Transcription
Project Manager User GroupProject Management and SecurityMay19, 2021Bryant Lister, CISSP, PMPOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office
Bryant Lister is the Chief Information Risk Officer fromODHS/OHA Received PMP about 8 years ago Received CISSP early in 2020 (right before pandemicshutdown) Been an application developer, system analyst, projectmanager, development manager, strategic manager Director of the Information Security & Privacy Office inthe Office of Information Services for ODHS/OHAOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office2
What we will discuss today Project Management & Security Triangles Shift Left Project Phases – where does Security fit in? Project Documents – writing about Security Security Controls Security Standards & Frameworks Regulatory Bodies & Data Types Data Acronyms & Terms Risk Management Consequences of not shifting left ResourcesOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office3
TrianglesProject ManagementOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office4Security
Shift Left Setup projects securelySecurity issues should be identified earlyLess cost to address/fix when found at the beginningSecurity incidents can have extreme costsProject WorkSecurityProblemsOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office5
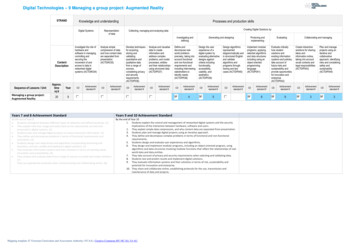
Project Phases – where does Security fit in?There is a role for security in every phase Scope – what overall level of security is needed? Requirements – detailed security plans and needs Implementation – apply security controls, test forvulnerabilities Reports – security findings, access controls End – remove security rights for project teamOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office6
Project Documents – writing about SecurityStandard docs Scope Plans Requirements WBS Schedule Contracts/Agreements Quality Metrics Risk RegisterSpecial docs PIA POAM SSPOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office7
Security Controls Doors Cameras Card readers Firewalls Passwords EncryptionOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office8 Policies Standards Dataclassification
Security Standards & FrameworksStatewide Information and Cyber Security Standards Created by Enterprise Information ServicesSecurity Control frameworks National Institute of Standards andTechnology (NIST) Center for Internet Security (CIS) CriticalSecurity Controls Control Objectives for Information andRelated Technology (COBIT) International Standards Organization (ISO)OFFICE OF INFORMATION SERVICESInformation Security & Privacy Office9
Regulatory Bodies & Data TypesOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office10
Data Acronyms & TermsPII, PCI, PHI, FTIData Levels 1, 2, 3, 4InferenceObfuscationOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office11
Risk ManagementMinimizing risk is an important part of securityOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office12
Consequences of not shifting left Project Delays and Increased Costs Security deficits cost more whenimplemented later Leaked project information Public perception degraded Integrity of project data Non-compliance with regulations andmandates Fines, penalties, rework Risks to information systems Breaches – loss of data privacy Malware – system disruption Service attacks – decrease availabilityOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office13
Resources DAS – Cybersecurity urity.aspx ISO 27001 A.6.1.5 Information Security in ProjectManagement Cybersecurity & Infrastructure Security Agency (CISA)https://us-cert.cisa.gov/ Certified Security Project Manager ldevelopment/cspm-certification/OFFICE OF INFORMATION SERVICESInformation Security & Privacy Office14
QuestionsOFFICE OF INFORMATION SERVICESInformation Security & Privacy Office15
Project Documents – writing about Security. Standard docs Scope Plans Requirements WBS Schedule Contracts/Agreements Quality Metrics Risk