Transcription
Utilizing the DoD PKI to Provide Certificates forUnified Capabilities (UC) ComponentsDISA NS2 Capabilities CenterNovember 3, 2011Revision 1.2
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011Change TableChangeRemoved references to “RTS” and replaced with “UC”Changed OCSP responder sections to reflect that ocsplegacy.disa.mil URL was deactivated on Nov 1, 2010. Only OCSPDTM is now supportedAdded IP addresses of OCSP responders corresponding toocsp.disa.mil URLAdded instructions for verifying CSRs using OpenSSLAdded an example action item register for all DoD PKI relatedactivitiesInserted warnings to backup the private keys associated with aCSRNoted that 2048 bit certificates are now the only ones that canbe ordered from the NIPRNET DoD PKI CAsCorrected the steps for retrieving ordered certificates from theCA websites and updated screenshotsAdded additional IP addresses for OCSP responders and CRLdistribution pointsAdded DISA RA Operations contact information for CSRssubmitted to DISAAdded information on OCONUS OCSP URLsAdded a more detailed diagram illustrating the OCSP delegatedtrust model (DTM)Added new section, 2.11, which describes the information thatmust be added to an IT helpdesk ticket to open up firewalls andweb proxies for OCSP and CRL requests/responsesUpdated IP addresses associated with the crl.disa.mil andcrl.gds.disa.mil CRL distribution pointsUpdated to address new CAs coming online in December 2011(CA-27, CA-28, CA-29, and CA-30), new static CRL URLs , andCRIMSON tool availabilityDateAuthorNovember 19, 2010DISA NS2 TeamMarch 17, 2011DISA NS2 TeamSeptember 7, 2011DISA NS2 TeamNovember 2, 2011DISA NS2 Team2
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011Table of Contents1Ordering Certificates from the DoD PKI .51.1Contacting Your Local Registration Authority to Expedite Service . 51.2Generating a Certificate Signing Request (CSR) . 61.2.1What Information is Required to Generate a Signing Request? . 61.2.2Using Commercial Tools or UC Equipment to Generate a CSR . 81.2.3How many certificates do I need to request? . 91.31.3.1Use of One DoD PKI Certification Authority Versus Another. 101.3.2Websites Used to Upload Certificate Signing Requests . 101.3.3Selecting the Certificate Profile . 111.3.4Uploading the PKCS#10 Certificate Signing Request . 121.3.5Adding Additional Identities to the Certificate . 131.3.6Inputting the Requester’s Contact Information. 141.3.7Confirmation of Your Submitted Request. 141.3.8Checking the Status of a Submitted Certificate Request . 151.4Submitting the Certificate Request to a Local Registration Authority. 151.4.1Tips for Expediting Your Certificate Request . 151.4.2Submitting the Certificate Request to the Air Force LRA . 161.4.3Submitting the Certificate Request to the Army LRA . 161.4.4Submitting the Certificate Request to the Navy LRA . 171.4.5Submitting the Certificate Request to the US Marine Corp LRA. 171.4.6Submitting the Certificate Request to the DISA Registration Authority . 171.4.7Submitting the Certificate Request for All Other Organizations. 171.5Loading the Trust Chains and CRL/OCSP Pointers into Equipment . 181.5.1Loading DoD PKI Trust Chains . 181.5.2Configuration of CRLs and OCSP Responders . 181.62Uploading the Request to the DoD PKI Certificate Authority . 10Retrieving and Loading Your DoD PKI CA Issued Certificate . 20Other Frequently Asked Questions . 222.1How can I contact the DoD PKI PMO to obtain assistance? . 233
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities Components2.2Certificate Revocation Lists (CRLs) . 232.2.1What is a Certificate Revocation List?. 232.2.2How can I obtain a Certificate Revocation List from the DoD PKI? . 232.2.3What If I Need an IP Address for the CRL Distribution Point? . 242.2.4Should I Use HTTP or LDAP to Retrieve CRLs? . 252.2.5How Often Should CRLs Be Retrieved? . 252.3Online Certificate Status Protocol (OCSP). 252.3.1What is OCSP? . 252.3.2What is an OCSP Responder?. 262.3.3What is the OCSP Delegated Trust Model (DTM)? . 262.3.4What are the URLs for the DoD PKI’s OCSP Responders?. 292.3.5What if I need an IP address for the OCSP Responder instead of a URL? . 292.3.6How can I obtain the self-signed certificate for the legacy OCSP responders? . 302.3.7Why do the OCSP Responders use HTTP instead of HTTPS? . 302.4Which is better: OCSP or CRLs? . 302.5Maintaining Valid DoD PKI Certificates in UC Equipment . 302.5.13Revision 1.2November 3, 2011How Often Do DoD PKI Certificates Need to Be Replaced? . 302.6Should I Order 2048 Bit Certificates or 1024 Bit Certificates? . 312.7Where Can I Obtain All of the DoD PKI Certificate Authority Certificates? . 312.8What if I Only Need Test Certificates? . 322.8.1Website for Submitting Certificate Requests to JITC . 322.8.2Submitting the Test Certificate Request to Your LRA . 322.8.3Downloading Test Trust Chains. 322.8.4JITC OCSP Responder . 332.8.5Points of Contact to Obtain Assistance with JITC Test Certificates . 332.9How Can I View Certificate Data Using the Windows Certificate Viewer? . 332.10How Can I Use OpenSSL To Validate and View Certificate Signing Requests? . 342.11What Do I Need to Tell My IT Staff to Allow Through Our Firewall? . 342.12Is There a Way To Request Certificates in Bulk? . 35Acronyms . 36Appendix A:Troubleshooting Tips . 38Appendix B:Example DoD PKI Action Item Register . 394
