Transcription
CIP Version 5 Transition Program –Lessons Learned & FAQsTom Hofstetter, CIP AuditorJune 2, 2015
Disclaimer Not speaking for the Commission, for NERC, for SPPRE, etc. These are dynamic issues, so content, descriptions,and musings may be an educated guess about who’sresponsible, what it is, where it’s going, when it’s likely,why it’s needed, or how it’s done Any perceived “guidance” on specific approaches forimplementing the CIP V5 Standards is unintentionalo compliance is dependent on how it is implementedo there may be other ways to comply with theStandards that are not discussed I focus on system-wide TFE issues; details typically canbe addressed by the Region2RELIABILITY ACCOUNTABILITY
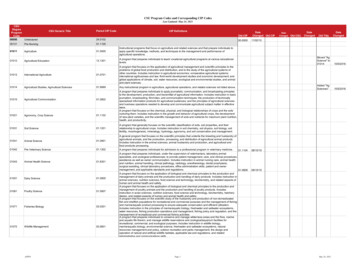
Lessons Learned and FAQsTopicGeneration SegmentationLesson LearnedDate Posted forStakeholder CommentOctober 23, 2014Far-End RelayBES Impact of TransmissionScheduling SystemsLesson LearnedFAQOctober 23, 2014April 24, 2015 Grouping of BES Cyber SystemsLesson LearnedMarch 2, 2015Shared Equipment at aSubstationVirtualizationIntrusion Detection SystemsFAQApril 1, 2015Lesson LearnedFAQApril 17, 2015April 30, 2015 Interactive Remote AccessLesson LearnedJanuary 8, 2015Mixed Trust EACMSMultiple Physical AccessControlsProtecting Physical PortsLesson LearnedFAQJanuary 8, 2015April 1, 2015FAQApril 1, 2015Identifying Sources of PatchManagementMitigating Threat of DetectedMalicious CodeFAQApril 30, 2015FAQNovember 25, 2014FAQApril 1, 2015Vulnerability Testing of PhysicalAccess Controls3Lesson Learned or FAQAt a glance: 23 originaltopics50 FAQs7 LLs57 topics viaSection 115 issuesaddressed byNERCRELIABILITY ACCOUNTABILITY
Lessons Learned & FAQ Document effective approaches to implementation orcompliance Suggestions on “how” to comply Somewhat prescriptive but not binding Uses industry comment and vetting approach4RELIABILITY ACCOUNTABILITY
Guidance: Effective Approaches toComplySection 11 Guidance Development Process5RELIABILITY ACCOUNTABILITY
NERC Communications Used when question is not about approaches toimplementation nor compliance Rather, used to address questions regarding the meaning of aparticular requirement or term Defers to Standard Drafting Team portions of “the record”: Guidelines and Technical Basis Comment responses Issued April 21, 20156RELIABILITY ACCOUNTABILITY
Status Far-end RelayGeneration SegmentationMixed Trust EACMsInteractive Remote AccessGrouping of BES Cyber SystemsVirtualization (Networks and Servers)3rd Party Notifications of medium impact assets*Generation Interconnection *Programmable Electronic Devices *Serial Devices that are accessed remotely *Network devices as BES Cyber Systems *Control Centers operated by TOs and non-registered BAs *General FAQs* - Not Issued as Lessons Learned or FAQ7RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 8Far-end Relay (AKA Transfer-Trip)–Status: Approved by Standards Committee and Posted asFinal.–The far-end relay does not automatically inherit a Mediumimpact categorization if the near-end substation satisfiesthe qualifications of Criterion 2.5.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 9Generation Segmentation–Status: Approved by Standards Committee and Posted asFinal.–BES Cyber Systems associated with a generating plant inexcess of 1500 MW Net Real Power Capability can besegmented such that there are no Medium impacting BESCyber Systems.–Includes a discussion of evidence required to demonstratesufficient segregation.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 10Mixed Trust Electronic Access Control or MonitoringSystems–Status: Addressing industry comments–The issue is whether corporate resources (Active Directoryservers, remote access authentication servers, log servers,Intrusion Detection Systems, etc.) supporting bothcorporate and Electronic Security Perimeter accesscontrol are Electronic Access Control or MonitoringSystems.–Current position is that if the Cyber Asset is providingelectronic access control or monitoring support to the CIPenvironment, the Cyber Asset is an EACMS for thepurposes of CIP compliance.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 11Interactive Remote Access (Scripts and ManagementConsoles)–Status: Addressing industry comments–provide guidance on implementing security controls forthe use of Interactive Remote Access.–Open question is whether scripts under programmaticcontrol and actions performed by management consolesconstitute Interactive Remote Access.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 12Grouping of BES Cyber Systems–Status: Addressing industry comments–Purpose is to describe useful methods to group BES CyberAssets into BES Cyber Systems (BCS).RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 133rd Party Notifications of medium impact assets–Status: Issued as a NERC “Communication” and not aLessons Learned–For IRC 2.3 and 2.6 Reliability Coordinator, PlanningCoordinator, or Transmission Planner addresses theFacility (generation or transmission)–The asset owning registered entity must then determinewhich BES Cyber Assets or BES Cyber Systems support theidentified FacilityRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 14Generation Interconnection (IRC 2.5)–Status: Issued as a NERC “Communication” and not aLessons Learned–The question is whether the line (sometimes referred to asthe generator lead line) operated at transmission voltagesbetween a generating plant and a transmission substationis a Transmission Facility for the purposes of the CIP-002-5Impact Rating Criteria.