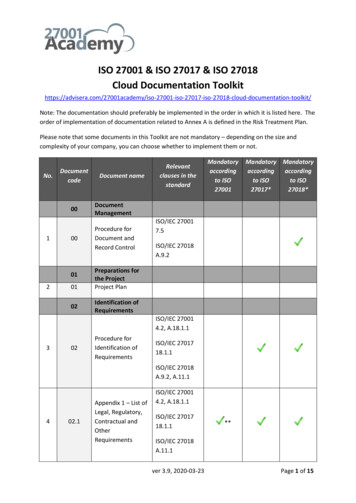
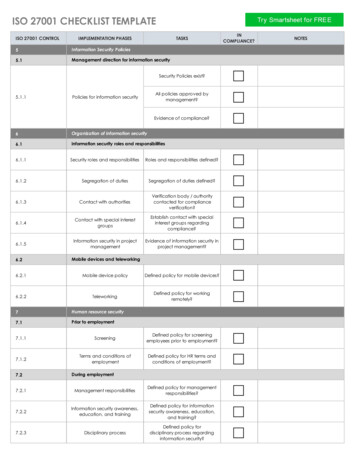
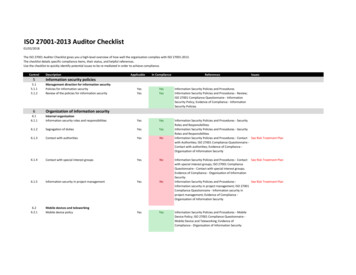
Transcription
ISO oachJune 2016ISMS ApproachPage 1
CONTENTSSectionPage No.1. Introduction32. Project Methodology93 Our Approach11Appendix A : Company ProfileISMS ApproachPage 2
1. INTRODUCTIONISMS ApproachPage 3
EMERGING THREAT LANDSCAPE Lack of awareness for today’sthreat landscapeLack of skilled resourcesPoorly defined security roles andresponsibilitiesPoor patch-management processesAd hoc processes and procedures formanaging operationsLack of post-incident “lessons learned”disciplineProcessPeopleTechnology ISMS ApproachPage 4Disruption of ServicesExposure to targeted attacksLoss of ReputationPoorly integrated anddeployment of securityproductsInability to discoversophisticated attacktechniquesLack of threatintelligence capabilities
What is ISMS? An ISMS enables an organization to systematically create and operate amanagement system for information security. By establishing an ISMS, an organization can initiate a formal process tohelp it determine the necessary security level requirements, create plansbased on Risk Assessment and selectcountermeasures to mitigateUnacceptable Risk. With an ISMS, an organization can maintain andimprove Confidentiality, Integrity, and Availability of its informationalassets. In particular, by measuring the effectiveness of controls implementedthrough risk assessment within the ISMS, an organization is able toimprove its information security in an efficient and effective manner. The most popular ISMS follows the ISO 27001 standard which offers aninternational certification scheme.ISMS ApproachPage 5
ELEMENTS OF SECURITYISMS ApproachPage 6
CONTROLS (ANNEX A and ISO/IEC 27002)ISMS ApproachPage 7
MANAGEMENT COMMITMENT IN SECURITY IMPLEMENTATIONISMS ApproachPage 8
2.PROPOSED METHODOLOGYISMS ApproachPage 9
OUR METHODOLOGY FOR ISMS PDCA Approach Plan Phase : conduct gap analysis and provide road map forISO 27000 implementation. Do Phase : Improve all ITSM documentation including policiesand procedures, Risk analysis according to ISO 20000 andassist in implementation Check Phase : ITSM internal audits, coordination duringcertifying audit Act Phase : post audit follow-up (including CAPA reports andassistance in implementation to close the audit points)ISMS ApproachPage 10
3.OUR APPROACHISMS ApproachPage 11
OUR APPROACH FOR ISMSPHASE 1PLANPHASE 2PHASE 3PHASE 4DOCHECKACTOUR APPROACHUnderstand businessprocessesPerform ISMSImplementation TrainingFinalize on the ISMS ScopeAssist in performing AssetInventoryReview of ControlsAssist in preparing theInformation Risk ManagementPerform ‘As-Is’ analysis (CurrentState Assessment)Perform VulnerabilityAssessment and PenetrationTestingPlan for ISO 27001:2013ImplementationDiscuss Internal AuditFindings with ISMSCoordinatorAssist in preparing AuditResponse PlanDrafting necessary InformationSecurity PoliciesAssist in Implementation ofInformation Security PoliciesISMS ApproachPage 12Perform ISMS Internal AuditPrepare Corrective andPreventive Action ReportsAssist in implementationof Audit Response Plan
PHASE 1- PLANObjective: To conduct Gap Analysis and prepare plan for implementation of ISMSActivities Understand the core and supporting business functions Understand and discuss the information security requirements of the organization Finalize on the ISMS Scope Review security architecture Review existing documents like policies, procedures, forms etc related to ISMSDeliverables Gap Analysis Report including a broad roadmap for ISMS.and other certification achieved by an organization. Perform ‘As-Is’ analysis (Current State Assessment)Client Requirements Provide Business Objectives, Provide information on Critical business processes, critical IT Processes, QualityProcesses Existing P&P Existing security processes, service processes and documentationISMS ApproachPage 13Expected Duration Based on Scope