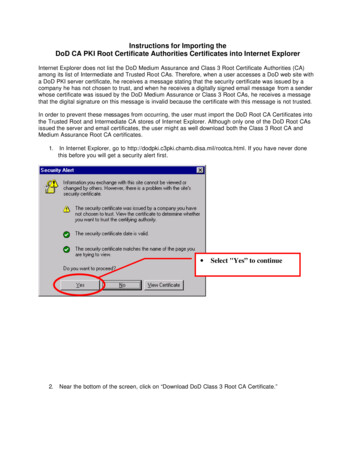
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 20111 Ordering Certificates from the DoD PKIUnified Capabilities (UC) equipment, including devices like Softswitches (SS), Local Session Controllers(LSC), End Instruments (EIs), and Edge Boundary Controllers (EBC) require the use of X.509 certificates toprovide confidentiality and establish mutually authenticated secure connections for telecommunicationssessions. The Department of Defense Public Key Infrastructure (DoD PKI), operated by the DefenseInformation Systems Agency (DISA), is expected to be the primary source for these certificates. In orderto successfully operate UC components using the DoD PKI, administrators must execute the followingfive steps:This step has the potential to cause the most delay. Please review Sections 1.1and 1.4.1 for more information on expediting this step.This guide is primarily designed to assist DoD personnel and hired technicians with obtainingoperational, DoD PKI issued, certificates for use in UC devices. This guide should not be used by thoseseeking to obtain DoD PKI issued certificates or tokens for human identification purposes (such asCommon Access Cards), since this process will differ. Also, for those who only need test (nonoperational) DoD PKI certificates, this information is located in Section 2.8.The six steps shown above illustrate the process for obtaining DoD PKI certificates at a high level. A moredetailed action item register has been added to Section 0 of this guide to assist UC site programmanagers with tracking all of the critical DoD PKI enablement actions.1.1 Contacting Your Local Registration Authority to Expedite ServiceTechnicians in the field requesting certificates for UC equipment have reported delays of several days ormore AFTER uploading the certificate request to the DoD PKI CA website. This delay stems from the timeit takes the Local Registration Authority (LRA) to approve the certificate request. The LRA is the primary“human element” involved in the approval process and all certificate requests must go through yourresident LRA. In order to expedite your certificate request(s), it is recommended that you call your LRAearly in the process, prior to submitting the certificate request(s), to find out if any options exist for5
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011expediting certificate generation service. This call will help to acquaint you with the LRA and help you tounderstand the submission process. Also, this call will provide early notice for the LRA so that theybecome aware of your pending request and make the appropriate preparations. Note that many LRAsrequire additional forms to be submitted before they approve the certificate request. Therefore, it isrecommended that certificate requesters fill out any such forms and return them as quickly as possibleto avoid delays with certificate delivery. Request these forms along with example, pre-filled forms ortemplates during your initial call to the LRA. It is recommended that this occur as the first step, ratherthan waiting until Step #4, where the LRA is contacted after the certificate signing request has beenuploaded. Section 1.4 contains the procedures for contacting your LRA.1.2 Generating a Certificate Signing Request (CSR)1.2.1What Information is Required to Generate a Signing Request?When a UC component communicates with a remote device, the remote device requires authenticationbefore permitting access to its services. In this case, the UC component must present a set ofcredentials, which can be verified by the remote device, in order to prove its identity. In other cases, theUC component may need to establish a shared secret with a remote device so that no other entities onthe network can eavesdrop on the communication. Certificate Authorities (CAs) make these scenariospossible by using cryptographic techniques to “digitally sign” a set of credentials, which can then beused for the purposes of identification and confidentiality. The CA must be trusted by bothcommunicating parties in order to allow this trusted exchange of cryptographic information to occur.In order for the DoD PKI CA to create a certificate, it has to know what information to “digitally sign.”When providing certificates for a human, this set of information would include things like the person’sname and the organization to which they belong. But for a device, like an Edge Boundary Controller(EBC), this information would include things like an IP address or the Fully Qualified Domain Name(FQDN) assigned to the device. The use of a FQDN is preferred.The following table summarizes the information that will minimally need to be known for each interfaceon the device that requires certificates in order to generate the “Certificate Signing Request” (CSR), alsoknown as the “to-be-signed certificate:”6