–Position is for transmission line to be considered aTransmission Facility and included in the Criterion 2.5calculation, the line must be used for network flow of theBulk Electric System and connected to anotherTransmission station or substation.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition Programmable Electronic Devices (PED)15–Status: Issued as a NERC “Communication” and not aLessons Learned–Went back to the official record of the Standard DraftingTeam and determined that questions raised were alreadyaddressed–Programmable electronic device (PED) “Is an electronicdevice which can execute a sequence of instructionsloaded to it through software or firmware, andconfiguration of an electronic device is included inprogrammable.” - SDT Considerations of for V5 PostingRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 16Virtualization (Networks and Servers)–Status: To be issued as a Lessons Learned–The concern with virtualization is when there is a mixedtrust environment–The standards do not do a good job of addressing thetechnology–For virtual servers where a mixed trust environment isbeing used there will be a lot of scrutiny of securitycontrols in place–For networks using mixed trust will need to see that theappropriate Electronic Access Point Controls are in placefor the deviceRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 17Serial Devices that are accessed remotely–Status: Issued as a NERC “Communication” and not aLessons Learned–ERC definition – “ ability to access ”–The position is that terminal server/gateways that areconnected using external routable connectivity withserial devices on the back end, and that perform noapplication-level processing are external routableconnectivity all the way to the serial device. They mustbe within an ESP and have protection of an ElectronicAccess Point.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 18Serial devices with ERC: Use a “dumb” converter (e.g., a “terminal server” No application-level processing or proxying of traffic Data passed from routable connection to serial connectionwith no application-level processing Require an EACMSRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 19Serial devices without ERC: Use application proxy converter (e.g., a “data concentrator”or “application gateway”) Application or protocol break between routable network andserial device Data passes through application-level filtering or conversionRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 20Network Devices and BES Cyber Systems–Status: Issued as a NERC “Communication” and not aLessons Learned–Exclusion: Cyber Assets associated with communicationnetworks and data communication links betweendiscrete Electronic Security Perimeters.–Network devices can be considered BCAs based on theBCA definition, especially if inside ESPs–ERO will use discretion to exempt any Cyber Assetsassociated with non-routable communicationnetworks/links that would be exempt if they wereroutable communication between discrete ESPsRELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition Control Centers operated by TOs and non-registeredBAs– Status: Issued as a NERC “Communication” and not aLessons Learned– High Impact Rating (H)o–Medium Impact Rating (M)o211.3 Each Control Center or backup Control Centerused to perform the functional obligations of theTransmission Operator for one or more of the assetsthat meet criterion 2.2, 2.4, 2.5, 2.7, 2.8, 2.9, or 2.10.2.12. Each Control Center or backup Control Centerused to perform the functional obligations of theTransmission Operator not included in High ImpactRating (H), above.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 22Control Centers operated by TOs and non-registered Bas– Went back to the official record of the Standard DraftingTeam and determined it was clearly addressed that theSDT intent was the functions you are performing and nothow you are registered.RELIABILITY ACCOUNTABILITY
What’s Trending with CIP V5Transition 23General Frequently Asked Questions (FAQs)–3 are already posted on the V5 Transition Program pageon the NERC web site as “Technical FAQs”–34 FAQs were posted for industry comment April 2 withcomments due by May 15.–More FAQs posted May 1; comments due June 15RELIABILITY ACCOUNTABILITY
References 24CIP Version 5 Transition page: .aspxRELIABILITY ACCOUNTABILITY
QuestionsTom Hofstetter, CISA, CISSPCIP Compliance Auditortom.hofstetter@nerc.net
CIP Version 5 Transition Program – Lessons Learned & FAQs Tom Hofstetter, CIP Auditor . is a Transmission Facility for the purposes of the CIP-002-5 Impact Rating Criteria. – Position is for transmission line to be considered a Transmission Fa