PHASE 1- SAMPLE DELIVERABLESISMS ApproachPage 14
PHASE 2- DOObjective: To Improve ISMSActivitiesDeliverables Performing ISMS training Finalize ISMS Documentation Reviewing existing asset management practices Do Handholding in ISMS Improvement Updating and improving existing Information Security Policies Assistance in improving of Information Security Policies Assist in improving the Service Risk Management ;Client Requirements Documentation and Technical details where necessaryISMS ApproachPage 15Expected Duration
PHASE 2- SAMPLE DELIVERABLES FOR ISMS TRAININGISMS ApproachPage 16
PHASE 3- CHECK (INTERNAL Audit ISMS )Objective: To conduct Internal Audit to assess the preparedness for ISO 27001:2013 CertificationActivitiesDeliverables Management Review meeting on Gap Analysis Internal Audit Report Management Discussion on implemented policies & procedures Corrective and Preventive Action Reports Perform ISMS Internal Audit Discussing Internal Audit Findings with ISMS co-coordinators Assist in preparing Audit Response Plan Prepare Corrective and Preventive Action ReportClient Requirements Provide information on Critical business processes, critical IT Processes Necessaryreports Existing Documentation and RecordsISMS ApproachPage 17Expected Duration
PHASE 4- ACT (POST AUDIT FOLLOW-UP)Objective: To maintain and improve ISMSActivities Assist in implementation of Audit Response Plan (Corrective and Preventive ActionDeliverables High Level Recommendation on emailReports)Client Requirements List on implementation done base on recommendationsISMS ApproachPage 18Expected Duration
CERTIFICATION AUDIT BY AUTHORATATIVE BODY*Objective: Calling authoritative body and award CLIENT with its ISO 27001 CertificateActivities Calling the external certification authority for performing ISO27001 auditDeliverables ISO 27001 Certification upon successful completion of the audit.(Surveillance Audit)Client Requirements Expected DurationClosure of all gaps identified in the Audit Report*ISO 27001 Certification Audit will be conducted by an external certifying authority.ISMS ApproachPage 19
APPENDIX A - COMPANY PROFILE - INFOPERCEPTISMS ApproachPage 20
ABOUT INFOPERCEPT Infopercept is a unique combination of young and enthusiastic blood, with a fire in our belly and arementored by Industry highly experienced veterans. we are executing varied (3600) projects and tasks, with emerging technologies and innovativethought process, to design and deliver a complete package of quality, efficiency and effectivenessbased on Quality Assurance theorem. Infopercept epitomize on all kind of projects of Information Technology and Information Technologyenabled projects which are on high demands these days.VisionInfopercept is built with Core vision to provide 360 degree technology expertise and deliverquality services globally by harmonizing though three C’s - "Creativity”, “Competency", and"Cost“.MissionInfopercept is firmly emerging with the lightning speed as we strongly believe in customersatisfaction and service excellence supported by our 3 Pillars - "People", "Process" and"Professionalism".Core ValuesInfopercept most valuable Asset is our People Team, who has passion to help our clients buildbusiness success and deliver all projects with three E's - "Efficiency”, “Effectiveness” and“Enthusiasm”.ISMS ApproachPage 21
Thank You!Regd. Office: INFOPERCEPT CONSULTING PRIVATE LIMITED 43 HARIOM VILLA, NEAR ISCONFLOWER, BOPAL, AHMADABAD - 380054, Gujarat, INDIAWebsite: www.infopercept.comEmail: jitenb@infopercept.com; jayeepr@infopercept.comISMS ApproachPage 22
ISO 27000 implementation. Do Phase : Improve all ITSM documentation including policies and procedures, Risk analysis according to ISO 20000 and assist in implementation Check Phase : ITSM internal audits, coordination during certifying audit Act Phase : post