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011Information Required to Create a Certificate Signing Request for an UC DeviceFieldExampleNameebc1redCountry (C)USState (ST)Texas(this field is not always used)Locality (L)Lackland AFB(this field is not always used)Organization (O)U.S. GovernmentUnit (OU)DoD(this field may appearmultiple times, example:OU DoD, OU PKI, etc.)server1.example.dod.milor192.168.2.100Common Name (CN)(populates theCommon Name valuein the Certificate’s“Subject” field)Key Size(2048 bits, may differfor SIPRNET)(depending on whether anFQDN or IP address is used –FQDN is preferred for thisfield)2048NotesA unique name for interface on the UCcomponent to which this certificate will beassignedThe country associated withthe entity controlling thisequipment. This willgenerally be “U.S.” for theDoD PKI (External Certificate NOTE:Authorities, which use aThe Localseparate root from the DoD RegistrationPKI, can grant certificates for Authorityforeign nationals)may editthese fieldsThe state associated withafter the CSRthe entity controlling thishas beenequipment.submitted.The locality associated with(See Sectionthe entity controlling this1.4)equipment.The organization associatedwith the entity controllingthis equipment.Enter the unit associatedwith the entity controllingthis equipment.The IP (v4 or v6) address or Fully QualifiedDomain Name (FQDN) assigned to this device(use of a fully qualified domain name isrecommended because IP addresses can changeas the network is redesigned or moves from IPv4to IPv6, necessitating reissuance of certificates.Also recent guidance from the JITC PKI labsuggests that IP addresses may not be allowed inthe future.)The naming conventions in DISA NS2 publishedUC deployment guides should be followed.It is recommended that the 2048 bit size beused wherever possible given its greatersecurity strength. The DoD PKI has ceasedissuance of 1024 bit certificates on NIPRNETas of the end of 2010. See Section 2.6 fordetails.7
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011The Department of Defense (DoD) requires the Common Name (CN) identified in the certificate beunique across the entire DoD. The easiest way to ensure uniqueness is to use a Fully Qualified DomainName (FQDN). Current DoD PKI specifications indicate that Internet Protocol (IP) addresses can also beused, but these can be volatile as networks are consolidated and redesigned.Note that if FQDNs are used, you may need to configure your Domain Name Service (DNS) servers tomap these FQDNs to IP addresses or manually configure name resolution tables locally on the device sothat the FQDN placed in the certificate and assigned to the equipment resolves to the appropriate IPaddress. This step is not necessary for all applications that use certificates (e.g. management interfacemay require this, but the call signaling interface may not) so be sure to check with the vendor of yourequipment to determine whether this step is required. Also, check with your UC equipment vendor toensure that it supports the use of FQDNs in certificates.1.2.2Using Commercial Tools or UC Equipment to Generate a CSRSome UC devices can generate their own certificate signing request while other devices rely on the useof commercial tools to generate the signing request. The request is generated by taking the informationidentified in Section 1.2.1 and creating a standard formatted message called Public Key CryptographyStandard (PKCS) #10 message. Other certificate signing request formats exist, however PKCS#10 is theformat primarily used with the DoD PKI and supported by most equipment.If your equipment does not support generation of a certificate signing request, the Air Force hasdeveloped a detailed guide explaining how to generate a certificate signing request using theinformation identified in Section 1.2.1 and it is located at the following website:https://afpki.lackland.af.mil/html/pke cots.asp (this site is accessible from .mil domains only)This website provides step-by-step guidance on generating a certificate request using many standardcommercial products. The DoD PKI is also in the process of developing a tool called CRIMSON which willassist with this aspect of the process, however this tool will not be available until mid-CY 2011. A betaversion is available for download by visiting www.forge.mil.Ensure that you are using a NIST FIPS 140-2 validated product to generate your certificate signingrequest and public/private RSA key pairs. Use of FIPS 140-2 validated cryptography ensures thatcryptographic operations, such as generating key pairs, are being correctly performed and use strongrandomization. Also, if the equipment itself did not generate the key pairs and signing request, take theappropriate precautions to secure the private key associated with the certificate signing request.Especially since the private key will eventually need to be loaded into the UC component. Most tools willprovide an option to use a password to protect the private key so that it is not stored in plaintextformat.Create a backup copy of the private key corresponding to a certificate signing request and store it in asecured location. If one loses the private key corresponding to the CSR, then the certificate returnedfrom the DoD PKI cannot be used. In fact, the DoD PKI will have to revoke the certificate, whichincreases the size of the DoD PKI CA’s certificate revocation list, increases the bandwidth used toperform revocation checking, and increases operational costs. The DoD PKI LRAs also may require8
Utilizing the DoD PKI to Provide Certificates for Unified Capabilities ComponentsRevision 1.2November 3, 2011remedial t
seeking to obtain DoD PKI issued certificates or tokens for human identification purposes (such as Common Access Cards), since this process will differ. Also, for those who only need test (non-operational) DoD PKI