revision and correction required––ISMS Implementation Master ClassSpecialist consultant oversight and guidance8 May 2008 IT Governance Ltd 2005 - 200813
What is the Complete ISMS Toolkit? Standard templates with pre-written content Includes: ––Abstracted from multiple, successful ISMS deploymentsWith line-by-line instructions for, and guidance on, completion––––––Draft corporate policy (level 1)Draft Statement of Applicability, ISMS manual and policies (level 1)Draft of every procedure likely to be required (level 2)Operations/work instruction templates (level 3)Correct PDCA cycleProject tools included in the price Risk assessment/gap analysis toolTraining slidesAudit checklistSupported by:––––Detailed guidance of “IT Governance: a Manager‟s Guide to Data Security and ISO27001/ISO27003” (4 th edition) see www.itgovernance.co.uk/products/4 “A comprehensive guide as to actions that should be taken.” Nigel Turnbull, Chairman, Lasmo plc, authorof the Turnbull Report.Online access to additional, current material, including a glossaryUNIQUE e-mail fast response drafting supportOngoing Toolkit upgrades8 May 2008 IT Governance Ltd 2005 - 200814
Open University The Open University's post-graduate courseon information security management forinformation security professionals. M886:Information Security Management is basedon “IT Governance: a Manager’s Guide toData Security and BS7799/ISO17799” 2M886“The Calder and Watkins book underpinsprofessional practice in InfoSec Management.Following the standard, risk managementguidance is given for each InfoSec area,including the trade-offs that arise betweencovering a vulnerability and leaving ituncovered. For complete coverage of thestandard, this book is unparalleled, andthat's why we have chosen it as the basis forthe Open University's new InformationSecurity Management Course." Dr Jon G Hall,Lecturer in Information Security, OpenUniversity, UK8 May 2008 IT Governance Ltd 2005 - 200815
Who are IT Governance Ltd? Governance, risk management, compliance and information securityspecialistsDeep expertise in management of governance, quality systems,information technology and information securityMultiple successful ISMS deployments in both public and private sectorsCertification body and ISMS international user group membersDelivering a growing range of IT governance and information securitybooks, tools and support servicesStrategic approach to product developmentFostering long term client relationships24 May 2005 IT Governance Ltd 200516
What next?BUY ONLINE Standalone Documentation Toolkit - just the ISMS documentation, or The No 4 ISMS Toolkit contains, in addition to the Documentation Toolkit,IT Governance: a Manager's Guide to Data Security and ISO27001/ISO27002, 3rd edition (ITG4)A comprehensive online information security glossary The No 5 ISMS Toolkit contains, in addition to the contents of the No 4 Toolkit ,Copies of both ISO 27001 and ISO 27002 The No 1 ISMS Toolkit contains, in addition to the contents of the No 5 Toolkit,BS7799-3, the risk assessment standard The No 3 ISMS Toolkit contains, in addition to the contents of the No 1 Toolkit,vsRisk , the definitive ISO27001 risk assessment tool The No 2 ISMS Toolkit is the same as the No 3 Toolkit, except that it doesn't containthe three information security standards.ALSO CONSIDER THE ISO27001 ISMS IMPLEMENTATION MASTER CLASS8 May 2008 IT Governance Ltd 2005 - 200817
The No 3 ISMS Toolkit contains, in addition to the contents of the No 1 Toolkit, vsRisk , the definitive ISO27001 risk assessment tool The No 2 ISMS Toolkit is the same as the No 3 Toolkit, except that it doesn't contain the three information security standards. ALSO CONSIDER THE ISO27001 ISMS IMPLEMENTATION MASTER CLASSFile Size: 248KBPage Count: 17